Don’t Get Reeled in By Financial Phishing Scams

NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
It will surprise approximately no one that scammers attack anyone and everyone. They’re in it to maximize profits, of course. When it comes to potential victims that you would hope would somehow be exempt, the financial services industry naturally comes to mind. Unfortunately, that sector is highly susceptible to phishing attacks, given the nature of precious information required from consumers when interacting with any given institution. Not surprisingly, FinServ domains—or more accurately, the assets and customer information they represent–are a motherlode for hackers. That’s why we wanted to take a closer look at the top financial services in both the United Kingdom and the United States to see how likely they are to be ensnared in phishing scams via spoof domains set up by criminals.
For those of you who caught last year’s PhishEye research on financial and retail brands, you’ll recall that we discovered plenty of bad actors squatting on the net waiting for the right moment to strike on a popular name brand. PhishEye finds existing domains that are variations of a keyword (typically a brand name) and monitors new registrations to find infringing domains as soon as they come into being. Among the domains it catches, PhishEye also flags those identified as “high risk,” meaning domains that received DomainTools Reputation Engine scores of 70 or higher. Scores in that range indicate that the domains are closely connected to other domains that have already been blacklisted for spam, malware, or phishing.
Because phishing is a form of social engineering designed to fool a human victim into taking a specific action, there are certain characteristics that phishing domains often exhibit:
- “Typosquatting:” the name itself is often a very close variation on the legitimate brand, created via typos or look-alike characters (called homoglyphs). For example, Wells Fargo owns the domain ‘wellsfargo.com,’ while a phisher registered ‘wellsfargos[.]info.’
- Another cybersquatting technique that allows the phisher to use a correct spelling of the brand is to append another word or words onto the brand name. Using our same example, another domain PhishEye found is “text-notification-wellsfargo[.]com.” Many potential phishing victims don’t realize that a domain name constructed that way should raise major red flags.
PhishEye is effective at detecting these kinds of variations on a name, and it can tell us about existing registrations and can spot new ones as well. For our research, we looked at the baseline of existing registrations. Read on for our results.
Choosing our subjects
Using the logic that the bigger the firm, the bigger the bullseye on them, we created lists of the largest financial institutions in the US and the UK and used these as our PhishEye queries. PhishEye returned lists of domains corresponding to each keyword (brand). We did a bit of manual review of the lists to ensure we didn’t count domains that may not have clearly been registered with malicious intent.
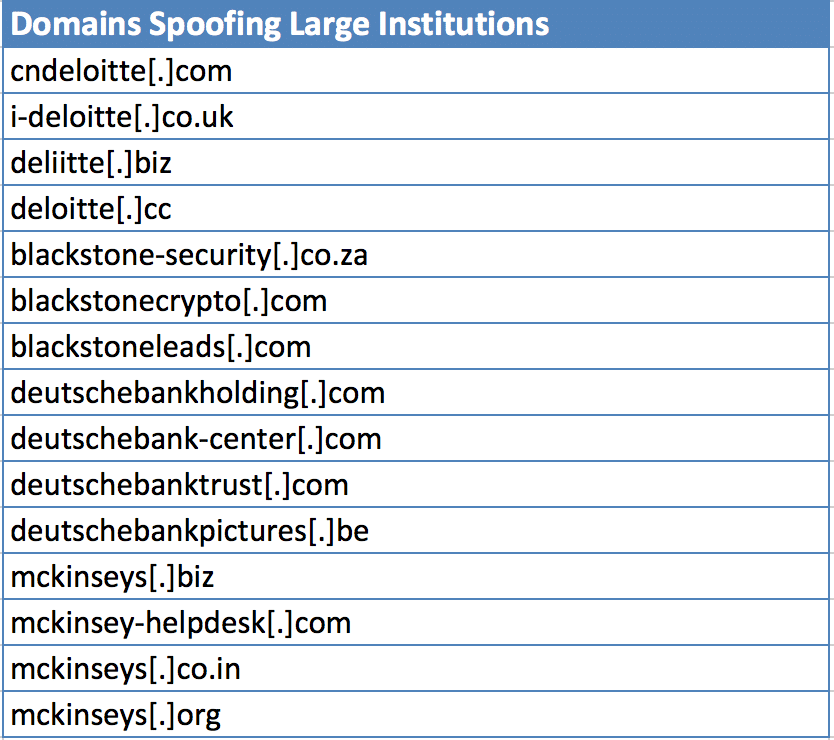
UK/Europe Highlights These were the 4 most-spoofed European institutions in our study:
- Blackstone
- Blackrock
- Deutsche Bank
Some specifics:
- For all of the spoofed banks, we have identified ‘classic’ phishing techniques used, such as cybersquatting (taking a non-typo domain that includes the properly-spelled name) or typosquatting (using typos to create shorter domain names that the phisher hopes will evade human detection). Some examples include a domain targeting Deloitte (a ‘big four’ accounting firm) was listed as [deloitte.cc], while one that spoofed Deutsche Bank was ‘deutschebankholding[.]com.’ It’s easy to see how even a savvy customer of Deloitte or Deutsche Bank could be tricked by those domains.
- Worth noting: two of the largest institutions, KPMG and PWC, represent somewhat tricky cases when it comes to detecting phishing domains at Internet scale. Because they are short combinations of letters, there are many domains that may have nothing to do with phishing, but which may or may not be dangerous for other reasons. Examples include the domains ‘h78wkpmg[.]com’ or ‘gtpwca3[.]ml.’ Those both have high risk scores, but it is possible that they received those scores for other malicious activity such as command-and-control of a botnet. If you’re on the lookout for spoofs of those institutions, context is everything: if you receive an email purporting to be from KPMG or PWC, this is where good phishing-detection practices, as outlined in our conclusion below, may save the day.
US key takeaways:
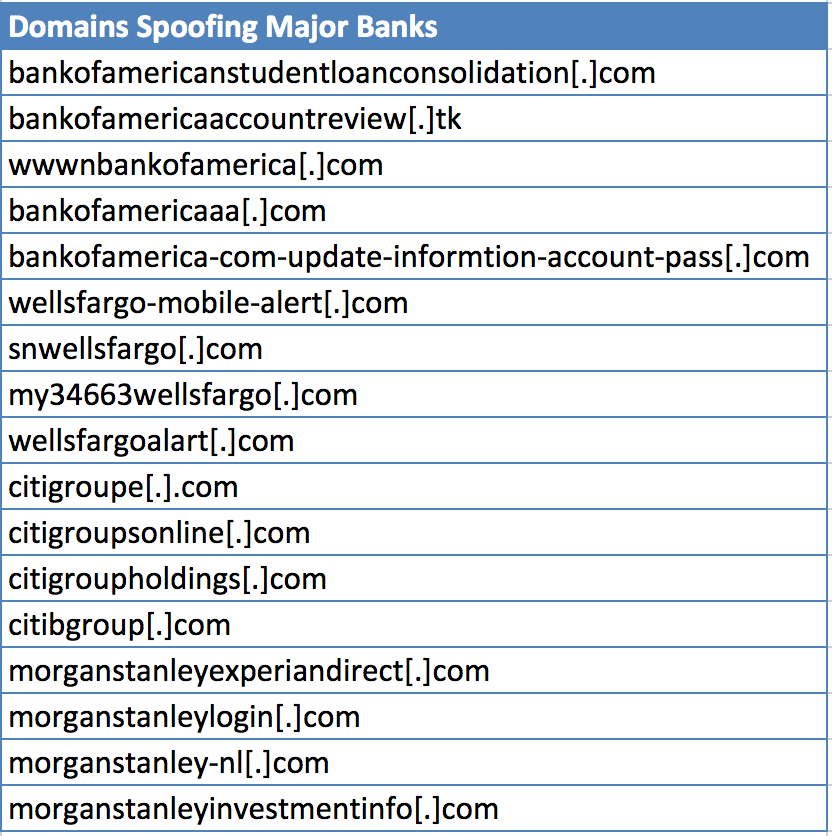
The top 4 US institutions in the study were these:
- Bank of America
- Wells Fargo
- US Bank
- TD Bank
Bank of America and Wells Fargo are two of the banking-related names most often spoofed by phishers – with over 180 “high risk” domain names associated with each institution, their popularity gives phishers a bounty to work with. Similar to the malicious domain names found in the UK, classic phishing methods are used such as misspelling of words or names that prompt quick action from an end user. For instance, it wasn’t uncommon to see domain names such as: wellsfargoalart[.]com, privacy-wellsfargo[.]com, or bankofamerica-com-update-informtion-account-pass[.]com. (By the way, we couldn’t help snickering about that last one: the phisher misspelled “information,” when there was no reason for them to do so. Part of the whole idea of creating a multi-word domain name like this is so that you don’t have to resort to typos!)
Steering Clear
While some of the spoofs are downright laughable, falling to a scam is obviously serious business. And some of the typos favored by phishers—especially homoglyphs that use characters that look almost identical to others—can be hard to spot. None of us should think that we are unphishable. Instead, exercise caution about any links that come via email, SMS, or ads.
- Familiarize yourself with the feature that many browsers have (desktop only, unfortunately) that expose the URL behind a link, typically near the bottom of the window. Hover the cursor over the link and look carefully at the URL. This can be an extremely effective way to catch homoglyph spoof domains because the domain name of such a URL will begin with the characters “xn--”. (For more information about homoglyph phishing, please see this blog post.)
- If you aren’t 100% certain that a link to your bank truly did come from your bank, and will lead to its actual domain, don’t click it. Instead, navigate “manually” to your bank’s site and take it from there.
- Remember the importance of context. If you initiate some kind of action with your bank, and then receive an email from them right afterward confirming or notifying you of the action, it’s less likely that the email is a phish; on the other hand, emails that come “out of the blue” and ask you to follow a link or open an attachment are much less trustworthy.
This isn’t a problem that will go away any time soon, so it’s best to be wary. A moment or two of examination of a banking-related email could save you money, time, and peace of mind.

