Introduction to SIE Channel 115: DDoS Events

PART I. What’s SIE Channel 115 All About?
1. DDoS (Distributed Denial of Service) Attacks
Stable and reliable Internet operations are critical to virtually every company these days (particularly in our Covid-19-impacted environment). Unfortunately, DDoS attacks can take even the largest companies or ISPs offline (or force targets to work very hard/spend lots of money to remain at least minimally online).
DDoS-As-A-Service is a real thing – no specialized expertise nor dedicated infrastructure is required for an attacker “to go to war.” Rather, attackers can “outsource” their DDoS needs.
Attacks may be “brute force” (volumetric) attacks consisting of hundreds of Gbps worth of unwanted traffic dumped on a target’s transit and peering circuits. Or the attack may be more nuanced – perhaps a constantly-mutating application-layer attack.
Victims can’t just “wait it out” – these attacks can potentially continue “forever.” Attackers (often located abroad) have little or no fear of prosecution. Even paying ransom demands may not always make the DDoS pain go away.
2. Instrumentation Is Key
You need to know what attacks are underway, and what techniques are being used in those attacks. You need visibility. Your own networks are probably well-instrumented, so you can see the attacks that are currently hitting your own network (or your own customers’ networks).
But do you know what the attacks that everyone ELSE may be getting hit with look like? (How can you be SURE if you only know what SOME of the attacks look like?)
And what’s coming NEXT? The miscreants ARE likely hard at work developing and testing new attack tools. Will you be ready for what’s coming NEXT? (How could you be if you have no idea what new tools may be under development?)
Farsight can help. Our Security Information Exchange (SIE) offers both a “raw” darknet (“network telescope”) channel in PCAP format and a second channel with identified DDoS events derived from the raw channel’s traffic.
Today we’re going to focus on Channel 115, the SIE Channel containing pre-identified DDoS events gleaned from darknet traffic.
But why would a darknet help us spot these attacks? For that matter, what IS a darknet?
3. Darknets
A darknet is a chunk of network address space that is announced to the Internet, but which doesn’t host any real services – no end users, no web servers, no mail servers, no name servers, no social media, nothing at all.Since it isn’t originating any OUTBOUND traffic, we’d normally expect it to not see any INBOUND traffic.However, we KNOW that that’s not the case. The bad guys are constantly probing the entire Internet, just like burglars checking for unlocked car doors or houses with open windows.This means that any address that’s announced to the Internet will CONSTANTLY be subject to unsolicited scans from bad guys looking for exploitable systems.
4. Known-Exploitable Hosts vs.Spewing Forged Traffic Over Virtually The Entire Internet
Carefully executed DDoS attacks will first do a scan to identify hosts that have a vulnerability of interest. After a bunch of these vulnerable hosts have been found, those hosts (and only those hosts) will then get sent spoofed traffic (pretending to be “from” the target of the attack). The responses from that set of vulnerable hosts will then cascade in, flooding the target of the attack and swamping that target’s network connectivity.If your botnet is big enough, however, you may simply send spoofed traffic virtually “everywhere,” relying on the fact that at least some of that indiscriminate traffic (maybe just a fraction of one percent) will hit an exploitable device. “Small” though that number may be in percentage terms, it may be Nx100,000 hosts, often MORE than enough to DDoS a typical target.
So why does the darknet see ANY of this traffic? The promiscuous (“spray and pray”) approach ends up accidentally hitting the darknet (and thus ends up acting as input data for Channel 115). Bad guys would like to AVOID doing that, but since they don’t know exactly where our darknet is located, they have a hard time avoiding “bumping into it.”
5. Getting Some Observations From Channel 115
nmsgtool
is the software that’s often used to read traffic from SIE Channels. Let’s assume we want to get 5 observations from Channel 115. We’d do that with the command:
$ nmsgtool -C ch115 -c 5 -J - | \
jq —unbuffered -c '.message.payload' | \
base64 -d —noerrcheck | \
jq -r —unbuffered '.'
Decoding that command:
6. An SSDP Amplification Observation From Channel 115
Note: Victim IPs are defanged here and below by converting the first literal dot in the IP address to “[dot].” The same IPs in the actual channel are not defanged.
{
"Victim IP": "196[dot]52.43.59",
"Number Of Packets": 40,
"Packet Rate": 0.395757659887,
"Number of Unique Sources": 40,
"Duration of Attack (in seconds)": 101,
"Attack Start Time": 1584663604,
"Attack End Time": 1584663706,
"Type of Attack": "SSDP Amplification",
"Victim City": "",
"Victim Country": "South Africa",
"Victim ISP": "",
"Victim Organization": "",
"Whois Information": {
"asn_registry": "afrinic",
"asn_date": "1995-10-09",
"asn_country_code": "ZA",
"raw": null,
"asn_cidr": "196.52.43.0/24",
"raw_referral": null,
"query": "196.52.43.59",
"referral": null,
"nets": [
{
"updated": null,
"handle": "CA12-AFRINIC",
"description": "Net Systems Research, LLC",
"tech_emails": null,
"abuse_emails": null,
"postal_code": null,
"address": "LogicWeb Inc.\n4509 Steeplechase Dr.\nEaston, PA 18040\nUSA",
"cidr": "196.52.43.0/24",
"city": null,
"name": "NetSystems",
"created": null,
"country": "US",
"state": null,
"range": "196.52.43.0 - 196.52.43.255",
"misc_emails": "[email protected]"
}
],
"asn": 60781 <--That's Leaseweb BV, Netherlands
}
}
If you’re not familiar with SSDP Amplification attacks, one nice introduction to that sort of attack can be seen here.
7. An SNMP Amplification Example From Ch115
{
"Victim IP": "170[dot]130.187.42",
"Number Of Packets": 40,
"Packet Rate": 0.438573803331,
"Number of Unique Sources": 40,
"Duration of Attack (in seconds)": 91,
"Attack Start Time": 1584727292,
"Attack End Time": 1584727383,
"Type of Attack": "SNMP Amplification",
"Victim City": "Alpharetta",
"Victim Country": "United States",
"Victim ISP": "MACTEC",
"Victim Organization": "MACTEC",
"Whois Information": {
"asn_registry": "arin",
"asn_date": "2014-02-26",
"asn_country_code": "US",
"raw": null,
"asn_cidr": "170.130.184.0/22",
"raw_referral": null,
"query": "170.130.187.42",
"referral": null,
"nets": [
{
"updated": "2019-02-28T00:00:00",
"handle": "NET-170-130-0-0-1",
"description": "Eonix Corporation",
"tech_emails": "[email protected]",
"abuse_emails": "[email protected]",
"postal_code": "89169-6014",
"address": "3773 Howard Hughes Pkwy. Suite 500S",
"cidr": "170.130.0.0/16",
"city": "Las Vegas",
"name": "EONIX",
"created": "2014-02-26T00:00:00",
"country": "US",
"state": "NV",
"range": "170.130.0.0 - 170.130.255.255",
"misc_emails": null
},
{
"updated": "2019-03-14T00:00:00",
"handle": "NET-170-130-184-0-1",
"description": "ServerHub Los Angeles",
"tech_emails": "[email protected]",
"abuse_emails": "[email protected]",
"postal_code": "90014",
"address": "530 W 6th Street",
"cidr": "170.130.184.0/22",
"city": "Los Angeles",
"name": "SERVERHUB-LOS-ANGELES",
"created": "2019-03-14T00:00:00",
"country": "US",
"state": "CA",
"range": null,
"misc_emails": null
}
],
"asn": 62904 <-- Eonix Corporation, Las Vegas NV
}
}
If you’re not familiar with SNMP amplification DDoS attacks, see here for an example.
8. Brief List Of The Types of DoS Attacks Called Out In Channel 115
Basic Attacks
- TCP SYN Flood
- UDP Flood
- ICMP Flood
- DNS Flood
Reflective Protocol Attacks
- Network Time Protocol (NTP)
- Domain Name System (DNS)
- Simple Network Management Protocol (SNMP)
- Simple Service Discovery Protocol (SSDP)
- Character Generator Protocol (CharGen)
- Quote of the Day (QOTD)
- Quake 3
- Network Basic Input/Output System (NetBios)
9. More Information About What Ch115 Finds And How…
- “On the inference and prediction of DDoS campaigns,” Claude Fachkha, Elias Bou-Harb and Mourad Debbabi, Computer Security Laboratory, CIISE, Concordia University and NCFTA Canada, Montreal, QC, Canada, Wirel. Commun. Mob. Comput. 2015; 15:1066-1078 Published online 6 August 2014 in Wiley Online Library (wileyonlinelibrary.com). DOI: 10.1002/wcm.2510
- “Inferring distributed reflection denial of service attacks from darknet Claude Fachkha, Elias Bou-Harb, Mourad Debbabi”, Computer Security Laboratory, Concordia University, Canada National Cyber-Forensics and Training Alliance, Canada. Computer Communications. 62. 10.1016/j.comcom.2015.01.016.
PART II. An Aside On Something Channel 115 Doesn’t Directly Address: WHY Was A Given Site Attacked?
10. Finding Out WHAT Is Happening Is Very Important, But Many People Are Also Interested In WHY It Happened
Motivation, just like attribution, can be hard to pin down, but we know that many people are very interested in WHY a given target may be getting attacked.
We know, for example, that some cyber extortionists have attacked online gambling sites immediately prior to major scheduled sporting events (Superbowl, World Cup, Kentucky Derby, etc.), a time when the gambling site would normally have lots of people placing bets. In order to protect that revenue stream, the online gambling site may be willing to pay online extortionists just to “make the attack go away.”
Other cyberattacks may be politically motivated, perhaps targeting government or military sites, sites operated by political parties or candidates, or news media-related servers.
Yet another category of attacks may be “red-on-red” attacks whereby one group of cyberattackers may attack another group of cyberattackers, perhaps as revenge for a perceived slight or as a way of demonstrating their own power for a potential customer.
In still other cases, an attack may be indirect, attacking someone providing services to an attack target, or a third party on the same network segment as the actual target.
Ultimately, this will be something you need to research yourself (if interested in this area).
11. What Can We Find Out About 196[dot]52.43.59 (From The 1st Example)?
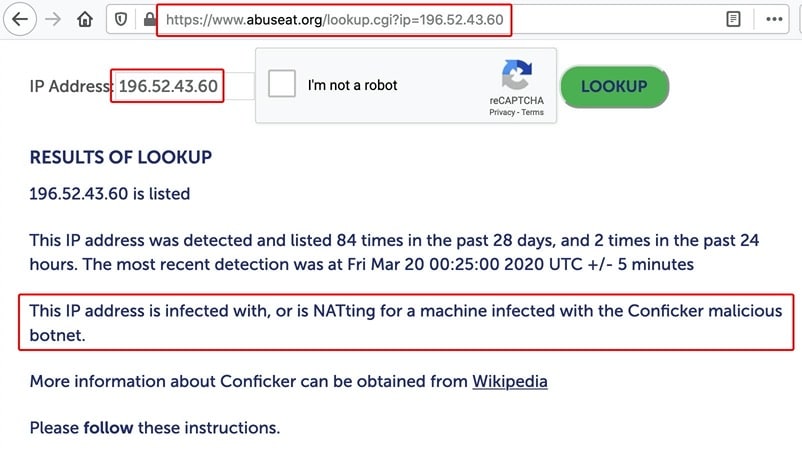
And if that system was infected with Conficker, what do we know about what Conficker hosts get into?
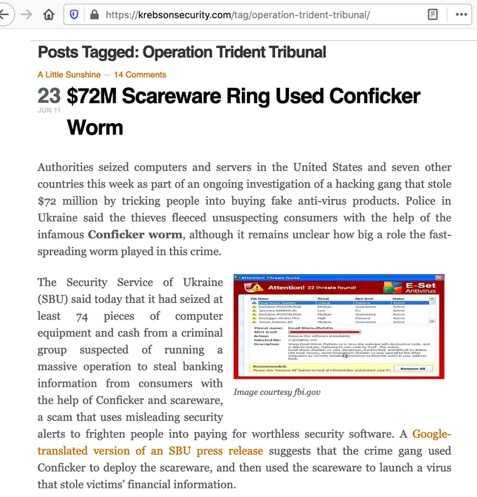
“If I WAS Just Interested In Conficker, Is Ch115 The Best One for Me?”
Not necessarily. Consider SIE Channel 80 instead.
See Conficker and a Brief Tutorial on Working With SIE Channel 80 Sinkhole Data
12. What Do We Know About 170[dot]130.187.42 (From The 2nd Example)? Checking the CBL Again…
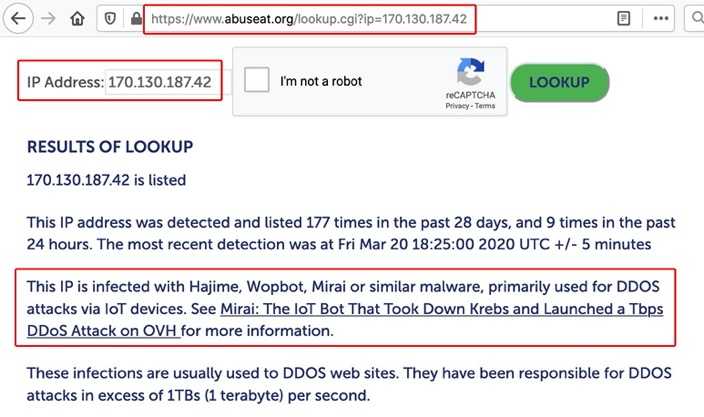
Not familiar with Mirai? Researcher Brian Krebs wrote numerous pieces about the botnet including Hacked Cameras, DVRs Powered Today’s Massive Internet Outage below:

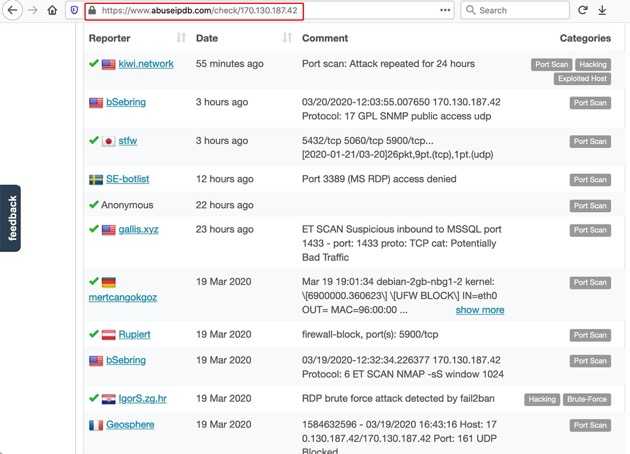
Another site’s notes on 170.130.187.42:
13. Article Takeaways
- Channel 115 is a DDoS channel created by Concordia University. It lists denial of service events based on data from the Farsight Security Information Exchange (SIE) darknet channel.
- The darknet typically sees traffic associated with Internet-wide indiscriminate attacks.
- SSDP amplification attacks and SNMP amplification attacks are examples of two common attacks. Examples for those attacks are provided.
- We also shared the full set of attacks that may be detected and reported.
- Users are often interested both in knowing WHAT is happening (who’s getting attacked? how are they being attacked?) and WHY they’re being attacked. The DDoS channel explains WHAT is happening; it is up to the user to determine WHY.
- We provided a couple examples of how to figure out WHY someone may be conducting attacks for our two examples.
If you’re interested in learning more about Channel 115 or other Security Information Exchange (SIE) data feeds, please contact Farsight Security Sales at [email protected].
Joe St Sauver Ph.D. is a Distinguished Scientist with Farsight Security®, Inc.


