Coming up this week on Breaking Badness. Today we discuss: et tu, Brute Ratel??, Maui Wowie, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
et tu, Brute Ratel??
- Hacking groups and ransomware operations are moving away from Cobalt Strike to the newer Brute Ratel post-exploitation toolkit to evade detection by endpoint detection and response (EDR) and antivirus solutions
- Cobalt Strike came into the picture as a red team tool, meant for legitimate pen testers and red teams to use in their work simulating attacks
- It’s extremely effective, and so cracked versions of it have been out there for years being used by adversaries all over the place
- It allows you to have compromised devices beacon out to command and control, and carry out all kinds of surveillance within the victim environment
- Brute Ratel entered then entered the picture (released as “Brute Ratel Command and Control Center” or BRc4) as an alternative to Cobalt Strike for red team penetration testing engagements
- There’s evidence that some APT activity from the likes of Cozy Bear (APT 29) and also ransomware action from former Conti folks are using Brute Ratel
- Cobalt Strike has been extremely popular, so there’s incentive to detect it
- Brute Ratel, though, is designed to be much more elusive when it comes to those detections
- Brute Ratel is supposed to only be sold to legitimate businesses
- There’s a bit of a vetting process where the developer manually checks customers wishing to obtain a copy of it (and they go for $2,500 a pop)
- Obviously, it has leaked
- The developer claims it was done by a disgruntled customer, but there’s some evidence that there’s other deception going on here, where some threat actors are just concocting fake US companies and using those “company” emails to get a hold of copies
- For now, while there is a low detection rate, really all you can do in terms of mitigations is to be very tight on all other means of detection you have, understanding of course that Brute Ratel (or Cobalt Strike) is not the the threat actor’s objective but just one of the tools to get them there—you have possibilities of detection in various stages of the operation
- It really comes down to the tried and true advice that it seems we give all the time, but it’s still pretty key
- Have all your defenses tuned as well as possible. Have your users on the lookout. Don’t re-enable macros in Microsoft even though they are threatening to reverse themselves on the default enabling of those. Monitor for suspicious domain registrations!
- It really comes down to the tried and true advice that it seems we give all the time, but it’s still pretty key
Maui Wowie
- State-sponsored actors are deploying the unique malware–which targets specific files and leaves no ransomware note–in ongoing attacks
- Maui ransomware has been active since April 2021 and has unique characteristics from other ransomware-as-a-service (RaaS)
- There is no ransom note with recovery instructions, which is unusual as threat actors typically want to get paid as quickly as possible
- It’s designed for manual execution by a threat actor, meaning operators decide which files to encrypt
- Manual executive is increasing in popularity as it targets the most important assets on a network
- Targeting specific files, though, does show good faith from the bad actors to the victims in that they won’t have to rebuild their entire server
- This attack is targeting the healthcare industry in particular
- It’s a lucrative industry usually having outdated IT systems
- Healthcare systems typically do not want to put patients at risk, therefore they usually work faster to rectify any threats
- This is not the only healthcare attack as of late
- The Quantum ransomware attack affected 657 healthcare organizations
- CISA, the FBI, and the US Treasury said we can expect to see continued attacks on healthcare systems
- CISA issued an advisory regarding this attack including technical details as well as mitigations
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
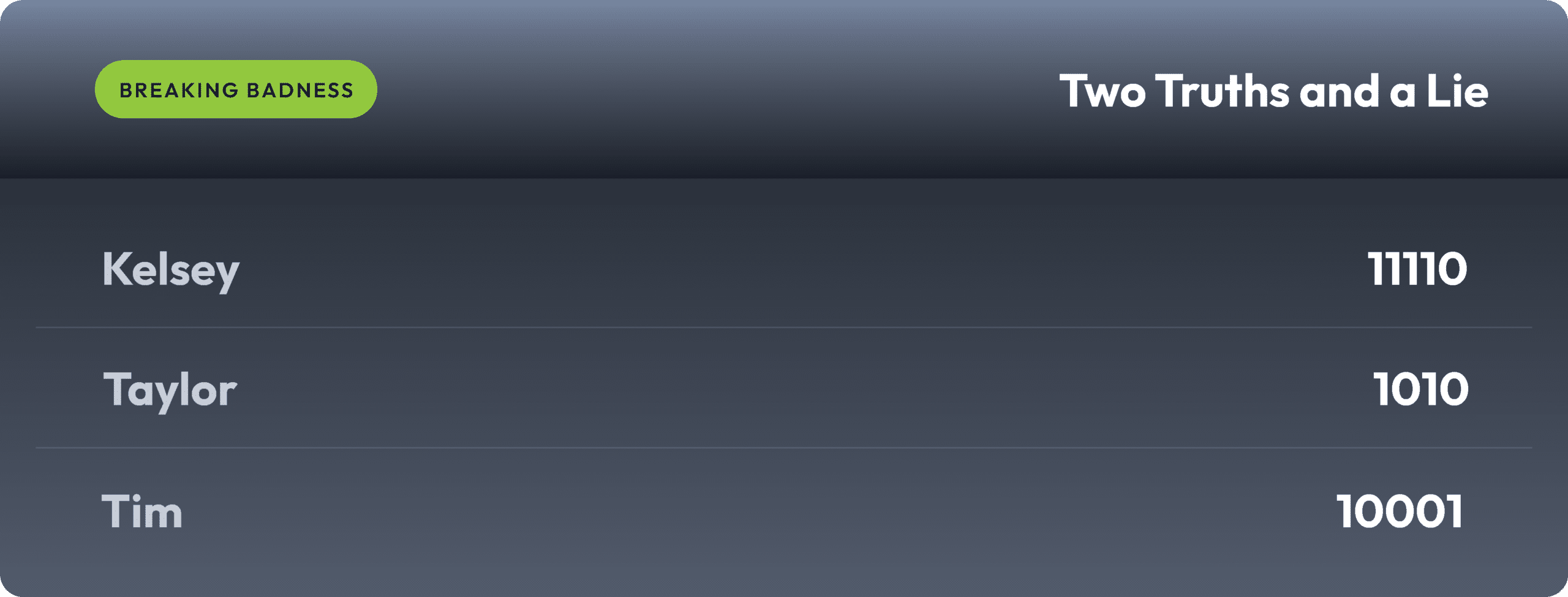
Current Scoreboard
This Week’s Hoodie/Goodie Scale
et tu, Brute Ratel??
[Tim]: 6/10 Hoodies
[Taylor]: 7.5/10 Hoodies
Maui Wowie
[Tim]: 3/10 Hoodies
[Taylor]: 4.23/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!

