DNS Threat Intelligence for Our Community

With the 2019 launch of the DomainTools MISP Plugin, we made DNS threat investigations available within the free open-source threat sharing platform. Our rich dataset continues to provide contextual enrichment for Indicators of Compromise (IOC) inside the non-commercial threat intelligence platform enabling our users to hunt for unknown malicious infrastructure.
Today we are delighted to announce DomainTools Iris Integration for TheHive and Cortex. With this integration, we extend our abilities in automating Incident Response (IR) and orchestration functions within Security Operation Centers (SOCs).
First things first – What is TheHive and Cortex?
TheHive is a scalable open-source solution built for SOCs, Cyber Security Incident Response Teams (CSIRTs), Computer Emergency Response Teams (CERTs) and any information security practitioner and allows them to investigate security incidents efficiently. Collaboration across the incident management phases and functions is at the heart of the platform. Cases can be created for every investigation either manually or automatically using templates which can vary based on the type of investigations.
Cortex is a standalone analysis engine and a perfect companion for TheHive. TheHive speaks natively to Cortex via REST API to perform quick assessments of observables.
Together, the two platforms can be a significant time-saver and take away some of the tedious tasks associated. Analysts can then use the Analyze functionality you can add and investigate a single or thousands of observables associated with the case. Finally, good old practices of associating TLP and source tags are also baked in the platform.
As TheHive project matured over the last 3 years, we noticed its adoption as a viable enterprise SOC/CSIRT/CERT tool in our customer base as well. As our users started operationalizing their incident management processes in TheHive, they quickly identified the need for DNS threat context in investigating incidents. Although many users already had access to our intelligence dataset, the analysts often had little to limited access to those applications. For some, who could access these upstream systems, they felt the burden of continuing their investigation and triaging in multiple toolsets.
The solution was apparent – enrich observables within TheHive with DomainTools Iris intelligence at scale and expound the value of incident management functions. With this integration, we bring in actionable truth along with evidence in the form of DomainTools analytics, Domain Risk Score, and threat evidence. All this leverages the much capable point-and-click interface within TheHive.
Before I dive deeper into the features, mechanisms, or the nuances of this integration, I would like to extend my thanks to my teammates, TheHive project members, and most importantly our customers, who have helped materialize the integration use cases.
Observable Enrichment
The DomainTools Iris analyzer is built with the Investigate API which brings in Iris data for a domain, including Whois, Domain Risk Score, and artifacts associated with the domain like SSL, ASN info, etc.
While enriching the observables, we persist the enrichment data in observable reports within an incident. This enables users to review the enriched dataset conveniently including DomainTools Guided Pivots, to help further their investigations.
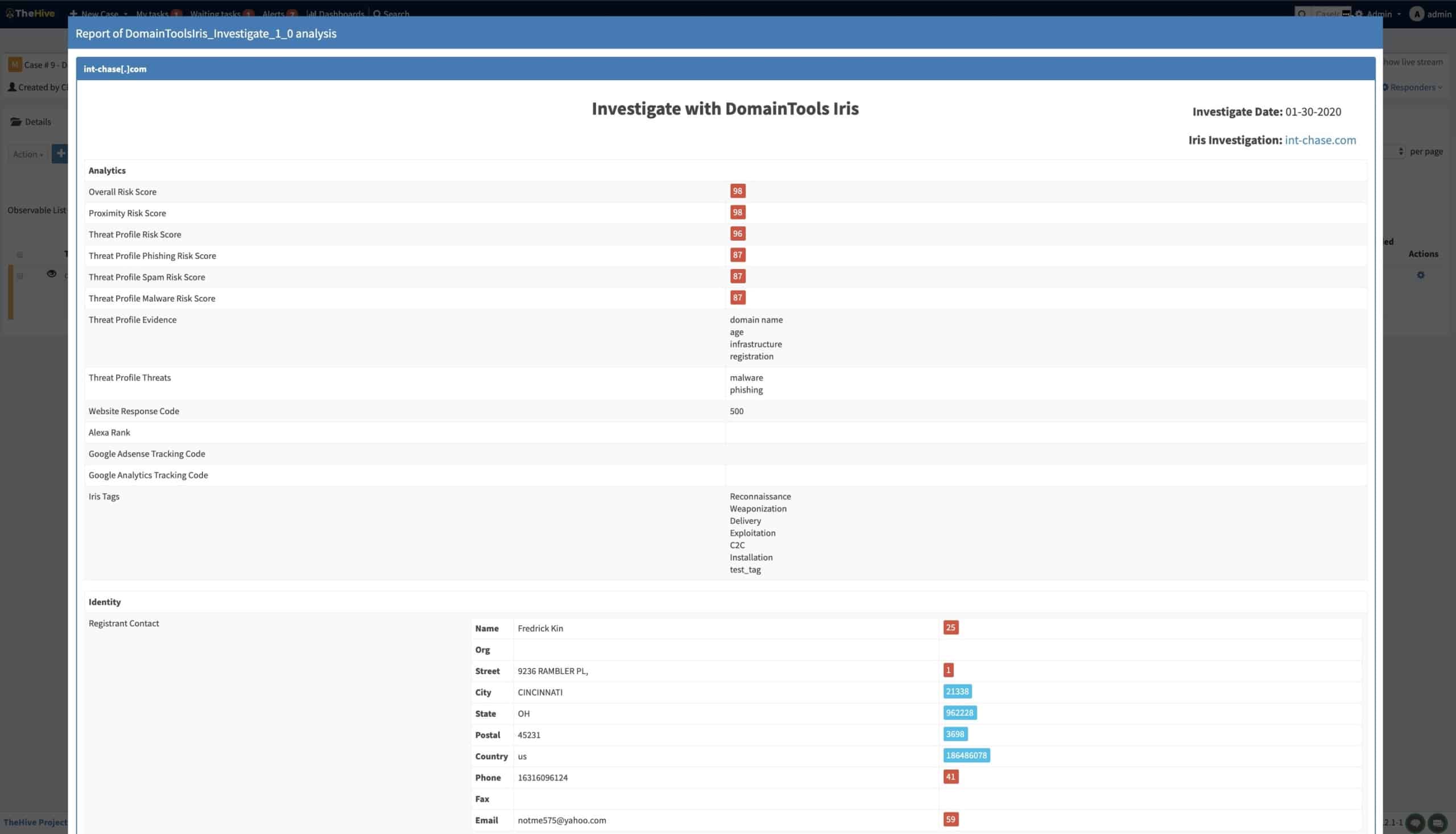
Artifacts with Guided Pivots below a threshold limit, configured by the organization, are visually highlighted for convenience. Users can add these artifacts as potential points of pivot/reversing.
This enables an analyst to investigate the incident without context switching across multiple tools. Further, the enrichment data inside of an incident forms a qualified tool for convenient reporting and reconciliation. And whenever an analyst feels the need to dive into DomainTools investigation platform, they can conveniently launch it from within the observable report, all without losing their context in the investigation.
Discover Connected Infrastructure
But what if just profiling the DNS artifact, does not provide you with adequate insight? If only you could lift up the curtain and look at what’s connected to the domain observable. Voila, DomainTools Iris pivot analyzer will allow TheHive users to achieve just that. With pivot action as an analyzer, users can pivot on any of the associated IPs, SSL hashes, and registrant email addresses and retrieve associated IOCs.
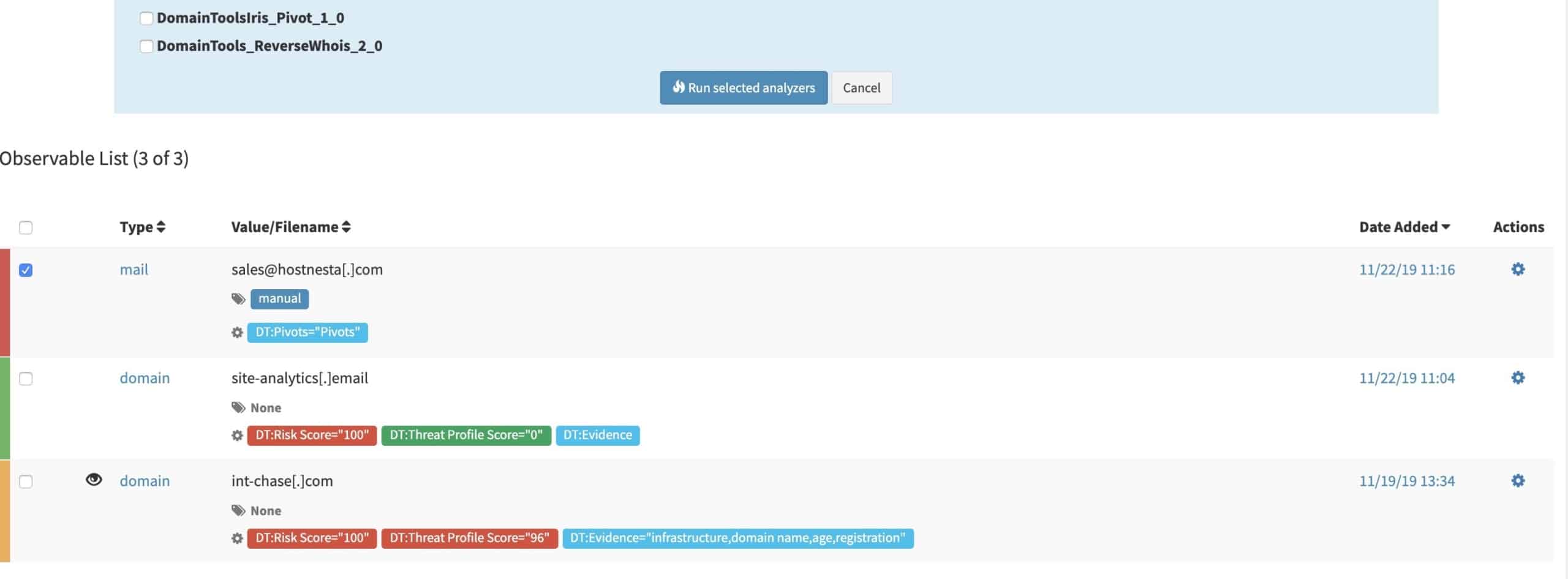
And if you are about to do a coin toss on which of the many attributes you should pivot on, you can save that for the jukebox. We bring in our proprietary Guided Pivots analytics, which will guide your investigation. Guided Pivot counts often create an investigation path on their own, even before you had decided to pivot.
Did I tell you we highlight (flag) the viable Guided Pivots for you already during observable enrichment?
Congratulations, you just discovered a completely new set of IOCs that would have otherwise gone undetected. Throw in some DomainTools analytics like Age, Domain Risk Score, etc. as filters and you have likely narrowed down a very target list of IOCs to be imported into the platform you use to consolidate intelligence and map forensics.
Now you may be thinking, this seems too easy to be true. And I say, you are welcome.
If you are a MISP user, you can also auto-create a case out of a MISP event by linking the two instances. It’s the good old open source community magic and all the investment members have made. If you need to see this in action, we will be happy to show you a functional demo and share our know-how so your team can get running quickly.
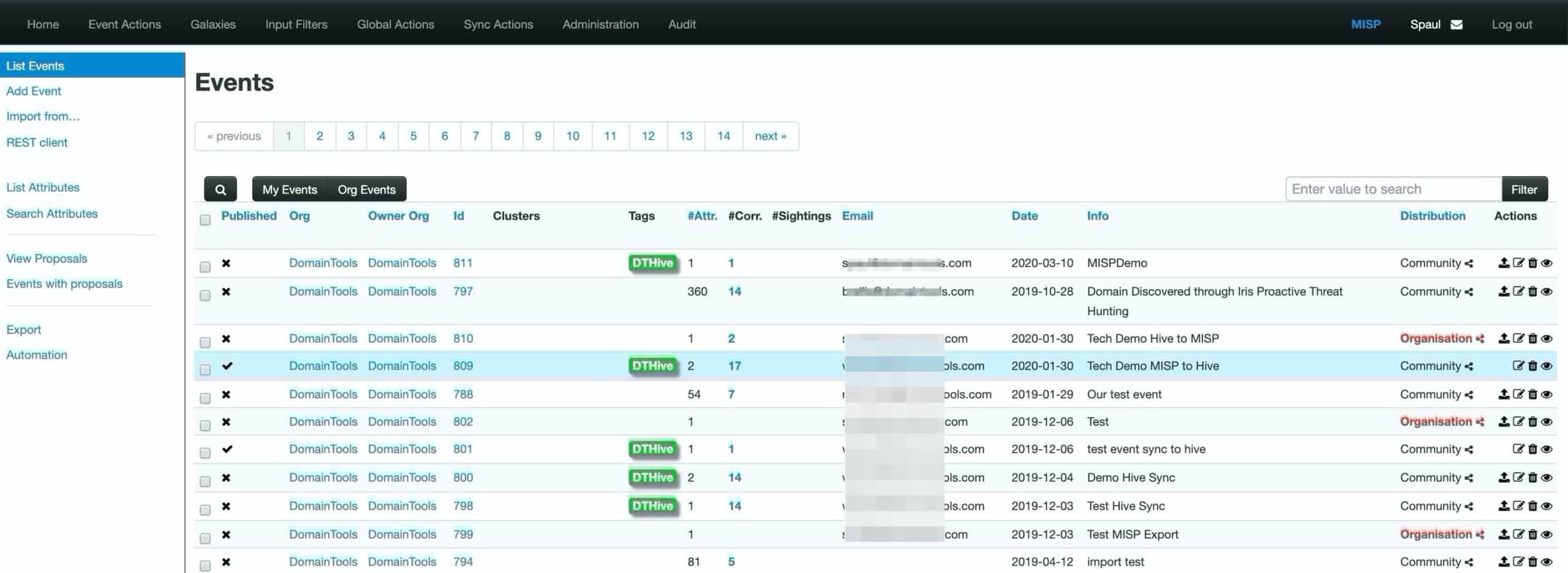
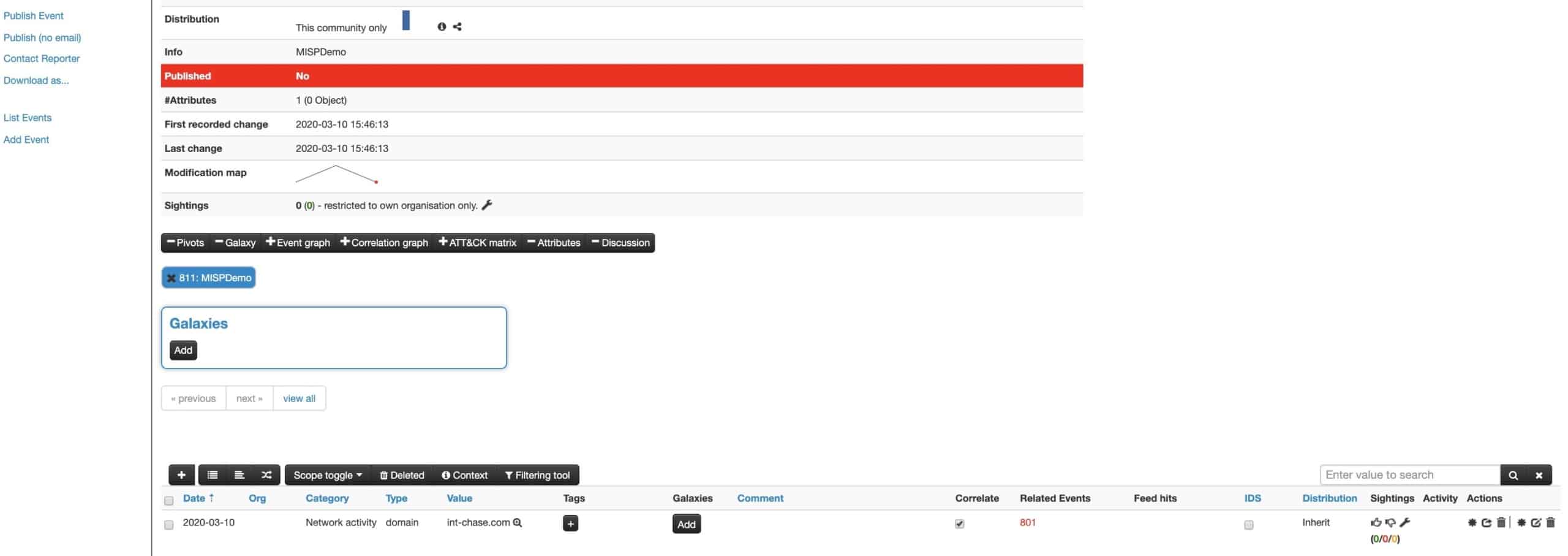
Fig: MISP events following Bi-directional sync with TheHive
For those who have not yet had a chance to play with TheHive or Cortex ecosystem, I would highly recommend it. If you desire enterprise support for the with TheHive and Cortex ecosystem, you can contact the founding team at StrangeBee.
For existing DomainTools Iris customers, the Iris APIs are all part of your platform access, so there is no excuse not to give it a try. Our analyzers are available for download from TheHive Github repo.
After all, it’s free and the most you may risk is a couple of hours on a lazy Spring afternoon.
With a bit more gravitas, yet grounded on our core philosophy, we continue to believe and democratized DNS threat investigation. The DomainTools Iris for TheHive integration proves incident response orchestration is not just possible within expensive commercial products. And, now we can leverage free and open source solutions when defending against cyber attacks. With MISP, TheHive, and Cortex integrated with DomainTools Domain and DNS infrastructure intelligence, we collectively can fend off the attacks at scale, and help make the internet a safer place.


