Coming up this week on Breaking Badness. Today we discuss: Cyber Warfare in Geopolitical Conflict, BEC you Later Alligator, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Cyber Warfare in Geopolitical Conflict
- There is obviously a ton of reporting on Eastern Europe. Our own government published intelligence on the Russian military to get ahead of the invasion.
- For the infosec community there is a lot of history here. In 2017, the notPetya “ransomware” variant saw Russian threat actors targeting Ukraine, which spilled over to western targets as well.
- In the latest phase (2/24), we saw denial of service (DoS) attacks on Ukraine. We’ve also seen HermeticWiper attacks that used a suspicious signing certificate to target Ukrainian interests with destructive malware.
- Anonymous has now attacked Russia, for whatever that is worth.
- Some of the unique challenges when it comes to consistent, and trusted intel in this situation is that it’s easy to publish screenshots, share to social media, and say it’s something that it’s not, so it’s difficult to navigate. You’ll see pictures of events, but it’s not always indicative of what’s actually happening or something is taken out of context. There’s just a lot of noise out there.
- It’s tricky to say how this cyber warfare will evolve. There’s the added impact of social media. Ukraine has deployed information warfare in an advantageous, perhaps unexpected way, but again how can you expect something like that? Third party groups are going hard on Russian targets. It remains to be seen how much will change. We’ll continue to sort through what’s real, what’s fake, what’s a nuisance, and so on. We’ve already seen so many norms shattered in such a short period of time.
- So far, we haven’t seen anything on the level of notPetya on the cyber front, but it’s really early on. It will take time for reactions, but we’ll see how things continue to evolve as the resistance digs in more.
- The Conti ransomware group initially released a statement in support of the Russian government, then one backing off a bit. There seems to be an internal struggle as their chat logs were released, exposing a ton of internal information on the group: payment wallets, infrastructure, operational planning, etc.
- Cyber warfare concerns Ukraine because this is literally life or death. From the IT side of things, so far the infrastructure that needs to be running is running. Elon Musk has seized the opportunity to deploy Starlink hardware to the Ukranians for added redundancy.
BEC you Later Alligator
- BEC (Business Email Compromise) in a nutshell are scams. They work through various ways of exploitation of email accounts to trick someone out of funds through various methods. Here are a few examples:
- Trying to convince someone an invoice was sent and needs to be paid
- False instructions from a “boss” to move money around accounts
- In recent years, the FBI has seen an increase in these scams. In 2021, they completed a report when they first mentioned BEC scams were on the rise. With more people working from home during the pandemic, threat actors are using the video call to their benefit.
- One example is like something out of a science fiction novel: a threat actor puts a still image of an organization’s CEO or CFO on the screen and provides instructions to employees indicating funds need to be moved around. Keep in mind, this is just the picture of a company’s leader, acting as if their camera isn’t working. They might even use voice alteration to further appear like the actual CEO or CFO, which treads into deep fake territory. For the FBI to report this, they’re doing a public service saying we need to be vigilant against it.
- There are ways to protect yourself from these kinds of threats, and really it’s all about cybersecurity 101. Ensure your email environment is secure and end users are educated on what to look out for. The fact is, everyone will click on something malicious at some point, but keeping your eyes on the basic security tactics is important.
- This uptick is no more concerning than anything else that’s currently happening out there. It’s really about the people component - ensuring end users are aware and educated on those basic techniques.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
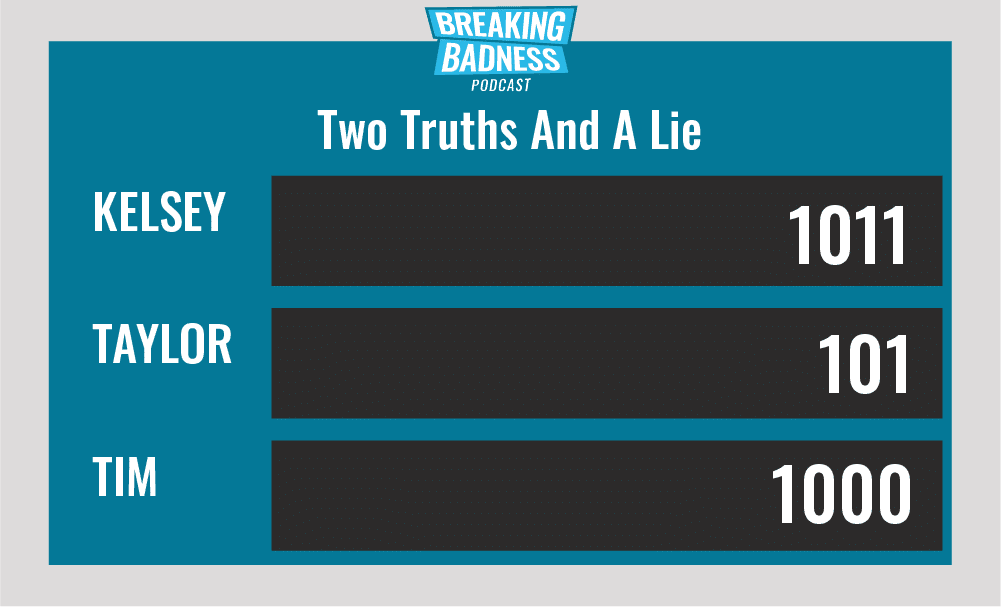
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Cyber Warfare in Geopolitical Conflict[Kevin]: 8/10 Hoodies[Taylor]: 10/10 Hoodies
BEC you Later Alligator[Kevin]: 3/10 Hoodies[Taylor]: 3.5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

