Coming up this week on Breaking Badness. Today we discuss: Welcome to HTM-Hell, Segmented Internet Reper-Russians, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Welcome to HTM-Hell
- Lazarus group hackers created a really convincing website and blog with other people’s research, then reached out to prominent security researchers asking for help on an 0-day they were working on. They would send them a malicious Visual Studio Code project or to a crafted site with a Chrome exploit, pop their box, then do Lazarus group-y things.
- So there was some confusion around how the Chrome exploit was working when Google’s Threat Analysis Group or TAG had first reported on it. Maybe the translation was a little dicey since the page was in Korean, but from what I’m understanding it sounds like the Chrome bug called a script which dumps a file which launches an exploit that works in IE which runs the next payload bit according to ENKI. That sort of daisy-chaining isn’t uncommon and would explain why Microsoft didn’t initially respond to ENKI’s submission of the bug to Microsoft’s bug program since it may just be Internet Exploder acting as it does.
- This attack wasn’t successful against ENKI researchers according to their reporting, but it was successful with some other research groups according to Google. The researchers at ENKI were able to intercept the MHT file that was the second stage of the exploit.
- So MHT is a bundled version of a website for viewing offline. It was a poor idea to begin with, has no solidified specification, and should be avoided like the plague. You can also see them as .EML files sometimes.
- From the sounds of it it’s the MHT format executing as expected. Just being a giant dumpster fire. I think in this case developers call that a feature not a bug
Segmented Internet Reper-Russians
- Reaching back a bit, if Dmitry Medvedev sounds familiar, it’s because he used to be the president of Russia. Now he’s the deputy chairman of Russia’s security council. He’s a relatively connected guy, in other words, and I think it’s fair to say that he has, maybe not as much influence as Putin, but still a fair bit, when it comes to Russia’s Internet.
- Russia probably can operate their segments of the Internet autonomously; after all, one of the hallmarks of TCP-IP, and the fundamental routing protocols, is their resilience, specifically to having nodes or segments become unavailable without warning. So it’s safe to say that their packets will keep flowing. Now, can we predict all of the possible nuances of what would happen if they actually did this? Like, is it certain that nowhere within their vast territory would there be any connectivity to the rest of the world? No way to know for sure.
- Now as far as what Medvedev said, in a certain sense this was very much like the posturing that we saw militarily throughout the Cold War—basically saying “we’re ready, we can do it any time, no problem, of course we wouldn’t just do it randomly,” etc etc.
- In Medvedev’s statement it sounds like Bartleby would prefer not to pull the plug so to speak. The actual quote, and this sort of ties together your last question and this one, was “Technologically, everything is ready for this. At the legislative level, too, all decisions have been made. But once again I emphasize: this is not easy, and I would really not want it.”
- If this whole scenario sounds sort of familiar, it could be because a couple of years ago there was a bunch of news about a test that Russia was preparing to do—a practice disconnection. WIRED ran a big story on it in February of 2019.
- I think a lot of that would depend on how it happened. There are huge numbers of unknowns. How long would they go offline? Would it be as a reaction to a specific event, or as a proactive move? What would happen to non-Russian traffic that goes through Russian infrastructure? There’s a huge Internet Exchange in Moscow, for example. What would be the means of enforcement for citizens who got around the blockade? I think it’s pretty hard to predict. As for what they’d gain, well, a certain degree of control, for sure. Possibly some safety against attacks from the outside, but how foolproof that would be is hard to speculate on. Really, there are a lot of unknowns to this story.
- So there are already some flavors of this, right? China has had its Great Firewall for years, and other authoritarian countries have dabbled in disconnecting too. They all will face the same challenges I just mentioned, though for smaller nations the scope of managing this kind of disconnection might be more manageable. It’s complex, because on the one hand, cutting off the free flow of information is dangerous to freedom and human rights. On the other hand, you’re also cutting off a lot of propaganda and hot garbage. The Internet does seem to be getting more Balkanized already, but it’s unlikely to become completely segmented. Some articles had a quote where someone compared Internet traffic to water—it will always find a gap to flow through. I think there’s a lot of truth in that.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
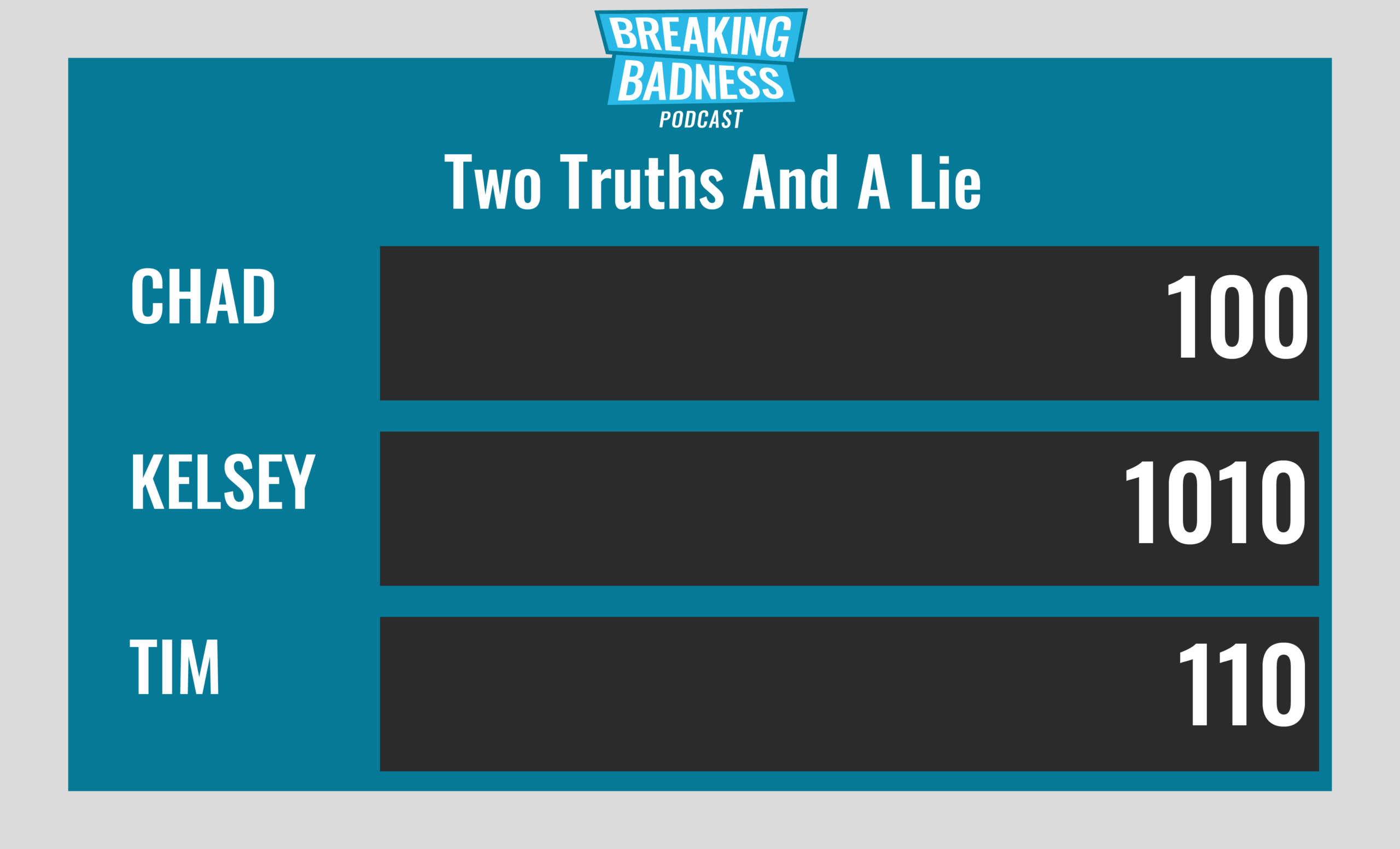
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Welcome to HTM-Hell[Chad]: 4/10 Hoodies[Tim]: 4/10 Hoodies
Segmented Internet Reper-Russians[Chad]: 2/10 Hoodies[Tim]: 2/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

