Coming up this week on Breaking Badness. Today we discuss: Nursery Nightmare - How a Baby Cam Company Got Its Toybox Raided, Gamaredux: New Activity From the Gamaredon Group, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Nursery Nightmare - How a Baby Cam Company Got Its Toybox Raided
- NurseryCam is an end to end surveillance-as-a-service provider offering CCTV and parental webcam solutions for daycares in the UK, along with web design services and access control solutions. They’ve been at this for quite some time, since 2002. They’re owned by Footfallcam ltd, which offers automated people-counting cameras to retail stores. Footfall made headlines earlier this year when it was discovered that they were shipping a rebadged Raspberry Pi with hardcoded admin credentials that also broadcasted an SSID whilst running SSH. When a researcher went public with this they filed a police report against them, that they then had to withdraw. So that’s great.
- In this instance the register was tipped off by a hacker that had obtained real names, usernames, passwords and email addresses for 12,000 NurseryCam users' accounts.
- There are a couple “incidents” at play here. One where Andrew Tierney (aka cybergibbons) discovered how easy it was to access the DVR systems and published a writeup and outlined the risks:
- Any given parent for a given nursery could login to the DVR and view any and all cameras.
- Because the password for the DVrs is common across multiple nurseries and is openly documented on the NurseryCam website, anyone on the internet with the IPv4 address for a nursery could potentially gain access to the DVR.
- Specifics on the data breach itself are not available, as for the DVR access we have a bit more to go on. The DVRs used by NurseryCam sit behind the firewall and the NurseryCam mobile app plus website used by parents allows them to view the cameras via port forwarding. In this process the username and password for the DVR are passed along and a direct connection is established. All parents connecting to a nursery are given the same username and password for the DVR. Once the username and password are given they are able to connect directly to the DVR itself and view all of the cameras managed there. The connection to the DVR is done over HTTP, meaning the usernames and passwords are passed in plaintext.
- NurseryCam isn’t sending the police after cybergibbons which is a step up from their response with FootfallCam. They shut down all of the NurseryCam services last week.
Gamaredux: New Activity From the Gamaredon Group
- Gamaredon is an interesting group. First off they are noisy which makes them really easy to follow. They aren’t subtle like some of the other APT groups and are real heavy-handed in their approach. They’ve been around since 2013 and have followed the same, general pro-Russian-ish activities since that time. And when I say noisy I mean we can see some thousand plus domains for this most recent bloom of work.
- Unlike most APT groups they don’t have a specific victim set. They target everyone and institutions one every continent. Much like honey badgers, they don’t care. Like literally everything under the sun they’ll go after. I think that’s what happens when you can operate like a cybercrime organization without impunity. They have about 4000 addresses of groups they won’t attack which seem to be organizations mostly in CIS countries or allied with Russian interests.
- They certainly operate like a cybercrime gang, but many loop them into an APT category. The non-specific victimology and pro-Russian activities has a lot of people believing that they are an initial information gathering and foothold group that then passes on any interesting access to a higher level group.
- They do have some decent chops. Little things like using malicious document templates that are large enough to evade some detection engines are interesting. I also think they must be somewhat skilled in infrastructure management since they keep up a huge amount of infrastructure behind these domains. Usually a few dozen will point to a single cloud hosting provider or VPS that’s running their first stage C2. So there has to be something decent there and they really don’t have a need for super good opsec if they’re Russia based right? They have to have some okay chops though, enough for initial intrusion. This may all be common tools written by a more sophisticated actor further up the chain if they really are an initial access group.
- They make use of Dynamic DNS providers quite a bit for their first stage using hopto and dyndns with common naming patterns that I would assume match targets like Tesla and what not. They also make use of VPS providers rather heavily with DigitalOcean being the latest round. There is also an interesting bit I noticed through looking at some crawls that have hit their infrastructure that their plain HTTP service doesn’t have a redirect to HTTPS which is a little interesting that their nginx config is that way—nginx being the web server I’ve seen on most of those crawls. The new activity is just the constant stream of their undeterred flood of work with the slight shift to DigitalOcean right now.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
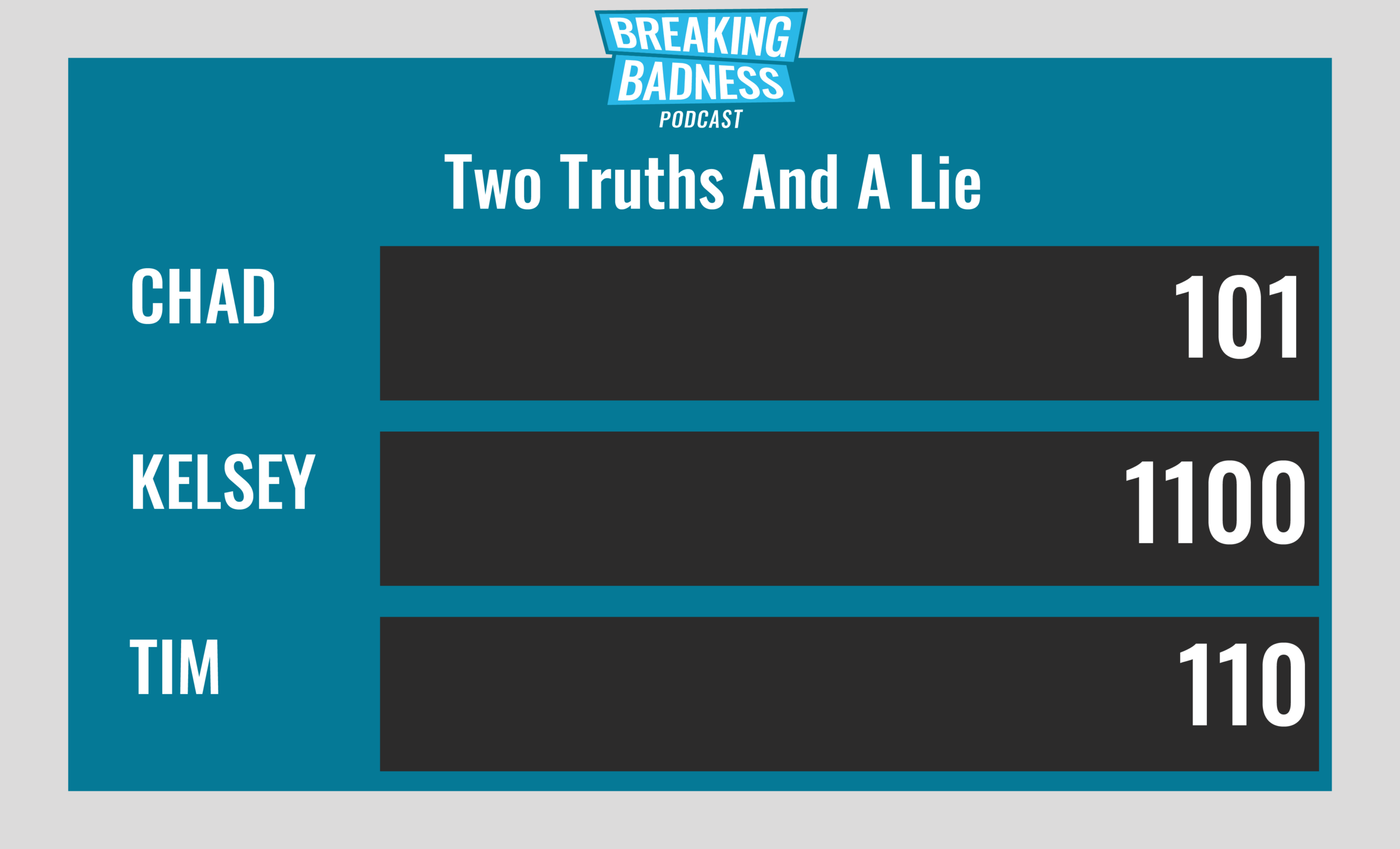
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Nursery Nightmare - How a Baby Cam Company Got Its Toybox Raided[Chad]: 1/10 Hoodies[Taylor]: 1.5/10 Hoodies
Gamaredux: New Activity From the Gamaredon Group[Chad]: 4.2 sleeves/10 Hoodies[Taylor]: 2 sleeves/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

