Coming up this week on Breaking Badness. Today we discuss: Anti-Piracy Site Malwarrrrrrr, Learning The RedFoxtrot, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Anti-Piracy Site Malwarrrrrrr
- This malware is one of those odd samples you come across now and again and shake your head, wondering what the author was really trying to accomplish and if you must be missing some follow-along stage or some hidden, packed element that activates under some super specific condition. In this case we’ve got a piece of malware that on execution adds a bunch of entries to the hosts file. These entries are designed to block access to common torrent websites. On top of that it reaches out to a typosquatting domain and grabs an additional executable. Perhaps that’s where the magic happens and what Brandt was missing. Happens often enough, can’t find the follow along sample.
- The actor used both bittorrent and discord to distribute the malware, masquerading as cracked game files or other cracked software. Pretty much run of the mill, but effective. People love downloading cracked software filled with malware. Common internet past time.
- The HOSTS file is something that’s super easy to spot, doesn’t survive in any persistent mechanism, and in some cases now is entirely ignored. With the advent of DNS-over-HTTPS (DoH), a lot of applications now ignore system-level settings and go right to the DoH DNS server.
- Discord has been on the rise as a malware CDN for the last several years. They will host files and let you call out to them from Discord chat groups. Just another simple technique for avoiding having to run your own infrastructure and get caught.
- So outside of the HOSTS file modification the malware downloads an additional payload from that typosquatting domain that mimics 1fichier, the cloud storage provider, then sends the name of the executable that was used to install the malware in a HTTP request to that domain as well. That’s pretty much it unless there is something unseen here in the random text blobs that it’s packed with, but Brandt didn’t mention finding anything additional there. Interestingly, it is packed with the same packer as Qbot by the way, a commodity malware that often leads to ransomware infections. Likely unrelated and just bought on some forum though.
- To help ensure you are not affected, you could check your hosts file and delete the entries. You’d want to so you can continue downloading torrents of course. Linux install ISOs. And seed them for the betterment of the open source community.
Learning The RedFoxtrot
- This Military Unit Cover Department is for a Technical Reconnaissance Bureau within the PLA’s Strategic Support Force Network Systems Department. Clear as mud? Thought so. Anyway, opsec became slopsec and bob’s your uncle, so now we’ve got a street address for 69010 and we can order pallets and pallets of Justin Bieber CDs and scratch-n-dent clearance-priced colostomy bags to their department just to troll ‘em, you know? But so anyway all of this leads Insikt to the conclusion that this is who RedFoxtrot is.
- RedFoxtrot has historically targeted government, defense, and telecoms organizations, and historically their victimology is largely central Asian: Pakistan, India, Afghanistan, Kazakhstan. They hit some aerospace and defense orgs in India within the last few months, among others.
- The Insikt Group was able to make these connections due to a specific individual, who leaked some information that connected back to what was already known to be the physical address of Unit 69010 in Urumqi, xinjiang. I’ll go ahead and direct-quote the report here: “Insikt Group is not publicly disclosing the identity of this individual; however, an extensive online presence provided corroborating evidence indicating that this individual is located in Ürümqi, has an interest in hacking, and also has a suspected historical affiliation with the PLA’s former Communications Command Academy located in Wuhan.” Moral of the story: while it’s always DNS, it’s also always Layer 8 that gets you into trouble.
- This group doesn’t appear to employ any particularly novel TTPs. To the extent that they are successful, they are doing it the “small ball” way—grinding out occasional but steady singles and doubles, rather than spectacular home runs. In other words, they use fairly commodity-level malware, they use infrastructure that does a lot of the usual spoofing of legit resources including Adobe, Google, McAfee, etc. I found this story interesting because of the good work that Insikt did in tying together these activity clusters. If you’re not in one of the targeted regions or industries, there’s not necessarily a lot that you probably need to be concerned about regarding this particular group. It does show that there are some Achilles heels for even the most sophisticated actor groups, including opsec fails, and the reliance on infrastructure that can be identified and monitored.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
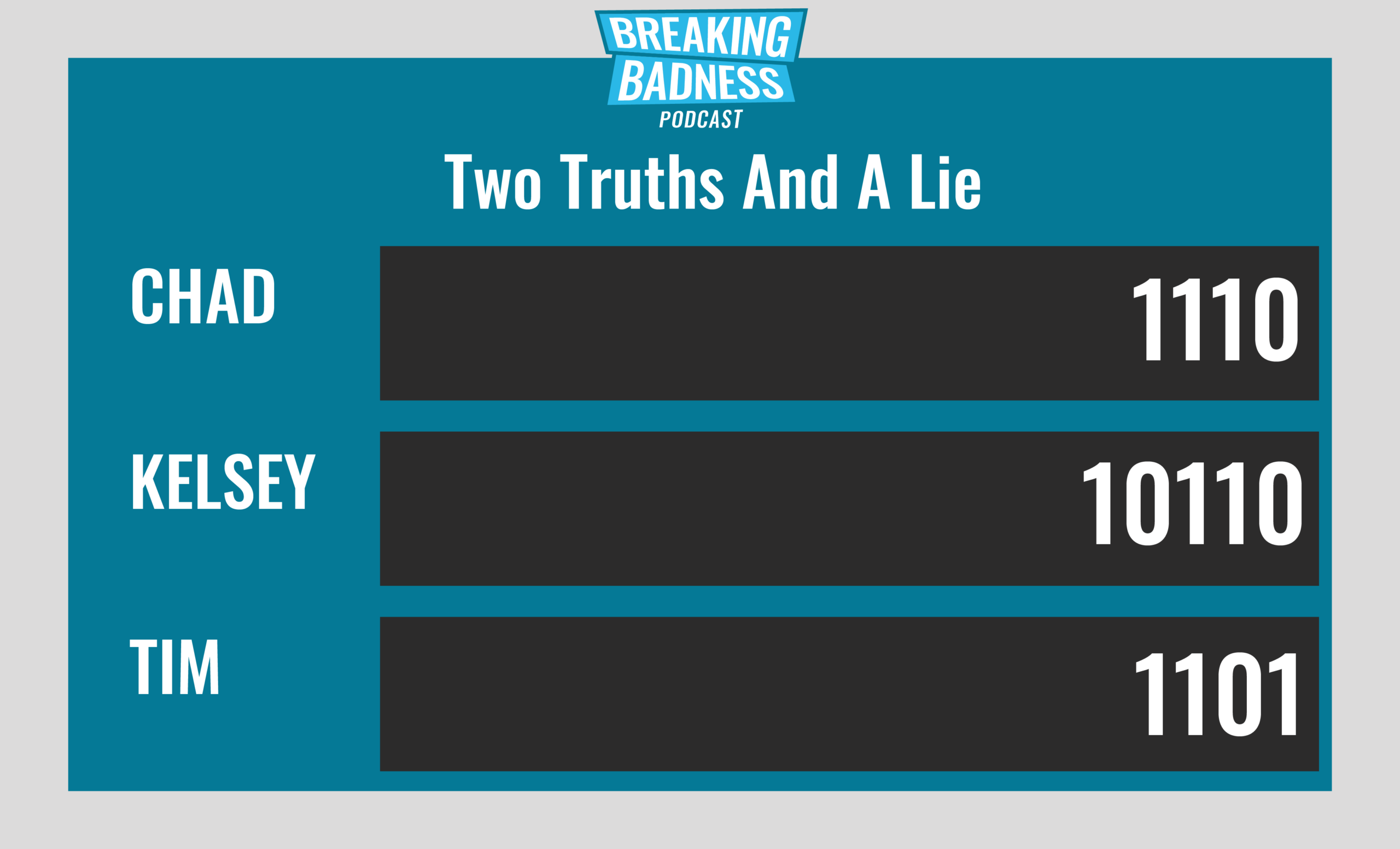
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Anti-Piracy Site Malwarrrrrrr[Chad]: 3/10 Hoodies[Tim]: 1/10 Hoodies
Learning The RedFoxtrot[Chad]: 1/10 Hoodies[Tim]: 1/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

