Coming up this week on Breaking Badness. Today we discuss: I Spy With My Little Eye Something Concerning, Hackers Go for the Gold Meddle, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
I Spy With My Little Eye Something Concerning
- The NSO Group is an Israeli offensive toolkit company focusing primarily on mobile OS backdoor development. They sell Apple and Android backdoors to government entities ostensibly for legitimate law enforcement purposes. They’ve been linked to Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Togo, and the United Arab Emirates. Pegasus represents a significant step up in surveillance capabilities for most of these customers.
- Their main product is their pegasus spyware, which allows for 1-click to zero-click exploitation of a target device, depending on what bugs are being abused. This means they spend a lot on the R&D required to keep it one step ahead of Apple and Android OS development. They claim to work towards legitimate law enforcement purposes: “The people that are not criminals, not the Bin Ladens of the world—there’s nothing to be afraid of. <emThey can absolutely trust the security and privacy of their Google and Apple devices.” -Shalev Hulio, NSO Group CEO (and the ‘S’ in NSO)
- The Mexican government was an early adopter for them and they claim that the operation to take down notorious drug lord El Chapo was assisted by Pegasus.
- There have been several claims of abuse by journalists and political dissenter/human rights groups, including targeting of their family members via SMS phishing links. They were also accused of supplying Saudia Arabia with the necessary tools to hack a ex-ceo and current rich astronaut, though no evidence has substantiated these claims.
- The Amnesty International forensic report includes a number of suspected malware dropper and command and control domains, along with their supporting hosting infrastructure. In addition to this they included iOS logs and processes involved with several exploit chains over the last few years. In addition to this a collection of journalists and publications worked together on The Pegasus Project, covering developments in NSO’s capabilities and a set of 50000 phone numbers thought to be targets of NSO’s customers (this is in dispute). This list includes several current and former heads of state, as well as prominent dissidents and journalists.
- “Amnesty International’s Security Lab has performed in-depth forensic analysis of numerous mobile devices from human rights defenders (HRDs) and journalists around the world. This research has uncovered widespread, persistent and ongoing unlawful surveillance and human rights abuses perpetrated using NSO Group’s Pegasus spyware.”
- Pegasus is tricky to catch and it isn’t memory-resident, meaning a reboot kicks it off the device. They had to rely on forensic analysis via iOS logs of some of the target phones from the aforementioned list.
- The exploit chains they cover give forensics folks something to look for in iOS logs. Primarily processes and suspected malware domains. As for recommendations, I’d say if you have this in your threat model regular iOS reboots may make you feel better and all the usual advice around avoiding phishy links apply.
- Taking it at face value, it shows that pegasus is being used by NSO’s customers at scale in their surveillance efforts. And given that the NSO group reported EBITDA earnings of $120 million on $250 million in sales for 2020 I’d say they aren’t going anywhere anytime soon.
Hackers Go for the Gold Meddle
- I may be wrong about this, but this is the first time I can recall a warning about broadcast hijacking going out ahead of time. Certainly there have been some notable broadcast hijacks in the past—Max Headroom, I’m looking at you—but for it to be anticipated and warned about like this, says a couple of things; a) there’s some credible evidence about it, and an assumption that the possible hijackers are highly capable; and b) that there are vulnerabilities in the production chain that are ripe for exploitation. Because if you read the reporting, it sounds like they are all saying it is inevitable.
- Our listeners might recall the malware called Olympic Destroyer that disrupted the opening ceremonies, and other parts of, the 2018 PyeongChang winter games. That one was attributed to the Sandworm gang out of Russia, and it had the official Olympics website offline for around half a day, which disrupted some of the TV feeds and prevented ticket holders from being able to print their tickets. And more generally, cyber attacks on the Olympics go back to at least the ancient Roman games, when an APT group out of Thrace took down the Roman Forum’s IRC server (you didn’t realize how old IRC was, did you?). I jest, of course. But back at least as far as the 2004 games in Greece it was an issue.
- The warning had a couple of different aspects that it highlighted, including as I mentioned possible disruptions of the streaming - which has higher stakes this year than in past years, since it’s going to be 100% online spectating this time. (The organizers had originally said that 10,000 Japanese fans would be allowed in person, but then COVID got worse again and they canceled that.) So your avenues for disruption are in some ways narrower - you can’t prevent folks from printing out tickets, for example, or go after personal data at POS kiosks at the games and stuff like that. This is why it’s all about the feeds.
- Both Russia and China have bones to pick related to the Olympics, for different reasons. For China it’s because there has been escalating tension with Japan in general, so this might be one of the ways in which they try to strike a blow. For Russia, they’ve been in a snit with the IOC (not, in this case, indicator of compromise OR indicator over cocktails, but the international Olympic committee) because of the ban they threw on Russian athletes for alleged doping. So you’ve got a couple of motivated, well-resourced adversaries here.
- The best case scenario is that no news is good news one, of course. We just get to watch Simone Biles do her thing without disruption (and I mean is there really much else that anyone’s going to care about?). Certainly the prep for keeping things secure has been in the works for many years. With all things cyber, the absolute worst case scenario is where human life is at risk, but I’m not aware of specific critical infrastructure risks for the Olympics. So I think the more realistic worst case scenario is a prolonged disruption of the live feeds, especially during Simone’s floor routine. And I guess if there were a disruption that was combined with some propaganda, that wouldn’t be nice. Some folks are speculating that one way in which the disruption could occur would be if the content were held in some kind of extortionary way, but there is a word that we are not going to breathe on this episode, so I’ll leave that to the audience’s imagination. Then I will recommend quickly shifting your focus to your favorite cute-animal-cam.
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
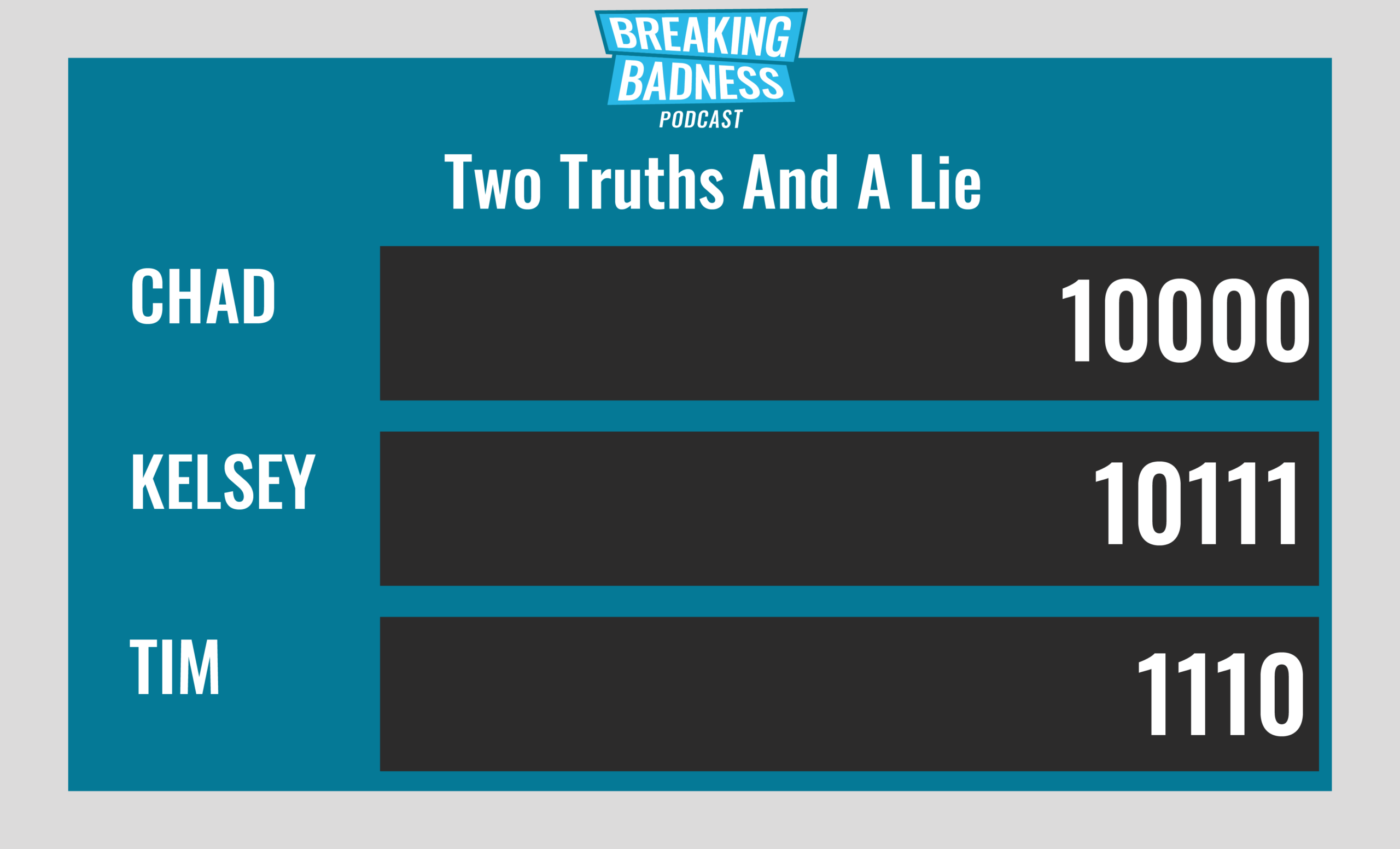
Current Scoreboard
This Week’s Hoodie/Goodie Scale
I Spy With My Little Eye Something Concerning[Taylor]: 7/10 Hoodies[Tim]: 8/10 Hoodies
Hackers Go for the Gold Meddle[Taylor]: 2/10 Hoodies[Tim]: 2/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

