Implementing the Continuous Security Model

In honor of cyber awareness month, the DomainTools team felt it important to share an effective approach when it comes to sustaining and maintaining a healthy security posture. As Lex Luthor once said, “the man of tomorrow is forged by his battles today.” This mentality is easily likened to a robust approach to continuous security, as past, present, and future all figure in our capacity to identify, attribute, and block cyber attacks.

Before running through techniques that employ data from the past, present, and future in a continuous security model, it’s necessary to understand where and what types of data can fuel your investigations. The good news is the majority of the data you need to apply a continuous security model can be obtained from the kinds of open source intelligence (or OSINT) that fills the DomainTools databases (as well as other sources). Examples of the OSINT data include (but are not limited to):
- Whois records
- DNS records
- Dig results
- MX records
- Search engine results
- Malware analysis
Many of these pieces of data are available online at no cost, but if you’re looking to scale your OSINT security strategy, it is likely you will invest in systems that will allow you to automate collection and querying of data. These commercial solutions allow you to scale your efforts quickly and efficiently.
OSINT in Continuous Security
In a continuous security-style cyber strategy you will need to:
- Actively detect initial indicators and expand to connected assets
- Return to past data and review archives for earlier occurrences of indicators from expanded threat networks
- Proactively monitor cyber squatters or other threat actors and block new threat infrastructure
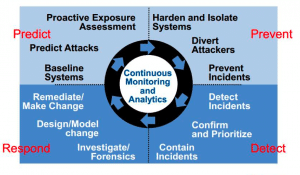
Below is a quick example from a well-known APT and the steps your team could take in a continuous security model:
- FireEye’s excellent APT 28 report states: “We have seen APT28 register at least two domains mimicking the domains of legitimate organizations in the Caucasus…One APT28 domain imitated a key Chechen-focused news website, while the other appeared to target members of the Armenian military by hosting a fake login page.” (Page 11). The team quickly detected the present threat.
- Using Whois lookups, passive DNS, and commercial providers, the team quickly identified there was an opportunity to expand on the data from the two domains mentioned above and understand the extent of the threat based on past data. In this situation, there were 17 other sites hosted on the same IP address, 54.255.143[.]112, and the domain names had a clear focus on Google, Yahoo and Microsoft branded web-pages. As a result of pivoting on said 17 domains, the team had 17 targets to search for (instead of 2) in old logs to spot earlier incursions or to block related malicious attacks.
- Finally, the data collected from OSINT sources can be used to block or anticipate future attacks, by either a) blocking this IP address outright, or b) monitoring the IP and blocking new domains that appear on it.
We have obviously condensed a lot of activity into a bite sized chunk here! In summary, attributing attacks or conducting adversary analysis is a valuable exercise that allows you to use a healthy mix of threat intelligence data and a continuous security posture in your efforts to understand present and past risks or incursions, and ultimately to prevent and block future attacks.
Be safe out there!

