The Layman’s Guide to Online Privacy and Anonymity

Recently, privacy advocates were dealt a swift blow, with the passing of S.J.Res 34. This will strip regulatory power from the Federal Communications Commission (FCC) and give it to the Federal Trade Commission (FTC). This resolution will also prevent the FCC from making any rules protecting Internet privacy. In addition, the resolution’s passing now gives Internet Service Providers (ISPs) the ability to collect, store and sell your browsing history, app usage data, and location data. All of this can now be done without a user’s consent.
In this blog, I break down the differences between anonymity and privacy. I will also look at Virtual Private Networks (VPNs) and the problems they solve, and problems they inherit. And finally, I will give recommendations to protect your privacy and anonymity online.
Anonymity vs. Privacy
To properly understand what steps you can take to protect yourself, you first need to understand the difference between privacy and anonymity.
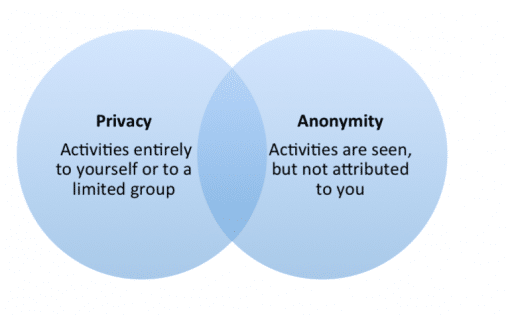
Privacy
is the equivalent of speaking to a close friend in a room with the door shut. I don’t necessarily have something to hide, I just want to keep the conversation private.
Anonymity
Anonymity is the equivalent of riding on a crowded bus. You have no privacy, but no one on the bus knows who you are.
Almost every service that operates on the Internet will track some sort of data. It could be IPs connecting to a web server, or it could be a Bitcoin wallet, but there will be data somewhere about that transaction. In the instances where the data trail allows for direct attribution, there are measures an individual can take to better protect their privacy and anonymity if they care to do so.
While there is no single solution to the privacy or anonymity issues, one of the most popular tools for privacy protection is the VPN.. Security and privacy advocates have been using VPNs for years, so we thought it might be useful to take a closer look at VPNs and their use cases..
VPNs and Use Cases
To fully understand VPNs, you first must understand what they do. A VPN masks your physical location and IP address, and also encrypts all of the data between you and the VPN server. Ultimately, the website you are visiting doesn’t know that you’re the originating point for the connection, as all the website logs see is connection from a VPN egress IP.
VPNs are commonly used in a number of ways. Most uses fall in the six categories below. Note that I am not endorsing using VPNs in ways that are illegal or that may circumvent the Terms of Service of any internet content or service provider:
- Public User: This person may be using a VPN for protection while browsing the internet at a coffee shop, or some other public wifi location. Their motivation is mostly to keep their information secure when using a public wifi network where multiple people are connected.
- Privacy Advocate: This person seeks privacy because of personal belief. They are default VPN users because they value privacy at all times.
- Traveler: Someone traveling for work often relies on the authentication and encryption of the VPN to allow for a secure connection to a trusted corporate network. A traveler also may want to watch location-restricted services. A VPN will enable them to connect to their native country, allowing them to view this regionally available content.
- Torrenter: This person likely purchases a VPN to use when downloading video, music, and other content that could be copyright protected. These users are trying to stay private to prevent prying eyes from seeing what they’re downloading, from where, etc.
- Journalist: Journalists will often use VPNs to protect their traffic when reporting from dangerous locations or regions that have content filtering enabled.
- Criminal: This person’s activity is criminal in nature. They may be connecting to the “deep web” to enact illegal or nefarious activity, and want to avoid law enforcement.
The Problem with VPN Providers
With VPN providers, you have to inherently trust that they are not collecting or storing your logs. If you are connecting to a VPN provider, you are in theory giving them access to your browsing history, since they control the connection your connection to the internet. Also, you have no verifiable proof they are not logging your traffic or connections. Using a VPN is effectively a Catch 22. You’re putting inherent trust in the VPN provider versus putting your trust in the hands of the ISP.
In addition to changing your individual trust model, some VPN providers are known to have security issues. In one instance, several providers have had their secret keys known and shared. This is a flaw in the fundamental concept of a VPN because this connects all of the VPN’s users using a single pre-shared key, which allows for possible decryption of traffic.
Privacy and Anonymity Recommendations
As mentioned earlier in this blog, there is not a single way to solve anonymity or privacy concerns in the digital age. However, there are several pragmatic recommendations I can make to help safeguard your privacy and preserve anonymity, should that be a priority that is important to you as an individual.
- To bypass some of the VPN issues we’ve talked about, use your own personally owned and created VPN. This keeps the trust of your data in your hands. This requires paying monthly fees since you will likely be using a cloud provider like Amazon AWS, Linode, or Digital Ocean. To help aid in the process of deploying your own VPN, use something like Streisand or Algo.
- Two-factor auth EVERYTHING possible. While this may not help with ISPs selling your browsing history, it can help keep your privacy intact, as it prevents unauthorized access.
- Use Tor where possible. On your Apple device, use the Onion Browser. On an android device, use something like Orfox. For Windows and OSX, use the Tor Browser.
- If you use a commercial VPN provider, use one that proves they are having external audits performed like the provider Cloak.
- Use DuckDuckGo as your search engine of choice. DuckDuckGo is both a browser extension and a search engine. Based on DuckDuckGo’s website, they don’t store your information, making it more difficult for advertisers to specifically target you.
- If you’re using Chrome/Firefox, use incognito or private browsing mode. While incognito mode will not prevent your ISP from knowing what sites were visited, it will help hide your browsing history from your machine. Also note it helps protect your privacy from the website you are visiting as well.
- Install and use the browser extension HTTPS Everywhere. This extension encrypts your communications with many major websites, forcing HTTPS to be used, therefore making your browsing more secure. Sites using HTTPS will at least limit what the ISP can see from your browsing This includes what domain you visited, but not necessarily the pages or subdomains on that domain.)
- Be wary of free VPN providers. Running a VPN service costs money. You have to ultimately ask yourself, “How are they making money to provide this VPN service?”
- Use a browser extension like Privacy Badger or Ghostery. Both browser extensions detect and block the ability for advertiser tracking.
Conclusion
A general concern about privacy or anonymity may no longer be sufficient. The responsibility is no longer shouldered by ISPs or governments, and for better or worse, falls to the individual internet user. In addition to paying close attention to new legislation and what it entails, there are certain tools and practices that you may consider adopting. Hopefully this blog offered some useful guidance on this topic and will help enable you to protect yourself in this continually changing digital world.

