The Burden of Spoof: The Ongoing Investigation of Walmartcareers[.]us

NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
15 days ago, our phishing detection solution PhishEye picked up multiple domains spoofing the term “Walmart”. The one that caught my eye was walmartcareers[.]us. When I decided to export the results from the July 25, 2019 PhishEye report, into Iris (our flagship investigative tool – which to be frank is pretty awesome) the investigation BLEW UP. So, in this blog post, I would like to share the current status of the investigation, as well as next steps in my research methodology. My intention is to use this blog post as a one-stop-shop (so to speak) for any developments or updates in the coming months. Also, for the sake of transparency, I want to note that this may or may not lead to a groundbreaking campaign. Additionally, like most folks that are researching, I often find it challenging to remain objective throughout the investigative process which can be difficult when we feel we are onto something cool.
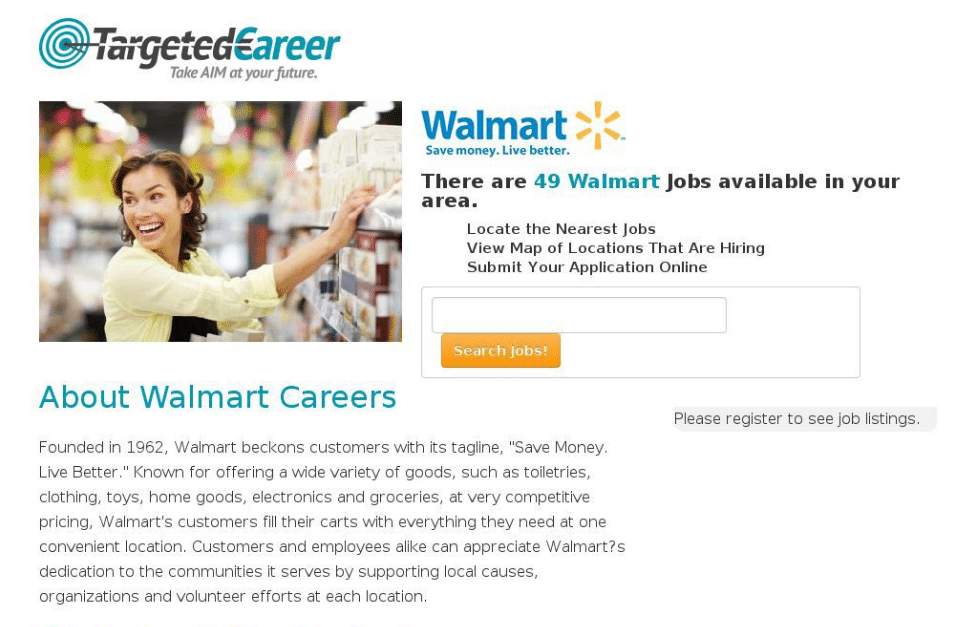
So, here is what I have found thus far, starting with the monitored PhishEye term, “Walmart”. On July 25, walmartcareers[.]us was flagged in my email in the early hours of the morning. This allowed me to look at all of my monitored terms for the day and assess which domains may be the most fruitful to investigate, which is an ideal start to any day.
When I looked into the domain walmartcareers[.]us, here are a few things that caught my eye from a simple pivot into Iris:
- Domain Risk Score of 96 – up from the original flag of 63. For context, domains scored at 100 are on industry blocklists, and our spidey senses start tingling around a score of 70+
- 4 Guided Pivots which are indicative of close connections between domains
- Email Address
- Name
- Phone number
- Registrant details
- Create date of July 22
- Nothing odd about the expiration date which I usually look at just as a quick indicator if the domain needs some more digging
- Registrant details are pointing to an address in Pakistan
- IP Country Code is US
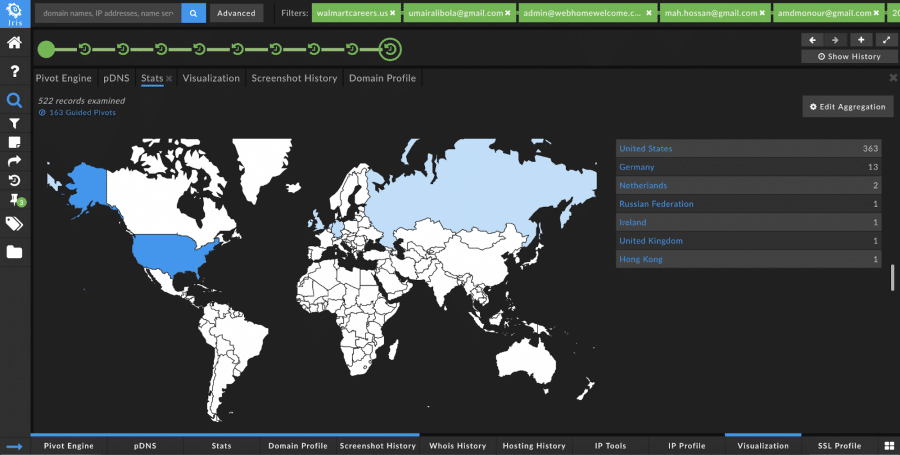
From the Guided Pivot on the email address, umairalibola@gmail[.]com, 184 domains shared this value with an average Domain Risk Score of 97 and an average age of 190 days. When unpacking these additional domains, it appeared to lead to a much larger campaign that is not only spoofing career sites but more significantly spoofing dating and movie/TV sites.
Of the 540+ identified domains in the campaign, only 181 have appeared on industry blocklists. The others were given average risk scores of 93 which indicates that at this point in time they seem to be doing some pretty shady stuff.
A majority of the IP country codes are in the United States, even though registrant details show an address in Pakistan:
Examples of other spoofed sites in the campaign
cashgiftcards[.]us
Still active – not on an industry blocklist (161 days old)
captainmarvelmovie[.]us
On an industry blocklist (209 days old)
mcdonaldcareer[.]us
On an industry blocklist (17 days old)
DomainTools Iris Visualization of online dating sites in the campaign
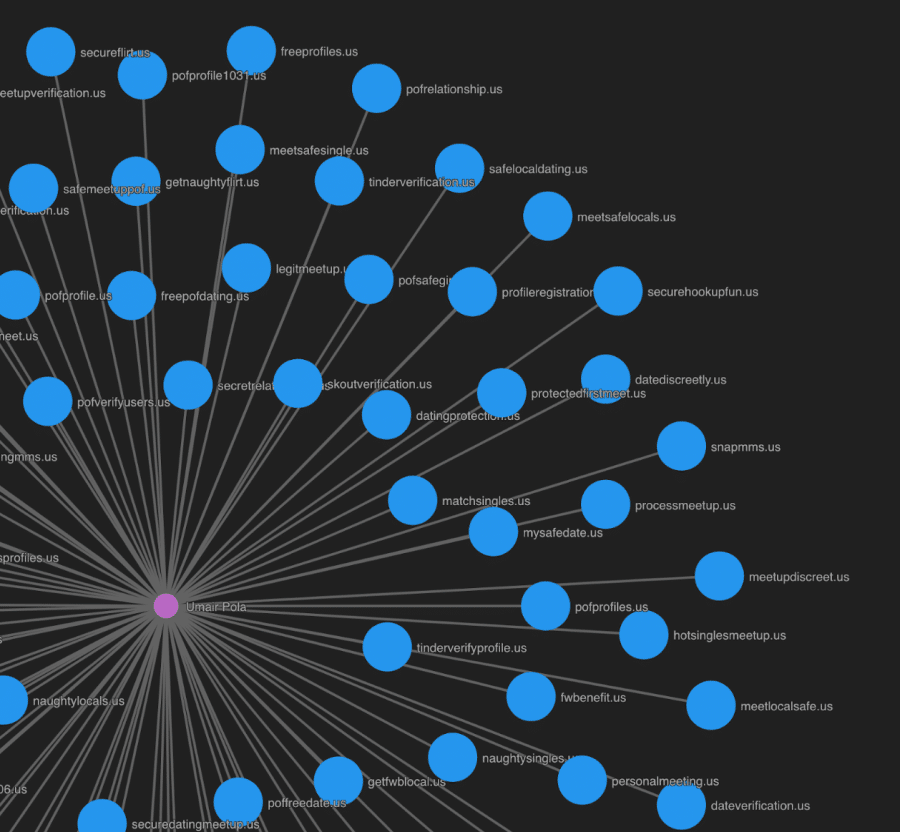
As we continue to unearth the intent of this campaign and potentially the actor/group behind it, we want to also take the time to make some recommendations.
For organizations
- Take steps to surface domains that are attempting to spoof your brand. A vast majority of the domains associated with this campaign are not yet on industry blocklists, so taking a proactive strategy of potentially catching malicious activity before it affects your customer base can be crucial.
- Examine your current takedown process and see if there are ways to expedite it by minutes/days/hours.
- Also, evaluate the cost of the potential brand damage that would result if a campaign of this type was successful in harming your reputation or impacting your customer base.
For consumers
- A good rule of thumb is to always verify a site’s legitimacy by checking the URL to ensure nothing looks suspicious before submitting credentials (username/password), credit card information, PII (personally identifiable information such as first name, last name, address and social security number), etc.
- Remember that if a deal seems too good to be true, it probably is.
- Don’t be afraid to verify by asking around, going to local resources, or finding a friend in InfoSec that can do some digging for you.
Disclaimer
We are still in the process of researching this campaign. For ongoing updates, please continue to visit this blog post and we will update it as we uncover or don’t uncover more.
Also, if you are attending Black Hat USA this week, stop by the DomainTools booth (#1404) and I will be walking through the investigation at 4:30 p.m. PDT on Thursday, August 8.

