Post-GDPR Security Investigations Part 3

Part III: Intelligence Resources
Welcome back to our blog series on security investigations in a post-GDPR world. In the past two posts Security Researcher, Emily Hacker, focused on conducting investigations and making non registrant-based connections. In this post, I’ll focus on OSINT-based methodologies, and information sharing.
Open Source Intelligence (OSINT) Resources
Open source tools and methods have always been important to researchers, and many of these routes were not impacted by GDPR at all. Social media platforms like Twitter, vendor reports, indicator sharing platforms, phishing feeds, and tools posted to GitHub are just a few of the many ways that intelligence analysts can continue investigations into incidents.
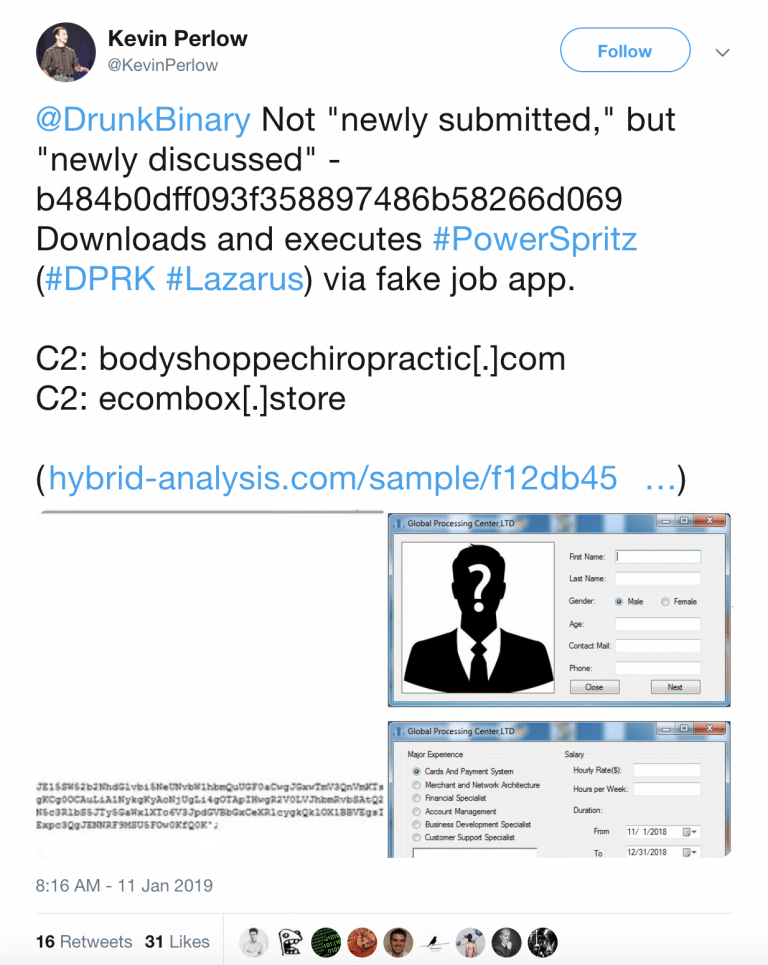
Twitter is an industry favorite for discussing current security trends and is a hotbed of activity. Security researchers will routinely post otherwise undocumented IOCs and investigation findings, so it’s usually a worthwhile endeavor to search Twitter for IOCs related to your current case. Depending on the sensitivity of your investigation you may even consider asking the community for any information they may have.
Well-known vendors, government resources (US-CERT), and the SANS Internet Storm Center (ISC) are continuously keeping up with the latest threats and do a fine job posting analyses in a timely manner. While your investigation may not currently be attributed to any larger campaigns it’s definitely worth checking recent industry reports for similar behavior or indicators.
Malware analysis services such as VirusTotal, Malwr, and Hybrid Analysis are a treasure trove of community-sourced data. These reports often contain community commentary attempting to enrich the automated analysis already provided. Keep in mind you don’t need to search these platforms with only a file hash, but can search on IP addresses and domains as well. VirusTotal in particular is known to have plenty of friendly bot accounts whose sole purpose is to tag uploaded files with enrichments.

When investigating a domain it’s important to check if it has a digital certificate, as the data they contain may allow you to link an actors infrastructure together (as seen above in “Non-Registrant Based Connections”). Sites like Censys and crt.sh are valuable resources for certificate information. Certificates may help provide some details for linking actor assets, as they may use the same information in separate places.
There’s such an array of OSINT tools out there it would be an intensive effort to try and cover them all, but resources like the OSINT Framework and the Awesome OSINT list on Github are fantastic jumping off points for investigations.
Information Sharing
One of the most important ways that cyber security professionals should be getting information is by involvement in various information sharing groups and the usage of Threat Intelligence Platforms. By actively participating in these groups, researchers can share and receive valuable intelligence that might otherwise be unavailable to them. Private-sector groups like ISACs, government groups like Infragard, and member-operated sharing groups are all valuable sources of information.
While the first two categories of groups are easy to find and join, the category of small member-operated sharing groups is purposefully more hidden. The best way to identify these types of groups is by networking – go to conferences, trainings, and meetups to find out what groups may be beneficial to join.
On a technical level most of these relationships involve STIX/TAXII feeds and/or Threat Intelligence Platforms such as MISP and the Alienvault Open Threat Exchange. The strength in these platforms is their ability to allow programmatic data sharing between organizations using tiered access (such as the Traffic Light Protocol). If your organization is currently lacking a threat sharing platform you may be missing a treasure trove of security data. Even if you have a paid threat intelligence platform free tools like MISP are extremely likely to have different data sets and more flexibility for sharing data with other groups. Keep in mind these platforms are also your opportunity to contribute to the security community.
Conclusion
While GDPR affected the way that many analysts have historically conducted investigations, there are still several methods to uncover threat actors’ tracks. By usingDomain Risk Score, non-registrant based indicators, OSINT, and participating in information sharing organizations, analysts can identify useful indicators to produce intelligence and defend their organizations.
Tools and Resources
VirusTotal: https://www.virustotal.com/#/home/upload
Malwr: https://malwr.com/
Hybrid Analysis: https://www.hybrid-analysis.com/
Censys: https://censys.io/
Crt.sh: https://crt.sh/
OSINT Framework: https://osintframework.com/
Awesome OSINT: https://github.com/jivoi/awesome-osint
MISP: https://www.misp-project.org/
AlienVault Open Threat Exchange: https://www.alienvault.com/open-threat-exchange

