Threat Intelligence Sharing in Action: Cyber Community COVID-19 Response

As we’ve seen time and again, cybercriminals will use any tragic event to take advantage of people when they are emotionally vulnerable. Many anticipated cybercriminal activity to ramp up in order to exploit a global pandemic. However, COVID-19 themed attacks sprang forward with a speed and scale that was unlike anything we’ve seen before.
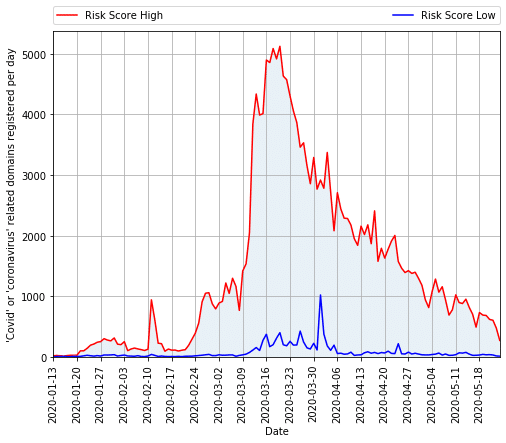
Beginning in early February we started to see hundreds to thousands of coronavirus-related websites appear daily. In mid-March, we also uncovered ransomware masquerading as an Android app called “COVID19 Tracker,” showing that cybercriminals were attempting to use every channel of malware distribution at their disposal.
During that same time period of mid-to-late March, we saw the peak of cybercriminal activity, with over five thousand “COVID” or “coronavirus” themed domains registered per day. An ISACA survey during this time found that 58% of cybersecurity professionals said that threat actors were taking advantage of the pandemic to disrupt their organization.
This was all happening during an unprecedented, immediate need to transition the entire workforce to remote work. Security teams couldn’t just focus on defense work. They were tasked with driving the organizational effort to rollout work-from-home capabilities as rapidly as possible. This meant everything from ensuring remote work security policies were in place to helping troubleshoot home users’ Wi-Fi problems. According to an (ISC)² survey, 47% of respondents said they had been repurposed into general IT to accommodate different needs for work at home amid the pandemic.
Everyone’s lives had been completely upended by the coronavirus. Security teams were being stretched thinner than ever and the bad guys were knocking at the front door. Instead of sitting back and watching as the world burned, a group of likeminded cybersecurity professionals came together and decided to take matters into their own hands. What started as a simple Slack channel transformed into the COVID-19 Cyber Threat Coalition (CTC) and volunteering my services there ended up being one of the most exciting and rewarding experiences I’ve had in this profession.
Bridging Traditional Boundaries
Much has been written about how threat intelligence sharing can improve the security posture across all industries. Knowledge sharing, however, has never come easy in the cybersecurity industry. When your job requires a good degree of paranoia to be successful, trust can prove difficult. But the gravity of this pandemic across the globe was just so heavy that it brought us together.
People wanted to use their expertise to do some good in the world, and that meant protecting against bad actors trying to use the pandemic for profit. CTC’s mission says, “We’re united in our feeling that extraordinary times call for bridging traditional boundaries to operate with unity and purpose.”
This call to unity played out daily as volunteers from different companies that otherwise might not have reason to work together were passing data back and forth to help each other in threat investigations and domain vetting. With all of our combined skills, tools, and products, we were able to move fast and rapidly get allowlists and blocklists in place.
Chaos Drove Community
When the CTC set up it’s Slack workspace for volunteers to join, it was a little chaotic at first. But over the first week the CTC leaders made changes to how it was organized and pretty soon everyone was operating full tilt towards addressing Covid-19 related cyber threats as a community.
Here are a couple key takeaways from my experience participating in the CTC that could help future threat intelligence sharing organizations ramp up to speed and start addressing threats as fast as possible.
- Figure out your organizational structure and operating procedures ASAP to get operating faster and avoid confusion. For example, if Slack is your primary collaboration platform, utilize channels to organize work and IoC discovery by threat vector. Be deliberate about your channel names and if anything opt for too many channels vs too few. It can be confusing when channels are renamed and channel topics are split into 2 or 3 new channels.
- Setup “vetted channels” and have a process for vetting volunteers early on. Within the first week of the CTC there were a couple thousand volunteers all participating in the different channels. It became clear fairly early that there was a need for a subset of vetted volunteers who were responsible for verifying IoCs or vetting domains in your allowlist.
- Consolidate IoCs in one centralized place from the get go. The first week of the CTC was a bit of the wild wild west via Slack. People were joining the Slack workspace in droves and dropping IoCs and domain allowlist requests all over the place. It was hard to scour the different channels to find relevant IoCs. Within a week, the CTC moved to using AlienVault for recording all IoCs relevant to Covid-19 related threats.
- Setup discipline specific channels for cross organizational collaboration. One of the channels I was highly involved with was the “data science” channel, which was made up of people from a diverse set of cyber security companies, each with a different view of the threat landscape. I was able to work with people who ran endpoint security systems, which gave me a view of threat patterns “behind the firewall” I normally wouldn’t get at DomainTools. Vise versa, I was able to enrich people’s analyses and investigations with DomainTools datasets.
Over the first couple weeks of existence the CTC morphed dramatically, but eventually stabilized into something that was very efficient and effective at identifying threats and communicating it’s learnings to the broader community.
One deliverable that we started publishing in early April was the CTC Weekly Threat Advisory. There we analyzed different COVID related security trends such as domain-spoofing trends, phishing and ransomware attacks, and everything else we were coming across that week. Any organization could freely use this to get the latest and greatest COVID threat intelligence that was put together by experts from organizations and tech providers across the cybersecurity landscape.
A Roadmap for Threat Intelligence Going Forward
Threat intelligence sharing outside of your organization not only works but adds layers of value that we’ve been letting go to waste.
Prior to COVID, many organizations never gave remote working a serious thought. Maybe it works for some companies, but not theirs. “It’s just not possible”, said leaders of many organizations. Now there is irrefutable evidence that remote working not only works, but people are thriving in this new environment.
The same attitude change is happening within threat intelligence. We’ve seen how much value is created when we share what we know as a group. The CTC allowed people who would normally be separated by corporate boundaries to come together and work as one for the greater good. We were able to organize a cohesive defense against a common enemy and disprove the notion of “It’s just not possible.” Not only is threat intelligence sharing possible, we thrive in it.
Over the past month, the number of Covid-19 related cyber threats has dramatically dropped, and the CTC has spun things down. But the goal of the CTC is to keep the organization and operating structure in place for the next big threat. No one is looking forward to the next high-impact event that may bring us all together again. But when the inevitable happens, we’ll be more prepared, especially if we incorporate more threat intelligence sharing in the cybersecurity community as part of how we operate daily going forward.
Originally Published in Security Boulevard



