Holiday Bazar: Tracking a TrickBot-Related Ransomware Incident
Background
On 21 December 2020, the start of the Christmas week, evidence emerged of a ransomware campaign leveraging BazarLoader (also referred to as KEGTAP) and linked to the TrickBot ransomware gang. Initially disclosed in a tweet, the campaign rapidly unfolded over the course of that day.

Based on discussions with intelligence partners and various network defenders, the adversaries responsible for this activity appeared to rapidly move from initial infection at victim locations to interactive operations en route to attempted ransomware deployment. In previous operations, TrickBot activity is associated with the deployment of Ryuk ransomware. At the time of this writing, DomainTools researchers were unable to confirm a final-stage payload for this specific campaign.
Although this specific campaign has since passed, it contains many lessons for network defenders and Cyber Threat Intelligence (CTI) professionals for monitoring and analyzing emerging campaigns to enable dynamic, flexible defense.
Initial Delivery and Download Vector
Analysis of the campaign indicates initial delivery takes place using a legitimate third-party email messaging or notification service. In this specific case, the adversary leveraged GreatResponse, used for email marketing and landing page design, to deliver seemingly benign-looking email messages with “Corporate Document” or similar themes. Observed link examples include the following:
corpdocument1221.gr8[.]com
companygeneralmeeting122220.gr8[.]com
Companydocument07851-3173f.gr8[.]com
When accessed, a victim would see a landing page such as the following:
The link would direct to a Portable Executable (PE) file, discussed in further detail below, hosted on Google Drive. Further execution would require the user to run the downloaded executable for follow-on exploitation to occur.
The above activity is consistent with observed TrickBot operations—as well as other entity tactics—using third-party services to evade detection and mitigation. For example, TrickBot gang campaigns have previously used third-party delivery services such as Sendgrid to distribute initial phishing messages. Follow-on payloads have also been hosted on cloud file storage sites, such as Google Drive, as well.
Examining Droppers and Installers
Further activity requires not only user interaction with the phishing message (displaying the landing page link) and downloading the file hosted from Google Drive, but then executing the payload as well.
Overall, as part of the completion of this “kill chain,” DomainTools researchers observed 18 samples of the next-stage payload. Naming conventions for these files matched the landing page themes, although DomainTools researchers expect more variants likely exist beyond our visibility.
One sample, “View Report.exe”, is a 32bit executable that appears to date from late November 2020 and from part of an earlier, undocumented campaign. The remaining samples are 64bit executables compiled on the day of the campaign, 21 December 2020.
The executables in this campaign are signed with the same Sectigo code signing certificate, with the name “СКАРАБЕЙ” (Russian for “Scarab”) and a fingerprint value of “348F7E395C77E29C1E17EF9D9BD24481657C7AE7.” This certificate has since been revoked by the issuer.
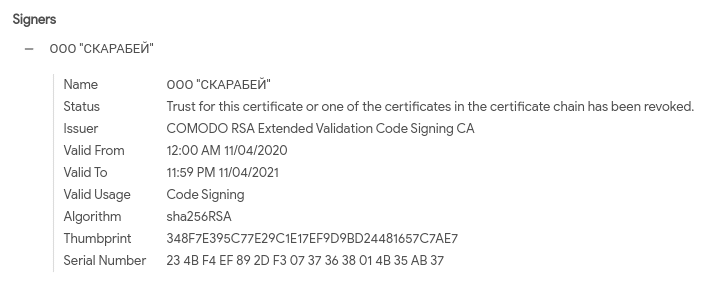
While signed binaries are not new to ransomware or related operations (with notable signed examples including but not exclusive to Ryuk and LockerGoga variants), they continue to pose a threat to users as many applications and security products inherently trust code-signed items.
Following successful binary execution (through user interaction), the malware attempts to resolve and connect to one of at most two Command and Control (C2) servers embedded within the binary. Successful connectivity allows for further actions on target, including the attacker taking control of implants to launch further commands or move laterally within the victim environment.
Associated Network Infrastructure
As noted in the original Tweet sparking this investigation, there were several domains immediately identified as associated with this campaign. Further investigation and analysis of samples yielded additional items, shown in the following table:
The identified network infrastructure serves as the next stage of the intrusion. Following malware installation, active C2 would be used to further exploitation of the victim, leading to likely ransomware activity.
Pivoting and Identifying Additional Items
At this stage, we as defenders are largely in a “reactive” state with respect to identifying indicators and characteristics of this BazarLoader campaign. While quickly ingesting and deploying defensive measures based on indicators and observables may represent an improvement over completely passive defense, it still leaves much to be desired.
Instead, by identifying characteristics inherent to the campaign—both its network infrastructure and malware samples—we can both gain greater knowledge of the attacker’s tendencies while enabling defense attuned to these tendencies. For the latter, this means adapting defense to the adversary’s fundamental behaviors as opposed to chasing specific examples of those behaviors as represented by indicators.
Network Observables
Looking at the domains identified above, several “themes” emerge:
- Typical use of naming “themes” reflecting local service providers or small business entities, with an emphasis on “cleaning” companies.
- Consistent use of NameCheap for registration purposes.
- Almost exclusive use of the “.com” Top Level Domain (TLD).
- Creation on the same day, 10 December 2020.
- Hosting on various relatively small, privacy-focused Virtual Private Server (VPS) providers.
- Use of Let’s Encrypt SSL certificates for encrypted communications.
As previously documented by DomainTools, these observations can be used to unearth additional C2 infrastructure for threat hunting or preemptive defensive purposes. Unfortunately, at first glance by plotting the above items using DomainTools Iris visualizations, there seems little in common on a technical level to enable successful pivoting to additional infrastructure.

Yet a combination of limited technical details that overlap (registrar, TLD use, and time of creation) along with “thematic” observables (the naming conventions used) can enable us to unearth additional items.
With this hypothesis in mind, looking for items with a similar technical structure that also mirror the “local service” or “local business” theme, we can identify the following through DomainTools Iris:
This list is extensive and includes items that are likely not related to this campaign, but other items seem to fit the pattern observed quite well. Examples include:
blueridgecabin-cleaning[.]com
carwashevanstoon[.]com
cleaningcompany-online[.]com
coloradobudokann[.]com
Johnnyclean-carwash[.]com
stonyhand-carwash[.]com
These items form the basis for further threat hunting and CTI analysis. Given that all of the identified items are marked as likely malicious based on DomainTools risk scoring algorithms, the options available to defenders range from adding the domains and related infrastructure to blocklists as a preventative measure to monitoring them for further activity. For example, items such as those called out above could be flagged in various services, such as DomainTools domain monitoring, to identify when changes or file associations occur.
File Patterns
In addition to domain patterns, the malware samples associated with this campaign also feature several commonalities that can be used for either hunting or alerting purposes, depending on the tools and visibility available to the researcher. From the information available thus far, we have the following insights:
- Exclusive use of 64bit binaries downloaded from cloud storage providers.
- Use of the same Sectigo signing certificate across all known samples.
- Common file naming conventions based on variations of “company report” and similar themes.
- Commonality in C2 infrastructure.
From the above, DomainTools researchers began investigating multiple data sources for similar file characteristics as well as items contacting domains revealed in the network pivoting exercise documented in the previous section. From this and follow-on analysis from initial findings, DomainTools researchers unearthed another BazarLoader campaign from 17-18 December 2020. The following samples and C2 domains were observed:
Multiple samples were identified with C2 infrastructure linked to the domain pivoting in the previous section. While this did not appear to succeed in identifying “new” items (as the files in question appear to have been active from 17-18 December 2020, before the originating campaign sparking this investigation), their discovery indicates other items in the list of possible domains may relate to future campaigns by the same actor. Additionally, some items were revealed which featured C2 domains not related to the pivoting documented earlier. Examples include:
akbuilding-services[.]com
Homeclean-heroes[.]com
Maidtoorderfll[.]com
Although exhibiting C2 domains beyond initial research, the items were linked by a common code signing certificate (again from Sectigo, and since revoked by the issuer) with the name “ИНТЕЛЛИТ” (Belorussian for “Intelligence”) and thumbprint “1103DEBCB1E48F7DDA9CEC4211C0A7A9C1764252”:

Although a different certificate than that used in the 21 December campaign, it reflects similar themes and observations. One item in common with both signing certificates is the prefix “OOO”, which in Russian (and related) languages is equivalent to “Ltd.” While there are many legitimate entities that can and do sign their software with certificates including “OOO” in their name, this may function as a robust indicator for organizations with few or no commercial ties to Russian or related language entities for blocking or filtering files with code signing certificates containing such language. This code signing observation represents a start in overall defensive planning against malware campaigns such as that observed in this report.
Defensive Recommendations and Mitigations
We have already discussed several examples of possible alerting items for this campaign, ranging from signing certificate observables to infrastructure commonalities. However, network defenders must be attuned and responsive to a variety of adversary “tells” in campaigns to ensure robust and complete defense from intruder operations.
First, the simple identification of new or anomalous network traffic—whether as email links, user interactions, or programmatic communication—can do wonders for network security posture. For example, all of the domains identified in the analysis so far have scored as likely malicious through the DomainTools risk-scoring algorithm. By programmatically tying network security monitoring or log capture (such as proxy logs) to a threat intelligence source such as DomainTools, defenders can rapidly identify communication to new, likely risky sources and use this as a mechanism to launch further investigations. Done in a timely fashion, this can work to disrupt ransomware actor operations and interrupt events before they proceed toward ransomware deployment.
Second, organizations must be attuned to the malicious use of code signing for the delivery of malware. In this specific campaign, the Sectigo signing authority was abused to sign malware for delivery and execution. From a defender’s perspective, we cannot completely distrust Sectigo (as it is used by many organizations), but we can identify ways to narrow our degrees of trust to reduce attack surface. Within the context of the currently discussed campaigns, identifying the “OOO” string, corresponding to “Ltd” in Russian and related languages, may be sufficient to distinguish between trusted and unknown software depending on one’s business operations. Identifying such “tells” and their implications can allow defenders to take even trusted items, such as code signing certificates, and narrow what is truly allowed or acceptable within their environments versus what is anomalous or suspicious.
Finally, the entire infection chain outlined above relies on a user interacting with a phishing message then executing an unknown binary from a cloud storage location. These items represent critical touch points for defensive response and monitoring—and user education. Through email security monitoring, organizations can identify, categorize, and filter providers for things such as landing pages and response emails to reduce attack surface. Furthermore, organizations can limit or completely block the download of files (or at least executable files) from external cloud storage locations to further reduce risk. Lastly, execution by the user of an unknown (even if signed) binary can be limited through either training or operating system controls to eliminate the ultimate stage of this attack sequence.

Overall, visibility into network communications, the ability to refine those communications with the support of external CTI sources, and combining this with host-based or malware-centric observations will enable defenders to identify, track, and hopefully mitigate potential ransomware events such as that described above. This whole-of-killchain approach, similarly documented with respect to BazarLoader by Red Canary in 2019, ensures detection at various stages of adversary operations. Through concerted effort and continued refinement, defenders will be able to identify “normal” activity within their environment and set that against abnormal traffic that may be related to malicious operations. As a result, defended organizations can gain some lead time over intruders, setting up proactive or preemptive defenses to limit exposure to campaigns as they materialize.
Conclusion
In this analysis, we identified an initial campaign and used related items to reveal a slightly earlier ransomware campaign likely related to the same adversary. By applying this process in a continuous, iterative fashion, we as network defenders and CTI professionals can continually reduce the scope and degree of movement for adversaries and improve the prospects of network defense. Marrying network security monitoring with network indicator enrichment through sources such as DomainTools can reveal campaigns in progress, while subsequent relations to file-based observations can cement these views to enable holistic network defense. Ultimately, network defenders must leverage all sources available to them in order to adequately respond to and detect such threats, with the goal of minimizing adversary dwell time and maximizing defender opportunities for response and recovery.



