Coming up this week on Breaking Badness. Today we discuss: Supply Chain of Fools, Phish Out of Water, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Supply Chain of Fools
- Last week, members of the Five Eyes intelligence alliance warned managed service providers (MSPs) and their customers that they're increasingly targeted by supply chain attacks
- For a brief background on the players behind Five Eyes (FVEY):
- They are an intelligence cooperative of sorts between the US, Great Britain, Australia, Canada, and New Zealand
- If Wikipedia is to be believed, their origins can be traced back to “informal secret meetings during World War II between British and American code-breakers, which started before the U.S. formally entered the war, followed by the Allies' 1941 Atlantic Charter that established their vision of the post-war world.”
- The group is complete with other acronyms like ECHELON and PRISM, which both describe extensive electronic information gathering capabilities that have been considered controversial at various times and by various people, but nonetheless have provided a large amount of national security intelligence for all of the countries involved
- Given FVEY’s extensive background and longevity, this is hardly their first advisory
- They’ve issued bulletins over the years, but narrowed down to the cyber realm, their history goes back to 2017, if not further, addressing specific things that affect managed service providers (MSPs)
- MSPs in this advisory are “entities that deliver, operate, or manage ICT (Information and Communications Technology) services and functions for their customers via a contractual arrangement, such as a service level agreement.”
- For those less familiar with MSPs (or the more specialized MSSPs), you are putting a lot of trust into outsourced IT providers
- They need access to just about everything that communicates electronically in your environment
- For smaller organizations, MSPs essentially define the environment - they design, build, maintain, upgrade, and oversee it
- Any MSP, depending on its size, could have anywhere from a handful to hundreds of customers (where a “customer” is a company, not an individual)
- So if an MSP is compromised, then the bad actor or actors have access to vast amounts of data, communications, etc.
- There’s not a lot of information regarding how FVEY discovered these threats (which is to be expected)
- In the advisory, these do give a shoutout to SecureWorks, which was bought by Dell, then went IPO again on its own (but still with Dell as the majority owner) and which is itself one of the biggest managed service providers on the planet
- So undoubtedly SecureWorks is seeing lots of activity in their own networks, meaning SecureWorks itself as well as the customers they are protecting
- They did the right thing by going to the intelligence community and reporting up some of what they are witnessing
- Some of the actions MSPs and their customers can take before or during these situations is similar to actions you are likely already familiar with:
- Prevent initial compromise by securing vulnerable devices, locking down access, patching, etc.
- Beef up your logging and monitoring
- Enable multi factor authentication
- Apply least privilege everywhere
- Deprecate obsolete accounts
- Have awesome backups, where “awesome” means robust and to whatever extent possible, isolated from where a compromise can come infect the previous backups
- So all MSPs need to be doing the things they already should be doing, but doing them better. It’s probably pretty frustrating in some ways to be told to do what you already are stressed out about doing well, but at the same time you can’t fault CISA for saying it; they would be remiss if they didn’t
- Really the key thing here if you’re an MSP is to be aware that things have ramped up - and if you weren’t aware of that already, you aren’t doing it right
Phish Out of Water
- A novel form of phishing takes advantage of a disparity between how browsers and email inboxes read web domains
- This attack was brought to light by Perception Point’s IR team
- It’s a hastily-designed phishing email that should have been caught by spam filters, however because it was crafted using an “@” symbol in the middle, it wasn’t flagged and made it past security
- It’s unclear if this was intentional - as mentioned above, the message wasn’t designed well and the domain name was “storageapi.fleek.co with a string of random characters, so their plans may be been concrete, but there’s also the chance they got lucky in their message making it to inboxes
- This technique worked because, depending on your browser, typing “https://” in your address bar following by the @ symbol can return an error or just disappear
- This feature was recently removed from Microsoft’s Internet Explorer given how easily threat actors can create malicious websites using it
- The actor behind this incident is still unknown, though their IP address comes from Japan
- The good news is while this is a novel attack, it didn’t fool anyone
- In order to mitigate these types of attacks, security teams need to review and update their detection engines to see the URL structure and if an @ is included
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
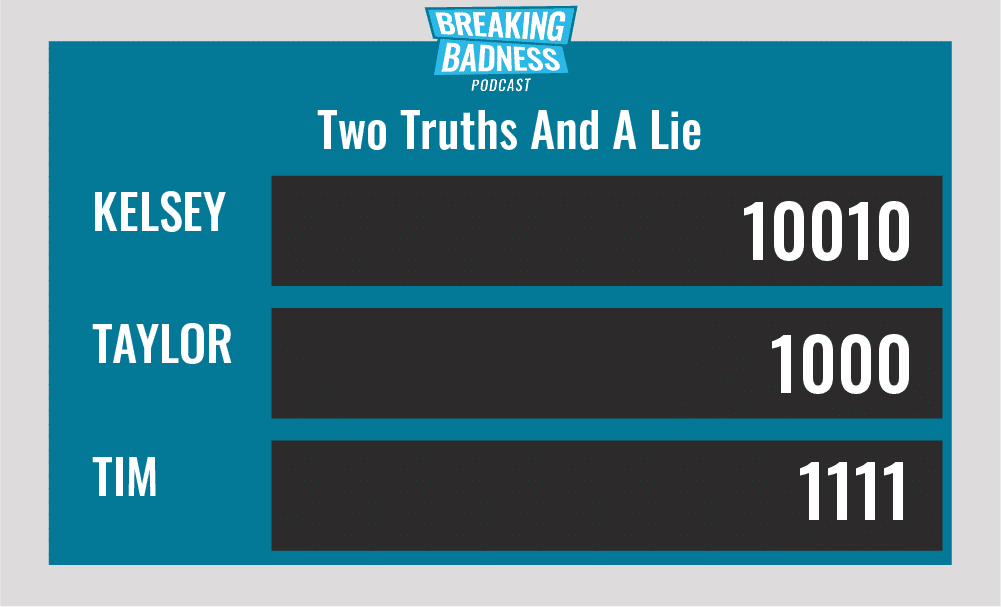
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Supply Chain of Fools[Taylor]: 3.5/10 Hoodies[Tim]: 4.5/10 Hoodies
Phish Out of Water[Taylor]: 4.5/10 Hoodies[Tim]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.*A special thanks to John Roderick for our incredible podcast music!

