Coming up this week on Breaking Badness. Today we discuss: Disturbing the Hive, True GRIT, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
Disturbing the Hive
- Last week, the Department of Justice thwarted the Hive ransomware network in over $130 million in demands
- The Hive syndicate popped up in the summer of 2021 and were fond of hitting healthcare victims in the middle of the pandemic
- They were big in running with affiliates and publicly sharing their victims’ names and who wasn’t paying the ransom
- In terms of tactics, techniques, and procedures (TTPS), you name it, it was everything you’d expect from a cybercrime group
- They targeted retail, healthcare, energy and infrastructure, you name it - they had 1500 victims in 180 countries
- The FBI made the takedown, but this is a global threat
- The FBI partnered with INTERPOL and German law enforcement in this takedown
- For the size and scope, the FBI definitely had help
- How does sharing decryption keys work?
- The FBI sat inside of the ransomware group for basically 6 or 7 months pulling decryption keys
- So if you’re already working with the FBI, that’s a pretty easy lift
- This is an ongoing case, so there aren’t any details on how they were able to thwart this group, but it could be as simple as password reuse or as complicated as running with one person in the US to watch and wait and acquire more
- That sentence “we legally hacked back,” could mean so many things
- They were able to identify two back end servers in Los Angeles and execute that takedown
- All the affiliates had the rug pulled out from under them
- If these people ever do get in front of a judge for these crimes, we might get more information
True GRIT
- In this article from Dark Reading, we’ll take a look at a few findings on ransomware trends in the latest report from the GuidePoint Research and Intelligence Team.
- Some say ransomware attacks are declining and others say they’re just as strong as ever
- Tim says it’s definitely not going away - there’s no question about that
- What made the news a lot at the end of 2022 was the story was how ransomware profits dropped according to one study, so that’s pretty interesting and there’s a number of factors why that might be the case
- The ‘it’ we’re talking about can take different forms, because if you’re talking about profits declining, then yes that has gone down, but if we’re talking about the number of events that happened in 2022, that seems to be on the rise
- So what is the GuidePoint Research and Intelligence Team (GRIT)?
- GuidePoint is more than a value added reseller (VAR)
- Part of what they offer to customers and the community is some of this research
- We’re unsure how many years running they’ve done this report, but it is interesting and we hope listeners take a look
- Part of this report organized ransomware groups into 4 buckets - what is this taxonomy?
- It’s hard to keep track of everything going on because there are so many different groups, they use different malware, and then you add in affiliates - it gets complicated
- The buckets defined are full-time, rebrand, splinter, and ephemeral
- Those are fairly self-explanatory
- LockBit would be a good example of a full-time group (they’re responsible for a third of attacks in 2022)
- No one has really put out an infographic of rebrands over time, but that would be helpful
- Useful way to think about it as a researcher
- Does rebranding make it more difficult to discern who is behind an attack?
- If you’re in the SOC, it’s not like you can create firewall rules based on ransomware groups - that’d be nice, but you can’t do that
- If you are trying to protect your users and environment, on a day to day basis, knowing which group it is may or may not be critically important
- From the SOC analyst point of view, we’re not sure it matters that much in terms of how you do your job
- From a research perspective, it’s a little bit different. If you’re tracking and studying these groups to expose their TTPS, then it is harder when they go underground and come back as a hydra with new limbs
- If you’re a ransomware negotiator, it will help your tactics and you know what your approach should be
- Can you trust that these cyber criminals will come through once the money hits? We actually discussed this a little on Episode 141 where criminals were outing other criminals regarding lack of payment or promise on tools, but what about the actual criminal/target relationship - can they expect better customer service?
- Tim has a little bit of a different opinion - again it comes down to your role
- If you’re a ransomware negotiator, the better you are at your job, the better the outcome
- But it’s far from guaranteed they’ll come through if you pay the ransom
- That’s why not paying is still the predominant advice
- There are laws that make it illegal to pay groups
- Somewhere between a quarter and a third of the time, you’ll see that the files get posted anyway despite payment
- If you do pay, you become more likely to be a target again in the future
- Hopefully your defenses become better after an attack, but it’s still certainly a risk
- Tim has a little bit of a different opinion - again it comes down to your role
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You'll have to tune in to find out!
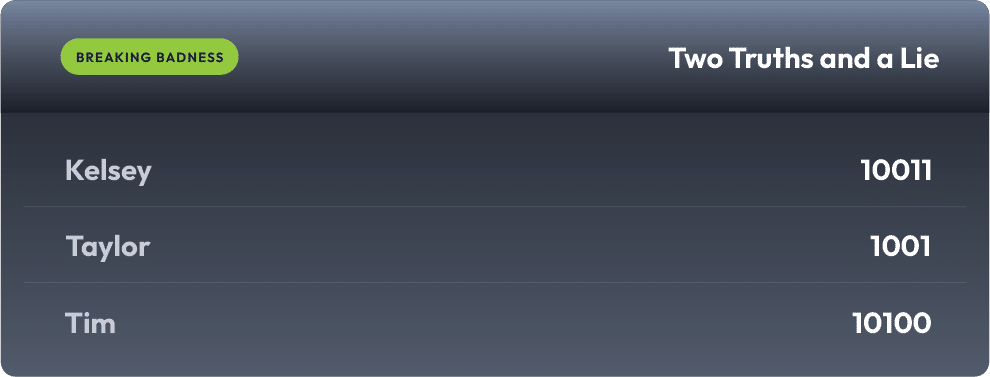
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Disturbing the Hive
[Taylor]: 6/10 Hoodies
[Tim]: 5/10 Hoodies
True GRIT
[Taylor]: 6.23/10 Hoodies
[Tim]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!


