Blog
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Blog

DomainTools & Cribl: Continuous Enrichment for Enhanced Intelligence
Blog
Avoiding Activation Scams this Football Season
Blog

Using the DomainTools Feed API in Splunk
Blog

Proactive Defense with DomainTools Real-Time Feeds
Blog

DNSDB Scout Updates: Streamlined Interoperability with Iris Investigate
Blog

Why Your Protective DNS Needs Real-Time Data: The DomainTools Advantage
Blog
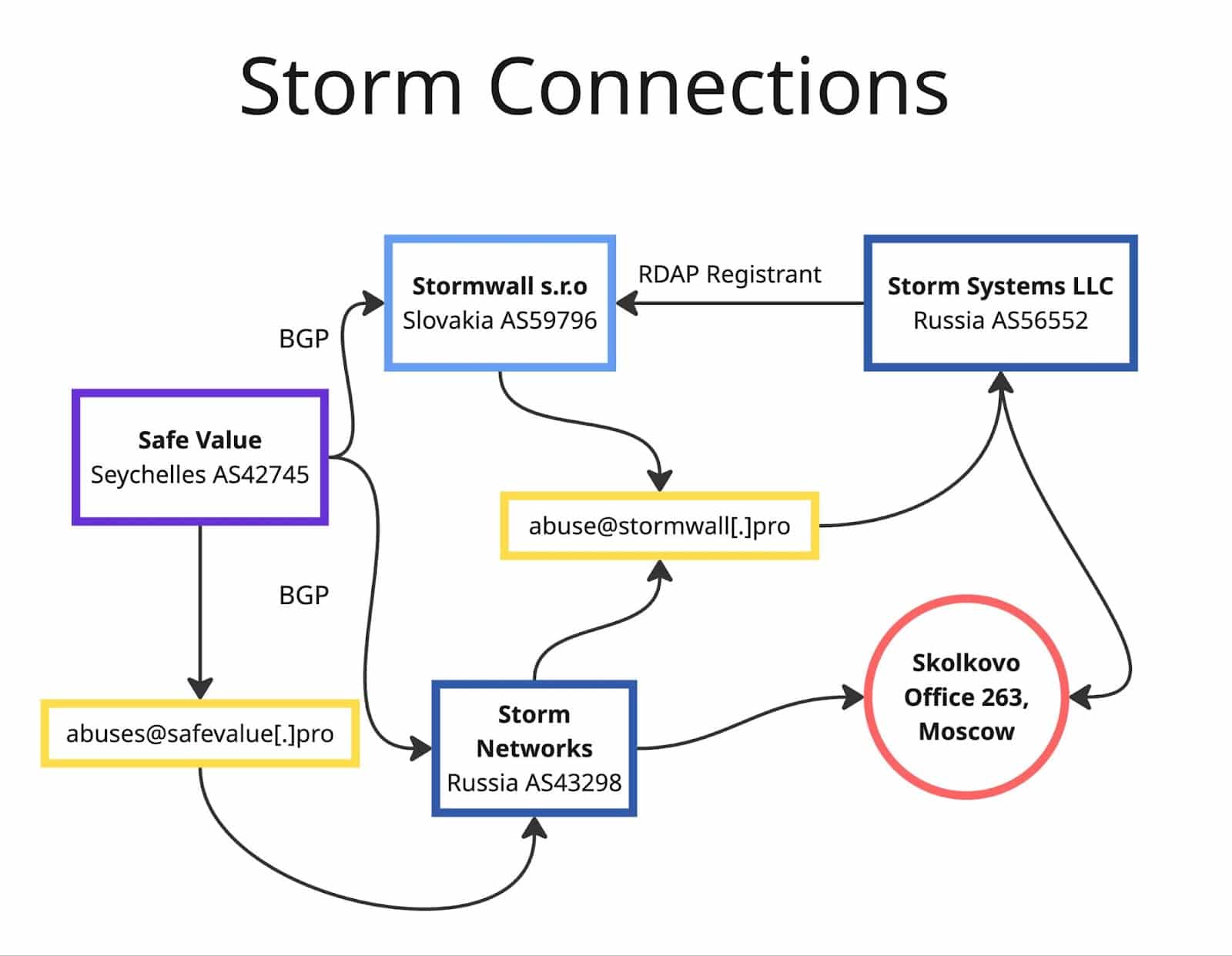
RDAP and BGP in Investigative Journalism
Blog

Part 2: Tracking LummaC2 Infrastructure
Blog

"I've Found Some Bad Domains—Now What?"
Blog

Newsletter No. 5: A Little Bit of Research in my life…
Blog

The Resurgence of the “Manipulaters” Team - Breaking HeartSenders
Blog

Tracking LummaC2 Infrastructure with Cats

