Catching Cybercriminals Exploiting the Pandemic Follow Up
Since the initial outbreak of COVID-19, cybercriminals have since found many ways to take advantage of anxious and fearful users. There have been reports of TrickBot campaigns, Ryuk ransomware targeting hospitals, and hackers hijacking routers’ DNS to spread malicious COVID-19 Apps. The DomainTools Security Research Team recently discovered a website luring users into downloading an Android application under the guise of a COVID-19 heat map.
Alongside the devastation of the pandemic, and opportunistic threat actors, we have seen both security organizations, vendors, and individuals do everything they can to minimize additional hardship. We thank them for their ongoing work and dedication. In an effort to support making the Internet a safer place, we have provided a free, curated list of high-risk COVID-19 related domains.
There was a huge response to the research conducted by the Security Research Team at DomainTools so we asked Senior Security Researcher, Chad Anderson and Senior Security Engineer & Malware Researcher, Tarik Saleh, to share their findings. Chad and Tarik walked through the entire process of identifying a nefarious domain, mapping connected infrastructure, and reverse-engineering a ransomware attack.
The presentation was so popular not only did we run out of space, we didn’t have the opportunity to answer your thoughtful questions. To this end, we included Q&A in this blog post. Finally, we asked all of the attendees to participate in two polls, so we’ve also incorporated the poll results in this post.
Catching Cybercriminals Exploiting the Pandemic Poll Questions:
Thank you again for those who participated! We asked two questions at the end of Chad and Tarik’s presentation:
Android based threats are relevant to me and my organization.
- Strongly Agree
- Agree
- Disagree
- Strongly Disagree
The influx of COVID19 related attacks has greatly affected my organization.
- Strongly Agree
- Agree
- Disagree
- Strongly Disagree
Below are the responses:
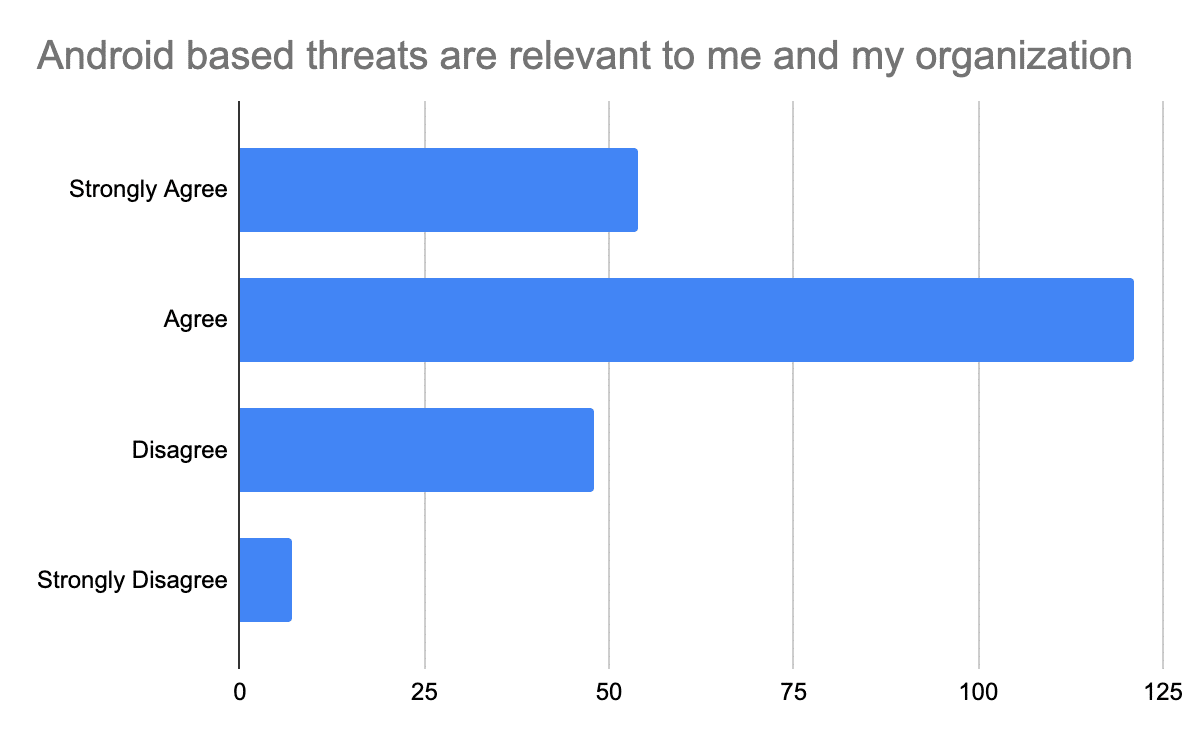
230 total participants
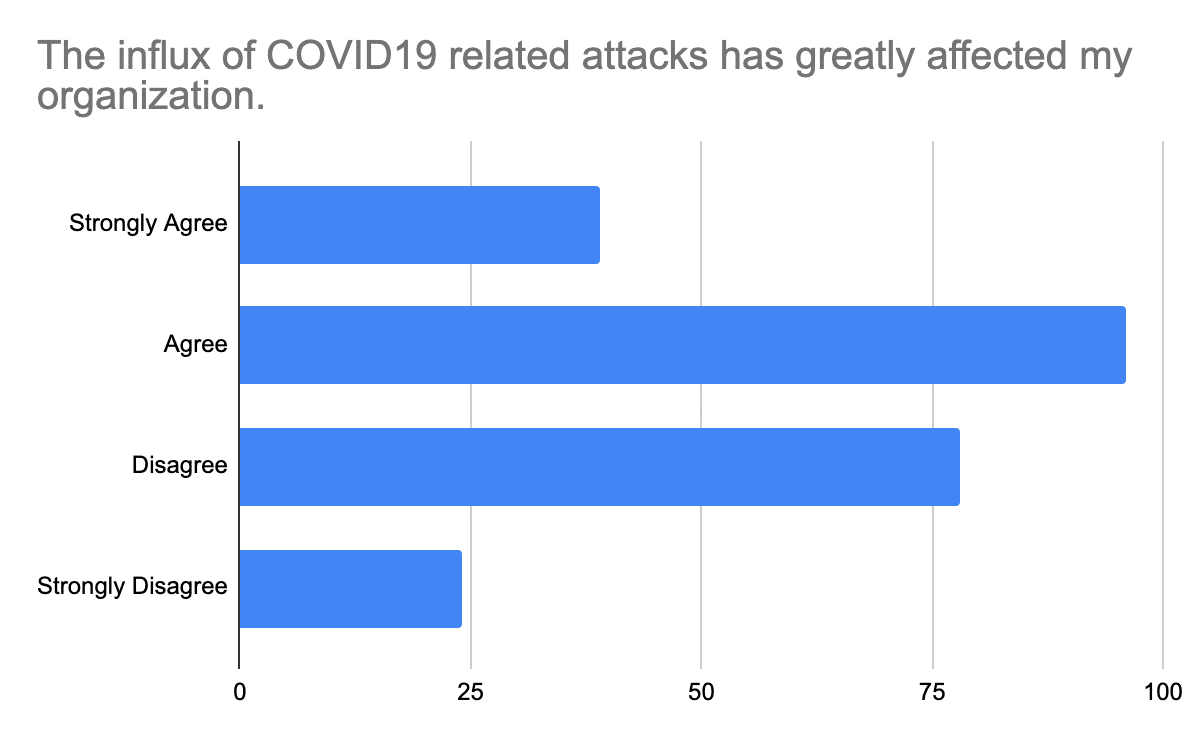
237 total participants
There was a fairly strong response to the second question. Over half of the participants have been greatly impacted by an influx of COVID-19 related attacks, which reinforces research conducted by Microsoft. According to the Corporate Vice President of Microsoft 365 Security, “Data shows that these COVID-19 themed threats are retreads of existing attacks that have been slightly altered to tie to this pandemic. This means we’re seeing a changing of lures, not a surge in attacks. Our intelligence shows that these attacks are settling into a rhythm that is the normal ebb and flow of the threat environment.”
Q&A with Chad Anderson, John “Turbo” Conwell, and Tarik Saleh
A majority of the questions fell under four categories:
- CovidLock Research
- COVID-19 Trends
- COVID-19 Threat List
- General Education
CovidLock Research
Q: Is the java code making direct api calls to the manifest after the .apk is unpacked?
A: A manifest file in Android is essentially informing the OS what permissions the application (among other things) is requesting to access. The code of the APK makes those API calls being requested from the manifest after you have given the APK permission to do so.
Q: Is the mentioned ransomware available on Darknet as a software generically marketed? Or does it seem to be specially developed by the criminal behind your case?
A: CovidLock appears to be compiled and used for this specific attack campaign. I’ve seen no evidence of the threat actor selling their code or APK on any marketplaces as of now.
Q: How many Bitcoin Wallets are there?
A: One single BTC wallet as of now.
Q: Is that the ONLY wallet they used? Didn’t you explain that they could change the BTC wallet address on the fly?
A: That is the only BTC wallet being used by CovidLock at this time. The attacker has the ability to modify the bit.ly link to redirect to another PasteBin site containing a different BTC wallet, but they have chosen not to. In addition, it’s an act of futility if they do since Google Play Protect is now aware of CovidLock and has appropriate signatures to detect it.
Q: Are you seeing these types COVID issues on IOS?
A: When it comes to malicious applications, no. Apple’s iOS doesn’t allow sideloading of applications outside of it’s App Store.
Q: Did you see any COVID-19 related ransomware for mediums other than android?
A: Windows OS is still the top target, for several reasons. The CTI’s I follow have shown almost zero COVID-19 related ransomware samples affecting MacOS or Linux. That’s absolutely not to say they don’t exist, they likely do, however we just haven’t collectively seen them in the wild as much.
Q: Does this malware encrypt all the phone data or simply block your phone?
A: CovidLock does not encrypt each file on your system like traditional ransomware does, however on a higher level it achieves the same means of “locking a user out of their access” to their data by resetting the PIN number for the lock screen. This is known as lock screen attack and is popular with Android ransomware.
Q: Can you say if the attacker has been identified? The reason I ask is to determine if this could be the same attacker involved in other scams besides COVID-19?
A: We performed attribution to the best of our abilities and there was an older WHOIS record containing a name and address. We passed that along to law enforcement. They were identified in previous scams over the past five years as well.
Q: Have these attacks linked to a particular organization or country?
A: Not that we can tell, just one individual.
Q: Is this all on clearnet what about the dark web?
A: All on the clear net. No dark web ties so far.
COVID-19 Trends
Q: Have you seen any COVID-related ransomware receiving a reasonably high amount of BTC? If so, which campaigns were successful?
A: Ryuk and Maze are two big impact ransomware campaigns that have targeted medical facilities under the guise of coronavirus maldocs but we don’t really have details on the ransomware value amounts.
Q: Have you seen COVID number tracking sites with malware lurking in the background?
A: Not as much as I expected. Phishing and “grey market” selling PPE’s are way more common.
Q: Have you seen any malware targeting healthcare staff and/or organizations?
A: Absolutely. Malicious documents with ransomware payloads seem to be the most common. Despite that so-called agreement by several notorious threat groups not to, the big players like Ryuk and Maze haven’t stopped attacking medical infrastructure.
Q: For what particular scams are the corona domains mostly used?
A: Mostly for fake products or medicine that never ships.
Q: If an individual finds suspicious sites or apps that appear to be exploiting COVID-19 maliciously, who can we report to for confirmation?
A: There are several ways to report suspicious apps or sites. You can always reach out to @DomainTools directly on Twitter and let us know, but you can also reach out to the Cyber Threat Coalition and let them know. They have several Slack channels for people to contribute both malicious COVID-19 related domains, as well as vetted domains that should be added to allowlists.
Q: What other terms are becoming more prevalent besides ‘stimulus’?
A: Hydroxychloroquine has been another huge one as well as reopen and liberate.
COVID-19 Threat List
Q: Does DomainTools have a stored DB of known bad domains using Covid19 attacks or have a project doing the same?
A: Yes, we do. Visit our recent blog post to learn more about the free DomainTools COVID-19 Threat List.
Q: I also see that the “DT COVID-19” list is shared to 3rd Party Threat Intelligence companies like Anomali ThreatStream
A: Absolutely. I have included a link to this blog post written by Anomali. Bandura Cyber also allows you to add the COVID-19 Threat List into their TIG. Finally, you can also view step-by-step instructions on how to add this list to Splunk Enterprise Security.
Q: Based on this Covid-19 “experience” do you see any improvement or new feature that can or will be implemented in DomainTools?
A: Yes, stay tuned for more on this in the coming days.
Q: Can you talk a bit about how you are vetting it and how you generate the risk score?
A: DomainTools Risk Score predicts how likely a domain was created to be malicious. The score comes from two distinct algorithms: Proximity and Threat Profile. Proximity evaluates the likelihood a domain may be part of an attack campaign by analyzing how closely connected it is to other known-bad domains. Threat Profile leverages machine learning to model how closely the domain’s intrinsic properties resemble those of others used for spam, phishing, or malware. The strongest signal from either of those algorithms becomes the overall Domain Risk Score. The COVID-19 hotlist is made up of domains with a Risk Score of 70 or greater and have a COVID-19 related term in it’s domain name. Unfortunately there are legitimate domains getting into the COVID-19 Hotlist. Most of these are very young domains with similar messaging as the malicious domains taking advantage of this crisis. We recognize this and are working to address along two fronts. First we are working with several organizations who are actively vetting and adding legitimate domains to allowlists, and second we are tuning our models to try and differentiate between the two better.For more information about our Risk Score, you can read this in-depth blog.
Q: About the high risk domains, how would you classify the domains with high values (95-99), is it mainly phishing/malware distribution or something else? I am a little confused, are these domains connected to the CovidLock?
A: The domains on our COVID-19 Hotlist are not related specifically to CovidLock. They are domains with a Risk Score of 70 or greater and contain a COVID-19 related term in their domain name. DomainTools Risk Score predicts how likely a domain was created to be malicious. The score comes from two distinct algorithms: Proximity and Threat Profile. Proximity evaluates the likelihood a domain may be part of an attack campaign by analyzing how closely connected it is to other known-bad domains. Threat Profile leverages machine learning to model how closely the domain’s intrinsic properties resemble those of others used for spam, phishing, or malware. The strongest signal from either of those algorithms becomes the overall Domain Risk Score. You can think of the Risk Score as our confidence level that the domain is malicious, but as with any machine learning based prediction, you should not interpret this as proof (of malicious activity). A score of 70 is our minimum bar for considering a domain might be malicious, and a score of 99 is our strongest confidence that the domain is malicious.
Q: Are you sharing IOC’s with Law enforcement?
A: Yes, this list has been shared with domestic and international law enforcement.
Q: Beyond SANS Covid19 Domain Classifier initiative, do you know of other uses of this list?
A: It can be used within your organization to enrich your investigations into phishing and malware domains. Leveraging the list in an IDS mode is a good option, alerting you if a DNS request is made to any of these domains on your list and taking appropriate action from there.
General Education
Q: How do I identify malware on my system?
A: Malware is constantly evolving in how it infects and stays undetected on systems. That being said, the best means of identifying if your system is compromised by malware is to look at behavioral based AV solutions, such as Windows Defender, Cylance, Carbon Black or Crowdstrike. These types of antimalware solutions are really effective at looking at how a binary operates, as opposed to just metadata of the binary to determine if it’s malicious.
Q: Based on the effectiveness of mobile related malware do you see this as a new frontier that can be used as an entry point for malicious actors into organizations considering mobile phones are rarely regulated in the office environment?
A: This is a great point and I definitely agree, especially for BEC attacks. We usually allow people to have their personal devices connect to mail and other infrastructure, and they are oftentimes unmanaged devices from a security perspective. So there is definitely a risk there!
Q: In addition to Android users, are there any known threats affecting iOS devices users?
A: Phishing is still an issue that every user on every OS needs to be concerned about. While iOS is not specifically affected by these types of ransomware attacks like Android is, they are still vulnerable to phishing/BEC attacks which could lead to larger attacks against you.
Q: How can I use urlscan etc to find new domains that have just gone live, without knowing the URL?
A: Several companies offer newly observed domains lists from their passive DNS offerings. That is the ideal way to discover newly registered domains outside of getting zone transfers of updated zones. DomainTools discovers more newly-registered domain names every day than any other organization in the world. Iris Detect enables you to identify existing and new domains that spoof legitimate brand, product, organization, or other names, so that you can carry out defensive or investigative actions against them.
Q: Should any global pandemic/event be sort of a heads up for Cyber Security teams as malware authors will definitely try to exploit the situation & also people’s tenderness to access more information?
A: Absolutely. Any large event. Before this it was the Olympics, the World Cup, hurricanes, earthquakes, you name it. If the world is paying attention it will be exploited.
If you were unable to attend the webinar, or wish to watch it on-demand, it is available to stream at your convenience.




