No Blocking, No Issue: The Curious Ecosystem of Financial Advisor Impersonation Scams
Introduction
An increasingly common and highly effective fraud technique known as “pig butchering” uses a complex web of social engineering techniques to defraud victims. These scams rely on slowly building trust with a target–often under the guise of a financial advisor or successful investor–in order to convince targets to invest in a scam, such as a cryptocurrency “investment,” in which their funds are promptly stolen and rendered nearly impossible to recover.
Profitable cybercrime methods are rarely limited by geography, and other researchers have observed “pig butchering” activity in Southeast Asia. DomainTools Research is tracking a cluster of similar but likely unrelated activity with a significant West African presence. A subset of this appears to be the wholesale impersonation of financial advisors with a closely aligned underground economy supporting such activities. These scams appear to share orbits with what is likely a well-concealed bulletproof host operating out of West Africa.
This piece explores a specific advisor impersonation campaign, both through the lens of tactics as well as the technical infrastructure providers that enable these scams to flourish. Because of privacy concerns for those being impersonated, financial advisor names, domains containing legal names, contact information, photographs, and the associated financial institutions these advisors represent have been excluded or redacted.
This Financial Advisor Impersonation Campaign, A Form of “Pig Butchering”
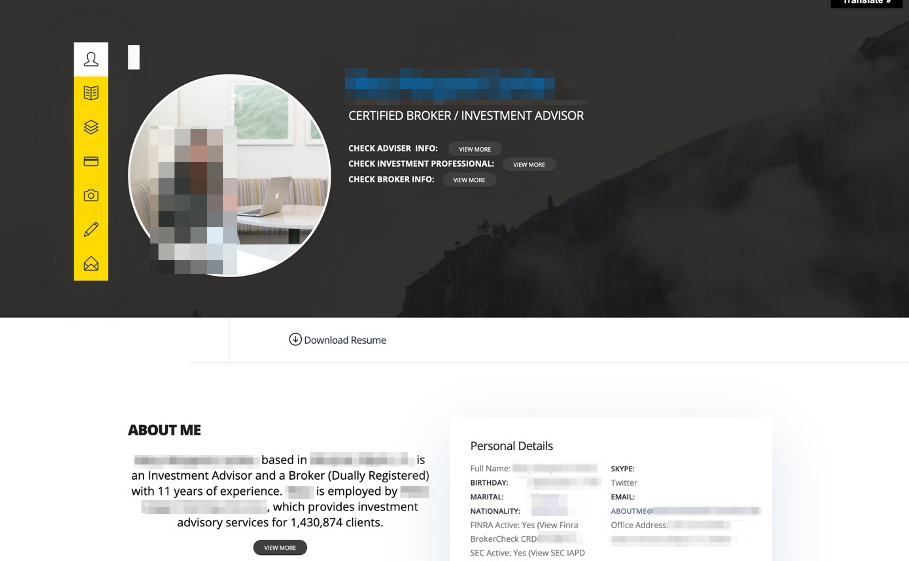
To date, this financial impersonation campaign has targeted several hundred financial advisors, each with a malicious domain and website deployed at one point. For example, Figure 1 above contains a redacted screenshot of one of the more popular financial advisor impersonation templates favored by this campaign. Much of this activity uses professional network services like LinkedIn to identify, research, and contact potential victims.
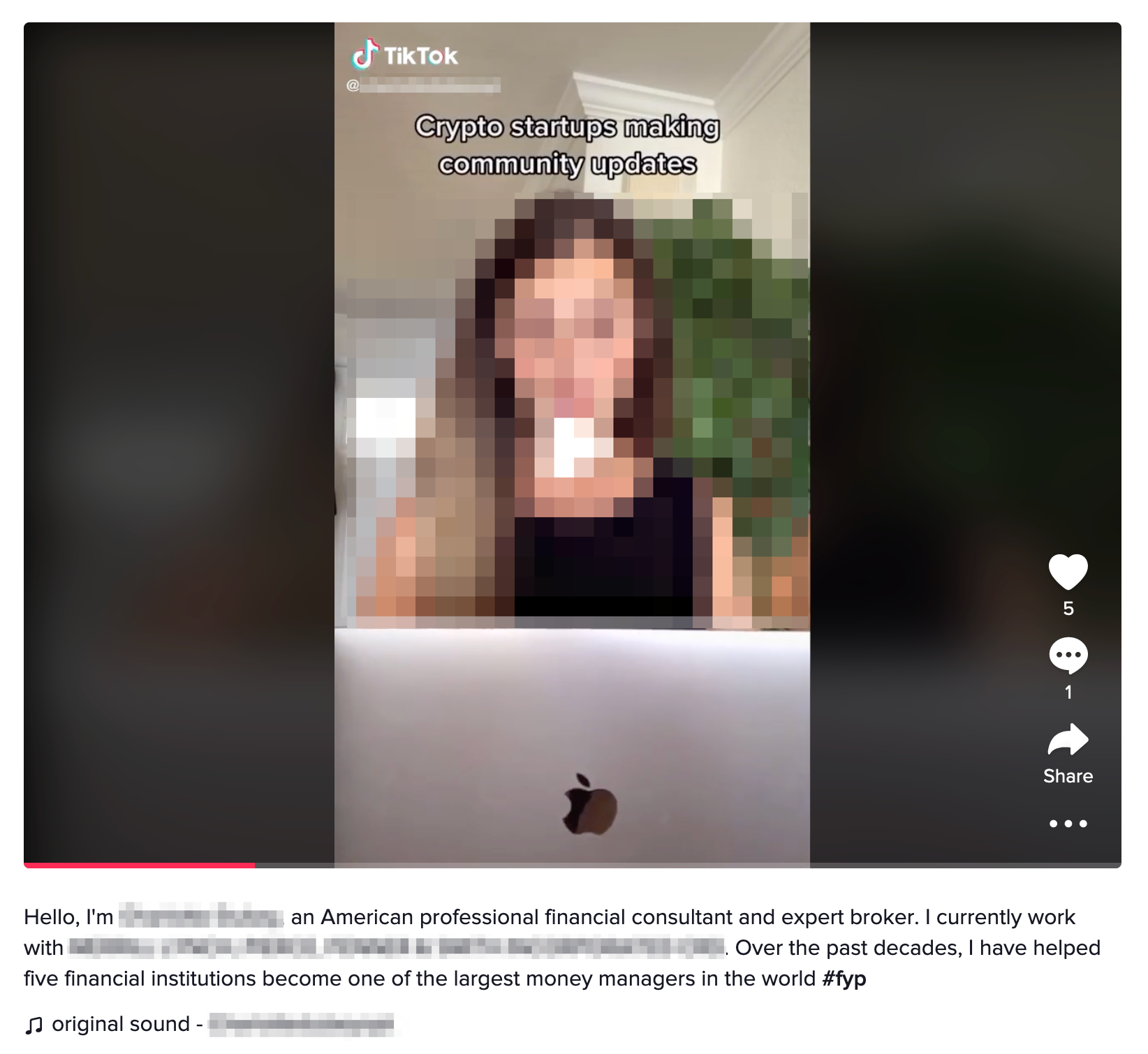
Notably, fraud actors associated with this campaign frequent social media platforms like TikTok and Instagram. Figure 2 shows a screenshot of a TikTok video promoting a financial advisor impersonation account that claims to be “an American professional financial consultant and expert broker” that “helped five financial institutions become one of the largest money managers in the world.” In this example, both the financial advisor and the TikTok influencer had their likenesses stolen for this campaign. This approach for contacting targets is often more difficult to detect, especially on platforms where target groups likely unfamiliar with such scams gather.
Financial Advisor Impersonation Methods in Practice
Whether a scam succeeds often depends on psychology and whether social engineering techniques successfully bypass a target’s innate skepticism. Financial advisor impersonation is especially dangerous because of the trust relationship that exists between advisors and their clients. This perception extends beyond an advisor-client relationship and into the public’s broader perception that financial advisors are competent professionals.
Financial advisor impersonation is straightforward conceptually, but simplicity in subject belies complexity in practice. Financial impersonation scams require careful, layered deception involving significant interaction with a target to succeed. To that point, engagements as prospective clients with several financial advisor impersonators suggest they possess a competent understanding of financial markets.
Financial institutions would be wise not to underestimate threat actors specializing in this type of impersonation fraud.
Scam Components
In practice, these are the steps that the impersonators used to execute their scam.
- Select financial advisor targets from United States government publicly available advisor certification records. Supplement gleaned public records with biographical data from sources like employer websites, professional histories on LinkedIn, and social media accounts.
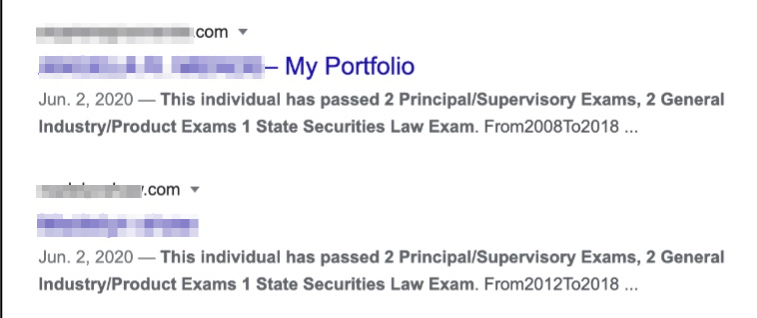
Content on many of these impersonation pages appears to be scraped verbatim from reports published on FINRA’s BrokerCheck and the SEC’s Investment Adviser Public Disclosure websites. Regulatory agencies offer certification data that can easily be supplemented with basic OSINT techniques. Figures 3, 4, and 5 show the overlap between impersonation website content and regulatory documents published by FINRA and/or the SEC.
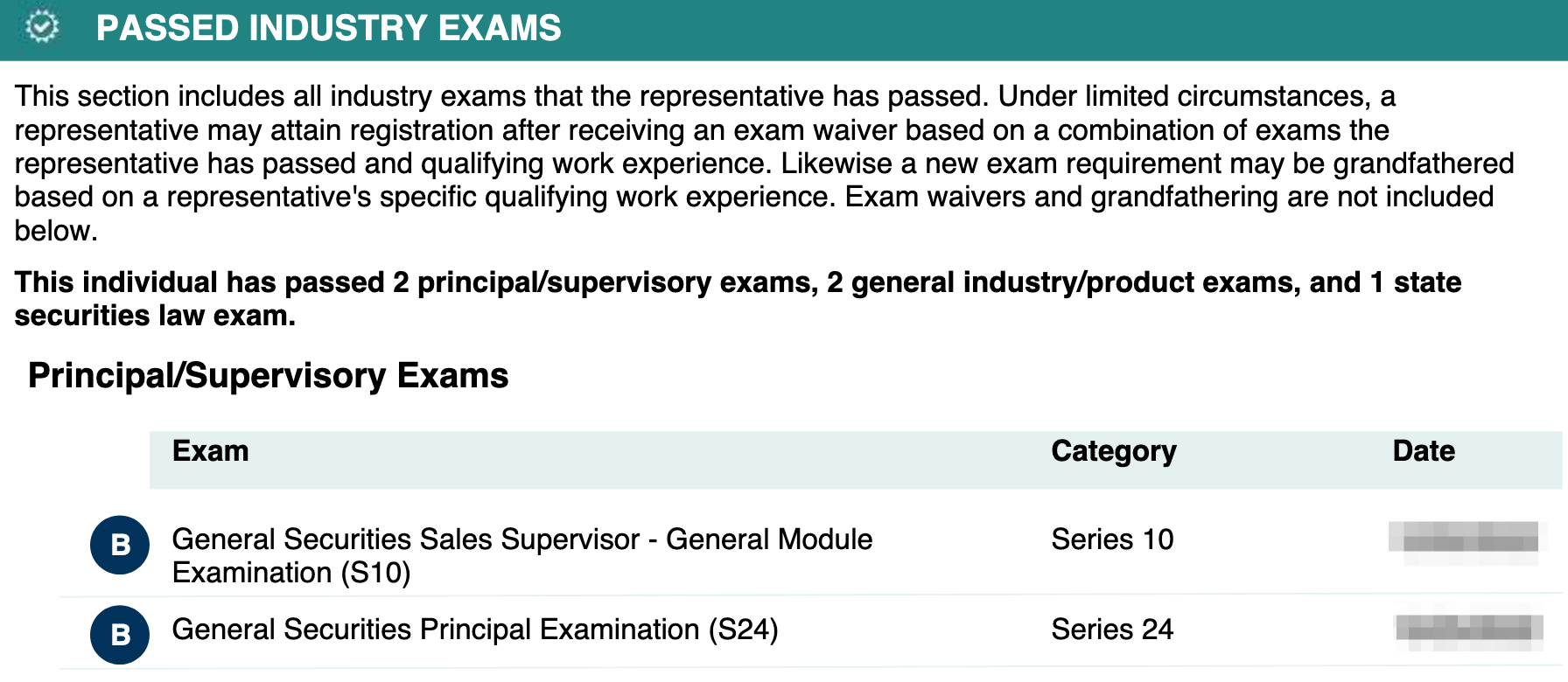
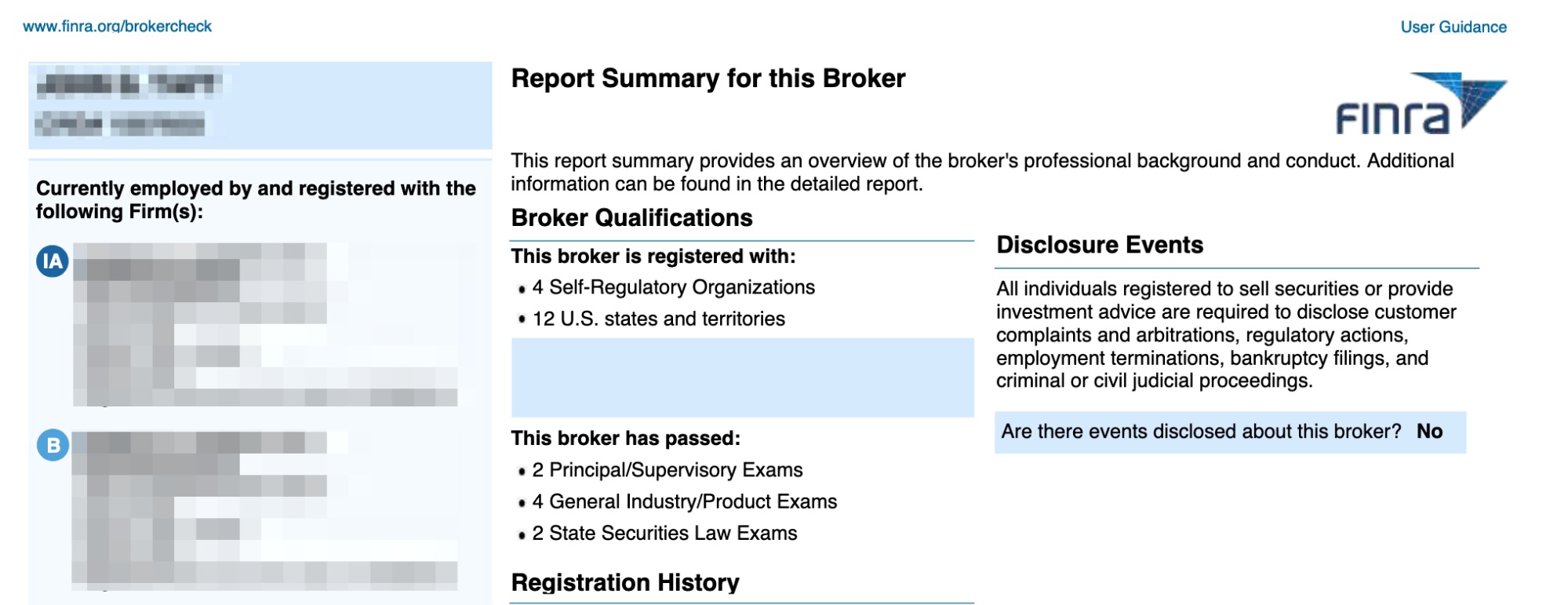
- Acquire financial advisor impersonation website templates on “nulled” marketplaces and communities. Use the scraped and enriched biographical data as content to create new advisor impersonation websites.

Financial advisor impersonation websites associated with this campaign rely on a relatively small set of templates. Threat actors associated with this campaign frequently used PreRaid, a now-defunct service offering “nulled” (pirated) WordPress themes and related products, many of which were modified into financial advisor impersonation websites and fraudulent cryptocurrency investment funds (see Figure 6). These impersonation websites are likely packaged and shared in a manner not unlike phishing kits.
Figure 7 includes the description of a PreRaid template named “Maxprofit” frequently used in cryptocurrency scams closely aligned with this impersonation campaign.

- Deploy impersonation websites, preferably with a “bulletproof” host, one that claims to be DMCA non-compliant or caters specifically to financial advisor impersonation campaigns.
Given the complexity of manipulating a target when impersonating a financial advisor, impersonation websites must remain accessible for as long as possible. Therefore, the selection of a hosting provider is critical to the success of this scam. This report explores this point in detail in the next section, using a particularly suspicious hosting provider as an example.
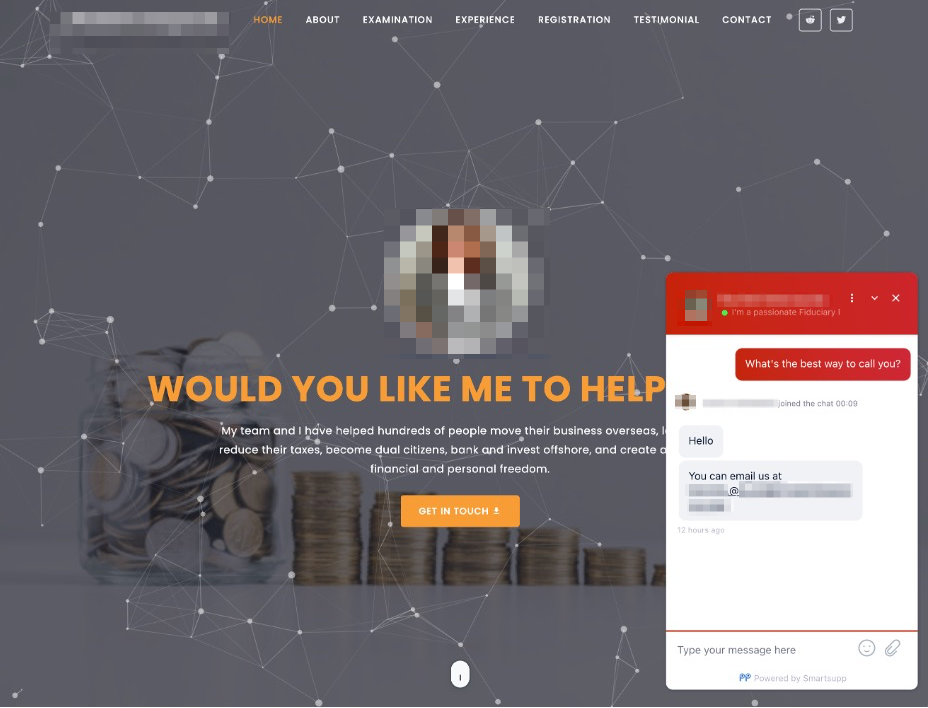
- Enable multiple communications channels with potential victims, including live chat serving as an inbound “sales” apparatus and a secondary purpose of convincing a targeted person that the person interacting with them is legitimate.
Many of these impersonation websites have live chat widgets, allowing potential victims to interact with the impersonated financial advisor immediately. The advisor is often very hesitant to speak over the telephone, instead preferring WhatsApp or email for future correspondence. This allows the impersonator to control the tempo of the engagement. Figure 8 shows such a live chat widget with a request to continue the conversation over email.
Bulletproof Hosting Providers for Financial Advisor Impersonation Websites
“Bulletproof” hosting services lack any substantive internal processes to detect and suspend malicious content since malicious content is often the very purpose of their service. In short, bulletproof hosts are incentivized not to act. These hosts themselves run a gamut of capabilities and risk tolerances. Some maintain physical control over the servers they host on. Others merely resell the services of legitimate companies and only serve to slow-roll or ignore takedown requests until those requests escalate to the infrastructure provider. The latter appears to be the case for a specific hosting provider tied to this impersonation scam.
Investigation into a Bulletproof Provider
A considerable amount of financial advisor impersonation activity associated with the campaign in question overlapped with a hosting provider named SpeedHost247, the domain speedhost247[.]com, and its respective online footprint. SpeedHost247 claims to be a web hosting provider based in Ontario, Canada. A deeper analysis of the information provided on their website suggests otherwise, including concerns about phone numbers, pictures, and their address.
SpeedHost247 lists two phone numbers: the first has a Florida area code, the second has the +234 country code for Nigeria (Figure 9).
Figure 10 shows that SpeedHost247’s website includes a photograph of a mid-rise office building bearing their company’s logo. This photograph appears to be a doctored image of a real building. Figure 10 is an unmodified photograph showing the actual building located in Madison, Alabama, named “Airport Office Center.”


SpeedHost247’s Ontario business address raises just as many questions as its office building photograph. The address provided appears to belong to Aramex, a global shipping and logistics company. Figures 11 and 12 show the front and back of the actual buildings at this address, located in an industrial area of Mississauga, Ontario.


To continue with the questionable images, a photograph of SpeedHost247’s office interior appears to be an altered and rebranded photograph from inside Rackspace’s UK office (Figures 14 and 15):


Curious, DomainTools Research began a chat with a SpeedHost247 about their services whilst posing as a prospective customer running a generic “financial service.” The results were surprising. Included below are pertinent sections of that conversation, copied verbatim with redactions of personal information.
> SpeedHost247: How May I Help You Today Please :)
> Researcher: Hi [redacted] what can I host here? My company offers financial service.
> SpeedHost247: Anything depends on the type You want to host i will give You Best Plan
> SpeedHost247: Real financial service.?
> SpeedHost247: Or just financial service.?
> SpeedHost247: :)
> Researcher: :)
> Researcher: Just financial service
> SpeedHost247: Nice
> SpeedHost247: I got it
> Researcher: So all good?
> SpeedHost247: Yes all good
> SpeedHost247: It will cost 85$ monthly
> SpeedHost247: No blocking no issue
> SpeedHost247: No suspension
[break]
> Researcher: What are whois requirements?
> SpeedHost247: Use any information
> SpeedHost247: Fake information please
> Researcher: Good good
> SpeedHost247: Correct email though so you can receive email from us
[break]
> SpeedHost247: Fully protection and zero information on Whois
> SpeedHost247: Welcome
> Researcher: Good good
[break]
> SpeedHost247: Send Payment to BITCOIN: [wallet address redacted]
Things are not always as they appear to be, especially on the internet. Whether SpeedHost247 is an active participant in financial advisor impersonation scams remains an open question, but their seeming willingness to accommodate dubious customers offering even more dubious financial services using false information is reason for pause.
Conclusions
This specific “pig butchering” scam is being perpetrated by a West African group impersonating American financial advisors. They scraped advisor information from several online sources and used “nulled” website templates hosted by “bulletproof” hosters such as SpeedHost247 to execute their campaign. They advertised on several platforms, including TikTok. Finally, they used real-time website chat, email, and WhatsApp chats to engage with their victims and convince them to invest in cryptocurrency “investments” which lead to notable losses.
With one impersonation campaign targeting hundreds of wealth management professionals across several global financial institutions and hosting providers seemingly happy to facilitate this, we urge financial institutions offering advisory services and prospective clients to take the growing threat of financial advisor impersonation seriously.
Prospective clients would be wise to contact financial advisors through their respective financial institution’s official website and insist on speaking with them over the telephone, preferably in a video call. Consumers would also be wise to approach any cryptocurrency investment with extreme caution and avoid nontraditional investments with “guaranteed” rates of return. Investment opportunities that seem too good to be true probably are.
For financial institutions facing impersonation campaigns, understanding how domains and hosts relate–and supplementing that data with context from researchers–can provide invaluable insight, whether the organization you seek to protect operates in the financial services industry or not.
Domains and hosts are indeed not always as they seem. Thankfully, DomainTools has the data sets and critical eye to see through the smokescreen.