Part 2: Tracking LummaC2 Infrastructure
Share this entry
LummaC2 Malware Campaign: Background and Initial Findings
In a previous blog, we analyzed domains associated with the recently-disrupted LummaC2 infostealing-malware (although there are now reports that a new infostealer known as Acreed has come to take its place). From 114 initial domains published by the FBI and CISA, we observed distinct registration patterns such as the use of Eastern European names that appeared to reference prominent Russian individuals.
A recurring detail stood out: many of these names were associated with registrant email addresses using the domain inbox[.]eu. This observation prompted a deeper investigation, hence the part 2 you’re reading now.
What we found was a much broader campaign consisting of nearly 500 domains that not only share similar registration traits, but also promote the same service: technical education courses. Despite appearances, these domains are scored as highly malicious, raising eyebrows about their true intent and – given how we got here – their possible associations with LummaC2.
Domain Registration Patterns
To expand on our original dataset, we pivoted from the 114 FBI and CISA-released domains by focusing on a key indicator: the email domain inbox[.]eu. We filtered for domains that met the following criteria:
- Contain inbox[.]eu in the registrant email
- Were active and observed after November 1, 2024
- Use cloudflare[.]com as the name server
This simple yet effective query surfaced 499 domains which had an average Risk Score of 98 – a strong indicator of malicious activity. Other domain registration patterns included:
| Mail Server Hostnames: titan[.]email hostinger[.]com | Whois Registrant Email Domains: inbox[.]eu |
| Server Types: Cloudflare nginx | Top TLDs: run live top com pro |
Many of these domains also used Eastern European names – a trend we observed in the original 114. As with that original set, some names appear to reference well-known Russian figures, including actors and athletes.
Email Address Reuse
Among the 499 domains, we identified 256 unique email addresses, many of which contain Eastern European names, use the inbox[.]eu domain, and are linked to multiple high-risk domains (Risk Score 90+). A full list of the email addresses is provided in the GitHub link at the end of this article, but below are listed those addresses associated with the most domains:
- iajds89ajsd[@]inbox[.]eu
- timur_pozniakov16[@]inbox[.]eu
- olga_savina1[@]inbox[.]eu
- macaronnen29[@]inbox[.]eu
- abjush1i[@]inbox[.]eu
- ivan_lukin15[@]inbox[.]eu
- margarita_maslowa10[@]inbox[.]eu
- abram_belkin17[@]inbox[.]eu
- emilia_holubeva7[@]inbox[.]eu
- alisa_stankevicheva3[@]inbox[.]eu
Technical Training: A Consistent Lure
Despite the large number of domains, many feature a common theme – technical education and skills training. The sites advertise a wide range of courses in areas like coding, 3D modeling, game development through tools such as Unreal Engine, financial analysis, web design, AI usage, and many more. Courses are often offered in multiple tiers – sometimes referred to as “tariffs” – with varying levels of access and pricing.

Screenshot Timestamp: 2024-12-13 | 7:45 AM UTC
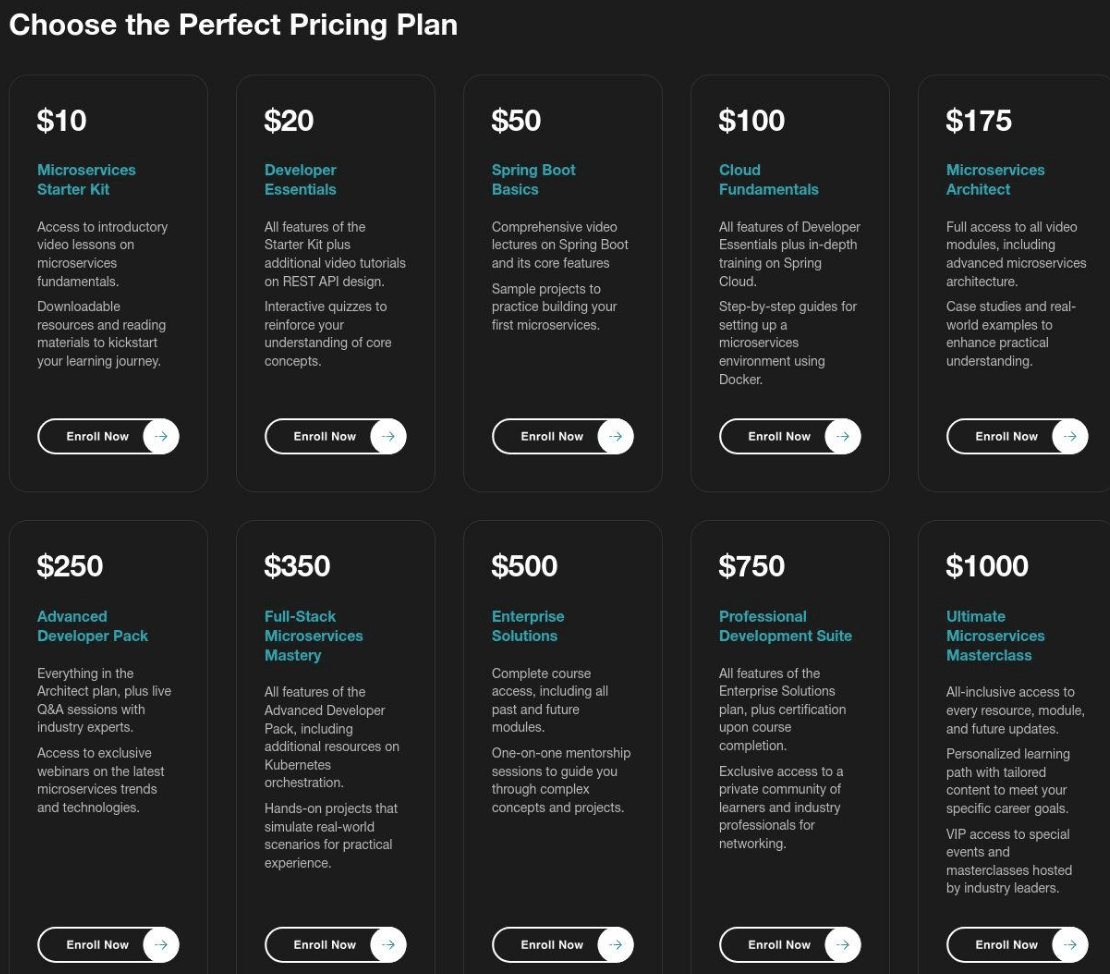
Screenshot Timestamp: 2024-12-11 | 8:42 AM UTC
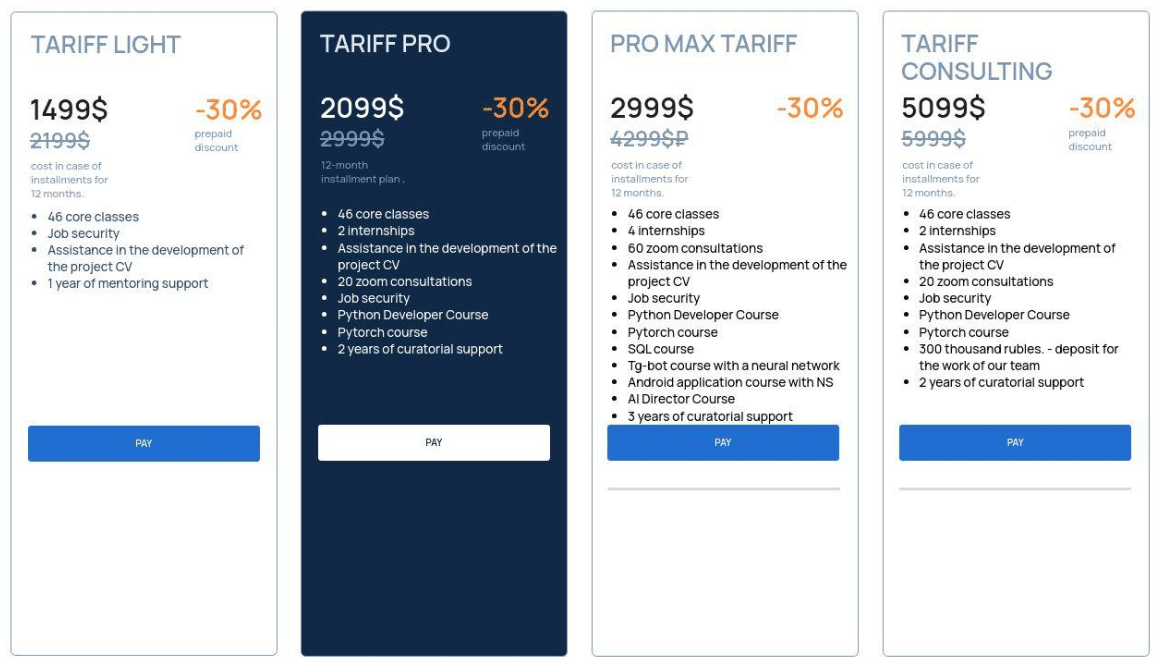
Screenshot Timestamp: 2025-04-22 | 7:51 PM UTC
Despite visual differences, the landing pages follow a similar structure, often including:
- A company description and mission statement
- The promise of career advancement
- One-on-one mentorship and personal consultations
- User testimonials and success stories
- Descriptions of each course module
- Featured instructors
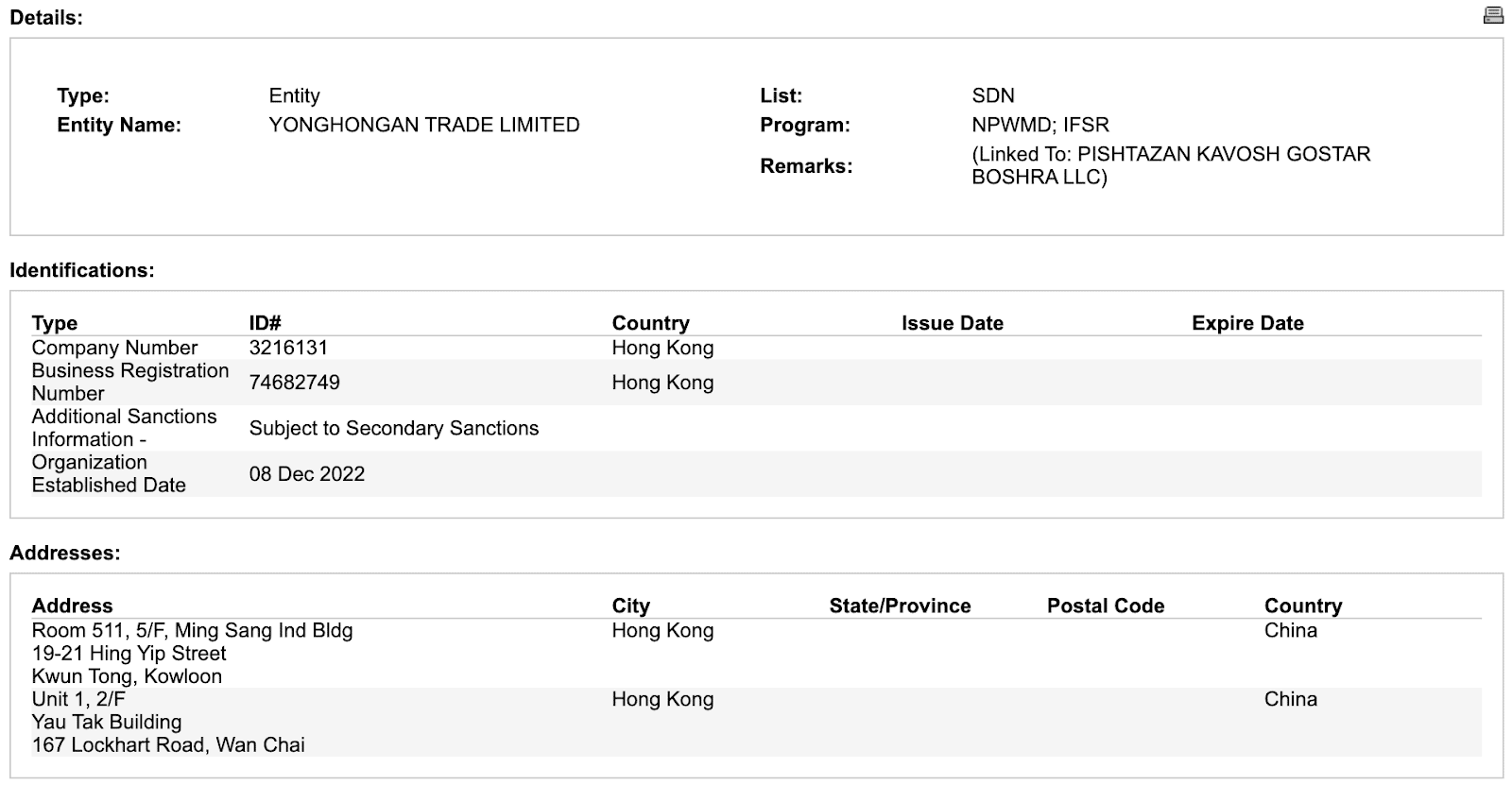
- The listed address ROOM 511, 5/F, MING SANG IND BLDG, 19-21 HING YIP STREET, Kwun Tong Hong Kong
The above address is notable as it appears on the US Office of Foreign Assets Control (OFAC) Sanctions List. OFAC associates it with the entity Yonghongan Trade Limited, which is further linked to Pishtazan Kavosh Gostar Boshra, LLC – a sanctioned Iranian entity identified by the US Treasury as a key player in a procurement network supporting Iranian military organizations, including the Islamic Revolutionary Guard Corps (IRGC).
Sample Malicious Domains and Risk Scores
Below is a selection of domains from the 499 identified in our investigation, each of which advertise the aforementioned technical training courses.
| Domain Name: 3dpaintexpert[.]pro Risk Score: 91 Create Date: 2024-11-20 |
| Domain Name: aipracticexpert[.]pro Risk Score: 90 Create Date: 2024-11-24 |
| Domain Name: analystproedu[.]online Risk Score: 96 Create Date: 2024-11-24 |
| Domain Name: chiefexcelnow[.]com Risk Score: 97 Create Date: 2025-01-15 |
| Domain Name: codehorizonschool[.]online Risk Score: 96 Create Date: 2024-12-02 |
| Domain Name: financemodeling[.]pro Risk Score: 96 Create Date: 2024-11-24 |
| Domain Name: gamedesignerscourse[.]online Risk Score: 94 Create Date: 2024-12-08 |
| Domain Name: jsdatacraft[.]pro Risk Score: 97 Create Date: 2025-01-15 |
| Domain Name: learn-csharp[.]com Risk Score: 96 Create Date: 2025-01-15 |
| Domain Name: metricsandmore[.]com Risk Score: 95 Create Date: 2025-01-15 |
| Domain Name: pythonexpertcourse[.]pro Risk Score: 95 Create Date: 2024-11-24 |
| Domain Name: quick-laravel[.]online Risk Score: 96 Create Date: 2025-01-15 |
| Domain Name: realistic-3d[.]pro Risk Score: 95 Create Date: 2024-11-19 |
| Domain Name: softwaretester[.]pro Risk Score: 96 Create Date: 2024-11-13 |
| Domain Name: ssistraininghub[.]com Risk Score: 88 Create Date: 2024-11-19 |
| Domain Name: textstoapps[.]online Risk Score: 98 Create Date: 2025-01-15 |
| Domain Name: unrealdevelopercourse[.]com Risk Score: 93 Create Date: 2024-11-24 |
| Domain Name: webfrontendeveloper[.]online Risk Score: 96 Create Date: 2024-11-24 |
As stated, a large portion of these 499 domains have a similar landing page structure which often features the supposed individuals behind the organizations. While many of these names are conventionally Western (Lucas, Sarah, Michael), others sound like they’re straight out of a Hunger Games novel:
Screenshot Timestamp: 2025-06-10 | 7:31 PM UTC
Screenshot Timestamp: 2024-12-12 | 6:48 PM UTC
Screenshot Timestamp: 2024-12-07 | 4:48 AM UTC
Although several of the sites appear well-constructed and professional, details like this point to the false nature of these alleged training organizations.
LummaC2 Panels
Among the 499 domains, four stand out for a different reason: they appear to be LummaC2 login panels. These domains include:
- anna-akhmatova[.]com
- iosif-brodskiy[.]com
- yuriy-andropov[.]com
- zestmedo[.]top
The names within the first three domains reference prominent Russian poets and politicians, echoing the naming pattern observed in the original FBI/CISA list. Below is an image of the panel, which is identical across the four domains:
Screenshot Timestamp: 2025-05-14 | 4:35 PM UTC
The presence of these panels is consistent with details outlined in the US DOJ’s press release on the LummaC2 disruption, which described how buyers and administrators accessed the malware through dedicated login portals.
Practical Takeaways for Security Teams
The domains uncovered in this investigation present a clear pattern: a coordinated campaign leveraging the appearance of technical education platforms. The overlap with known LummaC2 infrastructure, along with the discovery of the four control panel domains – suggests that these sites are simply lures to deliver malware (LummaC2 or otherwise) to unsuspecting users.
Now that we’re acquainted with this threat, here are some suggestions on how to better protect yourself and your organization:
- Monitor for Similar Infrastructure
- Watch for domains (especially young ones) using:
- The inbox[.]eu email domain in Whois/RDAP data
- TLDs like .pro, .online., and .top along with terms such as “training,” “expert,” and “course”
- Eastern European names, particularly those belonging to notable individuals and containing a “-” in between the first and last name
- Watch for domains (especially young ones) using:
- Inspect Suspicious Training Sites:
- Scrutinize new or unknown training platforms before allowing access
- Look for red flags like:
- Pricing packages referred to as “tariffs”
- Vague instructor bios
- Fantastical-sounding mentor names
- The Hong Kong address linked to OFAC-sanctioned entities
- Educate End Users
- Alert employees about the risks of downloading tools or enrolling in courses from unknown providers
- Spread awareness of approved training and continuing education resources
Lastly, we recommend checking out the full domain list and adding these sites to your blocklist. If you’ve got any additional insights or see something interesting, let us know – we’d love to hear from you.
Special thanks to our very own Ian Campbell for his helpful contributions to this piece.
IOCs on GitHub
https://github.com/DomainTools/SecuritySnacks/blob/main/2025/LummaC2-Domains-Continued.csv
Appendix
The below search hash can be copied and pasted into Iris Investigate to view the results detailed above.
U2FsdGVkX1+yZfE77PWNPBXzeCRdHIOUN/fq6neNrPGVlvoFkXs/qnyHfTNwYlkXWukcLsvuu0QTf2R6CJOQO4MBsesDmDofIkUsTKxkcSzVx7TnzJsxdEmGc999ii6fo3FcDvkYB9xC5mW0Nd8zq8W1RThuoo3lj+FsZKokm5liyOfIYzEjZ4Dhu9pykAfaqkF8QeXAE8WpK+mLG+EFhXeZacDmU43TXnzwx78UPN9bBt4AlFUzZ2PRRT1IgjBfcio6xN0MNcOHVbYbos1qDopBIsmjOXo7T2nsEoa/Jhg=





