London, UK, May 23, 2017 – DomainTools, the leader in domain name and DNS-based cyber threat intelligence, today released their 2017 DomainTools Report, looking at the various “hotspots” of malicious or abusive activity across the internet. The report examines four domain characteristics: generic Top Level Domains, Whois privacy provider, free email provider and IP geolocation.
The DomainTools research team analysed the generic top level domains (gTLDs) with the highest concentrations of malicious activity. Their research found that .science had the highest concentration of bad domains, followed by .study and .racing. None of the 2017 most malicious Top Level Domains were in meaningful operation in 2015.
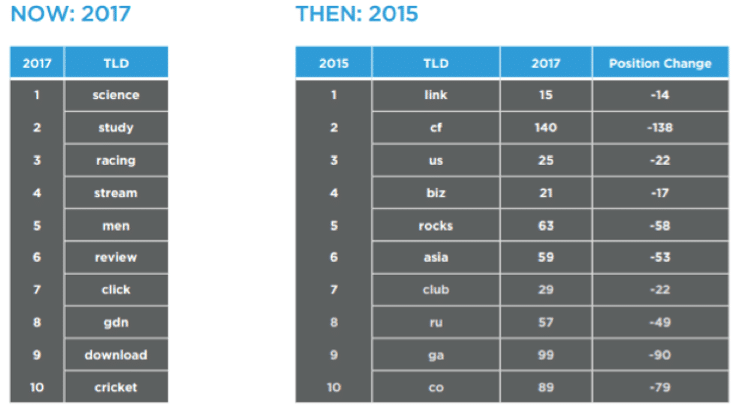
Tim Helming, Director of Product Management at DomainTools said: “We expect a lot of churn for the foreseeable future as the Top Level Domain space continues to expand, but that should not stop investigators from paying attention to the top ten from this year.” Helming clarified that these TLDs are not inherently malicious, as single registrants can be responsible for the vast majority of nefarious domains. “It is worth noting that in .science, of the 230,000 domains in the TLD, over 144,000 (63%) have been added to industry blocklists and even more noteworthy, perhaps, is that the blocklisted domains in .science are dominated by a single registrant. Similarly, the blocklisted domains in the .racing TLD are also largely the work of a single registrant entity.”
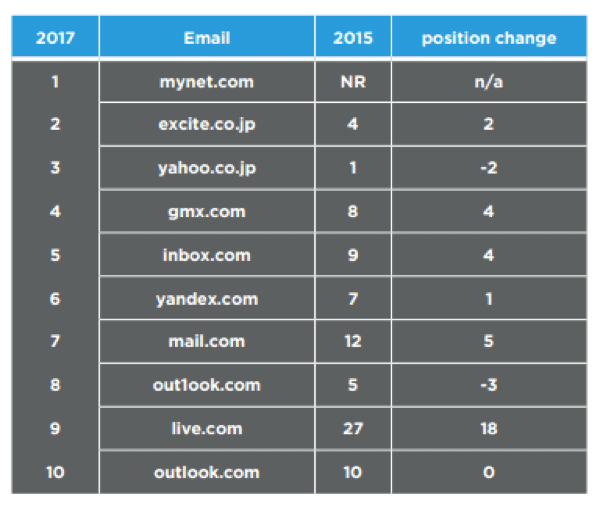
The DomainTools team was also able to identify which email providers, based on registrant contact information contained in Whois records, had the highest concentrations of malicious domains and mynet.com was at the top of the list. This list also included Microsoft mail providers live.com and outlook.com. “Mynet.com went from being completely absent in 2015 all the way to the dubious distinction of top slot this year, and live.com showed a significant increase in the rates of unsavory domains linked to it” continued Helming. “While it bears repeating that the use of any of these providers is not proof that a domain is dangerous, many of the actual concentrations are extremely high. Only one of the top ten had a lower than 10% incidence of observed bad activity among the domains connected to it.”
The full research is available on the DomainTools blog: https://blog.domaintools.com/2017/05/the-domaintools-report-spring-2017/
About DomainTools
DomainTools helps security analysts turn threat data into threat intelligence. We take indicators from your network, including domains and IPs, and connect them with nearly every active domain on the Internet. Those connections inform risk assessments, help profile attackers, guide online fraud investigations, and map cyber activity to attacker infrastructure. Fortune 1000 companies, global government agencies, and leading security solution vendors use the DomainTools platform as a critical ingredient in their threat investigation and mitigation work. Learn more about how to connect the dots on malicious activity at https://www.domaintools.com or follow us on Twitter:@domaintools
