Building your IR Plan Step-by-Step

In our Cyber Incident Response series, we’ve discussed the meaning of Cyber IR, the importance of it, why you need it, and the different team-building aspects. Here in the third blog post of the series, we’ll discuss building your IR plan.
The Gang’s All Here
Now that the team is in place, it’s time to build out your IR plan. Remember, a strong IR plan helps you to both prepare and prevent security incidents. But other positive effects of having a plan in place are numerous. The obvious benefits are that it can reduce cost and data protection. The most important, however, may be the reinforcement of your organization’s (positive) reputation, as an IR plan shows an organization’s commitment to security, and the privacy of its customers.
Now, let’s break it down!
The Six Steps of Incident Response
There are six steps that should be taken by the IR team in order to effectively handle security incidents. These six steps were developed by the SANS Institute and outlined in their Incident Handlers Handbook. Your IR plan should provide a well-defined process for each of these six steps. [NOTE: The NIST also provides an incident response outline, but composed of three models.]
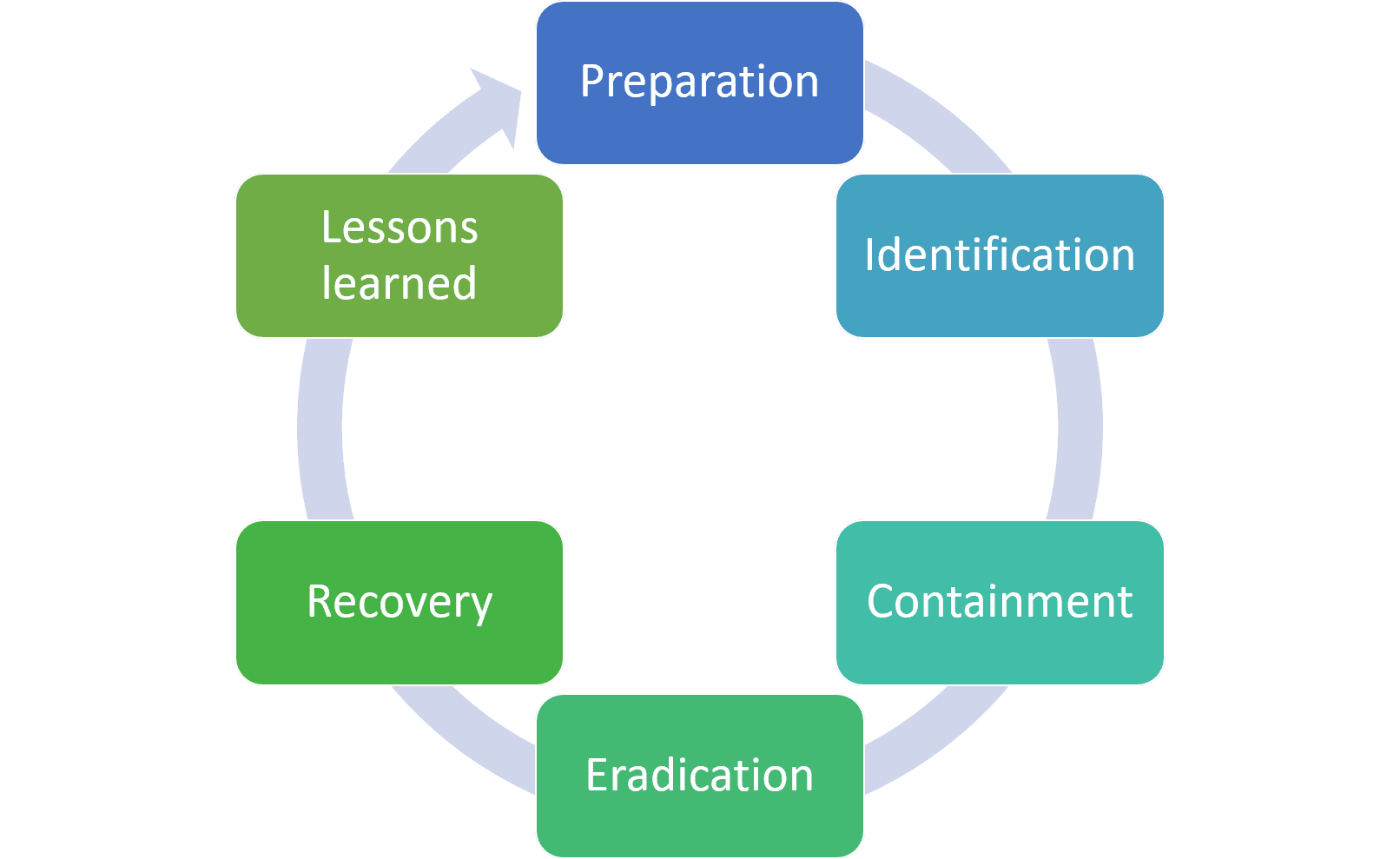
In each of these stages, there are a few items that you want to ensure you get right!
Stage 1: Preparation
The preparation phase is about making sure you have the proper response plans, policies, and other documents in place—in essence, you want to have the tools and training before an incident happens. You also want to ensure that you have identified the members of your IR team, including external stakeholders.
Stage 2: Identification
In the identification phase, you will need to discover whether you are dealing with an incident or an event, or a false alarm. This is the point where you must truly understand your environment—as you must be able to find and recognize deviations from normal baselines.
Stage 3: Containment
The containment stage is the most collaborative stage, in terms of your organization. As you head into this stage, you must work closely with other areas of your organization in order to limit the damage to the systems and further prevent additional damage from occurring. This is where you stop the event or incident, and gain control over where it could travel within your network. Containment could include blocking access at a firewall, rescinding user accounts, or updating antivirus rules
Step 4: Eradication
In the eradication phase, the IR team is ensuring the system is clean and ready to restore. You are getting rid of the malicious code or malware, unauthorized account, or in some instances, an employee that caused the incident.
Step 5: Recovery
You’re almost there! In Step 5: Recovery, the team decides when to bring the system back up, ensuring it meets company baselines and standards. At this point, the team also sets in place the monitoring timeline (how long the team will monitor the new system to confirm the incident has been fully resolved).
Step 6: Lessons Learned
This is the ‘postmortem’ stage. Oftentimes, an IR team will skip this final step; however, it’s imperative that you do not! As your organization moves back to normal operations, the IR team must reflect on lessons learned. You should compose a report detailing what happened, why it happened, how it could have been prevented, and how you will keep it from happening again.
Not as easy as 1-2-3
When laid out in a step-by-step format, it doesn’t seem like too difficult a task, but when it comes to protecting your organization, preparation is key. Develop and implement an Incident Response Plan. Train your team and employees on what needs to be done to both protect your organization and its employees. And remember, when it comes to cybersecurity and an IR plan, it’s all about planning ahead and having a plan of attack before it is actually necessary.


