Caught in the Act: A Phishing Expedition

Introduction
Cybercrime is everywhere. The news is filled each day with a constant drumbeat of reports detailing some kind of sophisticated attack that was carried out by unseen hackers who are located thousands of miles away. Cyber attacks are so ubiquitous that by some estimates they occur every 39 seconds. We hear about a random company’s massive data breach, spend a moment wondering if we or someone we know is a customer of the breached company, and then go on about our day. In many ways, we have become numb to the status quo. However, there are some types of attacks that shake us out of our collective stupor. These types of attacks feel personal, because they are.
Getting phished is one such attack. It causes one to second guess one’s choices with questions such as “How did we fail to recognize a fake login?,” “Have we used this username and password elsewhere?,” and “Why haven’t we been using a password manager?” Add the spectre of financial loss to these questions, and a sense of recrimination emerges that feels very personal. Even though we usually experience these feelings in isolation, research indicates that we do not suffer in silence. An American study conducted last year showed 24% of subjects admitted to having fallen for a phishing attack, and six in ten were unable to distinguish a fake Amazon login from the real one.
Who are the malicious actors that carry out phishing attacks? What do they want? What does their infrastructure look like? Where do they get their tools, and what tactics do they employ? DomainTools security researchers were able to provide some answers by analyzing the malicious infrastructure, commodity malware, and tool usage of a nascent phishing campaign that was set to target a large banking institution. Our efforts were aided in small part by the timeliness of the discovery and in great measure by the poor OPSEC practices of the scammers.
Fake Banking Login
Tesco Bank is a major financial services provider in the UK. Wholly owned by the British multinational groceries and general merchandise retailer Tesco PLC, the bank is home to 5.3 million customer accounts and holds over 15 billion GBP in customer assets. Tesco Bank also offers home and automobile insurance, further expanding its presence in the public sphere.
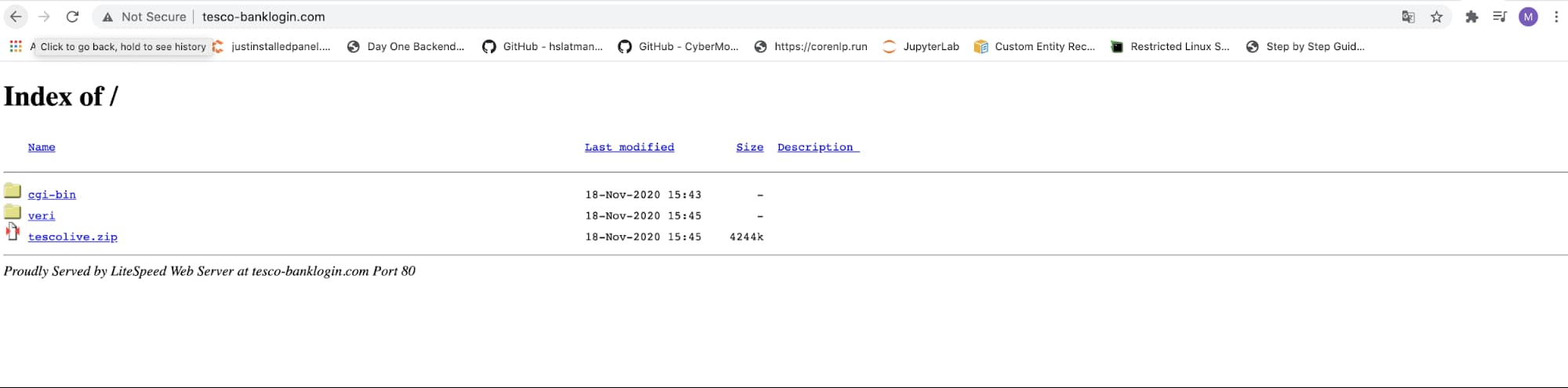
On November 18th, DomainTools security researchers noted the registration of a suspicious domain, www.tesco-banklogin[.]com. This domain piqued our interest not only due to the dubious naming convention used by the registrant, but also due to the fact that we were able to catch the domain registration on the same day that it was created. As such, we felt that this might be a prime opportunity to analyze the rollout of a phishing site in near real-time.
The domain registrar is Eranet International LTD, based in Hong Kong. The site was hosted by LLC Server v arendy, based in Moscow, RU. It utilized a free 90-day SSL certificate provided by ZeroSSL based in London, UK and Vienna, AT. Many certificate authorities now offer SSL certificates free for 90 days in an effort to compete with Let’s Encrypt’s cost-free offerings. It is important to note that DomainTools initially assigned a relatively high risk profile score of 81 (out of 99) within hours of the domain’s registration. This underscores the accuracy, timeliness, and expertise of DomainTools Machine Learning systems in carrying out threat identification. Customers who utilize DomainTools integrations with their SIEM or SOAR platform would have benefited from this timely recognition.
What did this site look like shortly after creation? DomainTools researchers were able to monitor and analyze the website as it took shape. Fortuitously, the malicious actors failed to secure the webpage stub, leaving the site open for view as it was being constructed. As denoted by the creation date of the directories, the attackers wasted no time in getting set up for their upcoming campaign.
Code Analysis
We wanted to understand the attackers’ objectives by analyzing the tools that they were employing. Therefore, we securely mirrored all of the content from the site for offline analysis. A look at tescolive[.]zip revealed that it is front end software for a phishkit consisting of commodity malware coded in Bootstrap, PHP, Angular, Javascript, and JQuery that was purposefully modified for this group of bank scammers. The PHP code was packed and minified, and then base64 encoded in an effort to obfuscate its true purpose.
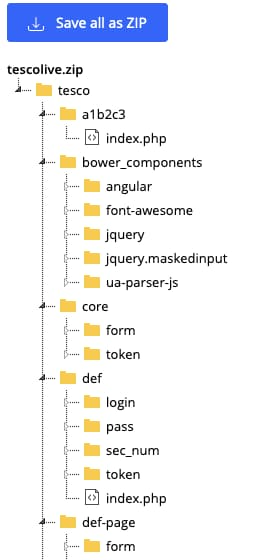
It is worth noting our luck in discovering this find. Due to exceptionally poor opsec, we found artifacts in the code that revealed that it was edited on November 9th, nine days before this domain’s registration, specifically for use against Tesco. The code was purchased on the dark web from a known .onion site. It was authored by a person or persons known as KTS Team, and thoughtfully signed for the customer, DennisBergkamp[at]jabbr.org, who appears to be a football/soccer fan and who failed to remove this particular email artifact prior to posting it to the www.tesco-banklogin[.]com domain.
<?php /*
Page made by KTS team;
http://xxxxxxxxxxxxxxxx.onion/shop/;
Edited for [email protected] on Mon 9 Nov 2020 14:21:22 EET
*/ ?-->
<!--?php>
KTS Team provided a man.txt file to its customer that served as a useful guide for our code and function analysis. The errors in spelling and grammar on this page may indicate that the author is someone whose native language is not English.
Key words;
zip = zip file you have been recived from me;
fake = cloned web pages
parent folder = folder which contain all files, after unzip ;
cfg = file "config.json" located on 'parent folder';
uadmin link = link to uAdmin panel, for reciving logs from 'fake';
step = single step with html form and inputs/fields collection, used for request information from client;
777 = permissions form specific folder/files wich mean xrw-xrw-xrw for all posable users;
uadmin = Universal admin panel
token page. = Can be known as (Live page|Intercept page). It is type of the page which can be controlled over admin panel in real time.
-After unzip 'zip' you will see 'parent folder'. Name for this folder can be changed to anything you like but it can not be removed and 'fake' MUST stay inside 'patent folder'. After all in url you can only have unique folders name.
good!:
domen.com/parentfolder/..../login
domen.com/anyname/..../login
domen.com/sgi/..../login
not good!:
domen.com/name/name/..../login
domen.com/domen/..../login
domen.com/com/..../login
domen.com/dome/..../login
-To connect 'fake' to 'uadmin' you have to edit 'home.php' file ,
OR download new 'home.php' file from already live uAdmin (no edit needed).
If you choose to edit existing 'home.php' then open 'home.php' and find line with "http(s)://{domain|ip}/uadmin/gate.php" and change {domain|ip} to your domain name or ip, where uAdmin located.
-Set '777' for 'parent folder' -R
-To access page over browser you have to open 'parent folder'
https://fakedomain.com/*/{parent_folder_name}/ where {parent_folder_name} is name of your 'parent folder'
-If page is 'token page' than after connect to 'uadmin'
-go to token page on uadmin
-find connected page with green dot
-press O-Panel on its row
-press Operations settings
-press Advanced
-empty pop up text box
-insert json-formated commands in the bottom of this text file
-press "save" on pop up box
-press "save" on current page
-go back to o-panel
after this you will be able to see commands set for current page
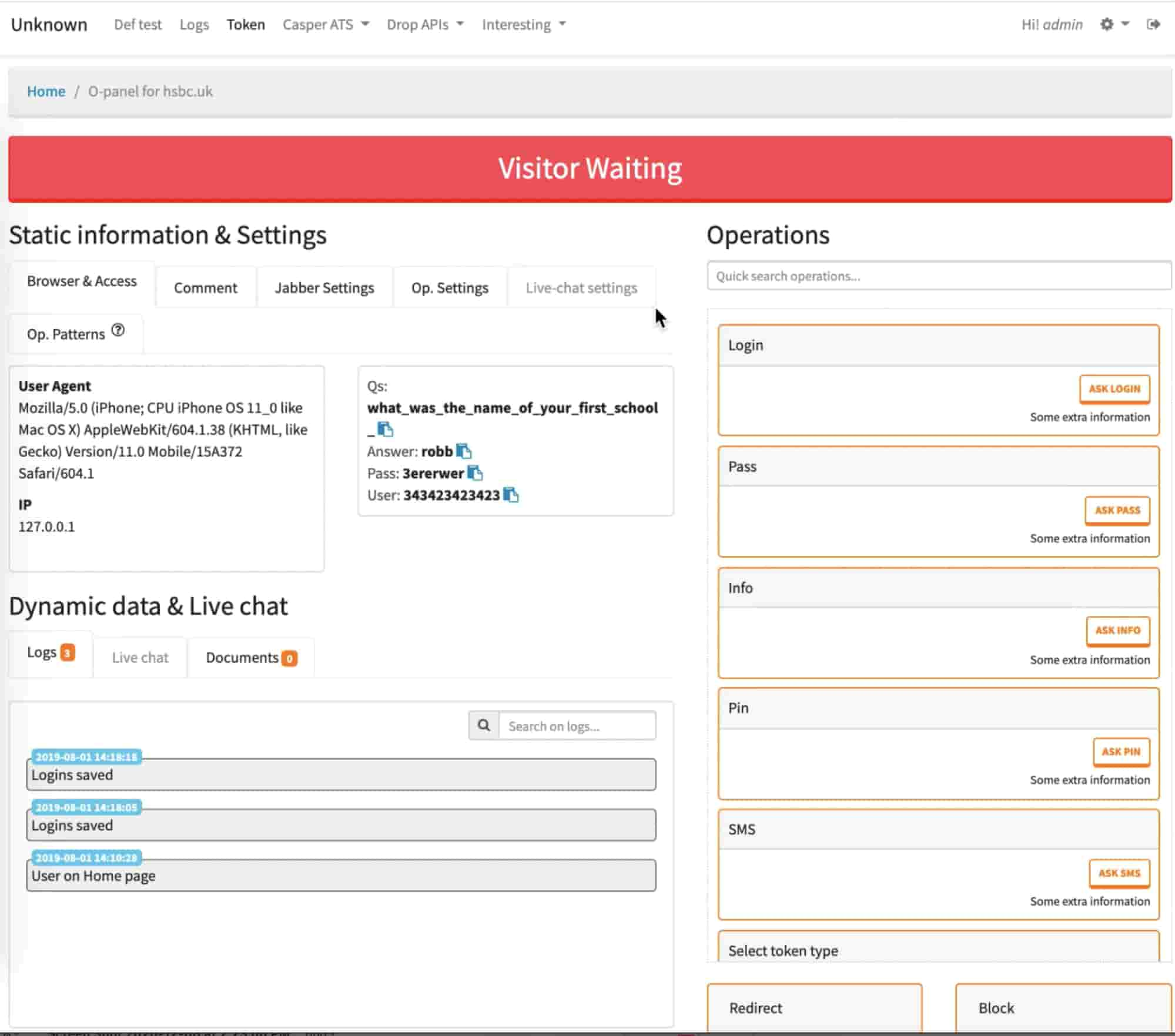
Analyzing the man.txt file, we can see that the customer receives their order in the form of a .zip file and that the file contains code that creates a single-step front-end login page that emulates a legitimate institution’s front end. The scammer is meant to utilize a subdirectory naming convention when setting up the fake front-end login screen on the “token page.” In our case, the token page URL is www.tesco-banklogin[.]com/veri/. The author of the code provides a way to connect the fake token page to a customer-controlled administrative control panel, known as “uadmin,” or the “Universal Admin Panel.” Harvested credentials or tokens are retained in a SQLite database. The admin panel allows users to customize messages that can be presented to victims on the fake login page through the use of JSON formatted commands. The following image shows the Tesco login page that is presented to a potential victim.

The fake page is virtually indistinguishable from Tesco’s true page located at https://identity.tescobank[.]com. Unsuspecting victims may be sent the fake domain URL via a phishing email or SMS text message that masquerades as a legitimate communication from Tesco Bank. Usually, these emails contain a message to the effect that the victim’s account may have an issue that can only be rectified by logging in via the link provided.
Further code analysis shows that the author included an automated notification module that notifies an attacker via the Jabber messaging app whenever a victim has entered their credentials. This is important because this type of attack can be time-sensitive. Amplifying this, DomainTools tested the site’s web server response codes via BurpSuite proxy and found that the site did not yet redirect us to Tesco’s legitimate site or any other site. It is unknown whether this feature was supposed to be added at a later time. The lack of a redirect (after credential theft) and failure to provide a legitimate log-in experience can tip off a victim that the site is fake, potentially raising figurative alarm bells. This underscores the need for a timely notification via Jabber. Upon notification, the attackers can attempt to leverage the purloined credentials to log into the victim’s true account via Tesco Bank’s online portal, set up a bank transfer, and drain the account of its funds. It is useful to note that two factor authentication may help to mitigate this form of credential reuse.
Credential theft is not the only threat posed by this Phishkit. We discovered a code artifact that seeks to install a custom APK that functions as a permanent backdoor on the victim’s device.
var php_js = {"device":{"isMobile":false,"isTablet":false,"isiOS":false,"isAndroid":false},"gets":[],"lng":"en","bb_link":"https://identity.tescobank.com/pf/adapter2adapter.ping","link": "tesco.uk","apk_file":"http://test.com/file.apk","encryption":0,"texts":"{}", "query":"","home":"../../../home.php","relative_root":"../../../","parent_folders":"a1b2c3/266c5260bde130cbd5f7f5ac3e469769/login/","fake_base":"login/"}
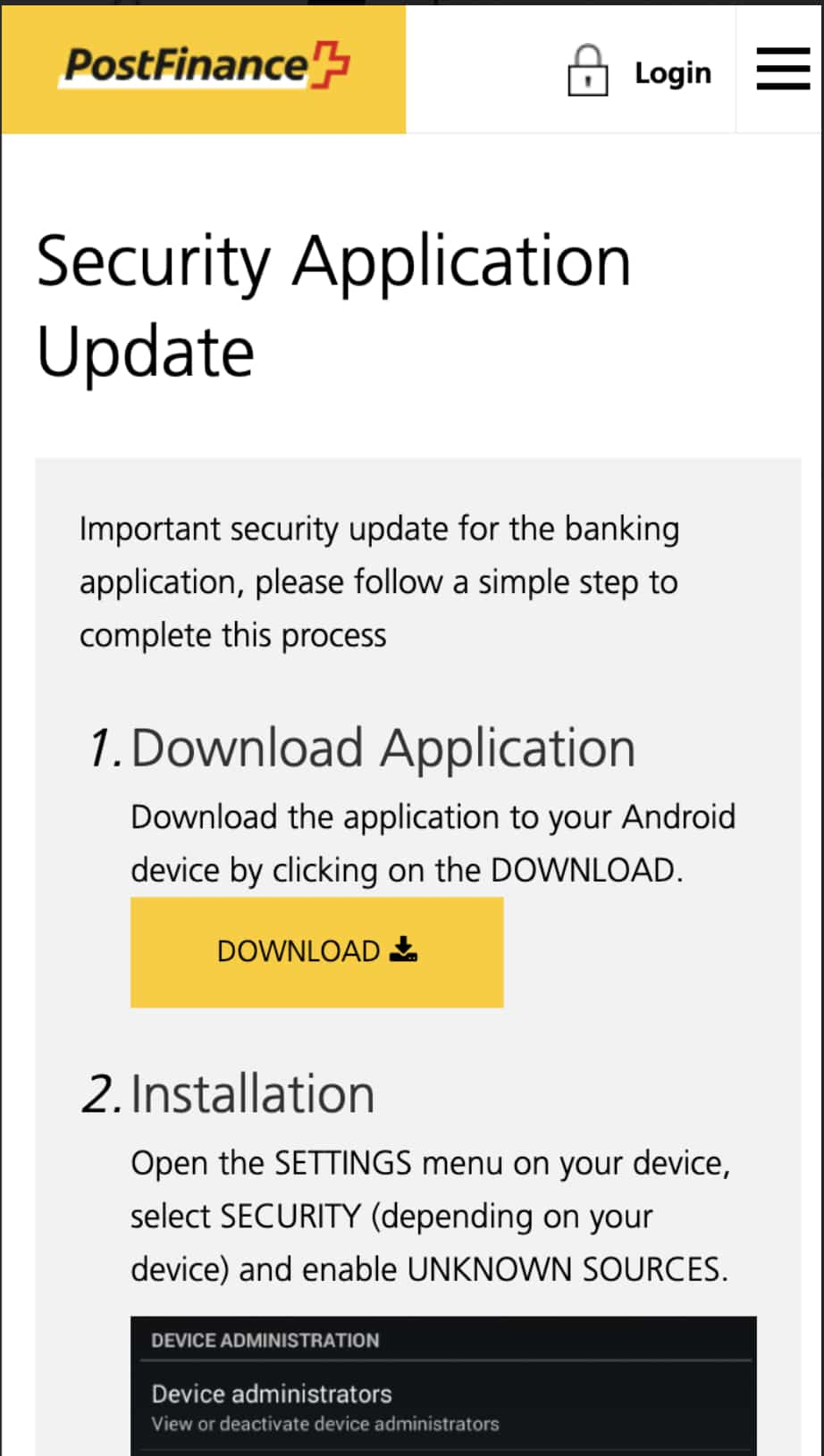
According to the phishkit’s author, the APK is capable of performing screen grabs, keyboard logging, and data exfiltration. The APK is presented to the victim as a “Security Application Update” or “Banking Security Certificate.” Links to the APK’s source are defined in a separate configuration file. Unfortunately, true source locations were never defined by the attacker before the site was blocklisted. bb_link is the URL of the real banking site. apk_file is the location of the APK source.
{
"lng": "en",
"bb_link": "https://identity.tescobank.com/pf/adapter2adapter.ping",
"link": "tesco.uk",
"apk_file": "http://test.com/file.apk",
"encryption":0
}
It is useful to call attention to a couple other features that were designed to mitigate anti-phishing efforts. We identified a .php file that is used for fast flux functionality.
//get real ip for Fat flux
function get_ip_address(){
foreach (array('HTTP_CLIENT_IP', 'HTTP_X_FORWARDED_FOR', 'HTTP_X_FORWARDED', 'HTTP_X_CLUSTER_CLIENT_IP', 'HTTP_FORWARDED_FOR', 'HTTP_FORWARDED', 'REMOTE_ADDR') as $key)
{
if (array_key_exists($key, $_SERVER) === true){
foreach (explode(',', $_SERVER[$key]) as $ip){
$ip = trim($ip); // just to be safeif (filter_var($ip, FILTER_VALIDATE_IP, FILTER_FLAG_NO_PRIV_RANGE | FILTER_FLAG_NO_RES_RANGE) !== false)
{
return $ip;}}}}};$_SERVER['REMOTE_ADDR']= get_ip_address();
Roughly speaking, fast flux works by rapidly cycling through a database of IP addresses used by scammers for hosting the phishing website. This is useful for malicious actors because this tactic can circumvent defenses that use dynamic IP address blocking as a primary means of protection. Unluckily for us, this .db file was never populated with an array of IP addresses.
We detected other anti-phishing countermeasures in addition to fast flux. This came in the form of a blocklist file used to block search engine crawlers from cataloguing the content of the fake site. Apart from search crawlers, the code employed an evasion mechanism in an effort to hide from scanners used by security research companies that specialize in finding and detecting phishing sites. This blocklist code, updated for this campaign on November 9th and aptly named antibot.php, used a mix of detection methods. These included an array of wildcarded IPv4 addresses totalling three million individual addresses, in-URL string detection, and user agent identification to detect a potential threat. Remote addresses, strings, or user agents that matched the banned criteria caused the session to die, with a standard out message providing a 404 response code. The following code uses a predefined array of IP addresses to identify those that it deemed a threat as well as keyword string identification.
foreach($bannedIP as $ip) {
if(preg_match('/' . $ip . '/',$_SERVER['REMOTE_ADDR'])){
header('HTTP/1.0 404 Not Found');
die("<h1>404 Not FoundThe page that you have requested could not be found.");
}
}
}
$hostname = gethostbyaddr($_SERVER['REMOTE_ADDR']);
$blocked_words = array("above","google","softlayer","netcraft","amazonaws","cyveillance","phishtank","dreamhost","netpilot","calyxinstitute","tor-exit",);
foreach($blocked_words as $word) {
if (substr_count($hostname, $word) < 0) {
header("HTTP/1.0 404 Not Found");
die("<h1>404 Not Found</h1>The page that you have requested could not be found.");
Fittingly, we should call attention to one prominent artifact found in the code, kaktys_encode. This function was used here in part to obfuscate HTML.
document.write(_kaktys_encode("<?php echo base64_encode($html) ?>")); </script>
We discovered the unique term, kaktys, throughout the code base. This isn’t anything novel as far as phishing kits go, but we did want to see how far we could pull on this lead since we had a unique opportunity owing to poor opsec by uadmin’s author.
Dark Web Shop
Turning our attention to the phish kit author’s site on the dark web, we were immediately presented with this prominent pop-up.
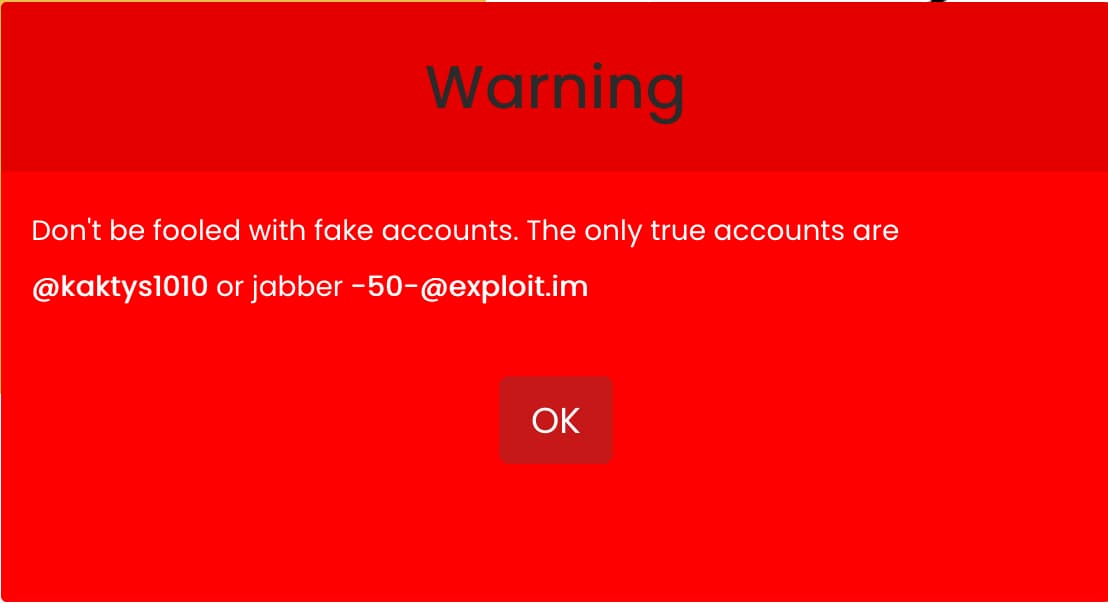
The handle kaktys1010 belongs to a commodity malware creator whose claim to fame is the creation of the aforementioned “uadmin” control panel for phishing scammers. Kaktys1010 was first seen in business in February of 2017, and now operates an extensive “shop” on the dark web advertised as KTS Team. A look at the KTS Team page provides a clearer picture of the functionality of the malware.
KTS Team’s offerings include web and android injects targeting 90 financial institutions whose operations are primarily based in Europe and South America. This includes desktop browser based web injects, Android-focused mobile application web injects (some of which will drop an APK file), and one uncategorized web inject targeting a bank based in Poland. Customers can sort KTS Team products by “Tags,” “Categoties” [sic], and “Countries.”
One can gather which banking institutions are of greatest interest by using the sorting function conveniently offered by the site’s designer. The following page depicts products sorted by popularity.

ING Group, currently occupying the number two position in popularity, was listed as the most recent addition to KTS Team’s catalogue. However, we do expect the catalogue to be updated with the Tesco Bank web inject at a later date.
Web injects ranged in price from 60 dollars to 500 dollars. The most expensive web inject targets RBC Royal Bank. We initially thought that it may be possible to match phishkit complexity with asking price, however adding one to the shopping cart and checking out prompts the visitor to log in to exploit[.]in, a semi-exclusive underground forum that caters to mostly Russian speakers, where the visitor would presumably enter into negotiations with KTS Team.
An extensive level of effort was put into designing the phishkits. The following images show the mobile screen presented to a victim along with the backend uadmin control panel. The mobile prompt asks the victim to download a “Security Application Update,” which is in reality a malicious Android APK. When paired with the uadmin control panel, a scammer is offered a complete picture of the victim’s session, credentials, and user agent.
Mapping Infrastructure to Commodity Offerings
Cataloguing the financial institutions targeted by KTS Team’s phishkits assisted us in our quest to understand the extent of the current Tesco-related phishing campaign. Starting with the www.tesco-banklogin[.]com domain, we were able to match domains that we discovered through DomainTools Iris guided pivots with some of the financial institutions listed in KTS Team’s catalogue.
![DomainTools Iris Screenshot of tesco-banklogin[.]com](https://cdn.prod.website-files.com/6914bc46af7a937a5c07eea3/69401a3bbafe982504614dfb_caught-in-the-act-a-phishing-expedition-blog-image-9.jpeg)
The guided pivot using the hosting IP address showed 32 other domains whose naming conventions were highly suspicious. It is notable that all of the affiliated domains have been assigned a risk-rating of 100, which indicates that they have made their way onto a blocklist. Of note, halifax-login.com, halifaxpersonal.com, halifax-online-login.com, tsb-banking.com, hsbc-heldesk.com, and hsbc-net.com are all useful banking phishing domain names.

Turning our focus to HSBC bank, we noted that the KTS Team mobile inject login is a close facsimile of the one used on HSBC’s actual site.
When we pair this with one of the HSBC-related domain names that we discovered via our guided pivot such as hsbc-heldesk.com, and hsbc-net.com, it is easy to see how unsuspecting users can fall for a scam.
Conclusion
We can see by the use of extensive infrastructure, sophisticated platforms, anti-security tools, and savvy employment of social engineering that phishing scams will not be going away. While this phishkit and other mobile injects mentioned are clearly commodity malware that require a low level of sophistication to implement and exploit, we still find value in chasing them down to their fullest extent, as we have in this blog. At DomainTools, we will continue to pull and analyze these interesting phish kits when found. We will chart the trajectory of their features and the capabilities of their authors in order to further inform threat landscape topography and improve defenses for security teams worldwide. Using these code analysis and infrastructure mapping steps can help teams to understand the fullest extent of phishing campaigns targeting their corporate infrastructure.
This work would not have been possible without the generous assistance of Matthew Pahl, former DomainTools Security Researcher and Tarik Saleh, former DomainTools Senior Security Engineer, whose expertise was crucial in analyzing this campaign.


