Cloud Atlas Navigates Us Into New Waters

Executive Summary
Taking recent Cloud Atlas nameserver activity as a starting point, the DomainTools researchers enumerated a potential sinkhole network containing hundreds of previously known malicious domains spanning dozens of campaigns. Using this domain knowledge, defenders and researchers can make inferences during day-to-day analysis such as the end point of a campaign or whether or not a particular sample is still dangerous. Additionally, DomainTools researchers provide a working method for enumerating infrastructure based on nameserver activity.
Background
In the past six months, DomainTools researchers have investigated multiple campaigns from the entity known as Cloud Atlas or Inception. As mentioned prior, Cloud Atlas’ targeting spans a number of government entities and industries, primarily in parts of the former Soviet Union and Europe, but has been actively seen across Asia, North America, and the Middle East as well. Cloud Atlas makes use of template injection to load malicious payloads on victim systems and spread their C2 infrastructure across a variety of cloud providers which makes tracking their activities a bit more difficult.
Nameserver Movement
On May 26, DomainTools researchers observed previously known Cloud Atlas domains transitioning their NS records from bitdomain[.]biz to one of three new nameservers that each contain roughly 150 domains that the DomainTools data science team’s risk scoring rates at a high risk for maliciousness. The original nameserver, bitdomain[.]biz, belongs to a discount hosting provider that accepts Bitcoin for payment, a common feature in APT group hosting provider choice. A number of unrelated domains exist on bitdomain[.]biz so this is not exclusive to Cloud Atlas and neither is the movement to these other nameservers.
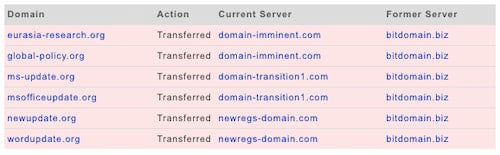
The movement between nameservers can be indicative of a number of things, but first and foremost movement means that there was interaction with the domain as someone or some process had to change the record. Many malicious domains, after use, are left to become stale but a domain moving between nameservers indicates that there is another intent left for that domain. This could be the final steps in a well organized campaign’s cleanup process, a further aging of the domain for other campaigns in the future, or movement to other infrastructure for a myriad reasons.
Since these domains are each less than 100 days old, they have not yet expired on their original registration, so this isn’t a “drop catch” situation. These nameservers also do not belong to any sinkholes that DomainTools researchers are aware of at this time. Lastly, the two-by-two pairing seems like an odd pattern since one would assume sinkhole infrastructure would keep domains from the same campaign on the same servers for measuring telemetry.
Examining New Nameservers
The domains behind these new nameservers, which Cloud Atlas has not previously been seen using, are well aged between the three of them with over five and a half years for an average age. With youth being a heavy indicator in maliciousness prediction products across the cyber threat intelligence industry, many threat actors have begun turning to well aged domain reseller services or trying to catch domains that have recently dropped from their registration. A prime example of this could be the avsvmcloud[.]com domain used in the high-profile SolarWinds supply chain compromise earlier this year. In this case, we have a long, contiguous set of ownership records in historical Whois for the domains attached to these nameservers so none of the above possibilities seem to fit here.
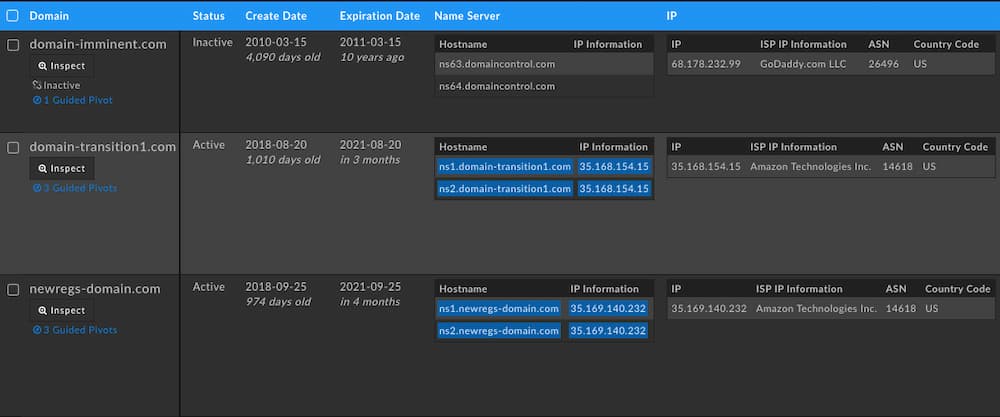
The top IP address looks to belong to a domain parking provider that has been around since 2010. However, the bottom two addresses point to Amazon EC2 nodes that are running just DNS services on port 53, acting as a DNS forwarding service — a sign this may be an unknown sinkhole. Digging into a history of domains that have resided on these nameservers ties them to other maliciousness, such as the .NET RAT SamoRAT’s domain samorat[.]com which resides on newregs-domain[.]com until May 19, 2021 or the domain 360mediashare[.]com seen distributing another RAT via phishing emails in late 2020. In fact, the same goes for the domain-transition1[.]com nameserver which hosts domains such as porkhalal[.]site which the Zusy banking trojan has been observed using for C2 and alhajikudi[.]com which has been observed in traffic of other malware samples in early 2021.
As DomainTools researchers looked further into these nameservers and the domains contained on them, it became apparent that this must be a domain reseller network or a sinkhole telemetry network due to the large swath of known malicious domains transitioning through these nameservers over time. DomainTools’ own proximity risk scoring rated all of these related domains an average of 80 due simply to their proximity to known malicious infrastructure on industry standard blocklists. Typically, in the experience of DomainTools researchers, a scoring above 70 means that a domain should not be trusted and should be investigated further. It became apparent that mapping this network would be a useful exercise.
Looking For More Nameservers
With these bottom two domains there is a pattern we can treat as a composite object for hunting additional infrastructure:
- They have nameservers that are hosted on the domain themselves.
- This domain is hosted on Amazon’s AWS on an EC2 node.
- The domain contains a dash.
- The emails in the Whois record have both privacyprotect[.]org and bigrock[.]com in the record.
Searching for these features in the DomainTools Iris Investigate data set reveals a total of 5 additional domains that DomainTools researchers can say with high confidence belong to the same clustering:
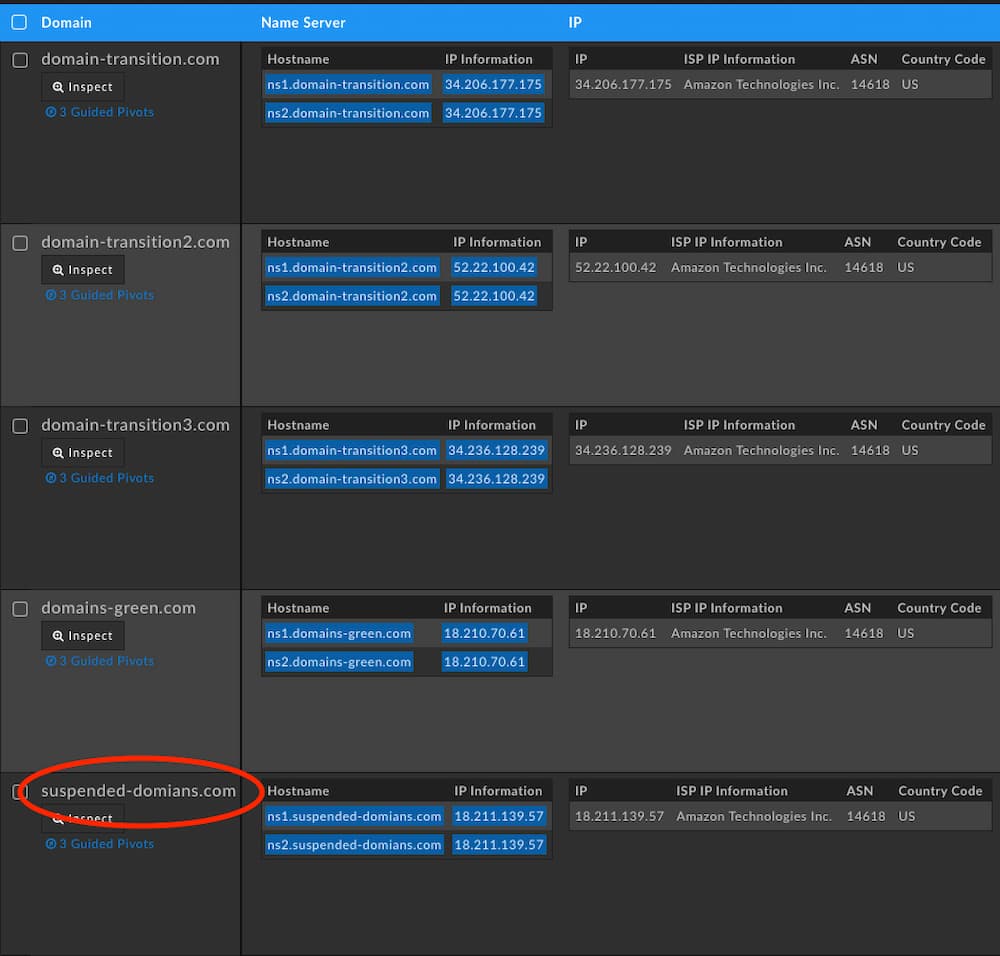
Note the misspelling in suspended-domians[.]com. Expanding on these nameservers reveals just over 1,086 domains, most of which have been involved in some sort of cybercrime activity in the past. Of those 1,086 domains none of them had a reseller page when navigating to the domain which domain resale companies use to signal that the domain is for sale. Lastly, DomainTools Research noticed that all of the domains associated with those nameservers pointed to one of 3 IP addresses, spread across all nameservers, that definitively tied this clustering together.
Inverting the search from nameserver properties to solely A records reveals a single site as an outlier: dropbox-download[.]com. It is an outlier because it contains a different nameserver in domain-imminent3[.]com, a naming schema nearly identical to one of the nameservers associated with the original Cloud Atlas movement at the beginning of this report, domain-imminent[.]com. Of note is that the dropbox-download[.]com domain here is associated with TA505, the group behind the Dridex banking trojan, from a campaign they ran over two years ago.
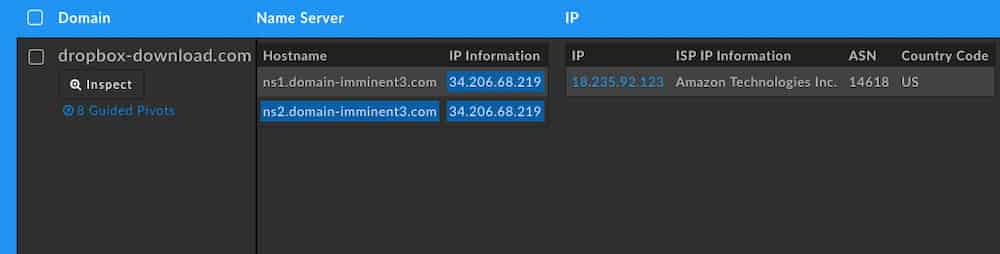
Viewing all domains on domain-imminent3[.]com, repeating the process from above, reveals another common IP address (52.6.206[.]192) spanning multiple new nameservers including domain-imminent1[.]com, domain-imminent2[.]com. The inclusion of these final two nameservers contain a recent lapse in privacy protection on the Whois record and an email address of resellerclub@protonmail[.]com that is tied to them.
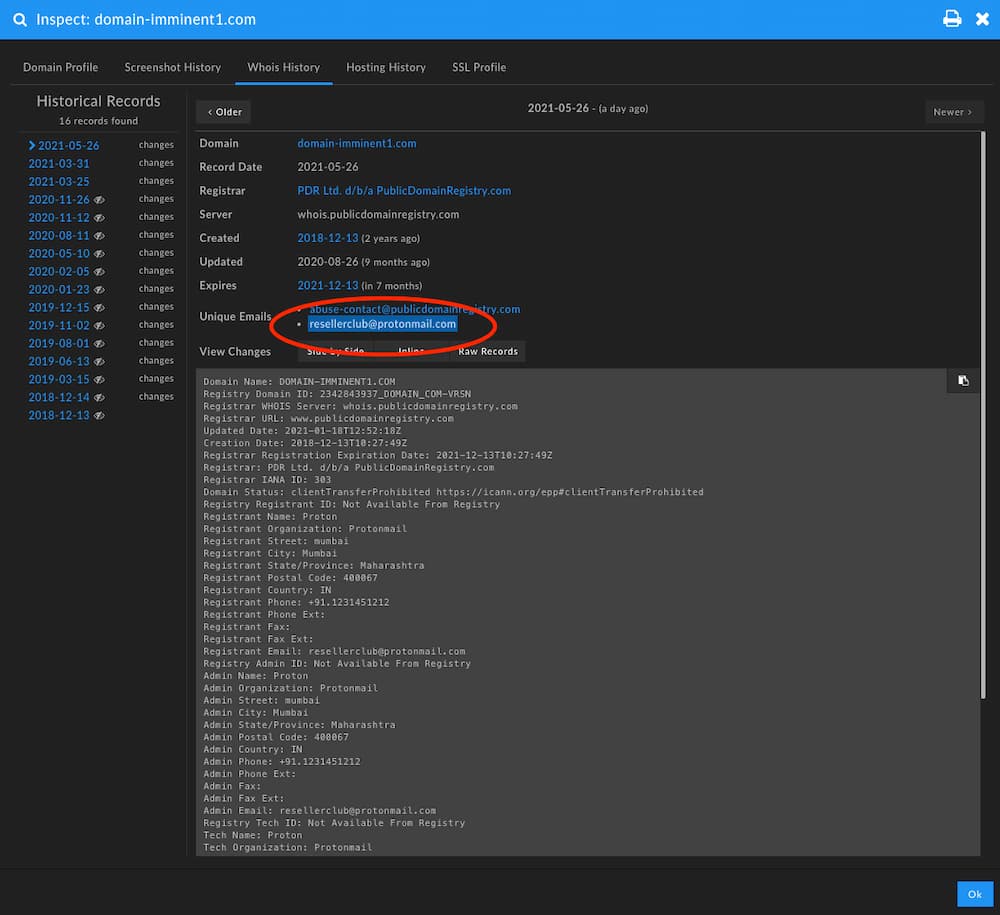
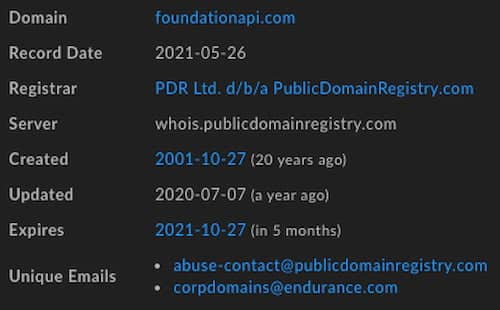
This email in historical Whois records ties to 20 records total that span most of the nameservers DomainTools researches enumerated. On top of that, many of the domains in that group—including elsewhere in the list of total domains—move to the nameservers at foundationapi[.]com at one point or another, a property of Endurance International Group, a company in the domain and web services space that owns a number of properties including BigRock, HostGator, and ResellerClub.
ResellerClub allows for the bulk resale of domains. Searching on their documentation you can see the use of foundationapi[.]com as a backend as well as the services and pricing they offer for bulk domain purchases.
The Domain Swamp
Expanding across the domains tied to all nameservers there are a total of 1,378 domains, 559 of which are on known industry blocklists for malware and on average score above 80 in the DomainTools Risk Score engine. Going through those 1,378 domains, none could be found on domain auction sites or for sale, so this further backs up the potential that this is a sinkhole network run by the Endurance International Group or one of their subsidiaries. To show the broad swath of domains and campaigns associated, DomainTools researchers coupled one nameserver’s holdings, domain-imminent1[.]com, with Alienvault OTX pulses below.
Conclusion
At this point DomainTools researchers are led to believe that these nameservers are a holding pen for known malicious domains on the reseller network until they can be resold or are actively being used as a sinkhole by the reseller network for telemetry. Since DomainTools researchers cannot find a description of the sinkhole network or any of that telemetry being posted elsewhere online, defenders can only assume that this is a private sinkhole network associated with Endurance.
Lessons for Defenders
If you are an analyst working with malicious software or mapping adversary infrastructure, knowing of these dead zones in domain data so that you do not get distracted by them when trying to map live infrastructure is key to efficiently researching threats. For threat hunters, watching the transitioning of domains on and off these nameservers, through a tool like the DomainTools Nameserver Monitor, can provide ample domains for hunting queries on public repositories of malicious binaries and lead to pivots of fresh, un-sinkholed infrastructure.
Nameserver List
domain-imminent[.]com
domain-imminent1[.]com
domain-imminent2[.]com
domain-imminent3[.]com
domain-transition1[.]com
domain-transition2[.]com
domain-transition3[.]com
domains-green[.]com
suspended-domians[.]com
newregs-domain[.]com
Iris Search Hash for All Domains On These Nameservers:
U2FsdGVkX19inpzBsHU8tDBrjLPfcJTcmLc+O13CCJpuRlnDdlUogNF5k0NIqexuO4v7GkilkMrvqup8FVTtMVQQrg/xPu/9Q4avDogSm4x0+yDsH/6+HVweHeKvZEpizpLP3Xtl631NnH2TCEnfgrvwrWX040a2z8HZXoiaFO78AqHDvHtV/q3OYA7lG4k8Hw7ZCkipo/b6nr3TiUNt35edO4IE+IavrfpoTUNu51/kvJASkxKi8paImchnBwX8hs4BjtrqeolMwwjYClGV5YW1JdOcm23P0s8AjHrN8+UCGg6sZi5kZLsYsTOWsTpo7+ZTNsJXzQ/xgYdHbRe5ADC+f1Jg3jyKHdxGKK6UsWZi6ThVo95AxEqttVvYY82AEl8gpybdiw2wnil+yu+7DfoNN5YNSl/5Q6VJjlQHlxScjy0TBOF3dQXK1J0NgLnPszEgyJf62LoyGdteGt94cvB0sKQ05v8ZiZBLAmyh5WlLIiTO01pQeHylJ10ZWt9VvCaf1ooe3hChHNuGdNzKufo50+GtdzYqiYKagIze6niqaWnRtDiW6sEc4m7HgUAEiuqKJ7Z4c5bWmZKIwM6AlILmJzrojnHhyKEiVLAzCmCRuMlVcv9sJ8fHc+8Y+5tMeuOUu5UPFmYyBJ951IyaMTT3ZDYUDBgdwdofH8ZdeODOf9I2/BoM1KkGEzsRBm1K6KN/R69txLMIa6YMuqmvEVYzaNFs9DS0yfxbGWiQTM8=


