Developing Threat Hunting as a Practice
Threat hunting as a discipline is a relatively new practice area. It evolved from a combination of SecOps and forensic investigation activities. Now, when an incident occurs, professionals engage in a reactive manner to gather artifacts and information to define the scope of an incident and remediation requirements.
The first integration and evolution of these activities came a few years ago, when operating perspectives changed to assume the organization has already been breached. With this reversal in perspective and approach, organizations needed some of their more skilled personnel to use their experience and whatever tools they could cobble together to search for indications of breaches. These investigations were focused on internal artifact and intelligence gathering, and the insider threat.
As cybercrime grew into a serious global threat to all businesses and fueled the growth of the dark web as a stolen information market, forward-thinking organizations are now looking externally to find indicators of threat and compromise. Whether looking for stolen information for sale or domains mimicking their brand, they know early detection is important.
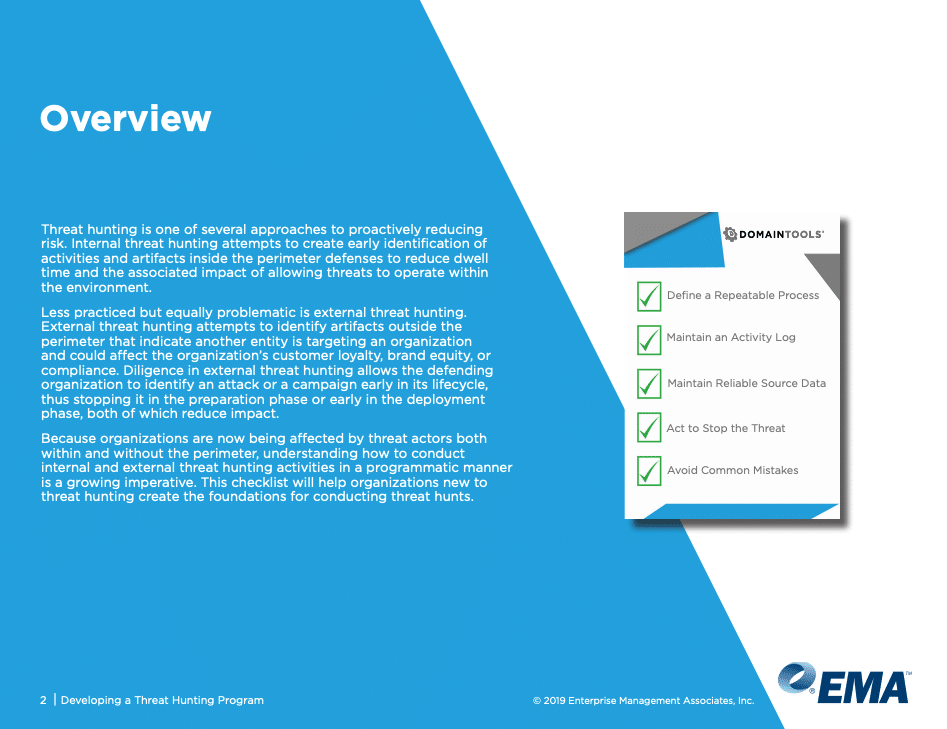
One of the crucial aspects of any threat hunt is making the process of investigation as methodical and repeatable as possible for two reasons. A methodical approach means investigators cover more leads faster to reduce discovery time. Repeatable processes mean that people of lower skill can more easily follow them to learn and become better. Together, these two options represent one programmatic approach, increasing the probability of success.
DomainTools and Enterprise Management Associates have published a five-step program to help teams getting into cyber threat hunting more effectively launch their programs and avoid the common pitfalls new teams experience. Click on the button below to get your free copy.