Discord Malware and TOWINAP ("The Only Way Is Nuke and Pave")
Introduction
At DomainTools, we take great pride in helping organizations detect and predict emerging threats, including malware infections. When not working, many DomainTools employees and their families also enjoy gaming.
Let’s talk about malware targeting the online PC gaming community via Discord. The PC gaming community may be a particularly-attractive target for bad actors because:
- Virtually all the most popular PC game titles are Microsoft Windows-based. The vast majority of malicious software targets MS Windows (see for example, “Almost all new malware is targeting Windows“). This means the PC gaming community represents a known-vulnerable attack target.
- Gaming computers are generally more powerful than non-gaming computers and tend to have top-notch network connectivity, since having a 2nd-rate system or poor connectivity tends to make it hard to be successful in most online games. If you’re going to devote effort to compromising systems, and it takes the same amount of effort to compromise one type as another, wouldn’t you prefer to get the most “bang” for your “buck?”
- Gaming computers also are normally personally managed. Such systems will often not be protected by the same range of security strategy and tactics as centrally administered systems.
- In fact, some gamers may intentionally shun system security features including antivirus software due to a perception that those measures may “slow their systems down.”
- Gamers are often dedicated to becoming experts in their favorite title, playing for long hours after what may have been an already-long day at work or school. Like a tired or distracted driver, a tired or intensely-focused gamer may be prone to making poor decisions when clearing other interrupts. This can result in mistakes they’d normally easily avoid making if they were well-rested and not playing their game.
- Online gaming tends to be a competitive and social activity, driving ongoing interactions with far-flung online team mates. This creates a diverse social and geographic graph of contacts for an attacker to potentially target when trying to expand the scope of their attack.
Why Discord in Particular?
Discord is a gamer-focused messaging service which lets friends chat with each other either directly or as a group. Chats can include messages, video calls, voice chat, and more. It is separated into communities, historically with a game being the subject of each community. Each community has its own Discord server.
- Basic access to Discord is free. All free services are prone to being abused, no matter how hard those providing the service work to remove abusers. Discord is no exception.
- Discord is popular, with roughly 19 million active servers, with roughly 90% being small/specialized with 15 or fewer people, and over 150 million total active monthly users.
- Discord is encrypted. This means that malicious traffic may totally side step network monitoring and attack detection.
- Discord users have assets that can be monetized by attackers.
- Sophos has characterized Discord as being a “rough neighborhood“ and “[…] a dumping ground for malware. And even for malware not hosted on Discord, the Discord API is fertile ground for malicious command and control network capability that conceals itself in Discord’s TLS-protected network traffic (as well as behind the service’s reputation).”
How Does This Particular Infection Tend To Happen?
Let’s focus on one popular style of attack, the “new game” attack. It involves a message sent via Discord, usually originating from a known teammate, asking for help “testing a new game.” Of course, the message is actually sent from a compromised account, and the “new game” turns out to actually be malware. With the Discord.io breach, bad actors could mine the hacked list of accounts and communities to determine possible targets for infection.
With one click, the targeted gamer’s computer is totally compromised, typically with an info stealer, but a remote access trojan or cryptominer or other malware may also be dropped. The one “good” thing about this particular infection mechanism is that there’s seldom much doubt or uncertainty about exactly how the user’s system got infected.
A specific example of this attack was documented on Reddit at the end of 2022, noting that their friend was tricked into running a “bby stealer” when they thought it was a new game created by a game dev/ art student. The file was uploaded to VirusTotal. Intriguingly, while 36 of 71 antivirus vendors are shown as flagging this sample as malicious at the time this was written, the other 35 antivirus vendors did not detect it, including ClamAV, Malwarebytes, McAfee, and TrendMicro. FileScan.IO also has a report about this file, it’s also linked-to from the above VirusTotal report.
A more detailed writeup is available over at InfoMalware, see ‘The Elusive “Try my game” Discord Scam.’
“Under-The-Radar” vs “Turn-It-Up-to-11”
Optimally-engineered malware, like the most-ultimately-successful human/animal/plant pathogens, tends to coexist with their hosts in a long-term-tolerable sort-of-way. On the other hand, more aggressive infections that seriously sicken, cripple or kill their human/animal/plant/computer hosts tend to quickly get prioritized for treatment and elimination (think “common cold” vs polio or Ebola).
The Discord malware, whether due solely to its own operation or as a cumulative result of interactions with other co-infections, may render systems slow to the point of unusability, particularly for gaming-related speed-sensitive uses. To be clear about just how bad this can get, it may literally take minutes just to login or open a window, and downloads that should happen virtually instantaneously may take minutes to happen (or time out entirely). That’s a level of dysfunctionality that’s impossible to ignore.
TOWINAP
Malware will often burrow deeply into a system, and may include defensive anti-tampering measures meant to ensure its persistence, helping the malware to successfully “hide” from antivirus products and resisting attempts to find and remove it, perhaps blocking processes from being monitored, keeping antivirus software from running or killing it as soon as it starts, or steps to keep patches from being applied.
So, try as you might to “clean” an infected system using antivirus software, you can never be totally sure that you’ve actually gotten “everything.” In fact, you might routinely run MULTIPLE antivirus products – each triumphantly reporting “nothing malicious found” – only to end up with a system that’s still exhibiting undeniable symptoms that something’s seriously wrong.
This brings us to the principle of “TOWINAP,” or “The Only Way Is Nuke and Pave” [“tip o’ the hat” to ‘TOWIE,’ “The Only Way Is Essex,” for inspiring this acronym]. That is, once a system’s been infected by malware, the only truly effective way to fix it is to reformat the system’s disk (“nuke it”) and then reinstall the operating system, applications and user files from clean backups (“pave it”). See also the obviously-related Aliens reference.
Most users dread receiving a “reformat and reinstall” recommendation for several reasons:
- The user may be ashamed or embarrassed at having been infected, particularly if they’ve already been “hazed” by team mates or family/friends.
- The user may not be technically ready and able to rebuild their system. In that case, they’ll need to identify someone else who can do it for them. That will normally not be free.
- Formatting and rebuilding a system takes time, particularly if this work needs to be outsourced, and during that time the user will lose the ability to use their computer.
- The user may not have a current clean backup of their personal files. This is routinely the biggest roadblock inhibiting even reluctant acceptance of the need for a “nuke and pave” to be done.
These days, even nuking and paving an infected system has become more complicated. Let me provide just a few brief examples:
- Nuking the hard drive: you will want to securely erase your drive to ensure no bad bits remain. This may require you to pull the drive out of the system and plug it into another machine or use a third party tool.
- To install Windows 11, your boot configuration must have Secure Boot and TPM 2.0 enabled. If the machine had Windows 11, you should be already good-to-go, but if you are taking the opportunity to upgrade, be wary of your current BIOS settings.
- You may need media with a clean current copy of Windows 11. You can download that from Microsoft directly.
- There are several options for writing bootable ISOs to USB thumb drives. Microsoft themselves provides a Media Creation Tool. Also, Rufus is a popular free and open source tool for Windows. Just be aware that the ISO is over 8GB in size, which is a problem for the required file system format.
- And then you may find yourself rummaging around for your Windows license key. Most modern computers which came with Windows preinstalled will have the license key stored in the BIOS, so you’re good here. For once, you may be worried about nothing. It’s also worth noting that if you logged into Windows using your Microsoft Account, Microsoft may also have a record of your keys.
- And then there’s the matter of restoring your backups. You do know where you put that last backup drive, right? And how to restore the entire backup? Many times users may no longer remember where they put their most recent backups, nor will they have ever tried to restore from them.
One other bit of hard reality: if your system’s four or five years old or even older, it may ultimately be easier to just replace the old infected computer with a new one. You’ll still need to restore your files from backup, and you’ll still want to wipe your old computer before selling it to someone else (if only because it may have still-accessible sensitive files on it), but it’s always nice to get onto current generation hardware.
Most of the time, however, gaming computers will already be relatively current, so we’re back to “The Only Way is Nuke and Pave.”
We Know You’re Going to Try Disinfecting Your System (Even Though We Both Know It Won’t Work)
Despite the reality that ultimately “The Only Way Is Nuke and Pave,” we know that many of you will at least try to disinfect an infected computer. If this is the case, you should be aware of the “distinction-without-a-difference” between various types of malicious software. It could be a bot, a true computer virus, a worm, a back door, a trojan horse, a rootkit, a potentially unwanted program, adware, crimeware, ransomware, spyware … The list is seemingly endless (and overwhelming!). The various terms of art just mentioned are not interchangeable even though they are all “malware” and there are real and important implications between those various “terms of art.”
The most important difference is that the type of malware may determine the sort of cleaning tool you should try to use. You must “pick the right tool for the job” and “ensure that all the right options have been set.” Many antivirus vendors do not provide a comprehensive approach to find and clean all types of malware using just a single tool. Instead of adopting a unified “all-threats” model, many antivirus vendors may intentionally segment their products’ coverage:
- An anti-virus company’s flagship product may successfully tackle most malware, but intentionally not tackle some particularly tricky categories of software threats.
- Some products may fully integrate all capabilities, but the more-tedious options, such as scanning within archives, may be disabled by default. Other options may be prone to “false positives” (saying something is bad when it really isn’t), so those heuristic rules may also be “off by default”. You may want to enable those options if you’re patient and willing to handle any false positives.
- Some products may not want to remove programs you have agreed to install. It may be a matter of “consent:” the argument you’ll hear in this regard is that IF you’ve agreed to the installation of a program (even if that program makes your computer run slowly, or redirects all your search traffic through some dubious overseas search engine, or the program drives you crazy with pop-up advertising), well, you did agree to install that software (even if only by blindly clicking on a multi-page online agreement packed with legalese).
From our point of view, if software hurts you or your system, or violates your privacy, it should be targeted for detection and removal, regardless of what it’s called, how hard it may be to do so, or whether you were careless or tricked into letting it be installed in the first place.
- Business issues can also have a perverse impact on how vendors choose to segment their anti-malware products:
- There have been a lot of mergers and acquisitions in the cybersecurity sector. When companies merge or get acquired, there may be overlapping products or products that can’t be cleanly merged and integrated for whatever reason. When that happens, you may see parallel products “stake out” and “defend” a particular coverage “niche,” inhibiting seamless integration of newly acquired capability with existing capabilities.
- You may also see segmentation in an effort to contain consumer sales price points and give consumers flexibility to “only buy what they really need.”
Business-side staff know that consumers can be incredibly price sensitive, and may balk at paying even $120 for a holistic “do-it-all” anti-malware product (“Oh my gosh! That’s so expensive!”).
So how to handle that? Well, they know that consumers might be willing to pay $40 for a general purpose antivirus product (and then, later, $40 for a particularly relevant add-on product, and later still, $40 for another feature they need, etc.). So, segmentation may be imposed as a way of addressing consumer price sensitivity.
We’ll also note that you should ensure you’re scanning ALL volumes on your system. Some systems may only scan your system disk, and ignore any data disks by default (again, often in an effort to be “fast”).
Doing What You Shouldn’t Do, And Why It May Not Be Effective (Hint: The Windows Registry)
So, what to do? We’re not going to endorse any particular vendor’s commercial routinely-running antivirus product, but we will call out one popular, good, and free on-demand scanning tool for tackling “Potentially Unwanted Programs,” sometimes also referred to as “Potentially Unwanted Applications” (PUPs/PUAs), in particular: MalwareBytes’s ADW.
It will routinely find PUPs/PUAs even after other scanners have proclaimed a given system to be completely “clean.” Most of the bad stuff ADW finds it will also do a good job removing, however some malware-related artifacts may remain. For example, on a sample PC infected with the Discord malware, ADW found and flagged but did not remove three Registry entries.
The Windows Registry is the database which centrally stores details about your system and how it’s configured. It can be accessed with bundled Windows utilities, such as Microsoft’s regedit or the Windows Group Policy Console, or developers can leverage open source libraries, such as winreg for Python or Golang’s windows registry package, to write their own Registry manipulation tools.
Most users may have no idea that the Windows Registry even exists. Ironically, that may be good, because it can be trivially easy to irrecoverably mangle the Registry if you muck around with it (and you should always be sure you’ve got a trustworthy recent backup before making any tweaks to it.)
Technical security people may be all-too-familiar with the Windows registry out of necessity. Some excellent compilations of security-sensitive Registry configuration entries can be seen in per-product security outlines (“benchmarks”) available directly from the Center for Internet Security or via Tenable. Some selected examples include:
- https://www.tenable.com/audits/CIS_Google_Chrome_L1_v2.1.0
- https://www.tenable.com/audits/CIS_Microsoft_Edge_v1.1.0_L1
- https://www.tenable.com/audits/CIS_Mozilla_Firefox_102_ESR_v1.0.0_Windows_Level1
- https://www.tenable.com/audits/CIS_Microsoft_Office_Enterprise_v1.0.0_L1
- https://www.tenable.com/audits/CIS_Microsoft_Windows_11_Stand-alone_v2.0.0_L1_Bitlocker
Some of the above benchmarks may call out hundreds of Registry settings that should be reviewed, and that’s just for a small subset of all software products you may be using. Virtually every piece of software running on your MS Windows PC likely has something in the Registry – it’s truly the soul of your computer.
When it comes to folks who routinely leverage the Windows Registry, there are three main categories:
- Commercial software developers who keep track of things (such as product settings, activation keys, or expiration dates) in the Registry – that data will sometimes be stored as an encrypted blob of opaque text that the commercial software knows how to read and validate.
- Enterprise administrators will also often leverage registry entries. Registry entries (often referred to as “policy objects”) can help keep users safe while ensuring compliance with local system and network standards. The preceding CIS benchmarks describes many of those.
Let’s just explicitly consider a hypothetical example. Let’s say a governmental agency decided to block printing of documents in Chrome. They can implement it by setting Chrome’s “PrintingEnabled” setting to false, see the following screenshot: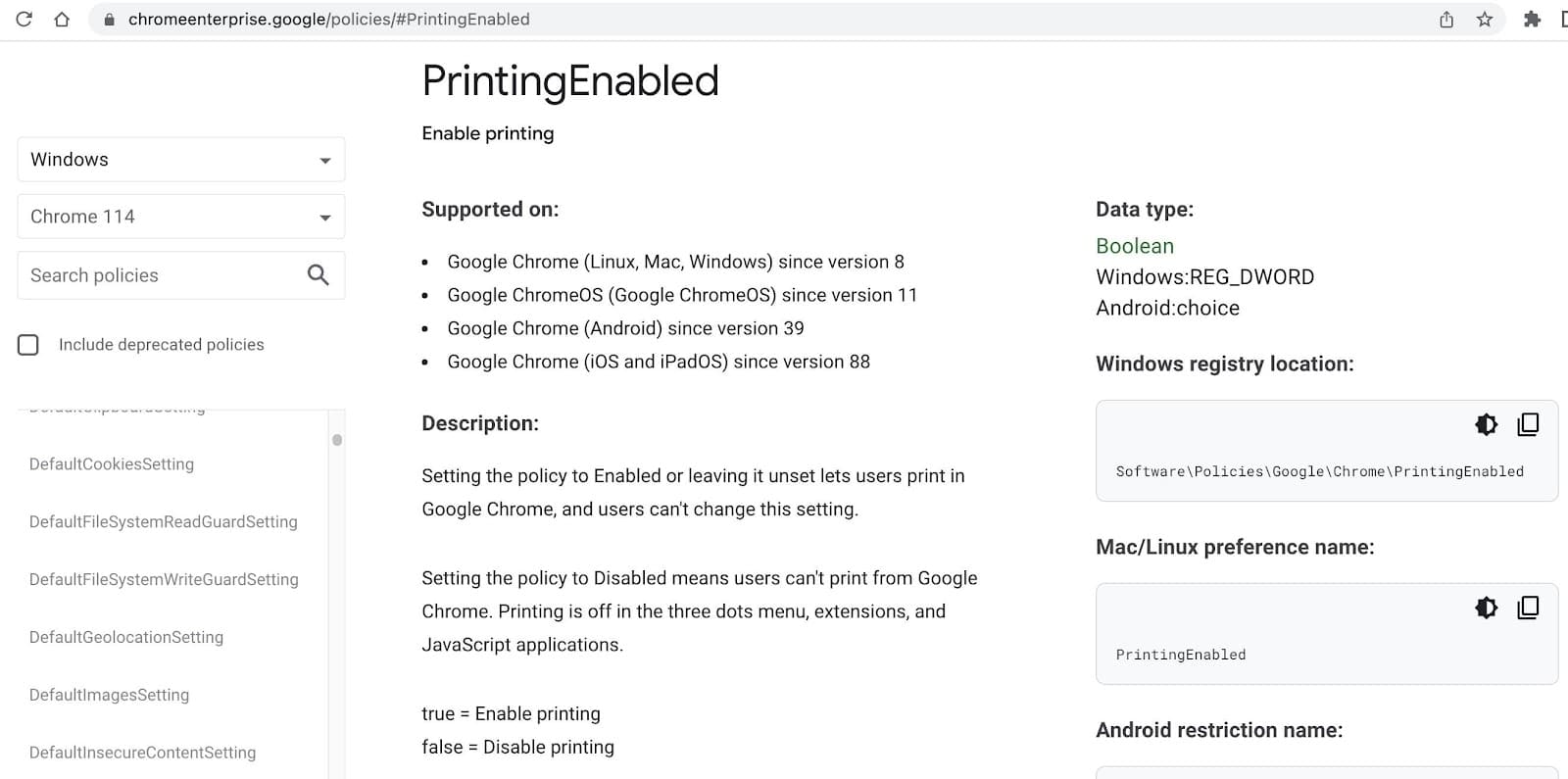
The Registry can be used by Enterprise administrators to set a surprising number of other features, too. You can get inspiration (or ulcers) by browsing Registry settings. I’m sure many bad actors have been inspired as well.
- Speaking of bad actors, malware authors are well known for manipulating registry entries. For instance, search hijacking malware might change the browser’s default search engine to one that pays the hijacker for rerouted traffic. Numerous scenarios where attackers have modified Registry entries can be seen in the “Procedure Examples” section in MIRTE’s ATT&CK framework.
In each of those cases, one party (e.g., the commercial software author, the enterprise admin, or the malware author) may want to keep another party (such as the user or the user’s antivirus software) from easily reverting the values set by the first party. How they attempt to accomplish this may vary from scenario to scenario:
- The commercial software vendor may decide to rely on strong cryptography to technically preclude unauthorized changes to their data entries. Unless you’ve got the vendor’s cryptographic algorithm and the appropriate parameters, you wouldn’t be able to craft a modified-but-cryptographically-valid fake license file, for example.
- The enterprise admin may simply rely on vendor assurances, such as Google’s assertion (in the “PrintingEnabled” policy document) that once set, “users can’t change [the PrintingEnabled] setting.”
- The malware author may decide to employ sneaky techniques to hide or deter changes to Registry entries, such as leveraging embedded null characters as described in “Hiding Registry keys with PSReflect.”
- Other times, the sheer volume of Registry entries and the general complexity of the Registry tree may make it hard for users to discover and change entries.
The key takeaway from all this is that cleaning up an infected computer is not JUST a matter of spotting and removing bad programs, there may also be problematic or obfuscated settings buried deep in the Registry, and it may be hard to fix some of those.
Other malware may hide in browser extensions, which may or may not be scanned by antivirus software, and which may autolaunch and run in the background at startup via entries primarily visible via msconfig. You get the idea: the number of possible infection reservoirs is large, and malware authors are continually looking for new ways to achieve “persistence” on infected systems.
So even if your family member or friend pleads with you to “give cleaning the computer a shot before just nuking and paving it,” think about the registry and its complexities and the corruption that may lay within it. You may give it your best shot, only to end up with a still-sick system.
Let’s conclude this section by reminding you of one other thing: malware authors may attempt to take advantage of those who have infected computers by offering tools promising to clean up infected systems. In fact, those tools may be just another way of installing additional malware on the user’s computer, making things worse, not better.
So remember, if a Windows system is known to be infected or is “acting weirdly,” The Only Way Is Nuke and Pave.
Takeaways for Your Consideration
- Review the online services you use. Yes, Discord is fun and hugely popular, but does it deliver benefits that outweigh the risks you’ll be exposed to there?
- If you do decide to join or stay on Discord, consider disabling “Anyone from this server can Direct Message me.” You’ll still be able to send and receive group messages, you’ll just block direct inbound 1:1 messages that may be targeting you personally.
- Think hard about whether you really need to be running Microsoft Windows. Remember, most malware targets Microsoft Windows, so if you can run something else, that one simple decision will serve to make most malware irrelevant. For example, if you’ve long been a PC gamer, is it time to give console-based gaming another look?
- Run the latest operating system and stay patched up-to-date. This means installing all Windows updates and all vendor-specific updates, including application updates and browser extension updates too. Staying up to date is one of the single most important things you can do. If you ever can’t install updates, treat that as a real red flag until you get that issue resolved.
- Use a regular (unprivileged) account for your daily work, reserving your Administrator account for when you really need to perform system administration tasks that need elevated privileges. (Remember all the Windows Registry discussion? Regular users can’t tweak many Registry settings while Administrator users can.)
- Routinely backup your system and keep multiple generations of backups. It can be distressing if your most-recent (and ONLY!) backup ends up tainted with malware just when you need to restore files from it.
- Use an antivirus product, even if they aren’t perfect and can’t/won’t detect everything. Enable your system’s other available security features, too!
- Use a password manager (don’t just store your passwords in your browser) and use multifactor authentication on all your accounts
- Disable all unnecessary services and block all unnecessary traffic, including advertising in your browser.
- Finally, remember that you don’t want to “make things worse” when trying to make things better: it is common for cyber criminals to create fake antivirus programs, knowing that owners of infected computers may be prone to downloading and running anything that might have a chance of helping them get disinfected. Well, badly infected as your computer may be, it can still get worse! TOWINAP!
Acknowledgements
The author would like to thank Dr. Sean McNee, Mr. Ian Campbell, and Mr. Leif Tishendorf for their reviews and helpful comments about this blog. Any remaining issues are solely the responsibility of the author.