DomainTools 101: How to Spot Phishy Domains on Cyber Monday
NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
Just as the Grumeti River in Tanzania harbors dangerous crocodiles just below its surface, a Phishing email usually contains malicious domains waiting for you to click. I read a great article by Bleeping Computer about finding some Google domains that were spoofed using what is known as small caps. This piqued my curiosity so I started a DomainTools Iris Investigate investigation with the first domain that was mentioned, “ɢoogle[.]com”. You have to look very closely but the first letter of the domain is actually a small cap, which is not a standard ASCII character, it is what’s known as an extended character. DNS only allows the usage of ASCII characters and so names like this are represented in DNS via what is known as puny code, which translates extended characters into ASCII. So for this domain name to be recognized in DNS, it is translated into the following: “xn--oogle-wmc[.]com.
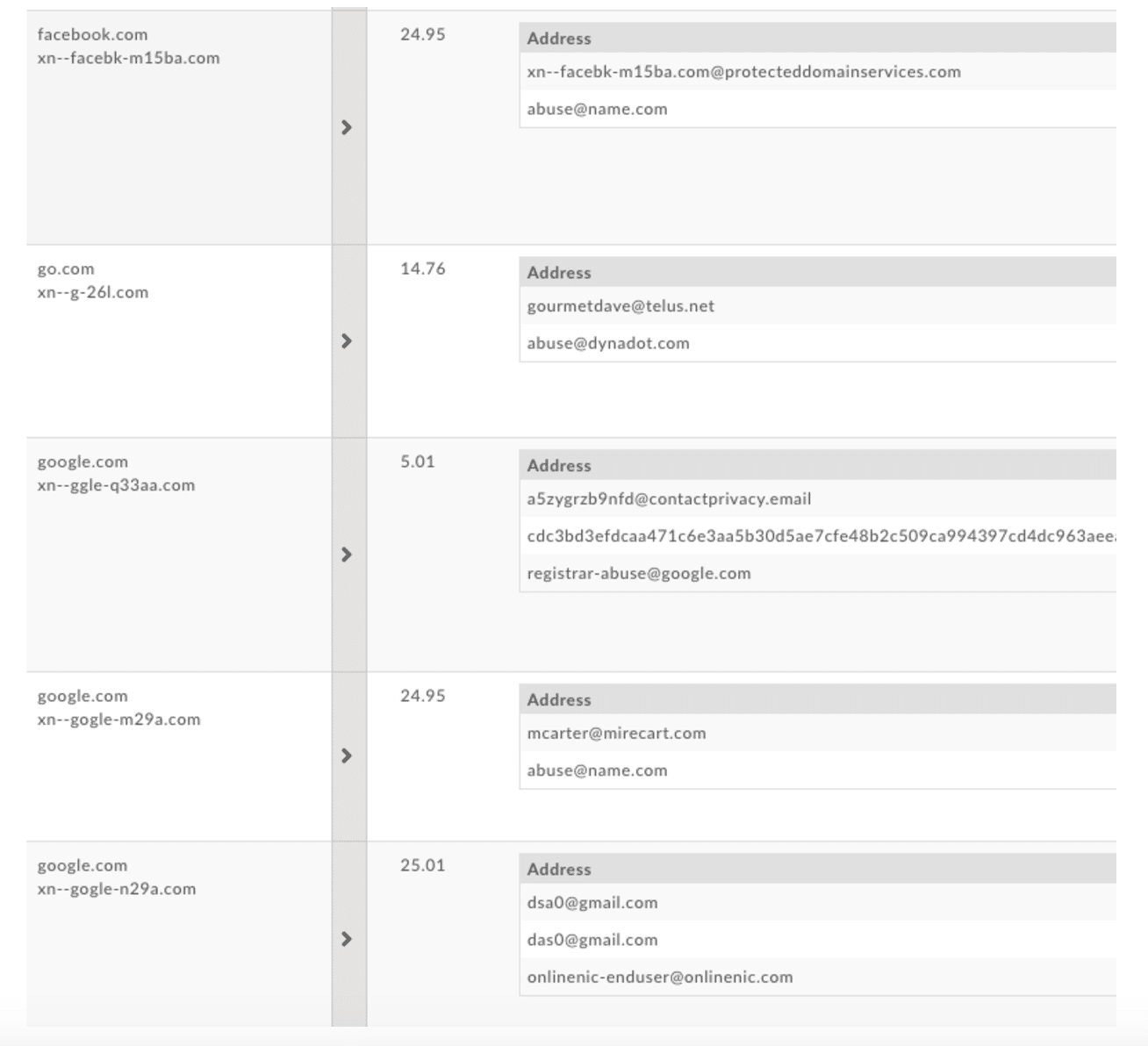
The first thing I noticed was that the domain wasn’t registered by Google, but rather by Vitaly Popov. By pivoting on the email address, I discovered that Vitaly Popov had 267 domains registered with his .ru email address. A little more digging unearthed his passion for his delicious spam meals and spam referral service.
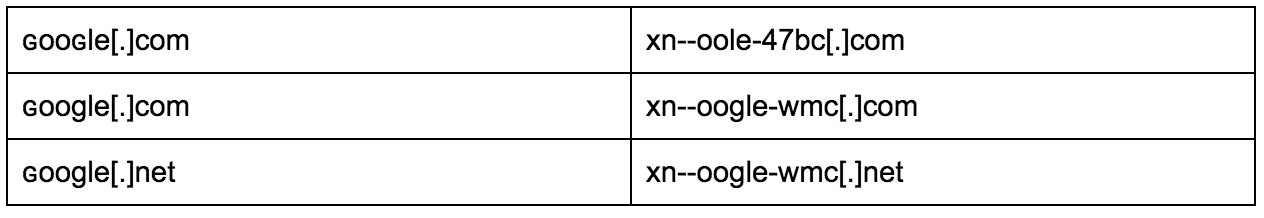
This got my engine revved up so I went a little further in the advanced search option in Iris and searched for domains that contain “ɢoo”. This returned three domains:
Then I wanted to see about domains that contain “ɢle”:
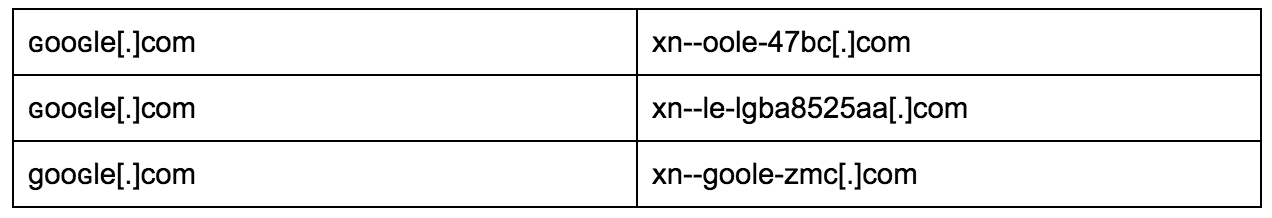
Next, I worked with one of our engineers to run some deeper searches on our data of domain registrations. We were able to identify 126 of these domains. Some are such good phishing domains, they would fool almost anyone. Here are some examples:
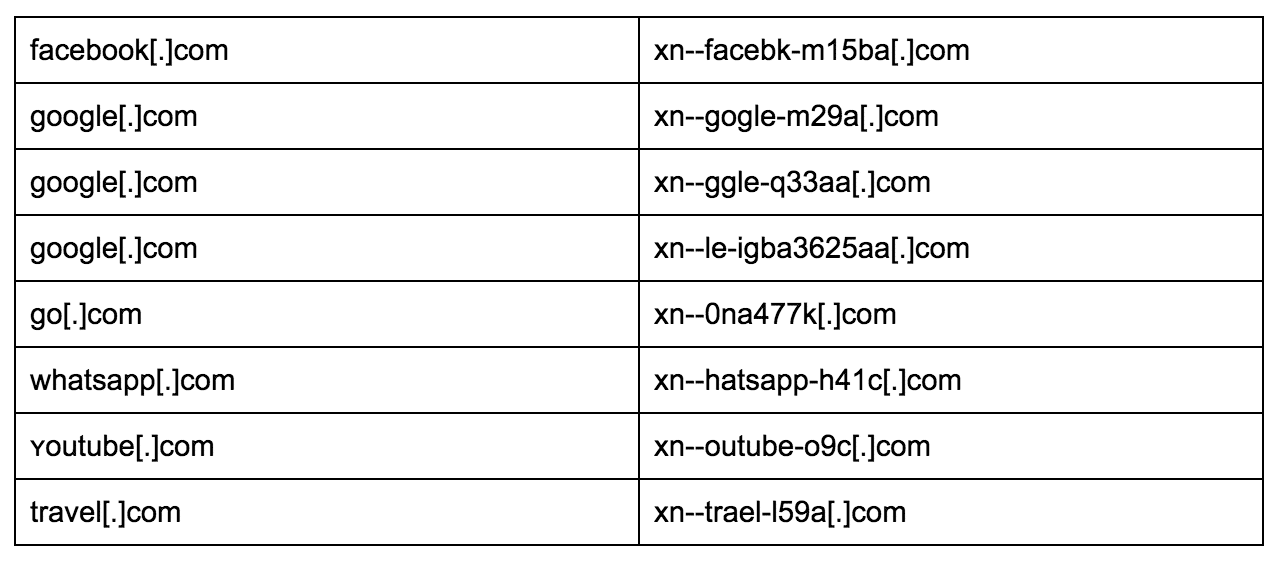
If you look very closely at the xn-- name, you can begin to decipher what characters were swapped. For example, in “xn--hatsapp-h41c[.]com”, the w is swapped for the small caps w. In the 3 google[.]com domains, you see that the first one has just one o swapped but the second has two swapped. Hopefully this provides some insight into how phishers are trying to fool us into going to the wrong domains and steal from us.
As we approach Cyber Monday, this is the time to be hyper vigilant as consumers. What I’ve shown here is much less than the tip of the iceberg, it’s more like the an ice cube from an iceberg. We have observed fake domains for every single company with a website so when you get that “HOT DEALS” email, text, or online ad, exercise extreme caution before you follow the link.
Have fun shopping and be careful.




