DomainTools 101: Nothing is Certain Except…

You know the old saying, right? Nothing is for certain except death and taxes. In today’s evolving cyber world, perhaps it’s time we update this idiom to: nothing is certain except death, taxes, and tax scams. Although we are (thankfully) not in the throes of tax season, it doesn’t make any of these scams less prevalent or dangerous for your network or your employees.
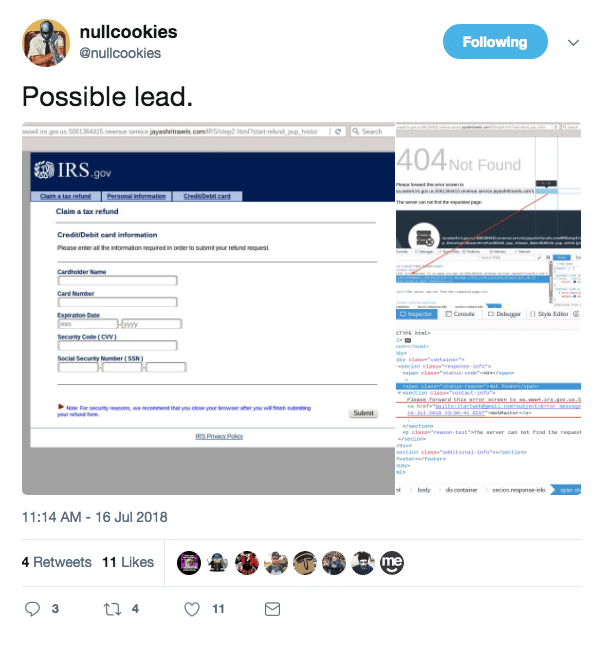
The other day I came across a tweet from @nullcookies referencing an apparent IRS tax scam. Nullcookies captured a few different indicators that might be helpful when investigating this potential scam. Why investigate you might ask? There are a few reasons an investigation would be helpful inside of an organization. First of all, it allows security teams to make decisions on prioritizing threats based on their relative risk to their network. Secondly, by pivoting through infrastructure connected to an indicator, you can gain insight into not only the tactics of a threat actor, but potentially their intent. Finally, this mapped infrastructure allows you to peel through archived logs to see if users on your network have interacted with this threat actor in the past, and to make a custom blocklist or alert based on their infrastructure to dodge future attacks.
Assessing Risk
Looping back to taxes and tax scams (these are not a few of anyone’s favorite things), let’s apply the investigative method to the IRS scam indicators. Nullcookies provide us with a few interesting starting points, for the purpose of this example, we’ll be staring our search with a domain name; Sa.www4.irs.gov.us.5061364415.revenue.service.jayashritravels[.]com. Before we begin our investigation, there are a few interesting things to note right off the bat. This domain has 8 subdomains, which raises some red flags as extensive subdomain usage is a tactic used to obscure the destination domain by throwing enough gibberish at the end user that they give up on trying to find it. It also includes a string resembling a phone number, and quite a few allusions to the IRS.
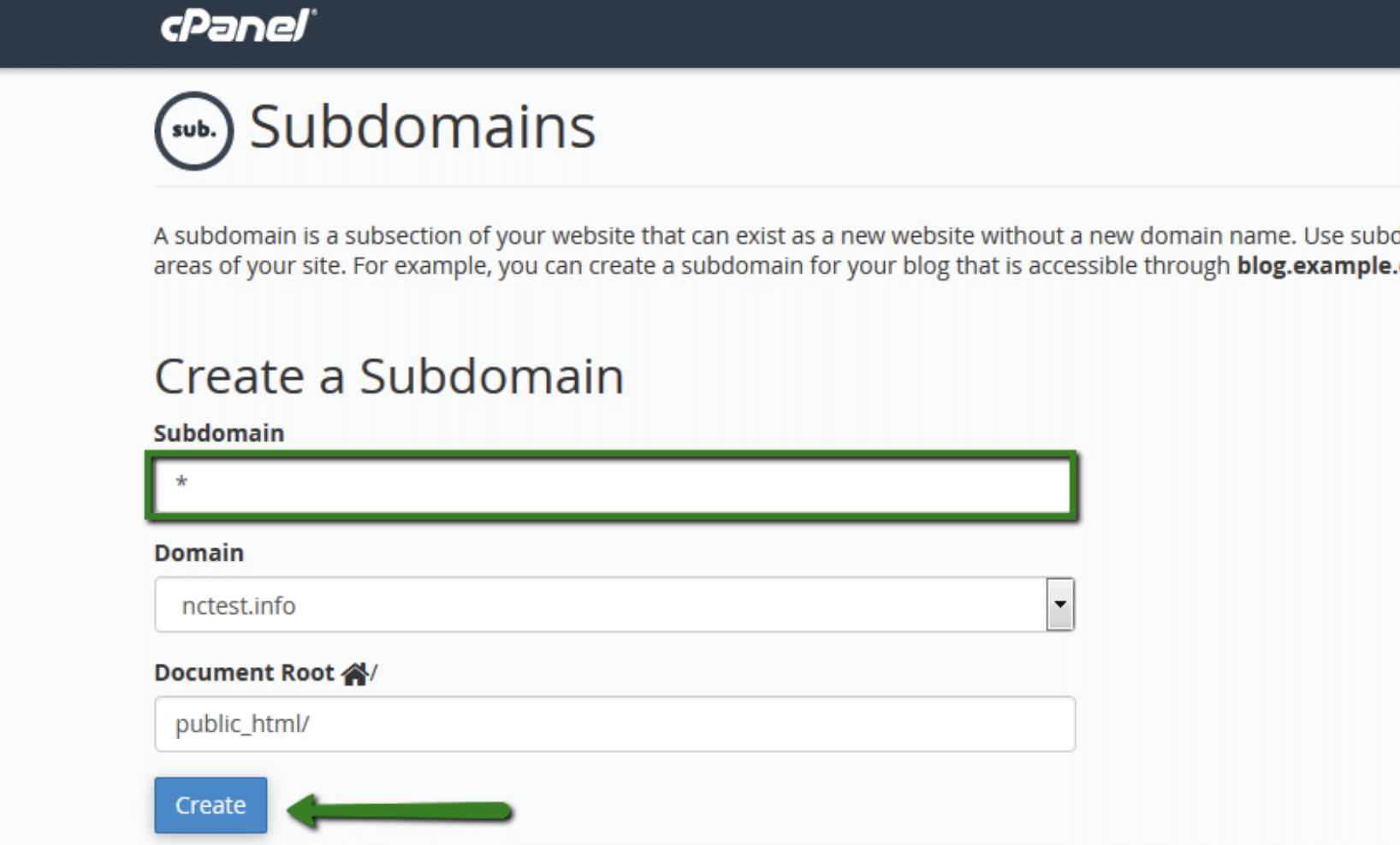
As a quick note, it is fairly simple to stand up subdomains. Below is a quick screenshot of how someone could go about setting subdomains up on cPanel.
Let’s throw the domain itself (jayashritravels[.]com) into Iris Investigate to see what else we can learn about this potential threat.
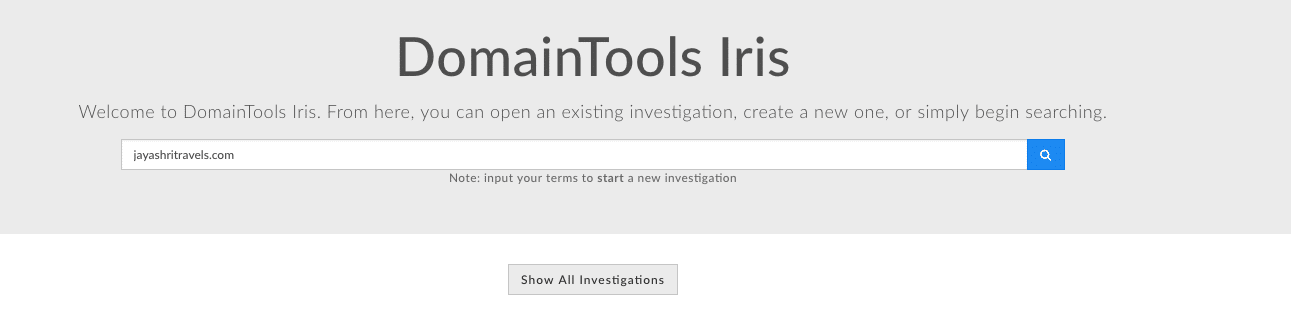
DomainTools Iris Investigate allows users to plug pretty much anything you can imagine into a search box whether it be an email address, an organization name, domain, IP etc. Iris Investigate then returns parsed records including information from DNS and website crawling like Whois, SSL certificates, and Google Analytics code. This is a great place to skim for additional red flags. A few things jump out at me in this scenario.
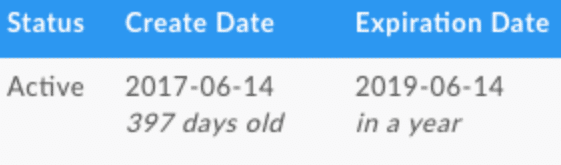
The domain itself is a little more than a year old (happy belated birthday there domain!). Additionally, the domain risk score is 100, meaning badness has already been observed, and the domain has been added to industry blocklists.
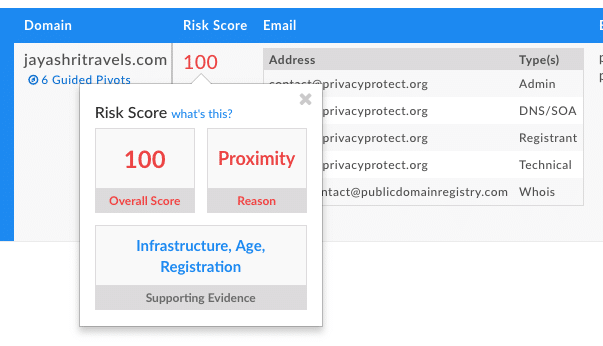
Finally, I’m curious if there is any indication of badness in the screenshot history. After pulling up this snippet, I googled the site and phone number only to find what appears to be a legitimate business complete with reviews and accurate contact information:
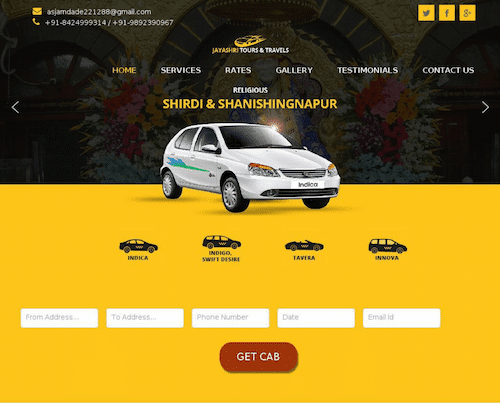
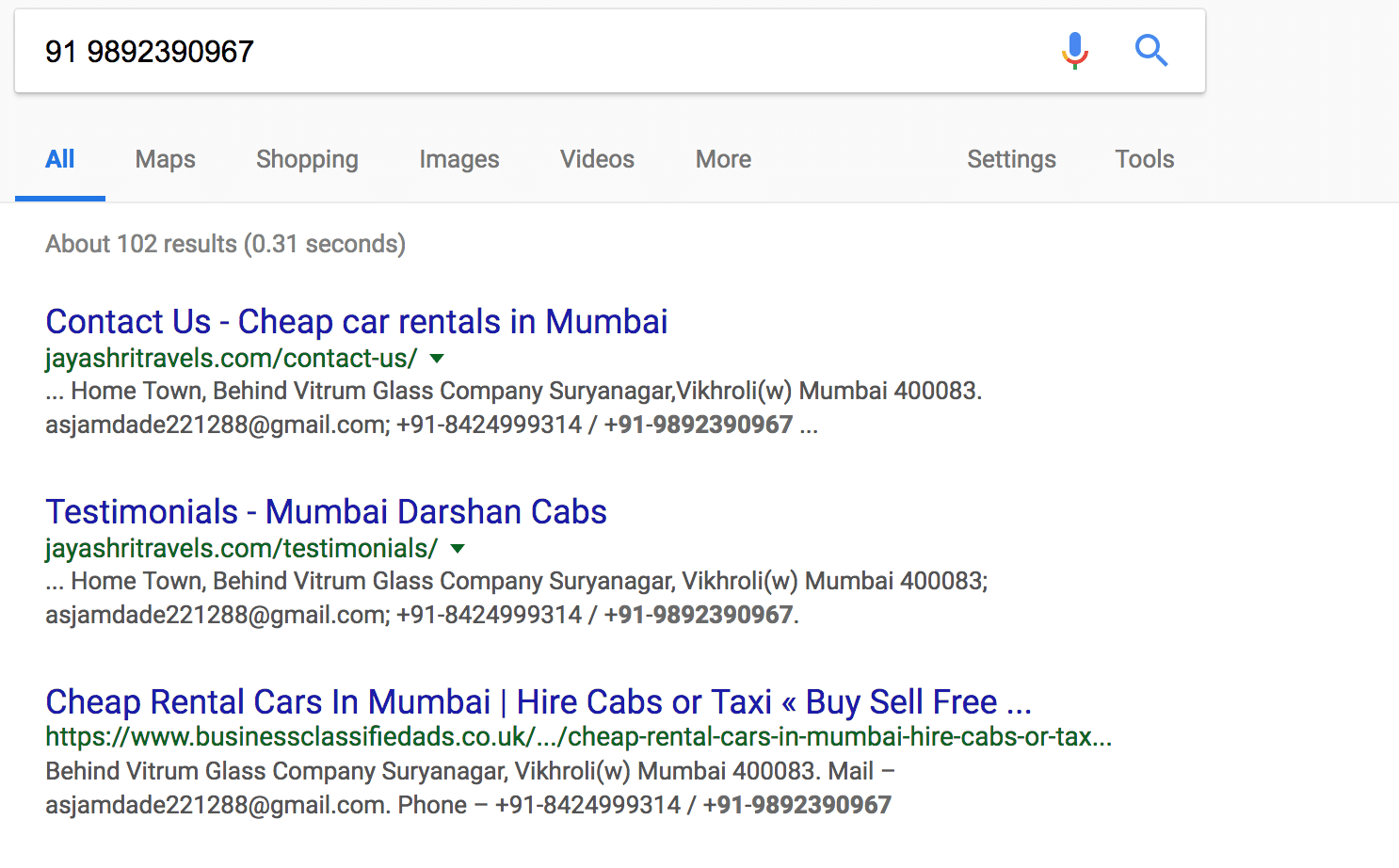
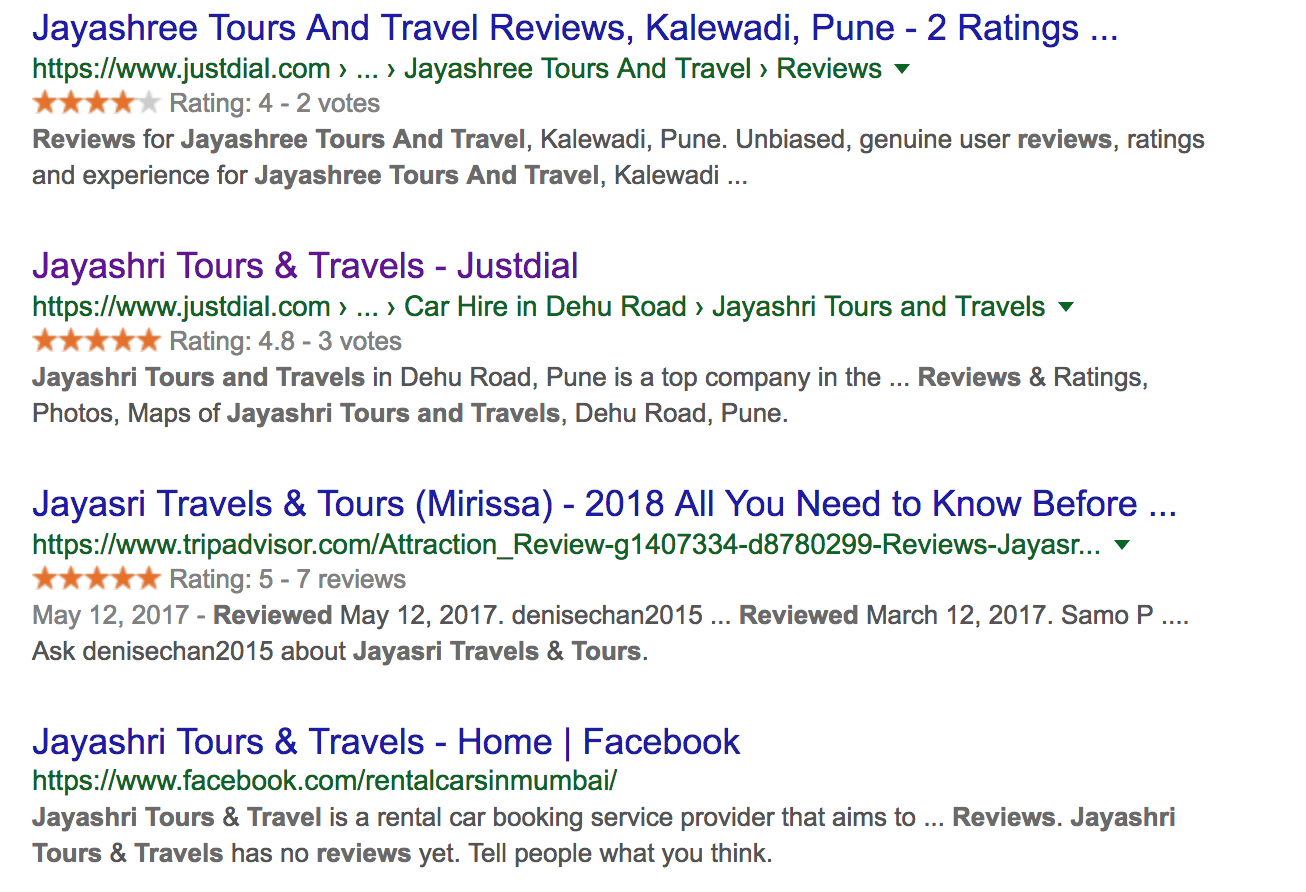
This new information leaves me with more questions than answers, so it’s time to dig deeper and understand if potentially this domain was hijacked? Are they running a sophisticated campaign? How worried should I be? To answer this, I need to map the connected infrastructure.
Mapping Connected Infrastructure My first inclination is to right-click on the IP address to see if there are any other domains hosted on this IP and it turns out there are 62. There is a pretty clear indication when expanding on this IP that there are some rotten domains associated with this IP (see screenshot below).
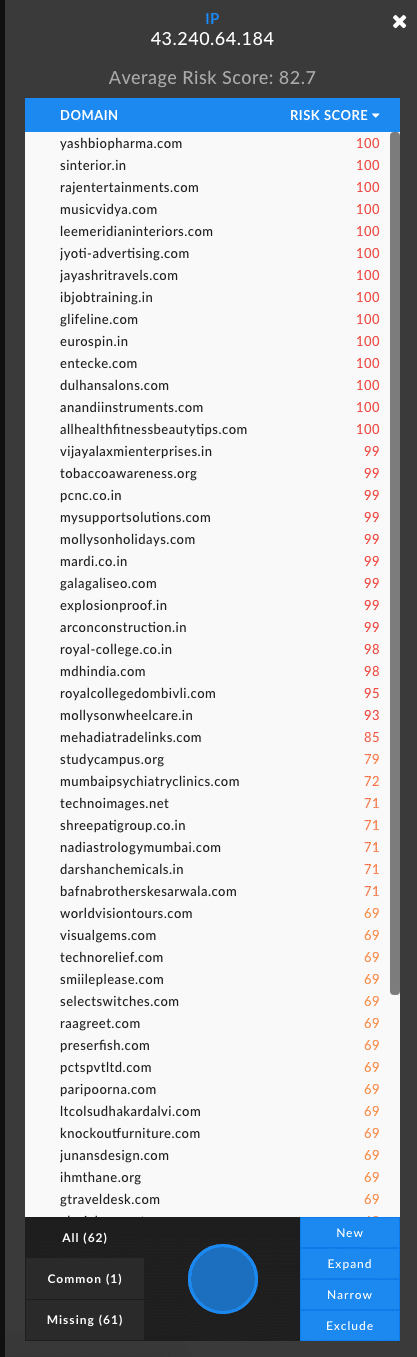
Now that we have a sense of how many domains are hosted on this infrastructure, I’m curious as to whether we can find evidence that this domain name has been hijacked, so I’ll look at the hosting history for more context. To do this, I’ll inspect the passive DNS resolution, which will unearth any subdomains like the 8-subdomain-wonder referenced in the tweet. To do this, I simply right-click on the domain and select pDNS.
To help expand the search, I’ll add a wildcard to the domain so we can see all of the subdomains that have ever been active including the subdomain that inspired this investigation. A few things to note from this list: the IP address 37.187.87[.]192 is looking malicious and it’s certainly not something I’d want to come across in my logs. This search also has made it pretty clear as to the intent of the threat actor and scope (they aren’t just targeting the US, but the HMRC UK tax program). Lastly, note the unique strings in subdomains that vaguely resemble phone numbers.
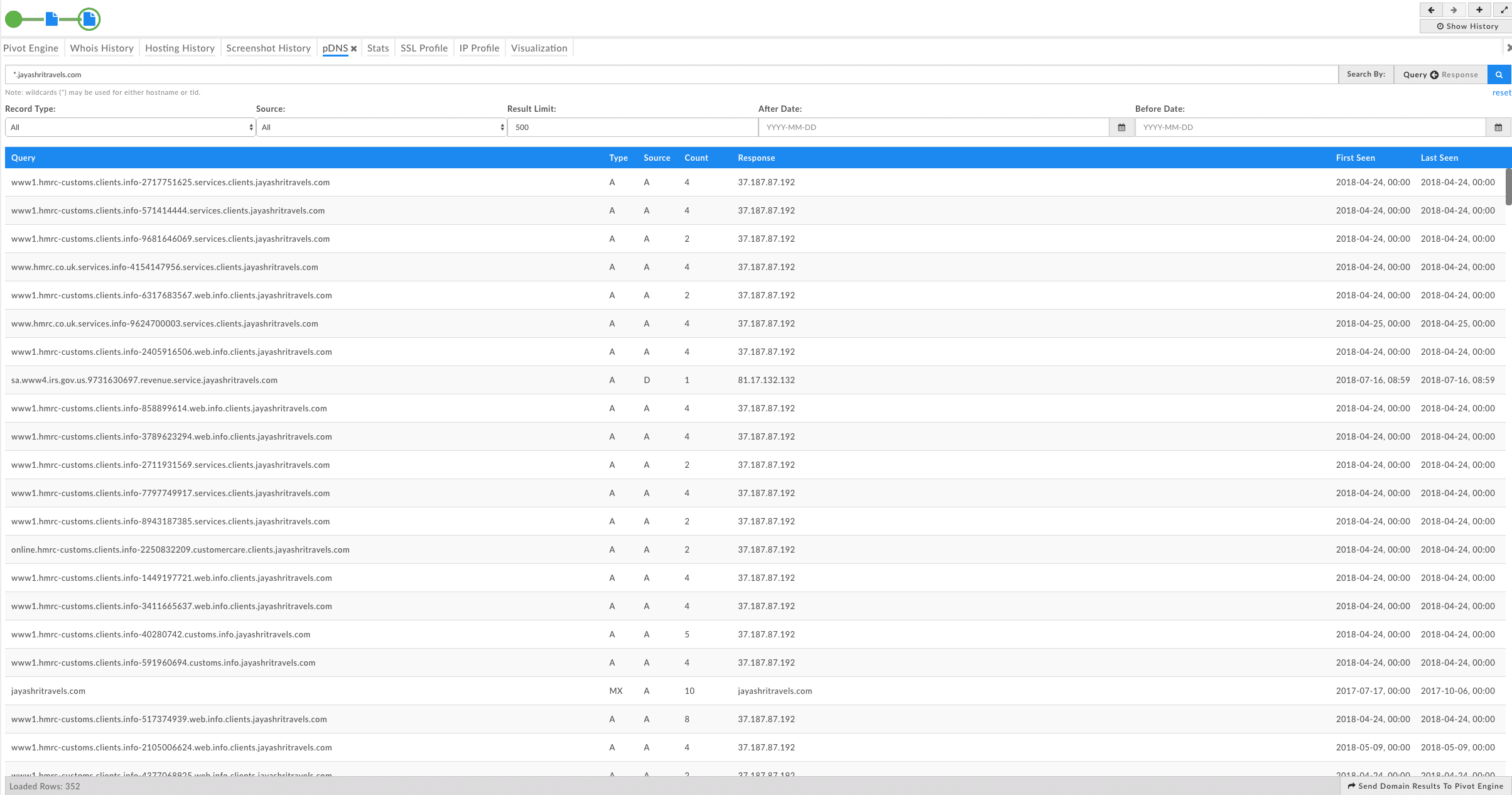
See a zoomed in example below:
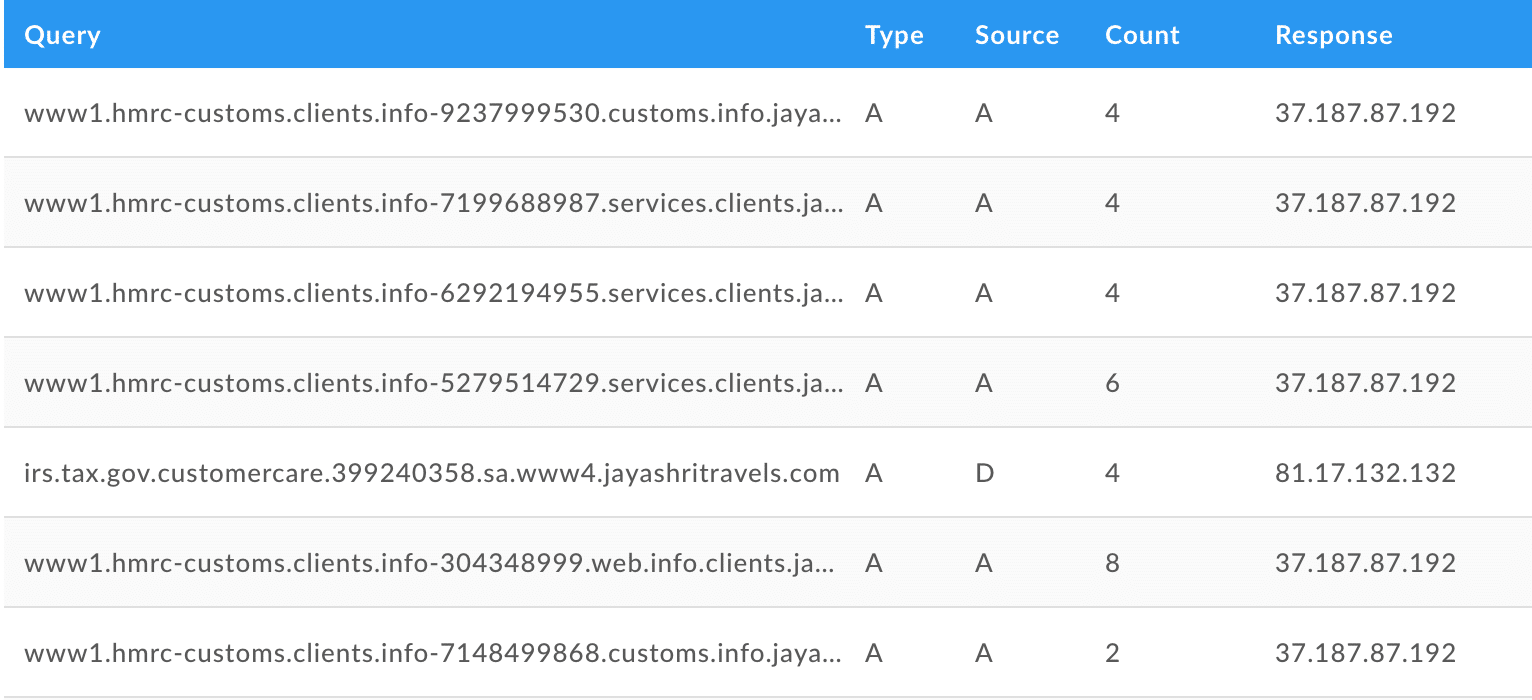
The scale of this campaign is fairly grand, but I still haven’t gotten a sense of the badness of those other 62 domains hosted on 43.240.64[.]84. To do this, I’ll go through each of these 61 other domains and repeat the passive DNS wildcard query. In doing so, I discovered that 56 of 62 domains have similar nasty subdomains associated with them. These campaigns were first seen in March of 2018, and are still currently active.
These campaigns targeted a number of organizations including United Kingdom, United States, and Canadian tax services, Apple, Paypal, Bitcoin, RBC, and AT&T. See a breakdown of domains with malicious subdomains targeting these organizations below:
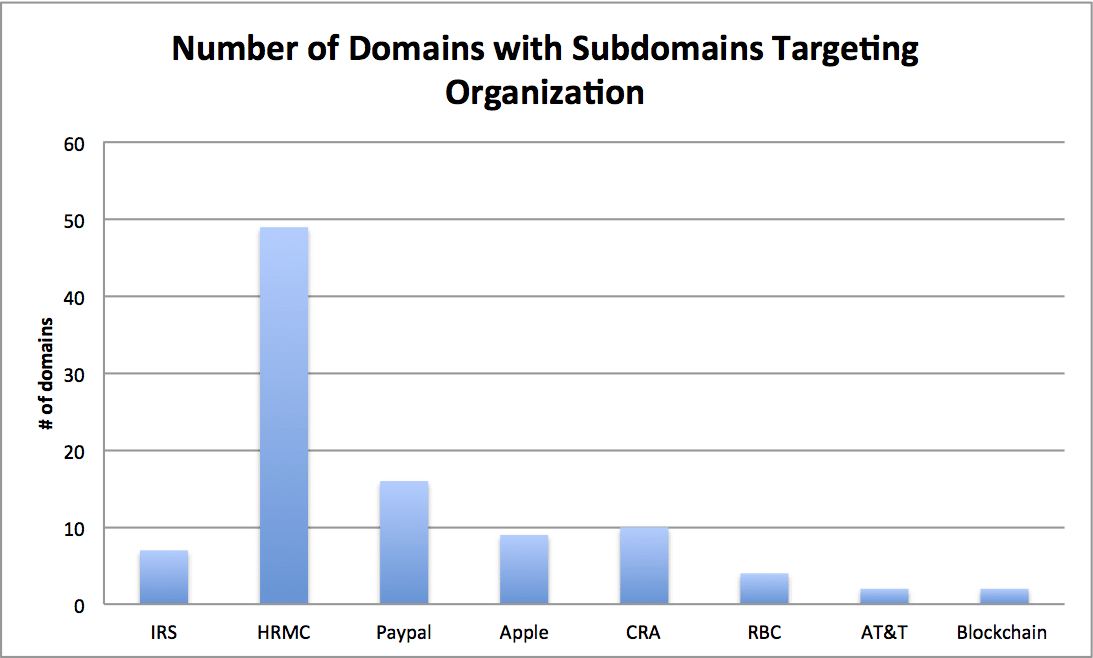
All of this evidence seems to point to an entire box being compromised, rather than a single domain.
Blocking and Alerting
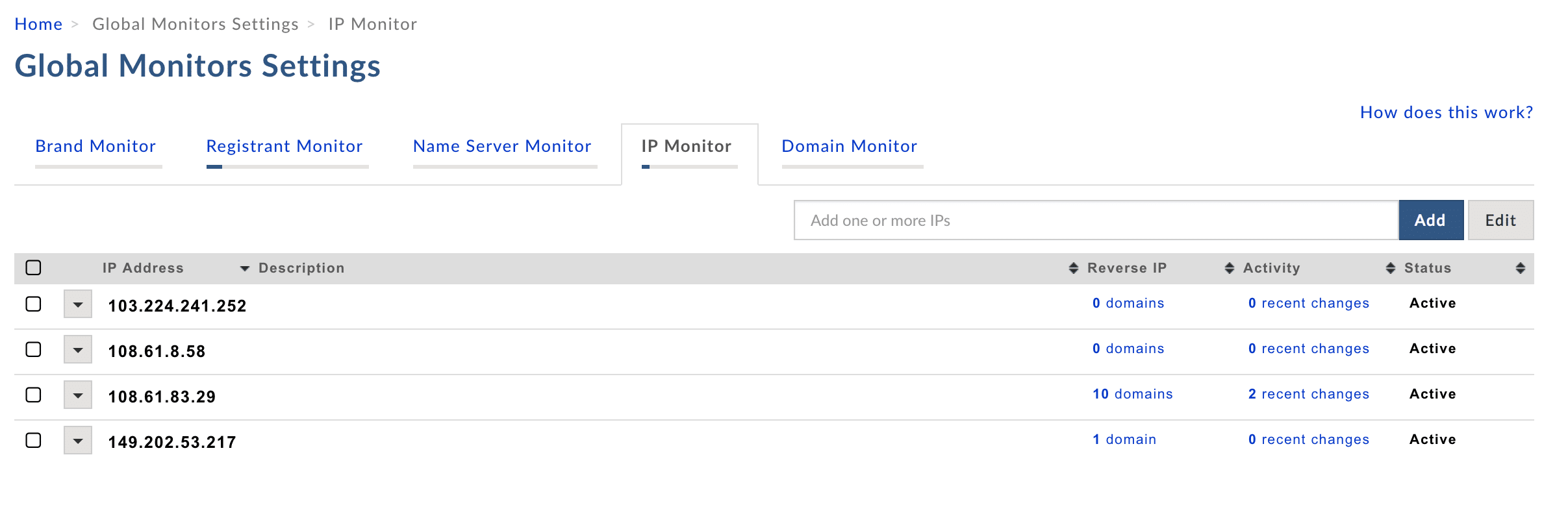
I collected a list of 40 malicious IPs used by this particular threat actor and you may be wondering, what do I do with a list of convicted IPs or domains? This is when organizations complete two very important tasks:
- Comb through their archived logs for these domains and IPs and see if this particular threat actor has already been on their network. If so, remediation will likely begin.
- Create a custom blocking or alerting list based on the IPs and domains you captured. As noted earlier, this threat actor appears to be moving infrastructure around, so pop them into an IP monitor to stay a step ahead of his/her next attack.
Conclusion
From one indicator (in this case a tweet but for security teams more likely their local ISAC, SIEM platform, or an APT report) we were able to quickly assess the relative level of badness of this 8-legged subdomain, expand on and unearth many more IPs connected to this campaign, and create a custom blocklist or alert to prevent this actor from booking a return ticket to an organization’s network. This investigation process took less than 10 minutes and created some actionable intelligence. If only taxes were so easy!
Appendix
Malicious IPs to Block
85.25.185[.]175
81.17.132[.]132
81.17.132[.]131
81.17.131[.]38
77.66.12[.]128
69.89.15[.]195
69.89.11[.]126
68.169.59[.]198
62.128.220[.]127
50.62.78[.]11
5.39.89[.]151
43.241.37[.]229
43.240.65[.]36
43.240.64[.]184
37.187.87[.]192
31.14.134[.]101
27.131.161[.]40
23.91.64[.]210
23.88.120[.]197
212.124.114[.]242
192.241.180[.]110
192.169.236[.]74
184.106.196[.]78
180.149.242[.]176
178.62.92[.]140
167.114.92[.]115
160.36.178[.]73
150.242.140[.]20
150.242.140[.]135
150.242.14[.]134
150.242.14[.]132
150.242.14[.]103
149.202.53[.]217
108.61.83[.]29
108.61.8[.]58
104.131.77[.]93
104.130.69[.]245
104.130.69[.]200
103.228.152[.]44
103.228.152[.]26
103.228.152[.]212
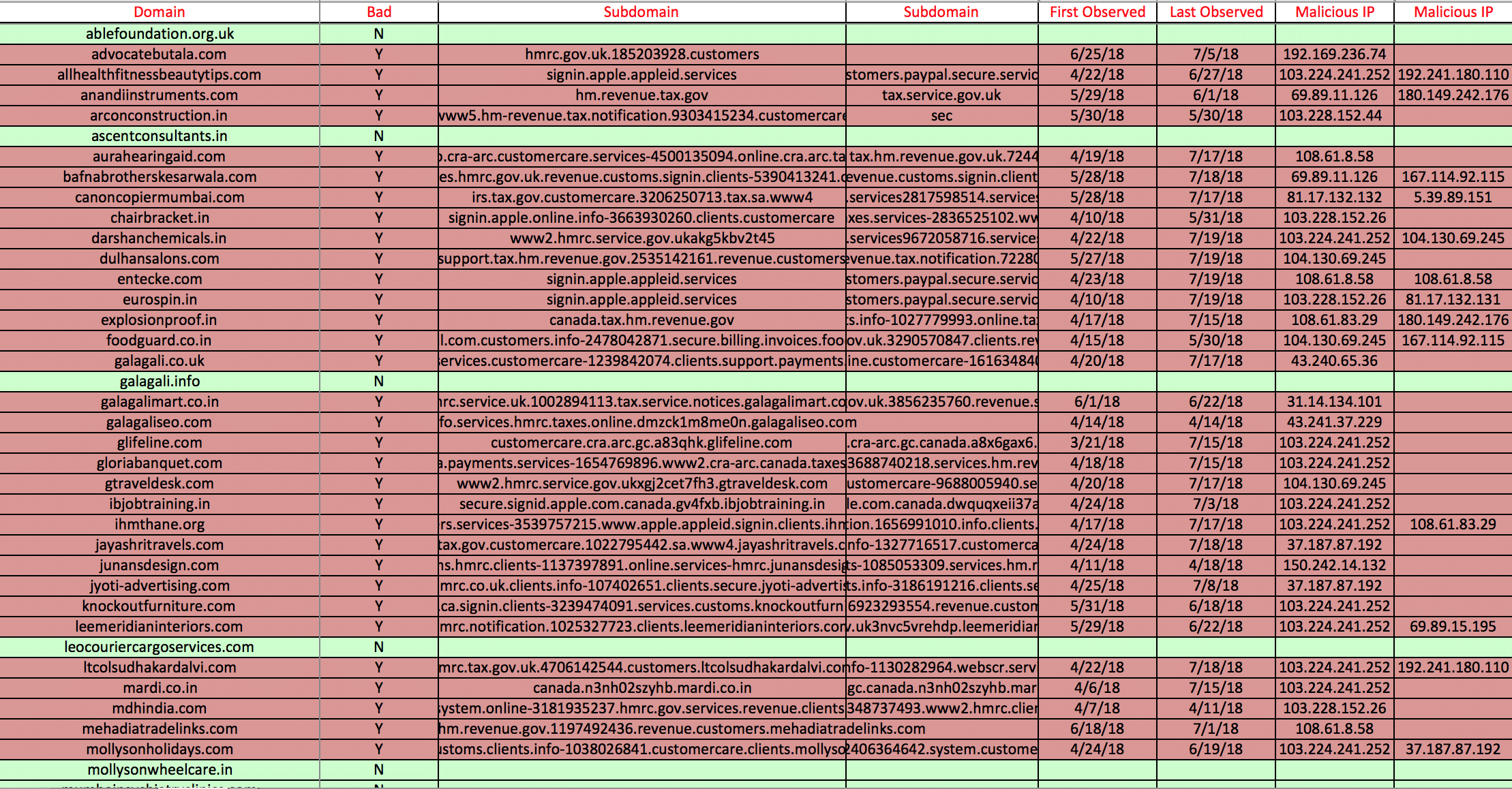
Impacted Domains
advocatebutala[.]com
allhealthfitnessbeautytips[.]com
anandiinstruments[.]com
arconconstruction[.]in
aurahearingaid[.]com
bafnabrotherskesarwala[.]com
canoncopiermumbai[.]com
chairbracket[.]in
darshanchemicals[.]in
dulhansalons[.]com
entecke[.]com
eurospin[.]in
explosionproof[.]in
foodguard.co[.]in
galagali.co[.]uk
galagalimart[.]co[.]in
galagaliseo[.]com
glifelin[.]com
gloriabanquet[.]com
gtraveldesk[.]com
ibjobtraining[.]in
ihmthane[.]org
jayashritravels[.]com
junansdesign[.]com
jyoti-advertising[.]com
knockoutfurniture[.]com
leemeridianinteriors[.]com
ltcolsudhakardalvi[.]com
mardi.co[.]in
mdhindia[.]com
mehadiatradelinks[.]com
mollysonholidays[.]com
mysupportsolutions[.]com
nadiastrologymumbai[.]com
paripoorna[.]com
pcnc.co[.]in
preserfish[.]com
raagreet[.]com
rajentertainments[.]com
royal-college.co[.]in
royalcollegedombivli[.]com
selectswitches[.]com
shreepatigroup.co[.]in
sinterior[.]in
smiileplease[.]com
spectratankclean[.]com
studycampus[.]org
technoimages[.]net
tobaccoawareness[.]org
vijayalaxmienterprises[.]in
visualgems[.]com
worldvisiontours[.]com
yashbiopharma[.]com


