DomainTools 101: The IP Crowd
I recently read a couple of great blog posts about the breach that occurred at the Democratic National Committee. These posts go into greater detail about Spear Phishing and how the threat actors go about breaching you and your company. I would really recommend reading both of them. The first article is written by Crowdstrike, and then ThreatConnect expanded on Crowdstrike’s research. The key takeaways from these articles is that the threat actors are very sophisticated, and have an arsenal of tools and software to attack you. The second highlight was that the threat actors almost exclusively used a broadly targeted Spear Phishing attack method. This attack included typo squatted styles of domains and a weaponized parked domain.
The DNC breach is a great example of how to leverage monitors in order to stay ahead of similar attacks, so for today’s post, I would like to dive a little deeper into Domain Tools Monitors, and how they can help you to get ahead of the threat actors, which ties in to our motto of “See Threats Coming”. According to the ThreatConnect blog post, “Farsight lists the earliest domain resolution as March 24, 2016. On April 24th, 2016 the domain misdepatrment[.]com moved from the parking IP Address 5.135.183[.]154 to the FANCY BEAR Command and Control IP Address 45.32.129[.]185”. This illustrates a common strategy where threat actors will create domains and leave them pointed at a parking IP addresses until they want to weaponize them and make them active in their attack. Now that I have 2 known IP addresses, I can use the IP Monitor and Name Server monitors to get a notification if any domains are pointed to or away from those IP addresses.
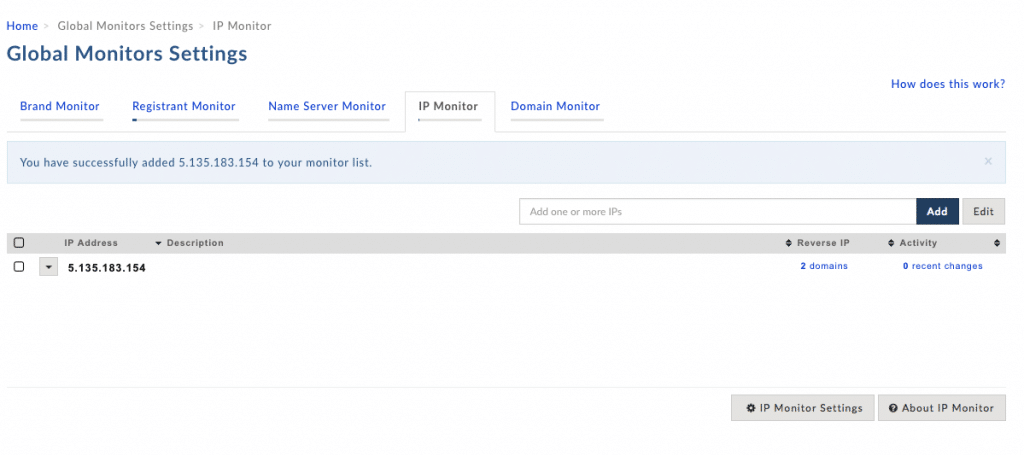
When I setup my monitors with Domain Tools, I will now have the ability to see the domains that are currently being hosted at a specific IP address and using Name Servers, but more importantly I can use those monitors to notify me when the threat actor provisions a new domain and points it at the IP address that I’m monitoring. Additionally, I can identify when threat actors move it from the IP address that they are using to park domains to the IP address that they are using as a part of their Command and Control infrastructure.
This will then open the window to learn more about the threat actor and their Tactics, Techniques and Procedures. I can begin to map out the infrastructure that they have access to, learn where they park domains, and when they bring them online, what is the range of IP addresses that they use. In many instances we can also learn more specifics about the threat actor, what email address do they use to register domains, how many domains do they own, of those domains how many are currently flagged as blocked domains.
In conclusion the key take away from the Domain Tools monitors is the ability to stay ahead of the threat actors, by learning more about them, and using that knowledge to protect your brand, track new domains registered by threat actors, using that expanded knowledge to track their infrastructure, and stop them in their tracks.
*ThreatConnect published two other articles regarding the DNC Breach: Shiny Object? Guccifer 2.0 and the DNC Breach and What’s in a Name Server?



