DomainTools And Digital Archeology: A Look At RotaJakiro

Background
On April 21, 2021, Netlab released an excellent report on a malware sample they dubbed RotaJakiro, a long-lived backdoor targeting 64-bit Linux systems with 0 detections on VirusTotal. This backdoor used a number of techniques to remain unnoticed and the craftiness of the sample piqued the attention of the DomainTools Research Team. Netlab’s post ended talking about how analysis of the binary was just the tip of the iceberg in discovering what this sample was about and that is where we feel that DomainTools, with our thorough historical data set of over 20 years of Whois and DNS information, had to take a look. For analysis on the binary itself, we suggest reading their excellent post while we concentrate here on one of our specialties: digital archeology.
Initial Indicators
In this instance, the samples found by Netlab were first added to VirusTotal in 2018. As mentioned, none of them were detected by any of the engines VirusTotal employs. These samples all called out to C2 infrastructure of the following domains:
news.thaprior.net
blog.eduelects.com
cdn.mirror-codes.net
status.sublineover.net
A quick look in passive DNS shows that these domains only have these subdomains listed and they do not appear to be a part of any Dynamic DNS system so we can assume that the SLDs are owned by the same operator. We’ll look more at passive DNS later, but for now we can throw these domains into Iris Investigate to see more about their intrinsic properties.
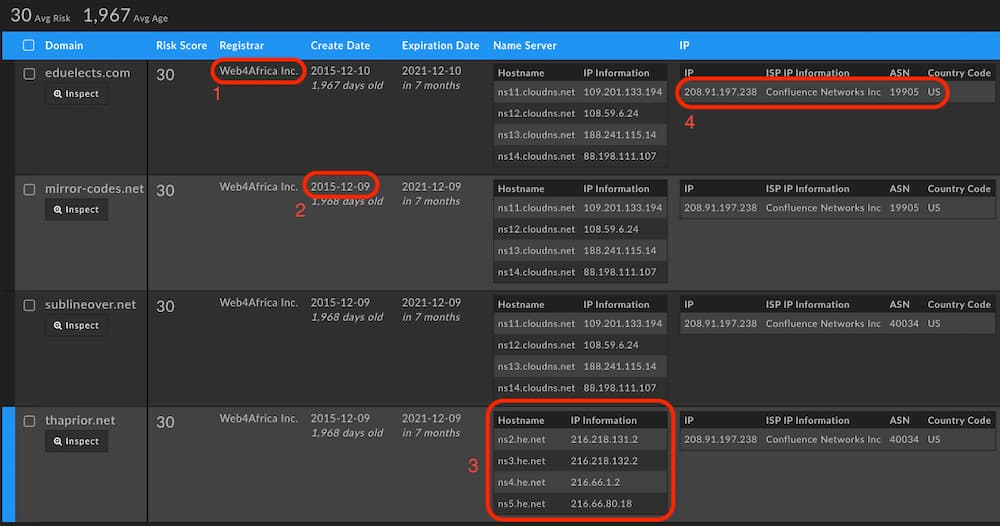
First is the use of the Web4Africa registrar. This registrar has just a little over 18,000 domains associated with it so the frequency of registration is rather low. Second, we see the registration dates are about the same for all of the domains being from December 9th and 10th of 2015. This aligns with the research from the Netlab report and may indicate that there are actually older samples to be found in the wild. Third, we see that all have the same nameservers except for one domain. Outliers are always useful as they often link to additional connections elsewhere in the broader domain name data set. Lastly, the use of the Confluence Networks IP for their apex A record which is only slightly valuable. This is a parking page IP address and makes sense as the operator of this backdoor used subdomains that all had A records to a specific IP address for C2.
Summary of Additional Information and What it Tells Us
Diving Deeper Than Domains
The first step from here is we look at Whois history. In this case, privacy protection has been in place since the domains were first registered in 2015. Most importantly we can tell that because the domain has never been allowed to expire,these weren’t domains that were dropped and re-registered. This lets us know that the same person has owned these domains since 2015. That is an important distinction to make as adversaries are increasingly aware that getting a drop catch domain is a nice way to immediately “age” a domain so it goes undetected as many machine learning algorithms rely heavily on registration date to determine malicious intent. We have certainly found that an overwhelming number of attacks come from newly registered domains in our analysis.
Since Whois history provides minimal additional points to pivot on, we can then turn to passive DNS. This data set of passively collected query and response pairs from recursive resolvers around the Internet shows a first and last seen entry for any pair along with a count. This can help determine both breadth of use as well as when something first began and was last seen operating. In the case of the IP address used for all four of the subdomains that were C2 infrastructure, we get the following list that shows activity as early as November 08, 2017 and as recently as April 29, 2021 which is the time of this writing. In addition to that we get three new domains pointing to the exact same IP address just a few months prior in 2017.
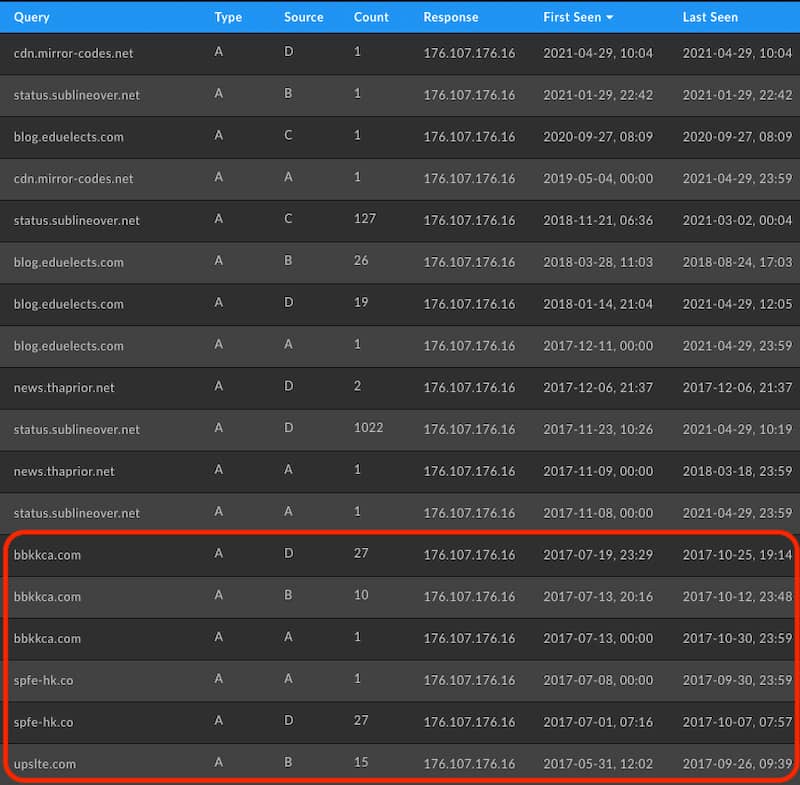
While this is interesting, it’s important not to jump to conclusions and tie this directly to the other domains. For one, the IP is tied to a Ukraine and Netherlands based VPS provider called DeltaHost. A VPS provider rents out servers and with that IP addresses. This IP could simply have been recycled that month when the operator behind RotaJakiro decided to become active. Secondly, there are no subdomain patterns that match the naming convention of the domains prior. Given that this IP has only ever hosted the confirmed RotaJakiro C2 domains and these new domains, though, it behooves any analyst to take a closer look.
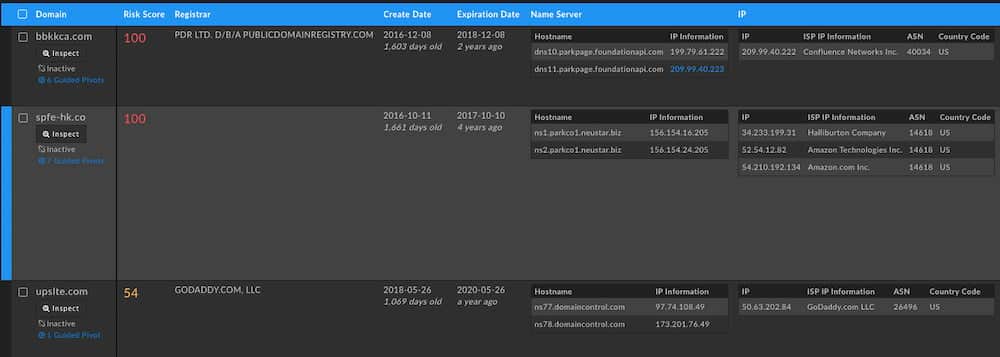
Unfortunately, these three additional domains do not provide anything that can definitively tie them to the other domains. They lack any overlapping times in passive DNS records and their registration patterns are different. One oddity however is their Risk Score of 100. The DomainTools Risk Score is informed by a number of things, but a score of 100 is indicative of a domain being included on a blocklist for a previous report of known badness. Looking at historical Whois for these domains we see them with a registrant email of daniel.madi@mail[.]com who is tied to 88 Office 365 based phishing domains.
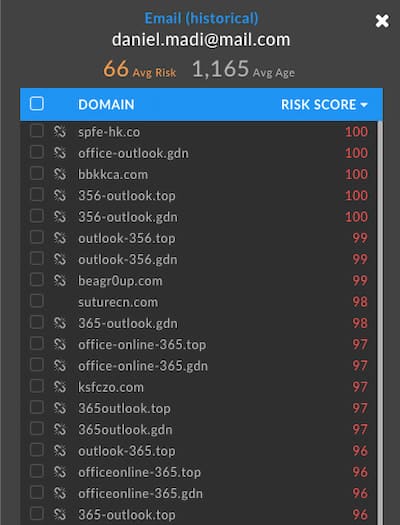
Given the complexity and stealth of the RotaJakiro backdoor it seems unlikely that such a noisy phishing campaign would be so easily tied to such a quiet operation. If we were to tie these together it would be with extremely low confidence. We feel as researchers that it is much more likely that DeltaHost recycled this VPS IP address shortly after the blocklisting of these domains and it was coincidentally used in other criminal activity and that the IP address was picked up by the RotaJakiro operators. In support of this, passive DNS records show that one of these older domains was suspended just before the C2 domains for RotaJakiro began operating on that IP address. Passive DNS also shows the RotaJakiro C2 domains existing on other IP addresses prior to moving to DeltaHost. Both of these facts support the theory that these are separate.
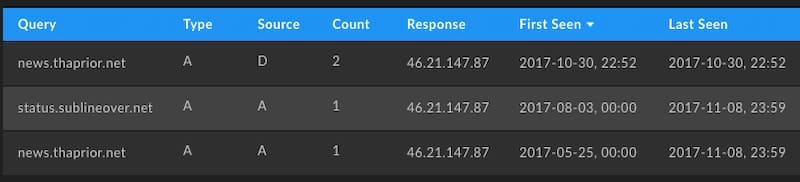
This IP now belongs to Hivelocity, a small cloud provider that has only owned the IP address since 2019 according to the create date on the IP Whois record for their subnet. According to historical IP Whois information, Hivelocity acquired this range from Swiftway after acquiring the company which had server locations in the Netherlands. The IP shown, 46.21.147[.]87 is still geolocated in the Netherlands.
Unfortunately, we also cannot find any connections between the C2s mentioned in Avast’s Torii botnet report from 2018 and the domains in the RotaJakiro report. Netlab did mention similarities between RotaJakiro and the Torii botnet in their operation. If there had been a tie between those domains even and the daniel.madi@mail[.]com domains we could increase our confidence in them belonging to the same operator.
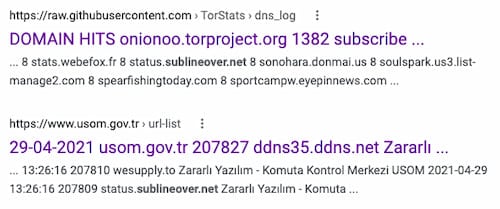
Sometimes when reaching a dead end on infrastructure databases the best thing for us as analysts to do is turn to traditional search engines. Throwing in the initial C2 domains we discovered and a few interesting hits came up. The first is a link to a 2016 repository of Tor DNS logs that show to us that this domain has at least been accessed since 2016. The second is from a Turkish government website and is a URL list in XML format. The domains are mentioned as appearing on April 29, 2021, same as the time of this writing, from the Zararlı Yazılım Komuta Kontrol Merkezi which is Turkish for Malware Command Control Center, likely having been an ingestion of the original Netlab report.
Summary of Additional Information and What It Tells Us
Conclusion
Although we were unable to tie the Netlab report on RotaJakiro to another operator, we have produced a good amount of evidence and potential conclusions for further analysis. We’ve been able to confirm timelines from the Netlab report as well as mark key oddities for further avenues of investigation. We were also able to identify additional IP addresses which had been previously used by the C2 domains and would lower the threshold of confidence for tying this to previous maliciousness. When all else brought us to a dead end we were able to expand upon our original timeline thanks to good old fashioned OSINT using classic search engines. Whenever coming across reports like this we hope that customers can find DomainTools useful in the practice of digital archeology.


