1, 2, 3, 4 Tell Me That You Love Newsletters
Subscribe to the Newsletter here
Welcome to the fourth iteration of my DomainTools Investigations (DTI) newsletter! I’m glad you’re back – and if you’re new, what you’re about to read is news from our group of researchers and analysts providing their expertise in investigating, mitigating, and preventing Domain and DNS based attacks.
Before we begin, you may have noticed some of my Carmen Sandiego-inspired social posts about where I’ve been traveling recently. I thought I’d take a moment to catch you up on where I’ve been (scroll to the end of the newsletter to see where I’ll be coming up in the next few weeks).
April is Spring Break Season for most of the United States. We usually meet up with other members of the extended family somewhere in the country, and explore new places. This year, we chose New Mexico, the Land of Enchantment™. I had never been, and I’malways excited to check a new state off my list (this makes number 30 for me!).
We flew into Albuquerque, and checked out a few locations from the TV Show Breaking Bad.

Then we move on to Santa Fe, which besides being the State capital, it’s also a fun place with lots of interesting places to see. Meow Wolf, the underground art collective and immersive experience was definitely one of the highlights!

Another highlight was the visit to the Puye Cliff Dwellings, a settlement that was inhabited as early as 900 AD. The dwellings on top of the mesa top were their summer homes, whereas the cliff side dwellings (partially carved into the cliffs) were the winter homes.

The Puye is great because it has many ancient ruins, but also a few examples of buildings that are accurate reproductions of the original dwellings.

The one thing I didn’t realize until on day two of the trip, when I got a pretty bad headache that wouldn’t go away, is that Santa Fe is at around 7000 feet elevation. As a sea level dweller for over half of my life, I got a nasty case of altitude sickness! Drinking lots of water helped, but it took a bit to acclimate. This concludes this month’s travel round-up, let’s jump into what the DTI team has been up to since my last newsletter:
The Domain Event
In case you missed it, DTI published its inaugural Domain intelligence year-in-review report (cue the confetti!🎉).
In the cybersecurity community, it’s generally accepted that the threat landscape is fast paced and ever-evolving. It turns out however that there are a few constants that rarely change: Domains and DNS are on top of that list. The purpose of this report is to illuminate Domain patterns and DNS infrastructure created by cybercriminals in order to collectively improve the community’s defenses.
What were some of the key findings, you may be asking yourself?
- Risk Scoring Detection Techniques: the likelihood of a Domain’s proximity to malware, phishing, spam, etc. to enable prioritization for further investigation and analysis.
- Keyword Analysis of Threat Detection: clear patterns of newly created Domain names that included frequently included terms such as “phishing,” “fraud,” “bitcoin,” “scam,” and others.
- High Publicity Event Exploitation: large events spurn Domain registration including elections/politics, technological advancements, natural disasters, social movements, and so on.
- Commonalities in Malicious Domain Attributes: recurring patterns in preferred registrars, ISPs, nameservers, and SSL issuers used by malicious domains.
- Analysis of Newly Registered Top Level Domains (TLDs): analysis to understand how threat actors utilize new TLDs (.lifestyle, .vana, .living, .music – to name a few) in their campaigns.
Want more? Of course you do! Find the full report here.
Looking for more of a highlight reel? Find the summary blog post here.
April Was Showered with Research
The team was busy during the month of April, which makes me extremely proud. In case you missed it, here’s what the team worked on:
Get Your Kicks with Proton66
In this analysis, DTI explores Proton66, a Russian bulletproof hosting provider that supports cybercriminal activities by ignoring abuse complaints. It highlights the activities of Coquettte (the three T’s are not a typo), an emerging threat actor using Proton66’s infrastructure to distribute malware and engage in illicit projects, including a website hosting guides on manufacturing illegal substances.
![A screenshot of a fake cybersecurity website, cybersecureprotect[.]com, masquerading as a legitimate antivirus service](https://cdn.prod.website-files.com/6914bc46af7a937a5c07eea3/69401d96f904b22e8abe0671_april-newsletter-image-5.png)
Why is This Important? This analysis sheds light on the infrastructure supporting cybercriminal activities, specifically through Proton66. By understanding how threat actors like Coquettte operate and utilize such services, cybersecurity professionals can better detect and mitigate these threats.
Harriet the SpyNote Malware
Here, we looked at how deceptive websites hosted on newly registered domains are being used to distribute SpyNote malware. These sites mimic the Google Chrome install page on the Google Play Store to trick users into downloading SpyNote, a potent Android remote access trojan (RAT) used for surveillance, data exfiltration, and remote control. The research details the common patterns in domain registration, website structure, and malware configurations, noting the use of both English and Chinese-language delivery sites as shown below:
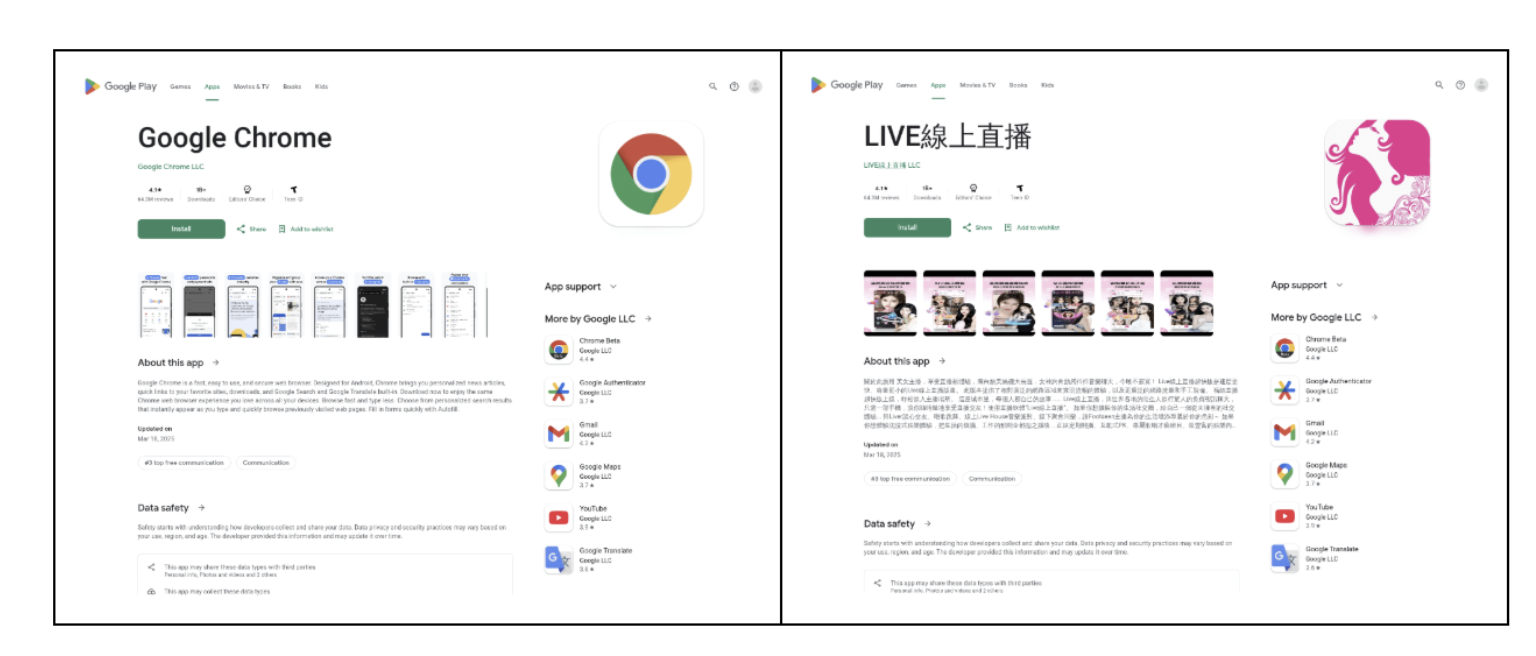
Why is This Important? SpyNote is a potent Android remote access trojan (RAT) that can steal sensitive data, including personal information, financial details, and credentials. Understanding its distribution methods helps in developing better defenses.
Juiced Up and AI Sloppy
I can’t resist the opportunity to reference a Rolling Stones song – especially when it comes to the idea of AI slop. Here, we illustrate how deceptive browser extensions within the Google Store manipulate ratings and transmit user data. These extensions, often promoted through newly registered websites, pose significant privacy and security risks and this analysis highlights common traits among these extensions, such as manipulated reviews and external data transmission, and provides insights into identifying suspicious extensions by examining their code and user feedback.

Why is This Important? These extensions could transmit sensitive user data without consent, leading to privacy breaches (a topic I’m incredibly passionate about). It also helps security practitioners to potentially identify and remove malicious extensions and helps maintain the integrity and security of users’ browsing experiences.
Book It
Remember that program from Pizza Hut? Getting rewarded for reading by getting some free pizza? I can’t give everyone a free pizza for reading Ian Campbell’s reading list digest, but I promise you the reward is becoming a better defender through shared knowledge (and that lasts way longer than pizza!)
Some of the topics Ian included in his recent reading lists include:
- Exposed Credentials & Ransomware Operations: Using LLMs to Digest 200K Messages from the Black Basta Chats – SpyCloud
- 4chan Is Down Following What Looks to Be a Major Hack Spurred By Meme War – 404 Media
- Disrupting Fast Flux With Protective DNS – Infoblox
Be sure to check out the reading list for his full recommendations!
Where We’ll Be
- TechNet Baltimore – May 6-8
- Catch my colleague, Malachi Walker, and the DomainTools Federal team at this three-day event
- GISEC – Dubai – May 6-8
- For those who will be in this neck of the woods, come find me here – I’d love to say hi!
- I’ll be presenting “Trends in Malicious Domain & DNS Infrastructure” on May 6 beginning at 2:05PM in Hall 6 on the Xlabs stage. Learn more here.
- Closed Door Session (Invite-Only, TLP:RED research – say I referred you)
- Washington DC, June 5
- SleuthCon June 6
- DomainTools is one of the sponsors for this event and Malachi will be present here, too!
- I’ll also be presenting “Seeing is Believing: A Visual and Analytical Map of Russian-affiliated Ransomware Groups” with Analyst1’s Jon DiMaggio. Learn more here.
Final Thoughts
Again, if you’re a returning reader from last month, I thank you. If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers.
We share this newsletter via email as well – if you’d prefer to get it to your inbox, sign up here.
If you missed last month’s content, here are some quick links:
- Phishing Campaign Targets Defense and Aerospace Firms Linked to Ukraine Conflict
- Domain Registrars Powering Russian Disinformation: A Deep Dive into Tactics and Trends
BUT WAIT. There’s more! Would you like to hear more about our Russian disinformation research? In this episode of the Breaking Badness Cybersecurity Podcast, I chat with disinformation expert, Scot Terban, about how Russian threat actors are evolving their playbook to mimic small-town US newspapers to push propaganda. Find the recording here.
Thanks for reading – see you next month!
Daniel



