DomainTools Iris App for Anomali
A few months back, in early 2019, I found myself on a customer call with a SOC manager who begrudgingly admitted how much his team had come to value the DomainTools Iris research platform.
A year prior when the same manager passionately proclaimed “I only want my team using Anomali, there’s no reason for them to look anywhere else!”
He had come to realize that domain name investigations, when informed by the rich dataset of ownership, infrastructure, SSL and web crawl data available in Iris, can be a powerful complement to other threat intelligence activities enabled by Anomali Threatstream. Even the pivot capabilities in Iris, too often considered an advanced feature for Tier 3 responders, had proven essential for his Tier 1 analysts, because it helped them quickly assess threats by discovering other connected domains, IPs and hostnames.
As pleased as he was with these outcomes, the SOC manager remained concerned with the context switching necessary to benefit from Iris, and he challenged us to work with the Anomali team to get Iris the data deeper in Threatstream. That certainly made sense to me: I’ve long sought opportunities to extend the existing DomainTools integration Anomali built into Threatstream way back in its early stages.
The opportunity crystalized in recent months as Anomali extended their “Investigations” concept deeper into their platform and also released a new software development kit (SDK) that allowed us to build a full-featured integration with the Iris Investigate API.
Enterprise customers with DomainTools Iris can now see nearly everything we know about a domain directly on the observable details in Anomali, including Whois data, infrastructure details, SSL certificate hash and subject details, web crawl data, and more. Domain Risk Score features prominently with a graphical treatment enabled by the Anomali SDK that quickly shows the overall risk of the domain, plus offers the component scores and machine learning classifiers that informed that score.
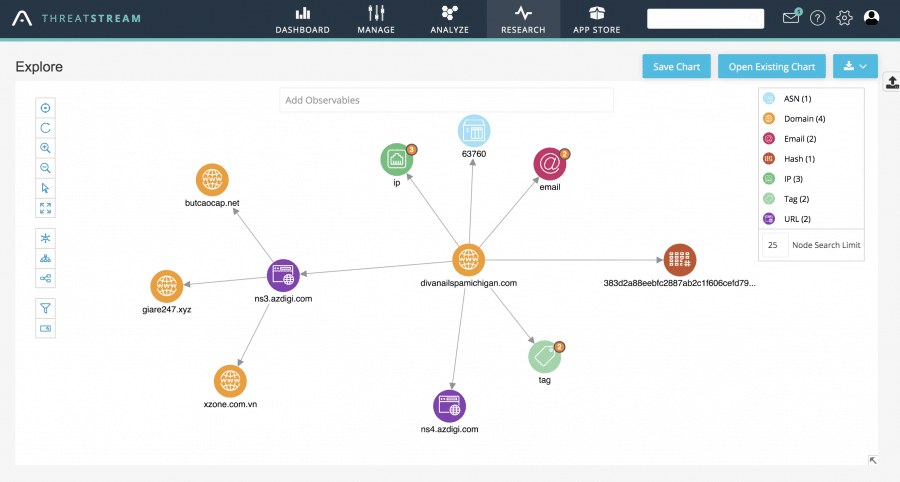
If you’re looking at an IP, hostname, or SSL hash observable, you’ll have the option to discover other domain names connected to that observable, including a handy chart that reveals the distribution of risk scores across those domains.
These capabilities are enabled by the Context Enrichment feature in Anomali that provides insights on individual observables. The DomainTools Iris App also provides Pivot Enrichment capabilities that extend the “Explore” feature in Anomali to a subset of the most essential pivots in Iris. You can right-click on a domain, IP, hostname or SSL hash and find related domains that enable further pivots.
Overall, we were very pleased with the ability Anomali gave us through their SDK to integrate so deeply in their platform, and we’re excited to provide this integration to our mutual customers.
I knew we’d done something right when I showed the SOC manager an early version of the DomainTools Iris App for Anomali and he declared “this is exactly what we were looking for” and even went so far as to say “we’ll start using this as soon as it’s available.” High praise indeed!
The app is powered by the DomainTools Iris Investigate API, which means you can use the app in Anomali today if you’re already an enterprise customer with access to the DomainTools Iris research platform (API access is included at no extra charge). We’re also happy to provide trial accounts to customers considering adding this capability to their team – contact us today to learn more.




