Don't be Schooled by Brexit Phishing Tactics
Barracuda Networks, whose early claim to fame was a spam firewall appliance, published a blog post on a phishing campaign that’s been making the rounds. The campaign capitalizes on a timely event—Brexit—by evoking the market uncertainties surrounding Britain’s move. The gist of the spam/phishing emails is that now is a great time to refinance or buy a new home; links in the emails go to phony lending site pages that are likely to do harmful things to the victim.
A screenshot on the blog post shows the sender’s email address, which includes the domain ancybo[.]com (link goes to our Whois record, not to the domain itself). I decided to dig into this domain with DomainTools Iris Investigate to see what I could learn about the spammer and any infrastructure connected to that domain. The results were interesting.
The domain is not registered under Whois privacy, which means I had a registrant email address to pivot on. This yielded 6 domains, all registered under the name Jeremy Arias. That may be the spammer’s actual identity, or it may be a stolen or made-up identity; either way, it exposes additional infrastructure related to the initial spam domain.
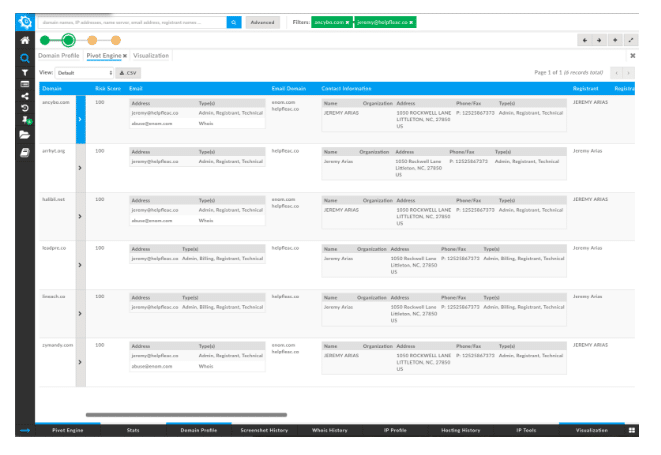
All of the domains have scores of 100 from the DomainTools Reputation Engine, which means they have appeared on industry blocklists. Jeremy’s consistent, at least!
Another common pivot that exposes infrastructure is to look at what else is hosted on the same IP address as a domain of interest. That pivot in this case, on 104.140.152[.]160, yields 26 additional domains, the vast majority of which are all on industry blocklists (shown here using the visualization tool in Iris Investigate):
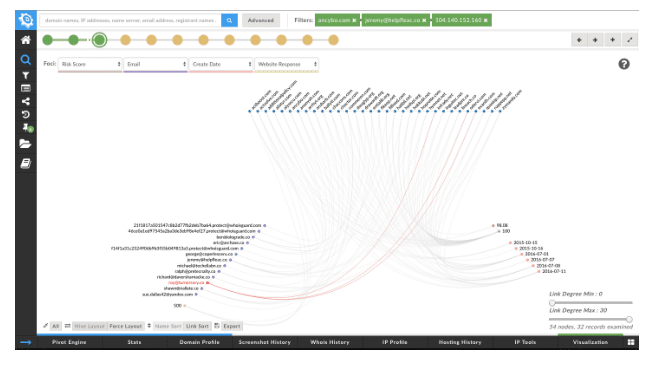
Pivoting on the non-privacy email addresses in this group of domains ultimately yields a total of 87 domains, all of which score 82 or higher on the DTRE (we have found that 70 and above indicates likely badness). 34 of the domains are below 100, which means that the DTRE flagged them as being closely connected to known badness without having (yet) been put on traditional lists of known-malicious domains or on industry blocklists. Many of these domains may be “on the shelf” awaiting later weaponization. The domains all have been registered within a 9 month period starting in October of 2015.
The additional IP addresses in this set of domains could yield additional pivots that might be instructive—indeed, if I were looking to protect an organization against threat infrastructure, or if I were law enforcement interested in taking action against the offenders, I would add those to my search. The pivots aren’t time-consuming, either; the entire investigation up to this point represents less than 10 minutes’ time in Iris Investigate. It can be informative–not to mention satisfying—to explore malicious infrastructure in this way.




