Empower your proxy logs with the DomainTools App for Splunk
Today, we are announcing the release of a DomainTools app for Splunk that will help teams leverage their proxy and DNS logs for threat hunting, incident response and quick, in-context triage of security events. Those sources of internal threat intelligence are finally getting the recognition they deserve, and rightly so: the domain names they contain provide a far more effective platform for analysis and alerting than an IP address. That is especially true when the domains are enriched with Whois data, and our new app helps Splunk shops find that value faster. Here’s how it can work for you.
Get Your SIEM Out of the ‘80s
DomainTools Iris Investigate is an outstanding product for investigating domain names and the actors that control them, which is great, unless you don’t have any domains to investigate.
Wait, what? Outside of an air-gapped environment, how is that even possible? Yes, the Internet’s routers only care about IP addresses, but the humans who create that traffic use domain names almost exclusively. Just try asking someone if they’ve seen the latest meme that’s blowing up on 69.171.230.68 and see if they have any clue what your talking about.
And yet, sadly, that’s the state a lot of security teams are in these days when they are trying to investigate and detect malicious activity on their networks. It’s like their SIEM somehow checked-out in the mid 1980s when the Internet’s domain name system was starting to take shape.
Sure, your firewall logs are going into your SIEM, but what about the web proxy logs, or better yet, the DNS logs? Most orgs are not there yet, largely because it’s hard to see an ROI.
Track Actors, Not Just Activity
Of course, even those orgs usually have “advanced detection systems” in place, often with the title of “CFO”, that emit warning messages like “So I clicked this link to approve an invoice from a vendor I’ve never heard of before, and now my computer is acting funny…” Those sorts of next-gen alerting systems explain why one SOC I visited had a fully-stocked bar in the corner with a sign next to it that said “Security Help Desk”.
But hey! At least you got a domain name – quick, drop that into Iris Investigate, right-click on everything, and find other domains that actor controls. Pop into your firewall or web proxy config and block those domains before they can be used against you. Revel in your proactive security awesomeness, then start searching for those domains in all the log files on every DNS, domain controller and web proxy server you can find. Also, set an alert on the miscreant who registered that domain so you’ll know if one of their domains is active on your network again.
Wait, you don’t have a log aggregator to help you with that search? Bummer. Do you at least have a place to set those alerts? No? Oh dear. What about your SIEM? Certainly it should have that capability?
Your SIEM might be able to help if it had the logs, so, back to what we said earlier. It would also need Whois data on every domain on your network so you could search and alert on registrant name, create date, registrant country, etc. Sounds great, right? It’s not just a dream – we’ve seen some of the best network defenders tune their detection rules to alert on attributes of the domain names they are seeing on their network, with great success. They are also watching for new domains hosted on known-bad infrastructure or owned by registrants with a history of previous attacks.
There are plenty of places to do that in a network, but increasingly, we’re seeing folks turn to their SIEM, and specifically Splunk, for proactive hunting, incident response investigations, event triage and more. In fact, we’re getting reports almost daily of security teams using Splunk or seriously considering it, and that’s why we targeted our first major integration effort at that product.
There’s an app for that…
With DomainTools’ app and a search add-on for Splunk, it’s now easier than ever to make actor-centric investigations and write alerting policies keyed off your proxy and DNS logs, or really any log that has a domain name in it. We partnered with Hurricane Labs, a managed SIEM service provider with solid experience in the security context. They’ve also published a few well-received Splunk apps, so we knew they’d be a perfect partner for this.

We’ve included hooks into nearly all our API end points so you can easily add context to any Splunk list with a domain name in it, or set up custom rules and triggers from the reversing APIs. There’s also a few workflow actions that link to a Domain Profile dashboard for a quick triage on a single domain name (you can also get their directly). That dashboard can show you the parsed Whois data, related domains by IP address or Name server, our Domain Reputation Score, and even the Reverse Whois results for the registrant.
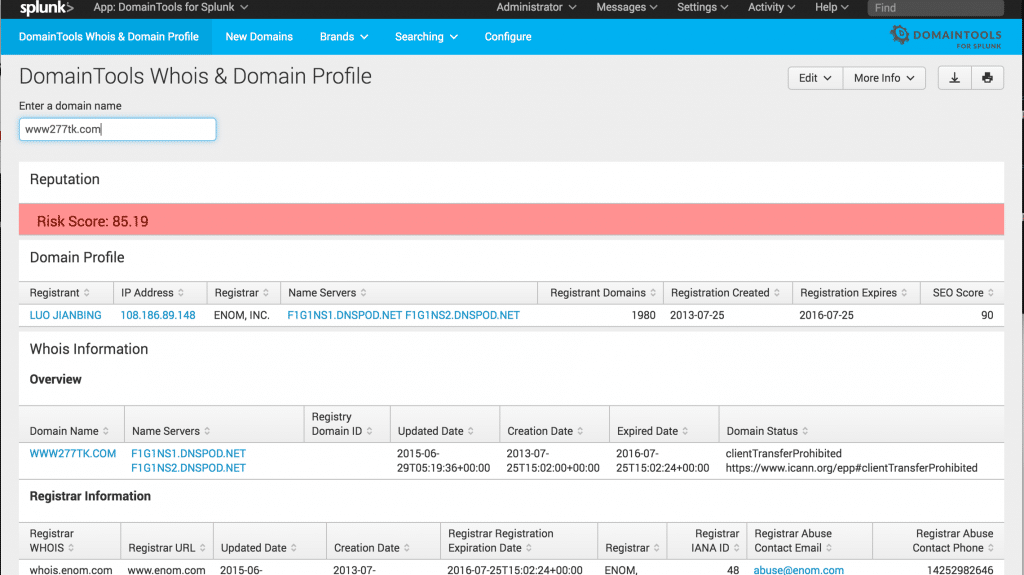
It’s a great in-context starting point before you begin a deeper analysis in Iris Investigate.
The app also provides a constantly-updated lookup table that will fetch Whois data anytime a domain name shows up in a datasource you’ve fed into Splunk. We’re using that for a simple dashboard that alerts on young domains active on your network (using the create date), but of course that’s just the beginning of what you could do with that data pre-populated and ready for analysis.
Those features, backed by DomainTools leading domain name intelligence data, add a powerful security dimension to Splunk and help give your proxy logs the status they deserve as first-rate internally-sourced threat intel.
It also positions you to surface meaningful results yourself without waiting for the CFO to call. Your liver will thank us. :)
If you’re already a DomainTools Enterprise API customer, please download the app and give it a try. We’d love to hear your feedback. Or, if you’re still considering how best to integrate DomainTools into your investigative processes, contact us and we’ll set you up with a free API account to try out the app.




