Flying Phish
Exploration of a common Phishing campaign in the global flock.
Introduction
In this blog post, we explore and analyze a current but prevalent phishing campaign targeting Twitter users that has been recurring over the last few years. Our goal is to characterize its behavior, intent, and ultimately demonstrate at least one set of ways one might go about investigating similar campaigns.
For some recent statistics on the issue of phishing in 2021, see the below report from the Anti-Phishing Working Group:
The above trend as shown in Figure 1 demonstrates that phishing overall is on a steady rise. This will continue unless we can begin to understand more about the most common attacks out there, hopefully allowing us as an industry to formulate more effective solutions to combat this behavior.
The example we chose is a campaign targeting the users of one of the world’s most popular social media platforms and one that has had no shortage of recent exposure in the media: Twitter.
Timeline
Our exploration begins with discovery; the most essential part of combating any phishing campaign is obtaining the knowledge that it exists. As such, it starts with one newly registered domain and one that triggered an alert in the DomainTools Iris Detect lookalike domain discovery platform.
- Iris Detect Monitored Term: “Twitter”
- Starting domain: “twitterreporterhelp[.]com”
- Registered: 18th of Aug 2022
- Discovered: 18th of Aug 2022 @16:24pm
Lure:
After discovery, the DNS delegation and a screenshot were collected over the ensuing 6 minutes, see Figure 2 for the collected screenshot including a unique take on the Twitter logo. Based on communication and co-operation from Twitter’s Security Team, we have a domain that we know is not legitimate in nature and one that might represent an initial peek into what could be (spoiler, it is) a larger campaign. To proceed, we will break our research into two facets: passive and active analysis.
Passive Analysis
Here we will explore and enumerate any entities which show enough characteristic similarity to be grouped with this starting domain. That is, we will pivot out from this domain to find other related domains and infrastructure which may represent a targeted campaign rather than a random scattergun approach often seen in phishing and spam actors.
We will utilize the DomainTools Iris Investigate platform as the effective case management and reporting tool for this investigation as well as a significant data source. This is because we will occasionally dip in and out of other tools that specialize in different datasets to acquire further pivots that will enumerate this campaign in the most complete way possible.
Some of those other tools we will user include but are not limited to:
- A platform specializing in page content: URLScan
- A platform specializing in malicious file detections and activity mapping: VirusTotal
- An Online Swiss Army Knife: CyberChef
Starting in Iris Investigate
Initial pivoting on the Microsoft Corp. hosting IP address for this domain, 52.226.25[.]237, produced two additional interesting domains. This pivot at the time of writing shows 14 domains (Figure 3), the vast majority of which fit the same profile as our starting domain using the exact same lure (Figure 2) in most cases. These types of domains are still being created / re-registered regularly. Many are quickly discovered by 3rd party vendors and added to publicly available blocking and CTI threat feeds, however they can often remain active and unreported to the wider community for some time.
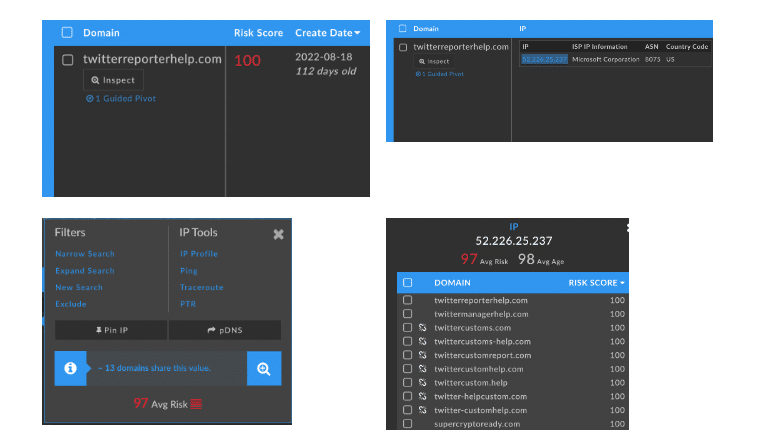
- Hosting IP: 52.226.25.237
There are a wide variety of options to map this campaign, and in this article we’ll focus on one way to proceed: monitoring the page contents of the lure (Figure 2). As previously noted, the image used to represent Twitter’s logo (actually a GIF in most of these cases) looked unique and might be a key source of valuable pivoting.
Additional domains:
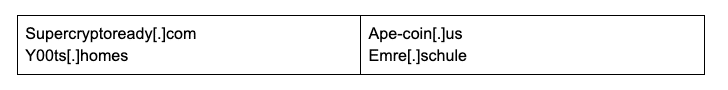
There were a limited number of other domains using the same hosting and SSL patterns (Figure 4), as well as some circumstantial evidence to connect them to this campaign (some of these domains appear to impersonate legitimate a legitimate organization “medium.com” which was created by one of the original Twitter founders). Considering this we have medium confidence in a potential attribution at this time using discovered registrant details. We specifically note the domain ape-coin[.]us, whose registrant details were also found to be linked to accounts on Twilio as well as Spotify and Discord. These details are:
- Registrant Name: Umut Can
- Registrant Phone number: +905468342455 (VODAFONE Telekomunikasyon)
- Registrant email address: emrecan3187@gmail[.]com
Reverse image searching and other intel from URLScan.io
The Twitter logo image used on these lures (Figure 2) pages is subtly different from the legitimate Twitter logo when seen via the DomainTools Iris Investigate sourced screenshots. Given the similarity of all of the remaining content in the source of these domains, the choice to use such a unique image was felt to be significant and likely a valuable pivot.
There were two variants of this logo seen at this time, the first of which is shown on Figure 5, which was loaded from a different domain hosted on Amazon. Pivoting in this platform on the specific image link above surfaced ~9 domains (Figure 6). The second variant of the logo is shown in Figure 7, and is also loaded again from a third-party domain, this time from DigitalOcean. Pivoting in URLScan on the second image link above surfaced 33 domains ranging in age from less than a month to a year (Figure 8).

This adds to the GIF / image resources from which we have found valuable pivots. See current resource list below:
- Twitter-gif-2.gif
- thoughtfulschools.org[.]au/wp-content/uploads/2021/11/
- Techtree_News_04_8.png?itok=nR8UCrz0
- www.techtree[.]com/sites/default/files/styles/story_page_315_236/public/2014/6/
When examining these newly discovered domains in Figure 8, they are largely all using the same lure (Figure 2) and are indeed a part of a much larger campaign with a defined set of targets. It is telling that these image links are so unique that they have only ever been used in domains involved in this campaign.
Now that we have made our decision that this is very likely to be a campaign with malicious intent, we will next begin searching through the dataset of another data vendor that specializes in malicious file detections and activity mapping.
Pivots from VirusTotal
Beginning with our starting domain (“twitterreporterhelp[.]com”) we searched in VirusTotal and found a downloaded file for a domain that had been added on September 1, 2022 (Figure 9). Pivoting on this file in VirusTotal surfaced 17 domains observed downloading this file in the wild closely resembling those already discovered via Iris Investigate, as shown in Figure 10.
There were some additional potentially unrelated domains:
- Markoliviaa[.]com
- Vakifbank-turkiye[.]com
All domains discovered through these different tools or threads of research are being returned to Iris Investigate and tagged with “TwitterPhish” for later de-duplication and reporting. These various threads are all represented in the Investigation History panel of the Iris Investigate platform, as shown in Figure 11.
VirusTotal File Analysis
We analyzed the common file downloaded from these domains:
- “/var/www/clean-mx/virusesevidence/output.195135302.txt”
A historical detection in VirusTotal of this file produced the below table of data shown in Figure 12, as well as seven seemingly unrelated domains. The raw contents of the file is provided below in Figure 13.
Raw Data:


When parsing this raw content for strings, we found the following:
- Sign.php
- douglas.walker@mitie[.]com
- data=04|01|
- emilie_garcia@paramount
- script>
- typo=1
- Noemie
- Apps
- andrew.spriet@voyav[.]com
- VirusShare_c77192ce3ea8610df69cb880424dd538
Further decoding of this raw data using the “From Base64” recipe in the online tool CyberChef provides these additional strings:
- ngreg.goodman@uni
- ncasey.horton@motiva[.]com
- monica.copeland@motiva[.]com
- jphish@test[.]com
- franco[.]ma
- ovjhiggins@tiaa-cref[.]org
- carolinek@strathmore[.]ca
Further recipe decoding using CyberChef shows simplified chinese character output, which may not be relevant to this exploration but is still worthy of note. Though the multiple layers of encoding is significant, it is believed that there is further encoding in the raw data that is as yet undiscovered. Finally, pivoting in VirusTotal on the last bulleted item from the raw content list in Figure 13 links us to the compressed parent file:
- Pivot: VirusShare_c77192ce3ea8610df69cb880424dd538
- Compressed Parent: twitter_sc_ig-lyufusx_.zip
- VirusTotal Hash: 674d1e3bbc6039855f4fb2874ddb7274905ae3ca598edd1cfeb2d347a2e6b669
Content of twitter_sc_ig-lyufusx_.zip:

With this new set of indicators we can see that at least one of the historical iterations of this campaign has previously been reported to VirusTotal. As shown in Figure 14, we can see the structure of files called by these lure (Figure 2) web pages. We can use this to compare newly discovered domains and link them to this campaign with a high degree of confidence. This will make effective mitigation easier and more efficient.
We now have a much greater understanding of the structure of these phishes and that they do appear to be engaged in credential harvesting with the potential for more.
To finish our passive analysis, we conducted online searching for text matches to some of the strings we identified on the possibility that this could surface useful context. GoogleDorks can be used effectively for this, but were not extensively audited in this exploration.
One interesting item discovered using this method was an Alienvault Pulse for Phishing domains that mentions one of our more unique strings as a URL parameter. Specifically, Alienvault “Domains used in Phishing” pulse shows a link to one of the artifacts found in “/var/www/clean-mx/virusesevidence/output.195135302.txt” (Figure 15):
- “http://jgt.aps5[.]xyz/[email protected]“
When we look for “more details” in the Alienvault pulse (Figure 16) we see the servers’ response and certificate information for this domain on the date discovered / reported (August 6, 2021), we see that the subject name for that certificate has a similar but different domain name mentioned: rfhv8[.]xyz compared to aps5[.]xyz:
- subject: {“common_name”:”rfhv8[.]xyz”}
Bringing this new domain back to Iris Investigate we observe that the DNS SOA email address for this domain as well as the hosting IP and NS IPs reveal relationships to a large number of similar domains which have the appearance of being created with a DGA, see Figures 17 and 18.
Possible DGA Domains:

The domains in Figure 18 are only relevant to this campaign depending on whether “[email protected]” represents either a victim or the actor. We currently cannot confirm either case.
Active Analysis
In this phase of our exploration, we obtained what we believe to be two of the most recent examples of this campaign as represented by the lure (Figure 2) sites. To do this, we visited these domains and presented them with whatever they required clicking through their interface. For the purposes of this stage of the experiment, 3 sock puppets were created, 2 of which would be used as victims to feed to these domains and one would act as the control and observer.
These sock puppet personas were created with legitimate email addresses and Twitter accounts. They were designed to be diverse, given unique interests that each followed, and the accounts tweeted about various subjects on occasion. They were also given AI-generated profile images consistent with their defined age and personal profile.
We selected two active domains in this campaign to feed each victim. We did this to compare behavior across domains to provide support that this is indeed a coherent campaign. The two domains we selected were:
- twitter-helpings[.]com
- twitterhelpers[.]com
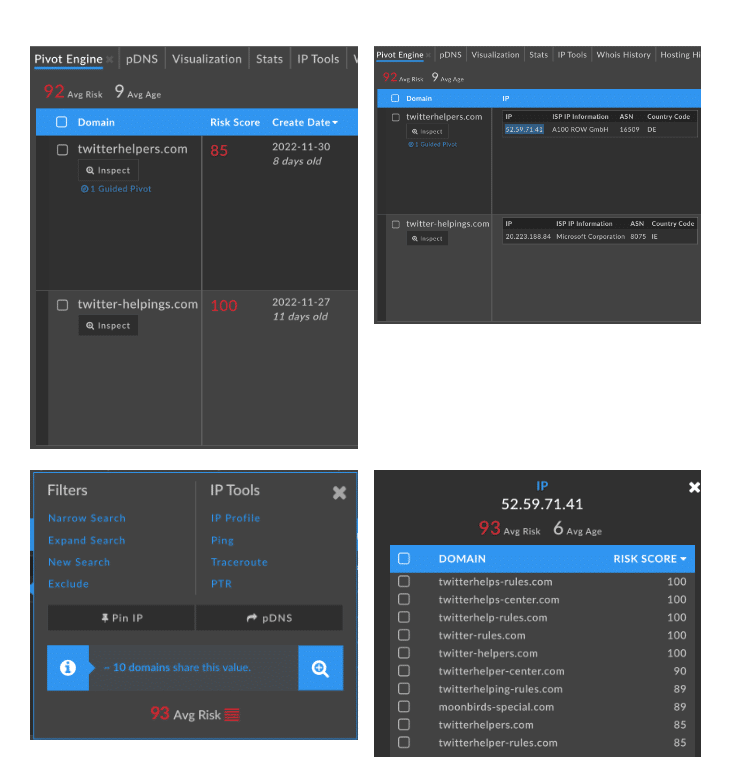
Below are the domains seen in our case management and overall repository, DomainTools Iris Investigate (Figure 19). The domains allow us to make further pivots to identify new hosting infrastructure that is likely to represent new tactics, techniques, and procedures (TTPs) for this actor, as well as further add to the cumulative list of domains both historically and actively involved in this campaign.
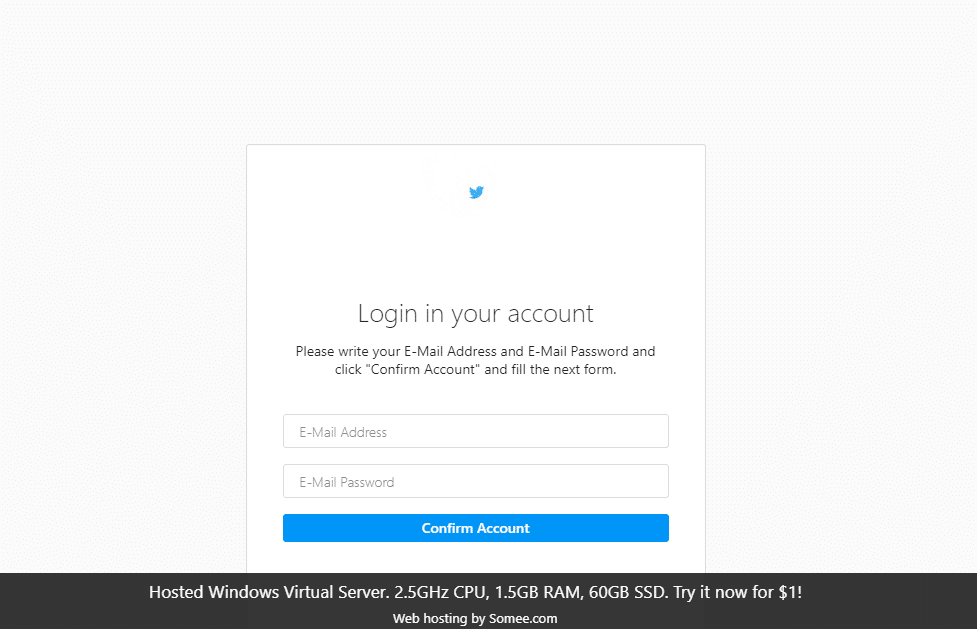
Resolving these domains show their intent is to harvest both email credentials and Twitter usernames. Email credentials are requested first after clicking confirm, then Twitter credentials are requested. The flow for twitter-helpings[.]com is shown in Figures 20 and 21. It was noted that while resolving this domain that pages tend to resolve in a very jagged way, starting with basic HTML then applying the CSS slowly. Another interesting note is that this page was using the Twitter API to confirm an account as genuine; we received a page never before seen when entering incorrect data–wrong.php.
twitter-helpings[.]com:
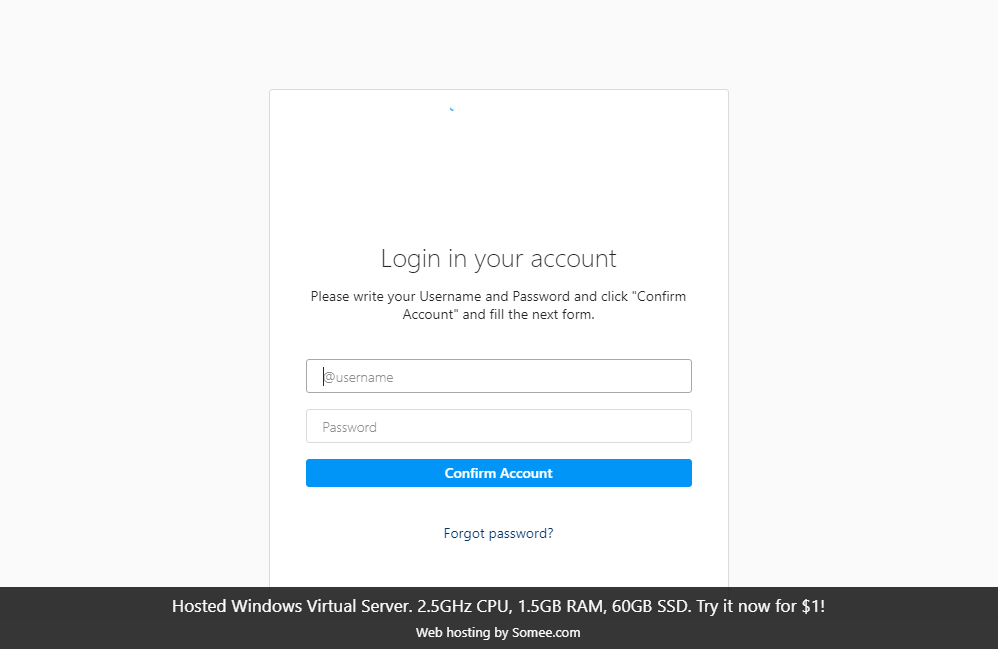
The flow for the second domain, twitterhelpers[.]com, is shown in Figures 23, 24, and 25. In a variation of this flow, a phone number is also requested.
twitterhelpers[.]com:
All of the requested information was supplied for our two victim personas. After all of the information was submitted and inputs clicked, the user is then auto-navigated to the official Twitter Help page, presumably to give the appearance of legitimacy and thus forgotten. We monitored our environment for changes in a number of ways in the off chance these domains were doing more than was immediately apparent. It was also observed that the Twitter logo being used on these latest members of the campaign has changed and might represent another addition to this actor’s TTP (Figure 26).
- https://cdn.dribbble[.]com/users/652798/screenshots/1846570/media/84230547bc98b3390e9e4a6f18690fdd.gif
Pivoting on these in DomainTools Iris Investigate brings our total of campaign domains and potentially related domains to 153. The full list can be replicated in your own instance of DomainTools Iris Investigate via the import hash found in the Appendix.
Data Gathered
All gathered lists of domains and samples will be made available via Github in the Appendix.
In this section we detail the tools used and the data captured that can be used to infer the behavior of this campaign with regard to a local machine that resolves one of these lures. Using a virtual machine environment with its own independent access to the Internet for this test meant that we could run several tools while performing our active analysis. These might allow us to capture the impact and indeed presence of any malicious resources this campaign might cause to be downloaded.
Several OSINT Tools were used to accomplish this sample gathering, but some of the most useful were:
- Regshot
- ProcMon
- Wireshark
- And more….
We can see from the results in our screenshots below that in both iterations of our test several new registry keys were either added or modified. Patterns matching known malware families were not detected in this data. These registry changes can be examined in detail using the github link in the Appendix.
Regshot result from twitter-helpings[.]com is shown in Figure 27, and one for twitterhelpers[.]com is in Figure 28.
Unusual network behavior was also observed in Wireshark where this domain called our in DNS to try to resolve subdomains of the following organizations:
- Googleapis
- Miro.medium.com
- Somee.com
- Yandex.ru
- Dzeninfra.ru
- Windows.com
- Trafficmanager.net
This pattern is common to both tests and could become a part of an eventual detection signature to be used by an automated playbook with the goal of finding and guarding against new iterations of this campaign. See Figure 29 for a short example snippet from Wireshark.
Process Monitor also displayed several interesting new file creations but again no pattern matching any known malware family was observed (Figure 30). As before this does not mean that there is none present to be observed, or that some other malicious content is here to be seen. We suspect there is indeed something here of note, this is another reason that we have included all of this data in the Appendix.
Sample files uploaded to VT
Below we can see confirmation that our freshly gathered sample data from this most recently created campaign iteration is indeed malicious and matches samples gathered by other researchers in earlier iterations of this campaign. Including a previously unseen sample “wrong[.]php”. Figures 31-34 show details from VirusTotal for the PHP files username.php, mail.php, a CSS resource, and wrong.php, respectively for Twitter-helpings[.]com. Identical detections for the samples gathered for twitterhelpers[.]com were seen when uploading to VirusTotal and so we will not present those here.
- Username.php from Twitter-helpings[.]com
- Hash: 1c2ed10af13441b48ae65abb975acfde2c6712d81308a8cd45bd2b6e0bc8ac2c
- Mail.php from twitter-helpings[.]com
- Hash: 49ddcb8734a8477ce0916ec4cb081a4c0e0dbd0c167450a140ab1f4e41d028de
- Interesting YARA Rule match for one of the css files from twitter-helpings[.]com:
- After_Click_Challenge_e6dcc76c8eaf.css
- Hash: 16c16a825280d02191f5bfa3b9084965ccfe31ca16621354c2625fd0e7e15dd3
- Wrong.php from twitterhelpers[.]com.
- Hash: 872efa01ea9d55db43a9ebce2eeef6fb84dfc8fb6f0b25f4349112c69255c2c6
**Last note from findings: Potential C2 connection called out earlier in this blog was not confirmed during the course of this research. The status of “andrew.spriet@voyav[.]com” as a potential victim or actor here also remains unconfirmed and as such the list of connected domains should be approached with the knowledge that they may represent a red herring for the purposes of this research.
Consideration of Findings
As of December 2022, all victim email and Twitter accounts were still accessible, meaning they had not been hijacked and credentials remained unchanged. This leads us to believe that the primary motive could be one of a few possibilities. First is to collect credentials for later sale in bulk. Second would be for the creation of “sleeper” Twitter accounts, which could be activated en masse to perform some operation or action. In both scenarios, the actors hope the theft will go unnoticed as the final step of their process drops you at the official Twitter Help page.
In addition, there were no obvious indicators of malware observed within the test environment. There were a great number of registry keys and processes spun up during the process of this experience that cannot be ruled out. It is possible that malware was dropped and it determined that it was in a test environment and removed itself. To facilitate future research, we are providing logs and data files of what we observed.
Given the behavior of new domain registrations and old domain re-registrations, as well as the consistency in lure variations detected by VirusTotal, we feel this may represent a long running Phishkit. This is something that can often be bought and operated by a wide variety of individuals and organizations with a multitude of purposes. Such purchases tend to happen in Dark Web forums and other similarly restricted-entry marketplaces. Further research will be required to determine the true nature of this campaign as well as a strategy for combating the same on an ongoing basis.
Conclusion
We do not believe this is a new campaign targeting Twitter users for their credentials but rather one that has been around for some time. This is likely a new wave / phase of that campaign which is displaying growth and complexity over time. We feel this is relevant to highlight given recent media coverage of Twitter as well as the sheer number of similar phishing campaigns at large today and not to mention the fairly open and brazen nature of this campaign. It suggests that we as a community need to continually assess the complexity of these campaigns if we are to find success in combating them.
Potential C2 connection called out earlier in this blog was not confirmed during the course of this research. The status of “andrew.spriet@voyav[.]com” as a potential victim or actor here also remains unconfirmed and as such the list of connected domains should be approached with the knowledge that they may represent a red herring for the purposes of this research.
Mitigation of this campaign could take many forms but one that we will suggest here is to create an automated playbook that can leverage both the DomainTools Iris Investigate API as well as the URLScan API to use what we have discovered here in terms of unique infrastructure-based as well as content-based artifacts to hunt for new variants of this campaign over time and defend ourselves against them.
One could also choose to further the research presented here by providing your own unique research perspective on this experiment, beginning with the linked evidence in the Appendix. This might allow for further mitigation techniques such as the creation of YARA rules for any files dropped as well as creating DNS filters for the somewhat unique network traffic structure observed in our network capture evidence.
We would like to thank the Twitter Security team for their valuable support during the course of this research.
Appendix
GitHub Link to gathered samples and log evidence from experiments for both active analysis domains:
DomainTools Iris Investigate, import hash listing all domains discovered in this blog:
U2FsdGVkX1/FC3BMsrJ7ITloKbBmi5mNqN2uGUkJcZFkILg63HA5iUXAKBda8bRcvt14n3nR3BjKh1ypFrrIG4UAiLjUfCtSy1Ll7VsHstPiexR686srnacEbFz3lBgCq/8Y/L0BBcnGzgLpi/2LeTjnSzzi67ErgA/HjAiS8Xw4SKQs5AqbgiGN0RAli2Qa2PAmCBAnV9TahalMgi97idSvWZn/pZ2mcOQ1VkBmGDcKId8PHnkBOm2j0WfUjTeQVQtfvEBOunTlawco7pvi2C2HO8eH/a7svTRMWskaBmLD1JL3SYR6yYqMVA2pwkD0wM6r7d9Umr1xHldyMvqXKmg6YQrRWmxGAV5iNvCYX9M04HINCpH4Wfy78Osx32uwNG2F0TFmdj9vo/iqIeLkCYHvJWzE1uQz0TsOZmeZl7U7FeTBmIa0pJB10G8eiH2o9Wgc8Zgd/GR0UIdXLqqz0wjGbiZIS8HzfKMXLitRzQRupyJ5KN1muUqsd7vyWR4iMQPPVS96m9J0n7nKxmh9eUBL+HJ17WzYB6QJ7B4r6SD7oTq9DqRpcOQJabfcPcuQFOLj+M9E7us2X1kYXv+UXX5j75bobLHSksqKfcqm+a5c/3mjVf8oFiLV1sl6XQCUArM8z5fmRbqjbrVVUNnFcmWL2U1jIy49KW0eZUdYtzUnRCS2wZuEHCfpT2BLeBgWiiXgjhmcDZtSgNCkXl/+W4tk9sdN4Kn+ITnRf9ZEDVZ8SUbtaK+bgKNgNA0lCtrKIAMHPTXScezNuvCLc1yg2mpFxUmEznbex4EmybxJpKbn4UfLqtJuWl6iDTDvA/o0tZdnQVwEu3hE4ftabyY9Bq+GQ7sjccKOoMvcPGvSnnQqhLV+k7t7OvpGTFsK84rWDfOf2ysZW5Eai6gY9Kiz2pmCzcbdxMr7POxZdtBKA9a/dwKW5h7cEn30HflXp9gCsTW/B32+WaX403VWN1tHMg2X3JqTlzGwTmWTTT7++4GhG0NLb9pi3MnPimLogzNmUFnAZbL2vqfVM2RsA2rUMRfQ0ighvV6kKhZvwz5OLjHQim+3efsQbymvkJO2rTnLFycvPitpu/Y9rU97UQy2Dc42kNXtjQ1UsF/GjpdyNjwDUbUUdzFTFf9XfrZIA3QT/Fr3s19eJYXJgAEmM4mpSVNjZfABgMMfjEk5SDKnqpEcWXlRgsYFzjnWZY5kIl16Te/ylP0SPxj0WjrrLrhCdvZal6ci65aw+EP2MbqQ2l+xQoKH9WSmG2t71AkqD78xeFK11Ofge0zu8vXXt3XyOgYefKgp0LpPrjuceQX5Eanx68yUcCjh9BImpa1N7ylR2TRsweFHdiuDFEkE8r0qGPrEqfQmQf1rw0rfR+wGIU62PMO31rBY8rYSisynNjGukO95+zvWzw+Z/XMwS+sDX28has79Wj/J3lbKRNlUwgFIoRbvviKz9mYxuwqPM/bWkyIB2FlIONupqrcsHuumKNGhvdcf4SG6gjRj0AcgIQ0XdG2E1Ha0FHs3kYJLQ63Vhnd5ertVGsiXymGXB0+blOe4NbwDuSGYewH8rDkZTu+drRt3Zh0Gi5uIZBPpd4bOPib1hcahhWA2ejWeIpATsQUOPlaHaCfbV8PhSnT7jyypPiqWGJ+vD5zslFS4xUSBhHW/1bsaCYFqHVQwMWNJv9cX/TZkfCmvqTXx50+takyQkjVJuIFYDKZLxIzC/LA0Da/rhB9cZBbmU4oWKmJMff1BOpiywft34vD+7aALM+F1pW7Ur0pJ0VM/hqz0LxLfm9ohmfinS3yjik6fXziffBDPopSFZG2CEd75dnf9m+E/hSBgiLdEoHDOuudX6Du8bhGu+U1eeIVrNZb6BJM+nDRkbLlwwIPhaC7d03oJjAbRkNoBypr0535jNCo7j7YT8q88pxfZC7G8xOFmuCVOIv6uA3P8Ty1W/9C7HQUALjWJbYj0i6nUuJ+0SRua8zgXCgACqUyzyThiA+m7x9GCicbIRqFApzN5nI9n9awfHEKHmFYDD1aDDlLe5DPSfFv0+f4jKchlLicUkTfzne11sX7KIPuQbuVuoilJMl9mWrJtUeIOtpFRhjVgoJ6jzOuSneyC7/oYgO4LvmZTsIXP3bkN7F4iC4CrYACD4D8IfagFmNdwIYCBLC4xX7alDD2RMYcR8QKINWfswqfd2Vg68J2PWdriY5oK9D/muRehyUhkjqwywz19cfK0v4qjJENrWToB0XDIIMwlDCAzxTC0TpOU8fEq+jzreE6gFnFA2fYDy2DkY7gdaeMlafpMqtogyYVTBXKkLHjpf8hIS1pRLGe0KYFUdBXyB/fRapHzMx8rEDIG2GcxVEA3CgmbhVlUrTbmRt7AuaLKqfVlvmk1XILQ8ta+0EOb3ELawnJFF5G8OBH0NUpS2NtBQGfFV9CHe5VOZYCoGC4Ad34j61zWF256eMUcrSqpegTvkGmm7JRb/QPdjiYv4sO+miyi8Mm1ONRgjnB86CXMxvs5zKBjeHTcX3PcnDdeRYSiBML14KyyIYAsbnkYbsQpOQUknhJHnSyOT97MhdaPwLeKipu50efIatFmxPUYidNb9j5cCWMJdg/54h0SZwK1Zv1yxSjoQvaue89GqkVC3/gcXAN2HfBgJlmYpfZE6DjjY5o8UyqklealyMxNuxhIHUC/RxMtxXNQV/ynHsxE/O3n2Ua10wxsZwQmqAMiGY2z1MbuhmbJRXV/05jYac6PspJ0uHn6TB6AiNs2JBNIvP1/X1VHaDg6zZ7LC6mZLqQJJFnf57doMtp2Kjgw9W1ThTqrtn2x/BGeGytEY0i52jsdFxbuC4FMHffpTEI1ewmKM2ZJFl5R3acrlZO470HMPnjYudtAv0XG5i8qo+SiHlmCGgOmV173bxEacepnaoFlv8qyOZAe+COdX4E5SwqKxClCM0E7VtBBKRdvLZj0Do2kwBW4A8lXJ9d3grzuYudD+HBiRh4F8pPWiqPRF+1qTtDz5XTzIyWVTthP5eWzOCW4ttIcVe8OIGZtYvI/csVZOS2MU0UWqJ1TLfFKUq4tvWzoE3QiYd4tcTqUlQJf6HJsT7B2BG8CQl/3x18JIzpMbLGkvbv9bjqLelZ+kdCc7uTQI8NOY2cG88lwvmtNY46X5KPhSqs0Fqiui1sx1m9/fp4NlEM42F2AHOznXy8QB6bpw1m1Vs/KroEu8BObaz7/t0x9Rq9nzQFBnCSsWSDZ/DBJRU28axBBtW/YuetpoJlpbVjJac+UA1N3ft0gplgC0xeFB51FAsY+sfBbppr+1dtklxgclsV8wF2SPdHMLPccL3/L/syDxfhbPSQCacCFY6UPCi/vZL44u4N59VaErxi9QnnGcXK95kL0s2fsixJs8GOuyXMo6eq+KVjubuRzUJJA68z5NmIkmNEgxVAT5iGgZMPMmEeodvBiiTOOatnAfVvreeRsFIkncoafrp8+h5zvLipkqpJonb6UxRuK1sAu32Ad/JVpd1RMiSXc3WgWnfjXaGE02mER8F6UeOlzVyrpvlJ5P8zEVw1cYn1LW9uyJjeOK6QSKG9YU37XvvVZVhORcuwAAKchYtlBH1l++9SdaFdB2PCS34ITyRFb6CQP1nSOE4HnYtBfctIfLGzdkyGAzdOtdi7y/XGe4uoL6xY4Yv49NVWeoGiJ9lkj145boKUpjBiHOV0wBUdjzLO0N37Sdzj/Sc6Knv6UG2lZvtvgRmfATIb/BeVHLZfxlzVVV3IPJsmeSp9eq6r6wOgCtshN+pQAYvssU/Af75UQoiUFabbfzdCzn0fYJ4l9DW6kGRXwk+HtWOcKyVm/EgQw4eafBBWVns1KXHnNGXFIx+8Rd+TmrH3ctCyKkNQHBwl+ODL2x7RIdU/Oqc9XPmofrjepU+quTwb8ira2boNnFxII+Vm7CPbnJHRESocSvdIKp8rnQ8bQWriL0aNHTnLs2eFfT9PrpLniYsIjbph3PjELcQHwsDGmZ6nod8f8GCKRzjjCeuGtEUCUzGniAqa4FVVl88V70V3qkvU01LZRfmC0nEcodTBLAUqSGVtlbt+SiKehF4BSLB3ugHVYq4LSjR1+TNcevYPbLkncOI/qDclFsEUpsxugrtdFe9rzsG16rR12kZTMrsjRY8+ApuAGPHhL+B/evvj5osD5VHfUrXJPJtJ+ehekcF7CMrbuuYm1C63br0dKtRs6C4++6uJth267bjXAY9XuspZ+Quu4Q82Rn0bISv+FO4SGQoMzNqAOljVaoBrKr9Av1TVT80j4qS6TmDwoyWRoh7W6OiB0USzHbrVN9YPsch2EjySRmJ0QHADXnA9N3+KMXJVNf1eO+Du0QE5+cXzYGKQ+GEqueRER8faO7tt8cPaHYLNMlQV8jrp5b+MrXuKqMkzSGWPn2zWU4GJ4qq7iXdwgmaG12Q24iBEIxeapHDO99eMz/AfrXIX42JbhVKdUkDTesLIscleRwA+pMlPAVAQG8If8vmQqxvfrMthOr9MZnBiLJ/TTmPF8JhvgtMKOTgh4KRFxEp/4NngSrofZVxa5MpsKJzlyLL/rFJ3NKlCSGns4X4O1r3rfNkxiiGCXPB/DZ8+pPMoGT9lumj6ciyzZJkRqJ5S0fQ==



