Fraud in the Time of COVID
Fraud where scarce and important medical equipment is concerned is abhorrent at any time, but during a pandemic when it’s urgently needed to save lives, the seriousness of such activity compounds dramatically. Investigating and stopping such actions becomes imperative in order to ensure legitimate medical facilities can deliver the care so desperately needed.
Such was the situation impacting a number of medical equipment manufacturers and medical systems in the early days of the COVID-19 pandemic. A Nigerian threat actor was systematically and thoroughly attempting to impersonate medical institutions in the US with the aim of fraudulently procuring medical equipment from the manufacturers in the name of hospital systems. Relying on normal commercial payment terms, the threat actor would seek to ship the medical equipment to illegitimate shipping destinations while buying time, usually 30 or 60 days, before the equipment manufacturer would even expect payment from the legitimate institution. Without further invention, the equipment would be sent to the fraudulent shipping location and the manufacturer or supplier would not only suffer financial loss, but much needed equipment would be diverted from use from legitimate medical institutions.
As illustrated by figure 1, which shows the entirety of the various types of data points related to this investigation, in this blog post we’ll review ways to marry traditional domain name Whois records and other IOCs with other sources of intelligence to help gain a better understanding of the actors behind such activity and bring them to justice for activity that costs the healthcare system billions in losses annually.
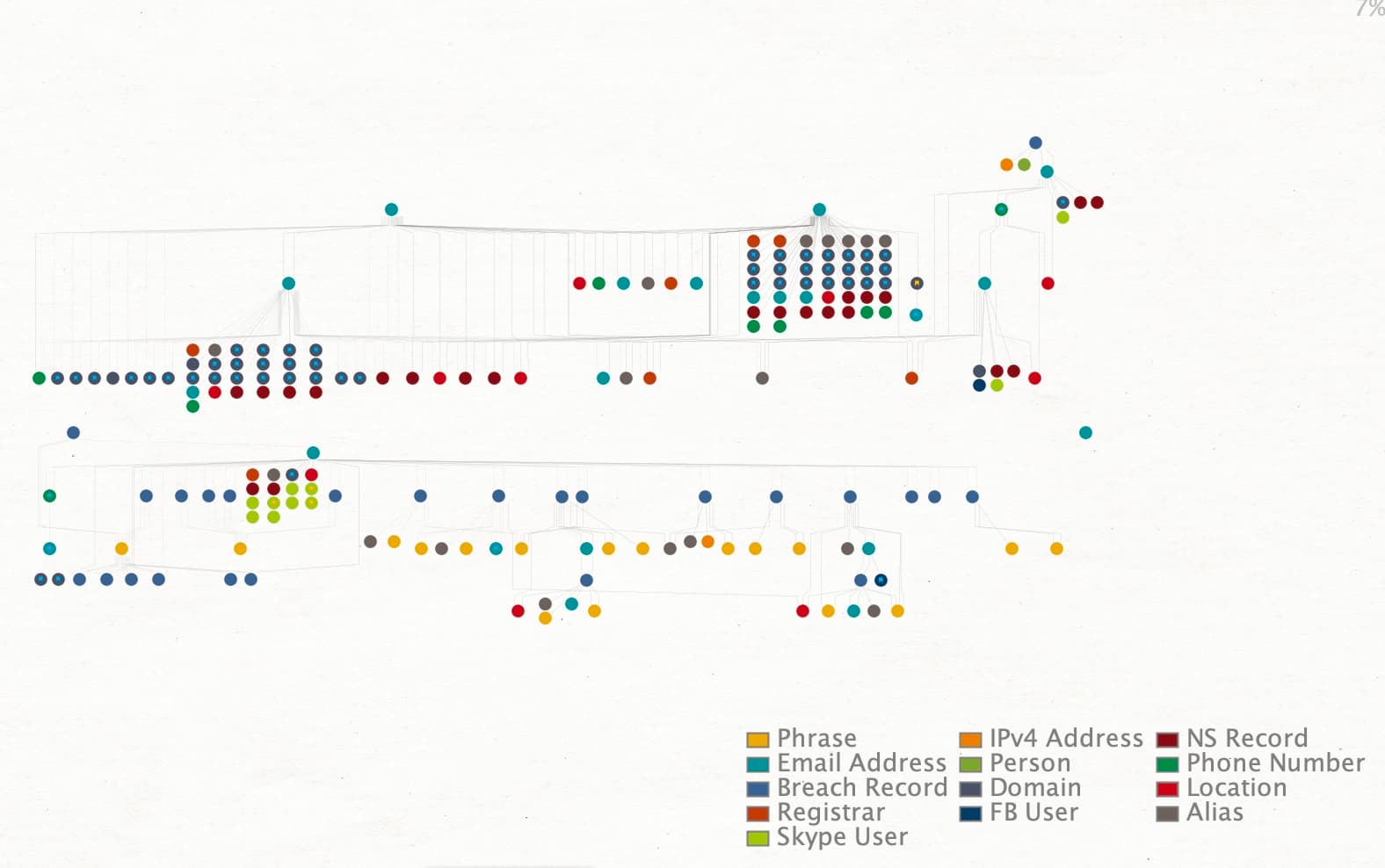
Threat actors use and abuse many legitimate commercial services in order to conduct their fraudulent activity, not only registering domains through registrars and using hosting provider infrastructure, but also employing other services as part of their fraud operations. These services can also be enumerated, tracked, and in numerous cases, may be the subjects of breach events themselves. When this is the case, many of the steps that an actor used to obfuscate their activity can be investigated.
Given the number of services they abuse and sheer number of indicators (like email addresses and phone numbers) that an actor employs, when they do not feel that they will be observed, they tend to “fall down” where their operational security is concerned. Two common examples are reusing information, like passwords, across different accounts, or using one email service as the recovery email for another service. These lapses in operational security are typically helpful sources of new pivots in understanding and correlating what is related to a particular actor.
Starting With Historical Whois
In this case, the actor used a number of popular domain registrars including public domain registry (PDR), Tucows, Wild West Domains, and Google. An examination of the fraudulent domains included a seemingly innocuous domain ryanlherco[.]com, but was later used as the email contact for a number of other fraudulent domains as well as the handle for a Gmail address (sales.ryanlherco@gmail[.]com) that included a host of other impersonating domains under the registration aliases “John Spencer” and “Maurice Dodd”. Phone numbers (+2348067506761) associated with those registrations were helpful in identifying two additional Gmail and Outlook accounts also associated with the actor. As mentioned earlier, fraud actors often require additional types of services in their schemes and a query of other services associated with these emails uncovered a number of Skype accounts used by the actor that were helpful in gaining understanding of where in the world the actor was operating. The accounts listed Abuja, Nigeria as the region associated with them.
Beginning To Unravel the Accounts Associated With Actor
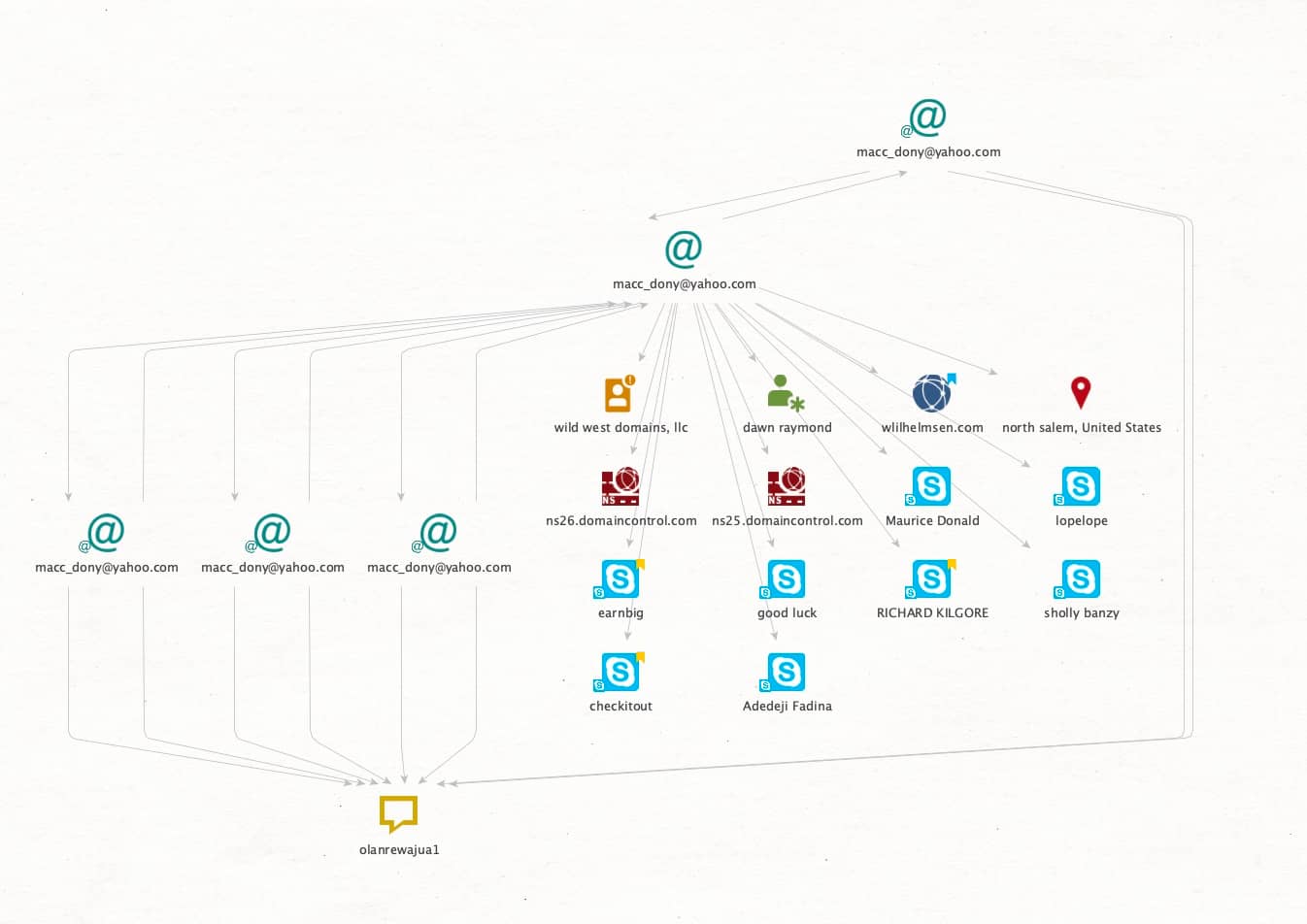
Given the large number of email addresses typically used by fraud actors, it is common for them to not use best practices and rely on password reuse across many different services. This is illustrated in Figure 2, where not only are there a number of Skype accounts associated with the email address (including the Maurice Dodd moniker observed earlier), but it was also used to subscribe to a host of other services all using the same fairly unique (and West African) password “olanrewajua1” choice.
Querying this password in other OSINT sources provided significant new opportunities for investigation as the actor had used it and a near-identical password for seven other email addresses. In addition to the password reuse, the actor also used a common tactic amongst fraudsters seeking to manage multiple accounts: using one email as the backup or recovery email for the additional accounts. The more frequently an email is used, the larger the digital footprint that email accumulates. Additionally, the linking of accounts provides more opportunity for them to slip up without even knowing it. That ultimately was part of this actor’s undoing, as illustrated in Figure 3 in a Maltego graph which shows the connection between the actors’ fraudulent accounts tied through email backup recovery accounts, and legitimate emails used for social media and other open source avenues for investigation.
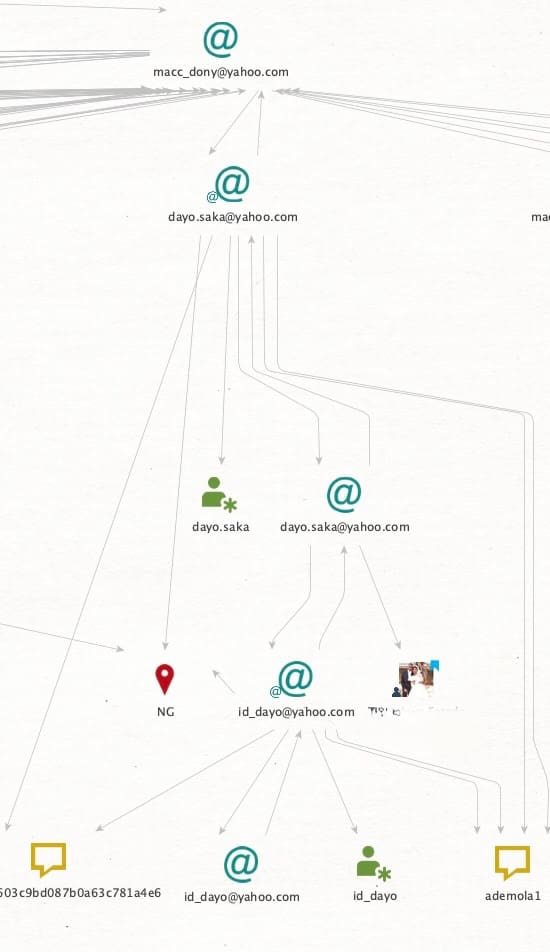
In addition to operational security failures such tactics tend to induce, many actors seek to hide the true nature of their criminal activity from the communities in which they operate, including keeping unsavory information from friends and their family. In this case, an email address that was reused repeatedly amongst services was also used as a recovery email that had social media accounts associated with it: that of the actor’s wife who posted their wedding photo and was apparently unaware of the nature of his criminal activity. This situation is more prevalent than not when investigating threat actors and can often be another source of intelligence when family members or friends and associates unwittingly provide important information about the actor. In this case, review of family social media accounts led to the positive identification of the actor, a male from Nigeria whose wedding photo was posted on the social media account of his spouse, illustrated in figure 4.

Bringing It All Together
Threat actors, particularly those with high rates of recidivism, or those that have conducted such activity over longer periods of time leave a bread crumb trail particularly with historical whois and infrastructure data that can become invaluable when trying to understand the nature of the adversary. While they tend to evolve and improve their tactics over time, this historical data doesn’t go away, and as we’ve illustrated, sometimes a handful of mistakes (or even just one) can be enough to trace criminal behavior that will define their future going forward. In this specific case, charges have been filed by international law enforcement against this threat actor for their egregious criminal activity.




