How to Not Give a Scam

Introduction
It was an ordinary Tuesday morning, and I was checking my email while drinking my morning coffee, there was the usual collection of spam sitting right where my various email rules had rightly relegated them. At this point, having worked in technology for many years, I had seen most of the common spam and phishing emails you usually hear about in the media and casually deleted several every day without a second thought. However, on this occasion, my inbox held something very unusual—something I had never seen before—an email from an address I didn’t recognise, which had one of my favorite old passwords sitting there in plain text in the subject line.
That password was fairly long and all letters, and even worse, it was a collection of three words in the right order (albeit not in my first language). Now to be clear, this was a password that I used over a decade ago, before becoming aware of the need for conscious and active security practices in my everyday life. But it was unique enough that this could not be the everyday brand of phishing I was used to—this was more targeted, and this might have been my very own case of personal spearphishing.
I’ll admit to a quick spike of fear at first glance. Generally, the best course of action is to either delete the offending email without opening it OR do nothing and report directly to your CISO/relevant security on call. But the addition of the old password just made me far too curious. I opened it—and found a pretty unexpected ultimatum laid out in plain text, broken English, and awful formatting.
The scammer claimed that I had been visiting pornographic sites on my smartphone and that they had installed malware on some of the videos hosted there. They further claimed that I had watched one of these videos, which had resulted in a number of things happening. First, an “RDP” session was initiated. This then installed a “KeyLogger” which ostensibly allowed these individuals to make simultaneous videos of the content on my screen as well as the view from my front-facing webcam.
Lastly, they intimated that they had used their “malware” to obtain all of my contacts from Facebook, Facebook Messenger, and email account and would forward this combined video to all unless I paid the sum of $1,029. I was to consider this a donation and deliver the amount requested to the BitCoin Wallet address mentioned below.
Proof was offered if I refused to take this individual seriously. I could respond to the email with “Yeah” and they would forward the video to only a small group of my contacts. Not incredibly important in the context of this discussion, but maybe an interesting characteristic that we might want to note.
Naturally, I decided to conduct an investigation of my own:
- I gathered my raw data points:
- Scoured the source of the email for any interesting headers or other crumbs
- Checked my email address on haveIbeenpwned[.]com (Sure enough my address had been leaked as part of three historical breaches)
- Looked up the BTC address on blockchain[.]com
- https://www.blockchain[.]com/btc/address/1869Xi5tCkzciMdiFnQZ6SyCndJMi4cjuF
- Researched the BTC address on bitcoinabuse[.]com
- https://www.bitcoinabuse[.]com/reports/1869Xi5tCkzciMdiFnQZ6SyCndJMi4cjuF
- Extracted a few more data points from these other reported abuse examples
- Then I started to investigate and build a picture around this raw data using the DomainTools Iris Investigation platform. I found out a lot of interesting stuff but I needed to put it all in context, more practiced eyes than mine were required.
At this point I had almost convinced myself that I was not the target of a spearphishing attempt—but rather a low maturity spam style sextortion campaign leveraging old password data—likely purchased online and delivered spam style with a mail-merge ‘esque email template.
But I needed corroboration, confirmation, and really just someone more experienced in threat intel than I. Enter one of our senior security researchers, Chad Anderson, who was kind enough to contribute to this investigation.
What is Sextortion:
The FBI defines sextortion as “a serious crime that occurs when someone threatens to distribute your private and sensitive material if you don’t provide them with images of a sexual nature, sexual favors, or money.” We know from analysis by security firm Sophos that these extortion emails have been on the rise in 2020, rapidly increasing throughout the year, and that millions of people receive them every week. New tactics, like the one above using a previous leak as leverage, are being used to place additional pressure to pay on potential victims. This mirrors the evolution of ransomware in some ways to their double extortion methods.
Although the emails may seem alarming at first, they are nearly always a scam and the attackers do not have any imagery whatsoever of the people they are attempting to extort. They rely purely on fear, unfortunately an effective tactic. In this case, there is evidence of the efficacy of this campaign—many of the Bitcoin and Monero wallets are far from empty. After some digging, I discovered some of these wallets exceed nearly $500,000 in gains. In fact, these scams so commonly involve Bitcoin that there is an official Bitcoin blog on sextortion scams.
These emails almost always get sent from compromised email servers from around the world—and this example is no different. This makes it trivial for extortionists to hide their origins and can make attribution even more challenging. However, one can understand more about the extortionist and their attempt by looking into the data available and potentially inform a systems administrator of their compromised email server to cut off one distribution mechanism. First, I always like to follow the money to find out if there have been any victims of this scam and if others have reported the wallet address yet.
Follow the Money
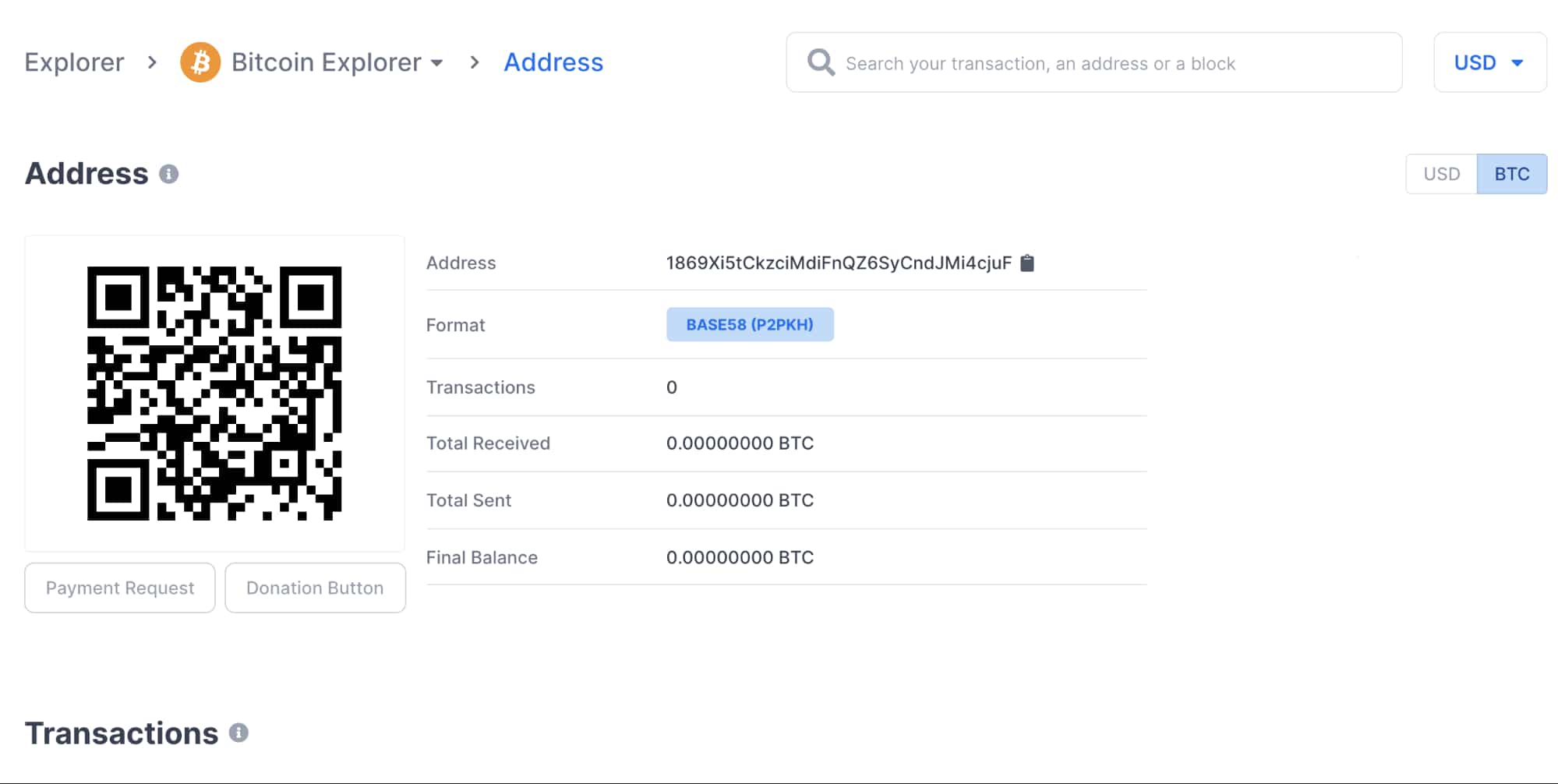
In this case, the Bitcoin wallet requesting money was 1869Xi5tCkzciMdiFnQZ6SyCndJMi4cjuF. Below is a screenshot of that wallet on the blockchain explorer. As illustrated below, no Bitcoin has made its way into the wallet yet, so it is unlikely that this extortionist has been successful with this address so far. To confirm that, I’ve included a screenshot highlighting that there have been no transactions that have come in or out of the wallet— meaning this is a fresh address.
While it is certainly possible for an attacker to create a new Bitcoin wallet for each and every extortion email, we know that because millions of these are sent out daily that attackers would have to be generating millions of wallets per day to make that work. These extortionists are, like many bad actors, lazy and only do the bare minimum for what it takes to get paid. The likelihood that they are spinning up a separate wallet address for each transaction is minimal.
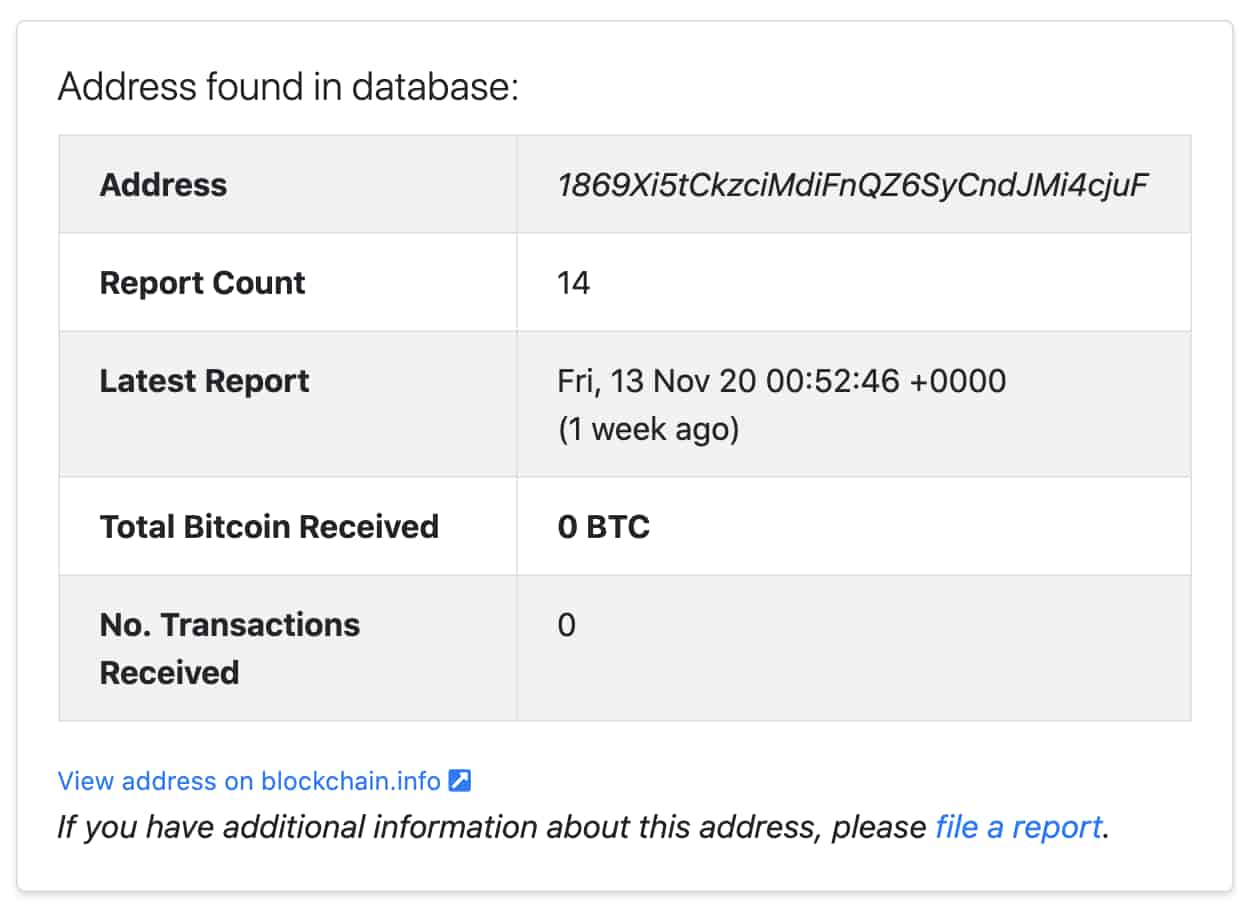
To confirm this, however, we can go and look up this address on the Bitcoin Abuse Database. From there we can see 14 reports with the first being submitted in August of 2020. From this, we can derive that this extortionist has been operating since at least then using this same address. Additionally, many of the reports include email addresses that were used by the sender which can give us some additional clues to find the potentially compromised infrastructure the extortionist is using here. We’ll take those email domains and move on to following the infrastructure.
Follow the Infrastructure
The first things to look at when investigating any email message are the headers. These are the additional, usually hidden from the user, metadata points the email servers ship along with the actual message. These can include information about the server receiving the message, various information about how it was passed along, and finally some information about the client. A clipping of the exact email headers are included below:
Received: from Gibson.wayout-offroad.com (static-pool-87-205.flagman.zp.ua. [46.46.87.205])
by mx.google.com with SMTP id a1si7144373ool.50.2020.11.10.12.28.30
for ;
Tue, 10 Nov 2020 12:28:31 -0800 (PST)
Received-SPF: neutral (google.com: 46.46.87.205 is neither permitted nor denied by best guess record for domain of [email protected]) client-ip=46.46.87.205;
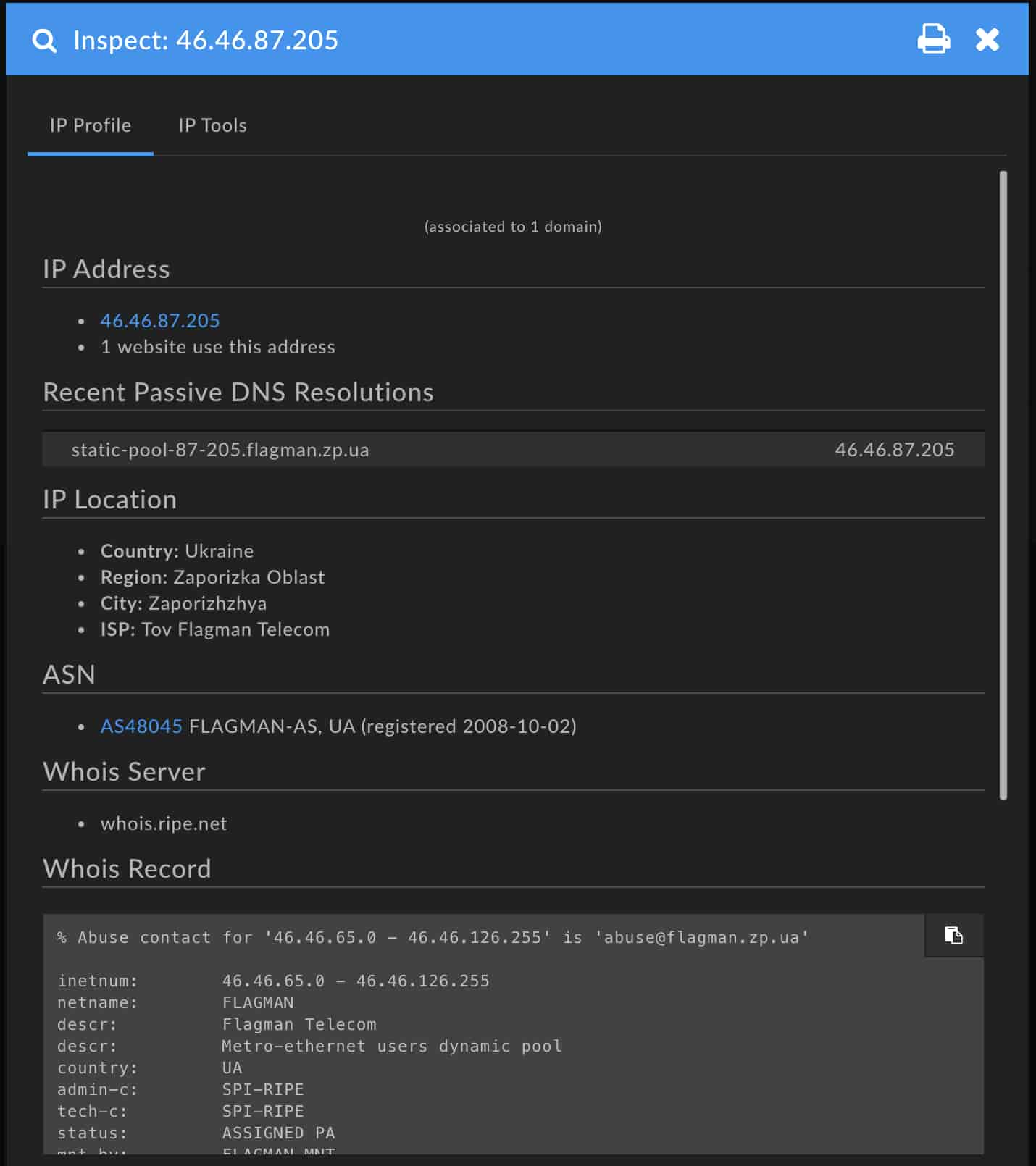
The received header here is important because that header tells us that the client who submitted the email to Google’s servers was 46.46.87[.]205. Looking this IP up in the DomainTools Iris Investigation Platform, it’s apparent that the IP belongs to a home Internet connection on the Ukrainian ISP Flagman and is located in the city of Zaporizhzhya. The fact that Zaporizhzhya is a city of under 750,000 people, this is a residential address, and that Zaporizhzhya isn’t known for being a hosting center where compromised email servers might reside makes us think that—although hard to confirm_this may actually be the extortionists IP address at the time of sending the email. We would need more data points to know for sure though.
After reaching the end of that investigation, the next step is to take a look at another piece from the Bitcoin Abuse Database. Each of those 14 complaints, plus our own attempt, had an email address associated with it. Can we find a relationship between those domains? Perhaps they were all the same hosting provider or ran a vulnerable version of WordPress? For this, we turn to Iris where we will take all of those email domains and plug them into the Pivot Engine. We could do that manually or we could import using the search hash below.
The below DomainTools Iris search hash will replicate how to pull all of the data points discovered during the introduction into an active investigation using only one query in the platform.
Import Hash:
U2FsdGVkX19DfLdXq9q9bKrUcph010ErS87LQEwmdaYIu49DteohoR+3sHPjjht5Mz+t33Ou8L5MsCyXatrt9+dHXRKp2WltjQaxxEptp/rz6oSUi7g0wKF3OJ8jpVPtYVVSy38hK97+HR6u5WNhLoZ+841b7rz1L1tFQ7w7QBsOXw2LvASBmWAhnH7l/u0cPbQYS/7QQ5RH/WeUyACTn0bwWotP47yiyFvCj0lfCOLlcQhxaey8qXw/DZqbUTR31xIX8PY0mIwfTTO1XTLqYasCp2t57Hh0G7C/SuhIuvVuwcnKQcyAZeC+s7Oww3bmkDTCYPGjy6o8CV1FsjNgwinL8/sC71qLUhqmDUos+RPC5v+/6KYc0z4+L9G4dsDAfoOyd5sPZGA9Rs6SoGHgbR2li+iKiJtfLqrhrH3UkWSy974pIgj++SaI3x0Uvs3BS90gHtumCUkFee9Spq3PrPtMkFt6eKL1yBi8C0vn8GMKzcAxP7eLax0ZHcrHfjVwST/z+pE1Gbj4ZpCF+VTUqDk4tCkpOqBCtwHmgJPzsDlORzBr53UzsKNEARxG8RDKSz6M8X5PwzHdqS9PIryNDWxbGb939ILlmQMqWhmgSFVrPxCi8ObsFyqV3n0m4qpIQHSAw4fmR7Hi78UTx+vfydyw85oQqCSOPb1d2t8vXDw9NxGfOnxfHZtiR5vEcqr9MS57oUnzt6TBF5in538PeZ3k/yrThO5gK0MyN39MtqfvwsqFLTNtO7ivytkncYrR0gTC6NjASojSgDrNhD8FX4sgJ5kXKUUbYqy+s2fuIbR5qlF0VWnctTNsddGsiTCX94GGn3iEujWUBqDuDP/WXvEJm4OHOJi9sgxKPlNBGMjeMnWNWpS2sYajHUnyXT+88toHHoiYNl1MQ7pun/x/+34pKzL6o65iTxSND8wE6fGh33qTpgcX4od91p/XsvJw+mujePBZ4lSSPL5dZl8OZxNfjDtx0fkeW2rVxQdGEMg1mJZLgIZ6CEbjuKKSsgQRhDDFXVq5TuhLyPSVXdRcZWAT3fku4XGH4f/+f4cF9ftXPck4Vhkmy8MABf5mtmJfzDZ60dyEHDusgXRYRR6dHPCYthPBTe1+KgjgttKRV5b6rUTWgetJQSYPFJTIMUGED/rQCF8p9tQ3CTLXptvJoLwvFSyu+lJAMDOc0lIV2sbZrHhur3R5YmfuabeHEJasfUFRFAIaaZi9+kge9ciJ44Ia+9n/tn04M62MmwPMCsq4mYgbFiCpSJgZvyCfTeq+xo3oNs581kkqz0qYIAODLxgNLBHpCJeBbZ1miGEwBz5IJT+ZKMm7FCOphhtcApolE6JnFIOG2utFFpcpM69L/BezXlDpqmaoR27W9OmePUK9HK7M+SuSdv3LYzXs6U30cAj8K38BznIfi84GrRcKaA==
While none of the email addresses have been used in the registration of a domain or IP address block we can discover valuable information from analysing the email domains themselves as this was something the scammer mentioned controlling in their email:
Scammer → “if you are planning on going to the law, surely, this mail can not be traced back to me, because it’s hacked too.”
When examining these domains we notice a few things:
- Of these six domains, two of them show a very high Domain Risk Score for a combination of predicted risk in the spam and malware spaces. (Seems like we’re on the right track!)
- All show registration data redaction due to a mixture of Whois Privacy services, privacy legislation, and GoDaddy’s response to GDPR.
- They are all currently active and were created on either March 12th or 13th 2020. (Tight grouping here is usually significant)
- Three of these domains had Hosting IP address changes to new IP subnets on the 30th of Oct. (This could be a potential takeover date)
- Three or more of these domains were registered with GoDaddy before March 2020.
- Skywtr[.]com added some address details in Sep 2020 to identify as being registered in Auckland District, New Zealand. (Unusual behavior in light of its privacy profile previously)
While the above may not mean much yet, these are good insights to keep in mind while performing research elsewhere and may potentially complete a pattern of behaviors.
Given the tightly grouped time of registration, we can make the assumption that March 12 and March 13 are significant in some form or another, but due to the spread of registrars, nameservers, and even inconsistent DNS records, we cannot say for certain that these domains were actually taken over by the attacker. Additionally, there is no link tying the various technologies used on these domains together. Unfortunately, this is the end of this thread as well without further samples and continued observation.
Conclusion
While one can often find out quite a bit more about a sextortion scam by tracing the cryptocurrency wallet associated, examining email headers, and tracing infrastructure in a correlation platform like Iris, you’ll find that oftentimes there will be no definitive attribution that can be determined. While the IP address here is suspect we would need dozens of reports to even begin to form a case proving that a residential user was behind these scams and a way to show that their router wasn’t just a hopping point for maliciousness.
As always with these sorts of scams, I recommend never engaging with the scammer or paying the demanded sum. You should always report them to an abuse tracker if possible and if pointed enough to your local authorities, but be ready to not find a resolution as these are near impossible to fully track back to a single scammer. If truly concerned, we suggest covering your laptop camera and microphone when not in use so you can be assured that no one has recorded you without your knowledge.


