Hunting Avaddon Ransomware Infrastructure with Jupyter and DomainTools Iris API
Avaddon Ransomware
The Avaddon ransomware is a new ransomware threat launched at the beginning of June 2020 and being delivered via email spam campaigns. Avaddon has been seen in the wild presenting itself as a malicious JavaScript loader file masquerading as a JPG inside of a compressed ZIP file attachment. When executed, the JavaScript loader will launch both a PowerShell and Bitsadmin commands to download and execute the Avaddon binary from a C2 server.
If you are a defender and an asset in your environment has been compromised by Avaddon, we can walk through how to leverage the DomainTools APIs and a Jupyter notebook to interactively investigate and respond to this threat. One of the big benefits of using Jupyter notebooks for security investigations is the ability to turn your working code into a repeatable, sharable and collaborative tool amongst your peers.
In this post-compromise scenario, a single DNS request was made (Myphotoload[.]com) from an Avaddon binary detected by your EDR solution. Do you have confidence in a post-containment scenario that you have the proper intelligence to block all of the associated infrastructure with this specific ransomware threat?
Leveraging DomainTools Investigate API for Incident Response
Let’s walk through leveraging DomainTools Investigate API to give us more threat intelligence for better incident response.
I’m going to use a Jupyter notebook and the DomainTools APIs for gathering more threat intel, as it’s important to keep in mind not all security investigations can be fully automated and still require manual interaction to get the data the security responder needs.
Here is a link to the DomainTools API Github repository for our Python library (https://github.com/DomainTools/python_api).
Kicking Off The Investigation
Let’s start by declaring what the Avaddon domain name is we found from our alert. We’ll use this as our sole datapoint to gather more threat intel.
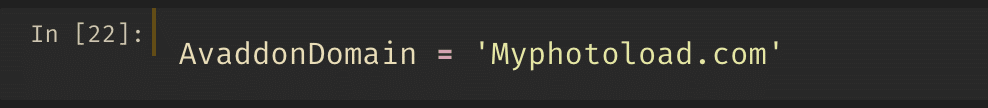
Security investigators each have their own approach to investigation workflows, but I generally operate from smaller to larger datasets as needed. Let’s query the DomainTools Investigate API with the Avaddon domain to get some quick triaging information.
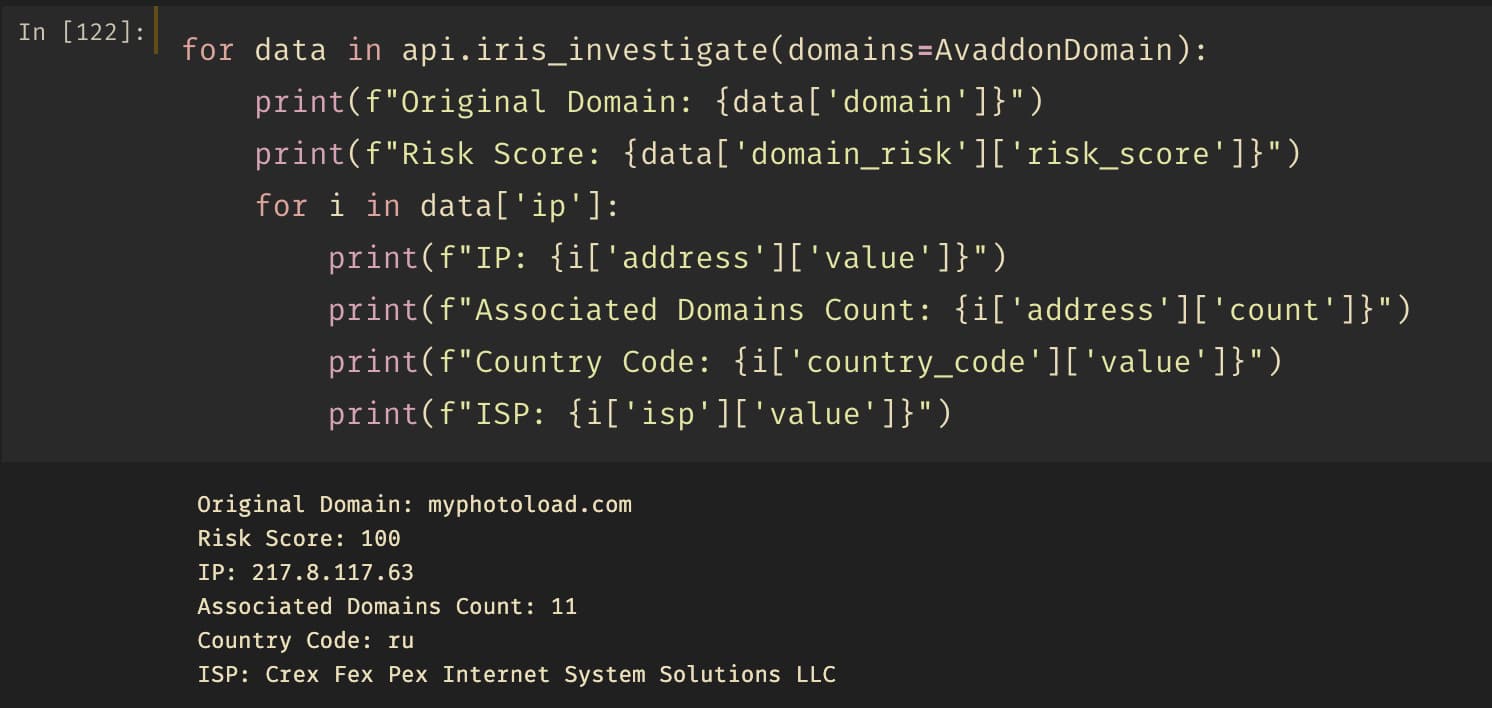
Assessing Risk
With a couple lines of Python and utilizing the DomainTools Python library, we can get some valuable information on this Avaddon domain. We can see it has a Risk Score of 100, which tells us that it has made its way on our confirmed malicious deny lists. Domains that are populated on these lists we can say with high-confidence are actively or historically malicious and can be used for your security control block lists. These types of domains on the deny list are categorized by their participation in spam, malware or the general proximity to malicious infrastructure. So, when a domain has a risk score of 100 we know it’s malicious.
It’s important to understand the country code of the IP address associated with the Avaddon domain. Certain country codes can often represent higher risk depending on your threat model. Some organizations or businesses might say a Russian (“.ru”) domain is more risky according to their threat model. In this case, we can see that the Avaddon domain is associated with being hosted on Russian infrastructure along with other data points we’ll need such as the IP address.
Identifying Additional Malicious Domains
Finally, one of the most important features in the DomainTools API is the Pivot Count for the IP address: 11. This tells us, quickly, there are 11 other domains associated with this single malicious IP address. An initial security responder might simply add the known malicious domain to their block list and move on, but we have the ability to leverage the DomainTools threat intelligence dataset to get 11 more domains that are associated with this threat to proactively block. This allows us to dramatically reduce the risk of future compromise from this specific threat actor and ransomware. If the attacker actively leverages these other domains in their attack lifecycle, we now have those domains to contain immediately as opposed to being reactive to the attacker shifting their operations to another domain.
Let’s query the Investigate API to get those additional 11 domains using the IP address we previously associated.
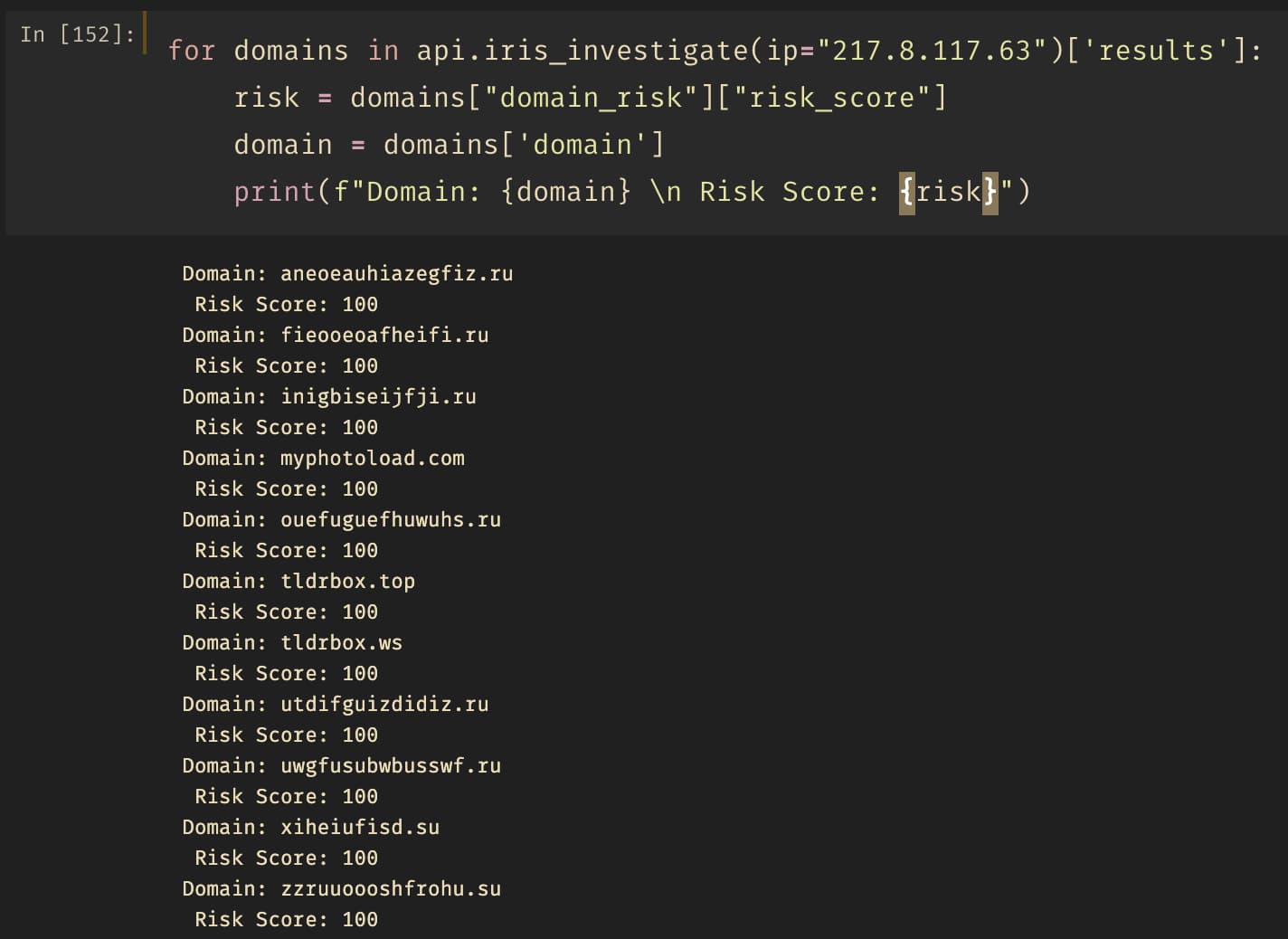
These are actionable domains we want to block, but also investigate. Have you had any of your machines in your network make DNS requests with any of these domain names? If so, that is a high indication of an additional compromise or potential lateral movement by the Avaddon threat or threat actor.
GDPR policies make WHOIS retrieving ownership data on a domain more difficult, but there are a lot of other options we have as defenders to connect attacker infrastructure. Datasets such as the historical domain registrant contact information and SSL certificate metadata (and their pivots) are extremely helpful for expanding your investigation scope during a security incident.
Continuing forward, let’s add some simple code to our ongoing investigation into the Avaddon malicious infrastructure.
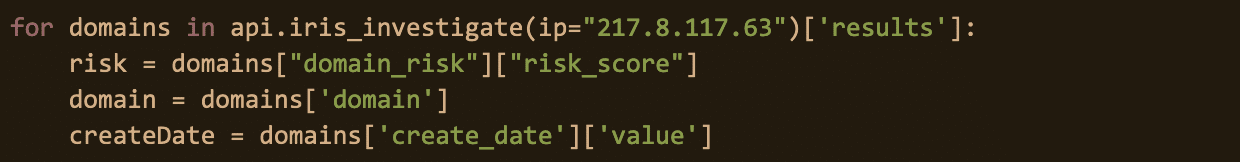
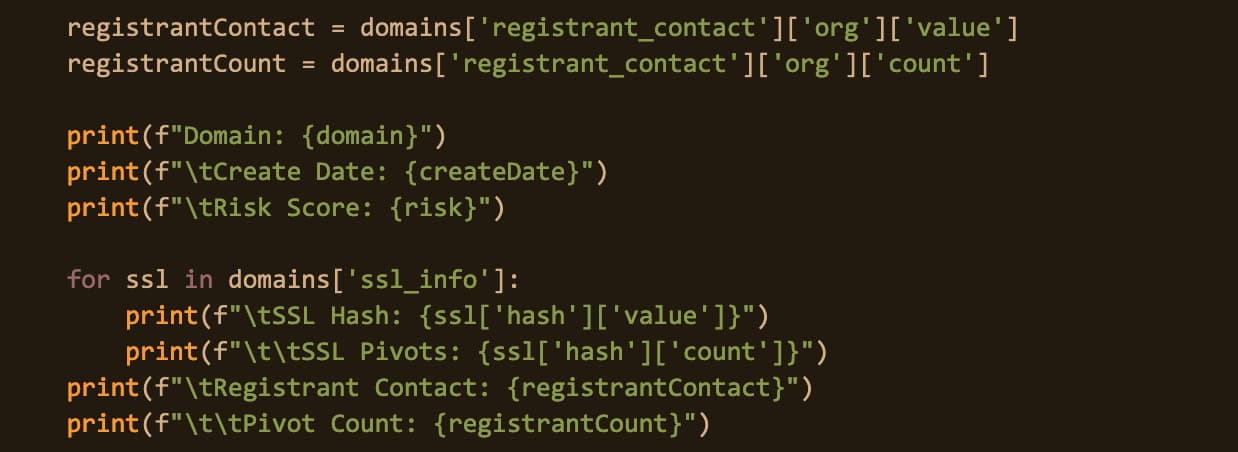
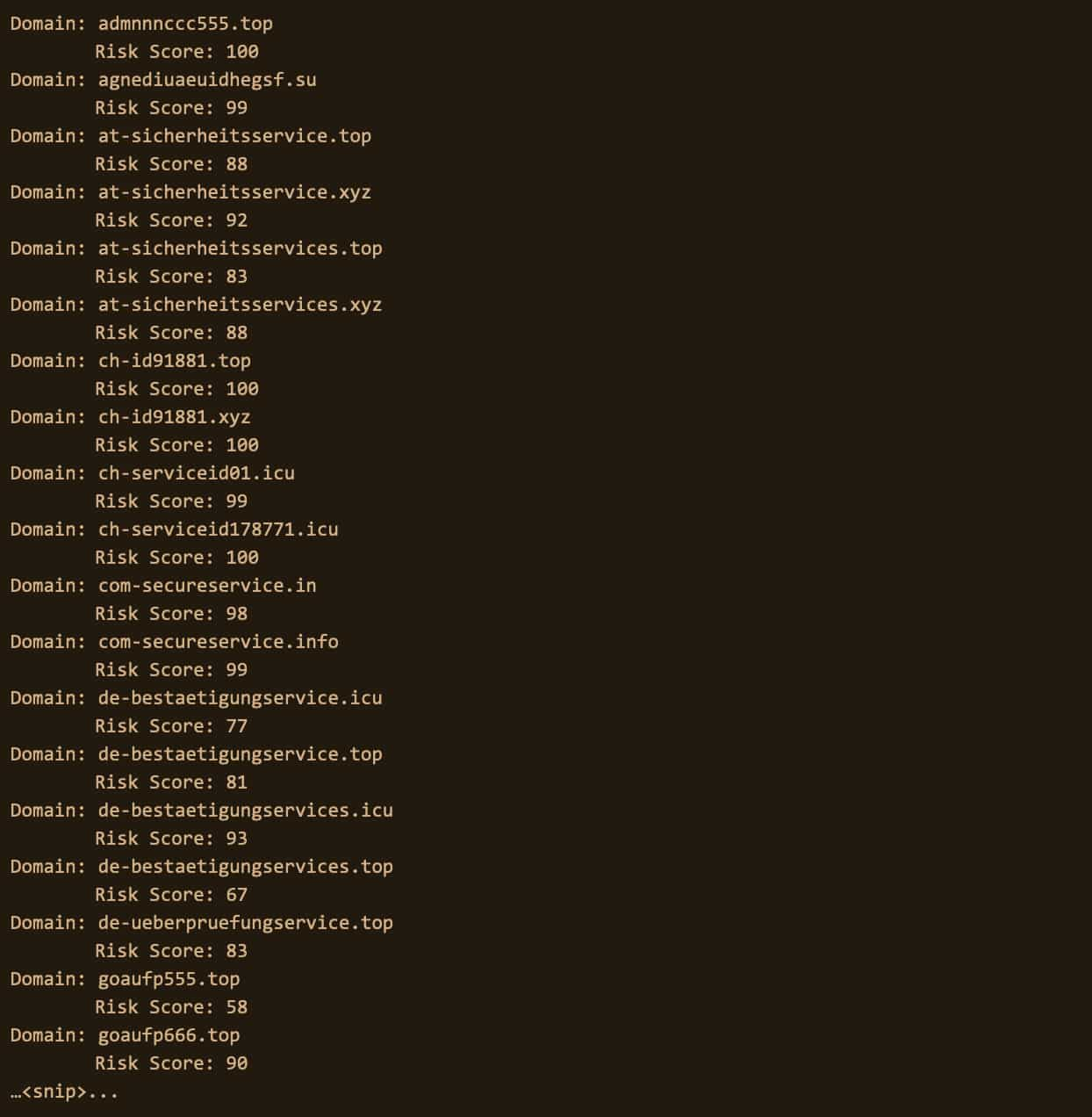
And we can see some immediate actionable data in our Investigate API response. Below, our code populates domains associated with Avaddon’s original IP address with a Risk Score (to help us gauge how risky the domain is). We can also see a really interesting datapoint: the SSL certificate associated with the Avaddon domain ‘ouefuguefhuwuhs.ru’ is also connected to 30 additional domains.
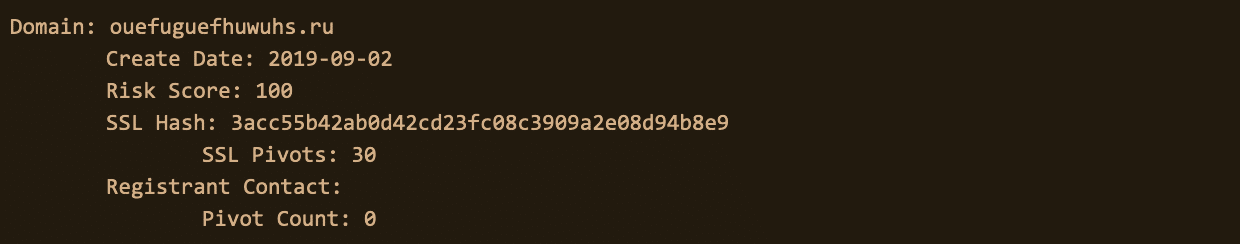
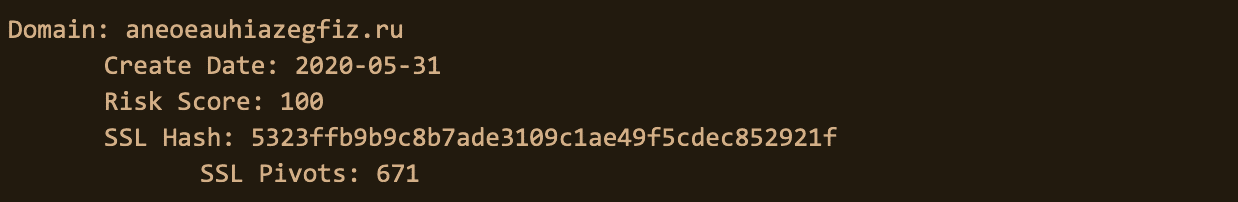
It’s important to note that Pivot Counts aren’t always actionable, in fact, when counts are generally really high (like the below associated Avaddon domain) we should generally dismiss that pivot point.
Furthering Containment Efforts
One thing we need to be cognizant of as security investigators is digging too far down the rabbit hole. In this case, we just want to see what those 30 additional domains associated with the single Avaddon SSL certificate and what their risk scores are. The goal here is two fold: get more infrastructure data to see if any devices on our network are communicating with them and furthering our containment efforts by expanding our block list.
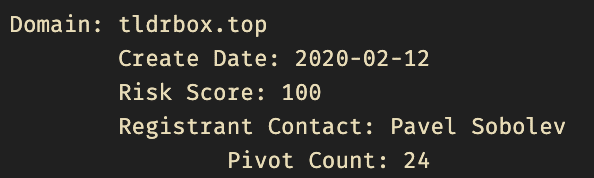
Registrant contact information is still really useful. We can see that these domains are still relatively new, but we can leverage the registrant contact name and see an additional 24 domains that contain that same registrant contact. We should look at those associated domains risk scores and determine if we need to action them.
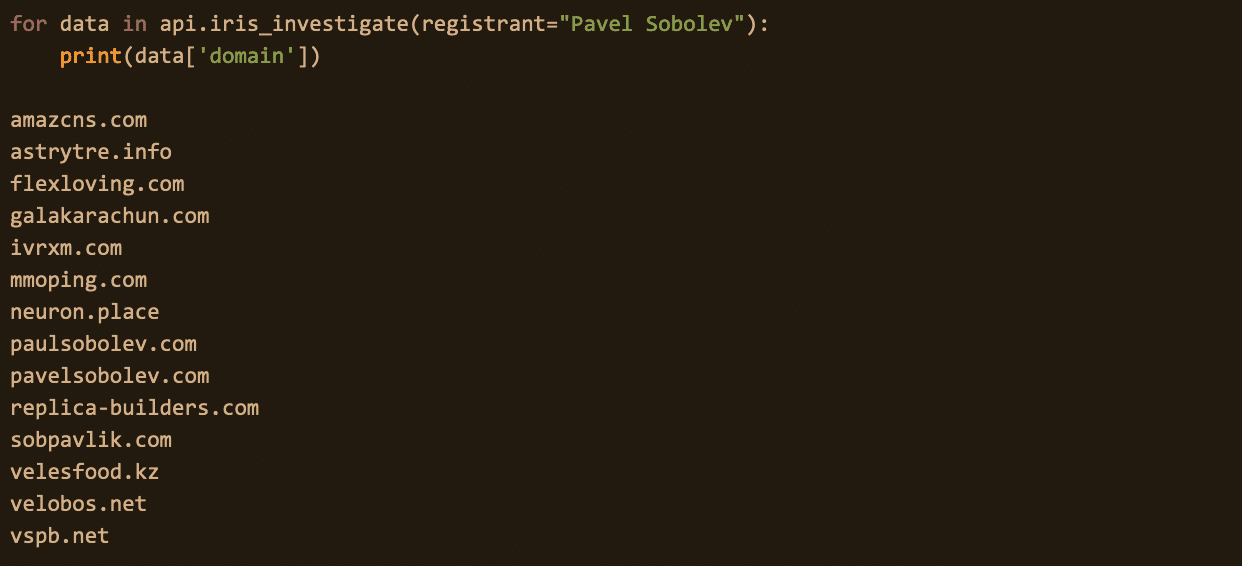
For those of us who conduct investigations, having a means to visualize the threat is always helpful. I created this Avaddon infrastructure mapping using the Python library ‘networkx’.
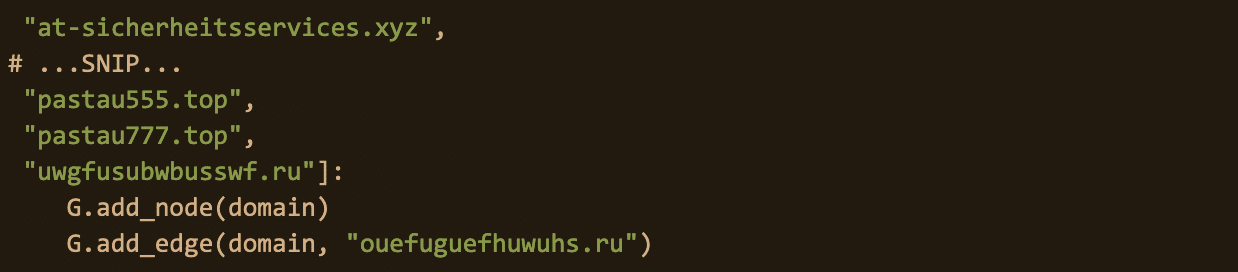
Creating mappings of nodes and node edges is trivial.

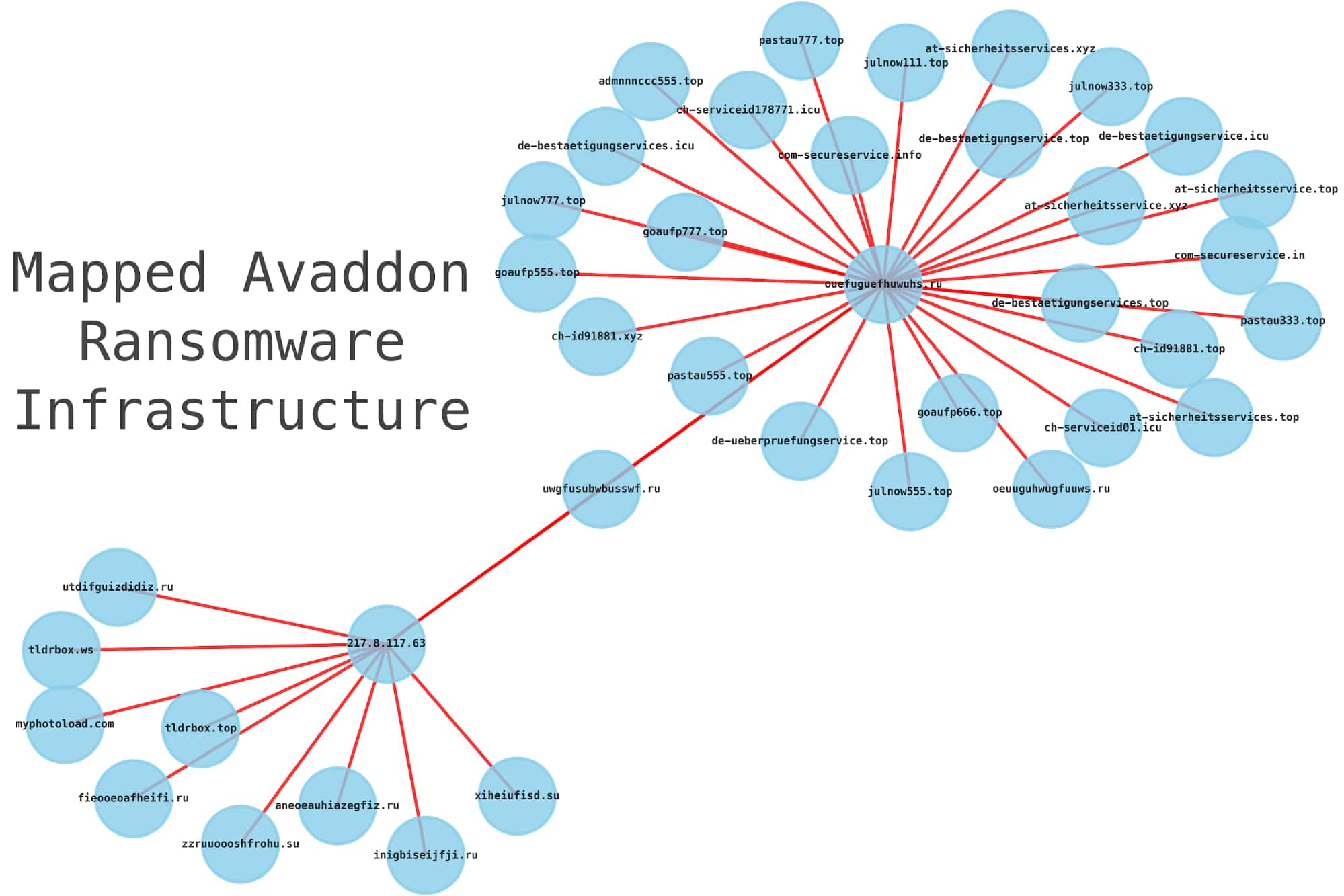
In summary, we took a single known malicious domain from an Avaddon ransomware infection on our network and gathered actionable threat intelligence in an interactive way to use in our incident response process. We used Jupyter notebooks and DomainTools Iris Investigate API in a way that allows investigators to use this as a repeatable interactive playbook for malware infrastructure investigations.
To learn more information on Avaddon ransomware, read my follow up blog post:

