Hunting Down Late Night Security Snacks - Raiding The Domain Fridge

Executive Summary
Security snacks are our way of referring to one-off, bite-sized intelligence that’s difficult to tie to a single campaign or actor due to their ambiguity or isolation. Nevertheless, they remain important bits of intelligence and knowing how to hunt for them can help your organization’s defensive posture as snacks will likely crop up in future investigations tying them to a full meal.
What Are Threat Intelligence Snacks?
Not all Indicators of Compromise (IoCs) are created equal. Sometimes there just is not enough evidence or data tying a piece of maliciousness to a campaign or an actor. Oftentimes generic low-level phishing that sits on shared hosting infrastructure can only be identified as malicious and not much more. Frequently sites will have a curious naming convention puppeting a potential login service or as a typo for a major corporation. While there may not be actual malicious content hosted yet, the naming schema and other components of the domain such as a discount registrar or a known bad name server may point to malicious content coming in the future even if the domain has not been operationalized yet.
These indicators, one offs, and oddities that don’t seem to fit with any known tactics, techniques, and procedures (TTPs) for a tracked actor or that are so generic that they could be anything, we call snacks. The reason behind this naming convention is that we kept finding indicators that didn’t warrant a full report in our day-to-day security research at DomainTools, but we felt the community should still be made aware of their organization’s security. Full reports we tend to think of as a meal, something you sit down to read, consume, and react to as a defender. Snacks, on the other hand, tend to be something worth monitoring and that our gut instinct from years of working in the field tells us will likely be malicious in the future.
How To Eat (Ingest) ‘Em
Since these are largely one-offs and oddities, we feel it necessary to note the importance of prioritization. While a lot of these snacks are interesting, you can get lost as a defender if you go down rabbit holes and pivot your way into oblivion trying to figure out more about a snack. For this reason, we suggest that unless the information presented is immediately affecting your organization that when you find a snack you simply add it to your threat intelligence platform (TIP) or indicator database and then move along. Curiosity is the hallmark of any good researcher and hacker, but only when it benefits your security organization. Let the indicator database surface relationships and build the snack into a full meal as you discover more potentially related infrastructure down the line.
Snack Aisles
There are a number of places you can hunt for snacks and it really all depends on what you are trying to find. If you are looking for malicious documents then a publicly available, industry standard site for analyzing binaries and a combination of YARA rules coupled with exploratory searching will be your best bet. If you’re hunting for malicious subdomains, full path URLs, and phishing kits then the free and publicly available search engine on URLScan.io gives you access to sift through thousands of webpages and the underlying document object model (DOM) behind the sites as they’re being submitted from around the world. However, at DomainTools we specialize in hunting for malicious domains and as such operate mainly in the domain aisle.
New Domains
When looking for malicious domains the most obvious thing you can do is monitor for new domains with common phishing terms. These include the tried and true classics like “365”, “admin”, “auth”, “login”, “microsoft”, and so much more. With DomainTools PhishEye you can receive an email each day as new sites containing your terms and all permutations, including punycode variants and typosquatting, come online. Below is an example for the term 365.
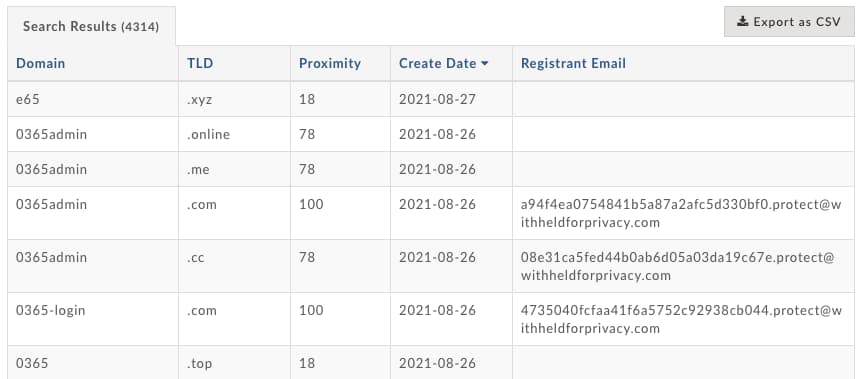
Other variations on this include newly observed domain feeds which provide you with an on-going stream of domains that have recently been registered or re-registered. Some feeds revolve around passive DNS and the first time an apex domain is seen in the data. These sorts of feeds can be overwhelming however so we recommend hunting for specific terms that include your company or product’s name and permutations as a first priority, then followed by the companies and products which may be a part of your supply chain and workflow, then lastly containing speculative queries for generic logins, administration panels, and other software. Rarely do we find that as defenders we have enough time with our day to day to reach the final bit of that prioritization.
Nameserver Tracking
Once you have begun to monitor for new domains you will begin to see patterns emerge in the data. Likely the most useful pattern is the repetition of nameservers. Nameservers are an essential touch point for attackers since if they want their domain to resolve and be accessible there has to be a DNS record involved. In addition to being an essential touch point, nameservers are also difficult to manage and run so adversaries tend to use a single nameserver or service to manage their DNS records. With DomainTools Name Server Monitor you can monitor as domains move on and off of nameservers. Below is an example for site-dns[.]com, a nameserver which tends to commonly be used for low-level phishing campaigns.
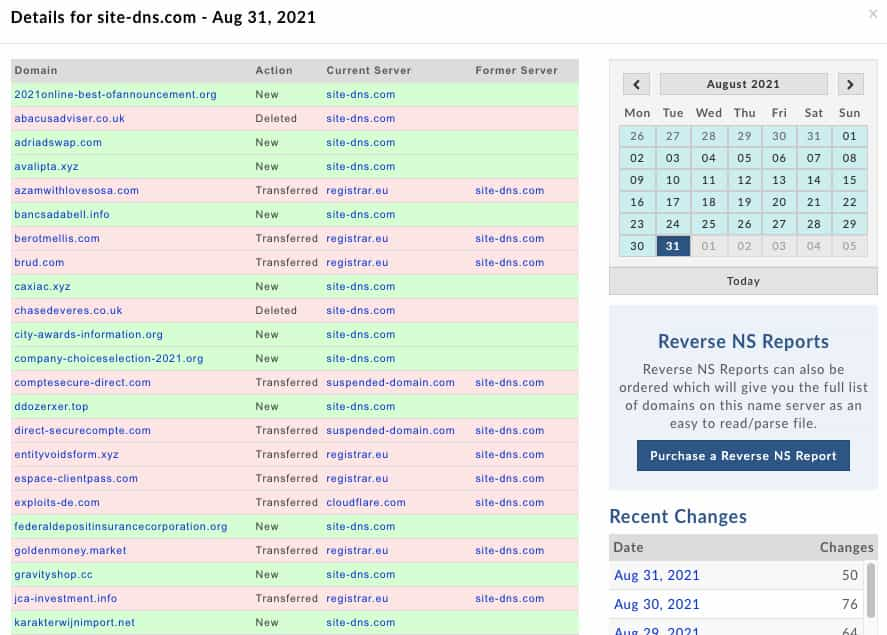
After you’ve spotted a nameserver which tends to host a lot of maliciousness you can greatly expand the amount of malicious domains you ingest each day and even spot new, unforeseen terms that would not crop up in your regular new domains analysis. This is also a useful way to spot campaigns against entire industries as adversaries reuse a single nameserver for say a host of phishing against companies in the shipping industry. Additionally, since domains often transfer off to other nameservers after being utilized you can find holding pens, other malicious nameservers, resellers, and bulletproof hosters recycling infrastructure.
Final Tasting Notes
From this point you’ll begin to spot patterns through snacks and can choose to look at clusters most likely to turn into a full meal, broader threats that require more research to unveil. Some indicators will remain just what they are, individual one-offs, but you’ll have turned a number of short examinations and low effort into usable intelligence all while getting to know sectors of maliciousness around the Internet.
No matter what kind of research or blue team work you are doing there are always little tidbits that don’t quite fit the mold for a larger investigation. These potentially not yet operationalized snacks still remain an important tracking component of any organization’s security posture. We hope that you will share any snacks you do find with us and the broader security community.
Additional Resources
Analyzing Network Infrastructure as Composite Objects
Strengthen Your Investigations’ Resolve with pDNS
Valuable Datasets to Analyze Network Infrastructure | Part 1
Valuable Datasets to Analyze Network Infrastructure | Part 2
Valuable Datasets to Analyze Network Infrastructure | Part 3



