Hunting for synthetic substances using DNSDB Search
The Threat
This week, the U.S. government reported overdose deaths soared to a record 93,000 last year in the midst of the COVID-19 pandemic, up 29% over the previous year, with much evidence pointing to the increased use of the opioid, Fentanyl. The emergence of numerous synthetic fentanyl analogs, including acetylfentanyl, butyrylfentanyl, acrylfentanyl, furanylfentanyl and β-hydroxythiofentanyl, which are manufactured in China, were made available to the illicit drug traffickers over the Internet. If we are tasked to assist the Law Enforcement with finding online resources that offer these chemicals, how can we go about it?
There are many ways, and neither will be complete, however, there is a very powerful tool that usually yields very good results – DNSDB Flexible Search. First introduced by Farsight Security in 2020, DNSDB Flexible Search enables investigators to search, by keyword, for Internet sources for these chemicals. DNSDB is the world’s largest passive DNS database and goes as far back as 2010. For more information, visit our blogs. In this article, we are going to show you how you can use this powerful tool for investigations.
The Hunt
As you may already know, passive DNS allows us to find historical internet resources without querying the DNS of the suspected criminals’ infrastructure – hence, there is no “tip off” during an investigation. Also, passive DNS flexible search allows us to find resources without precisely knowing the Internet asset name (e.g., host or domain). Equipped with this knowledge, we first identify the relevant keywords for substances:
fentanyl, acetylfentanyl, butyrylfentanyl, acrylfentanyl, furanylfentanyl, β-hydroxythiofentanyl, valerylfentanyl, 3-methylfentanyl, carfentanil
and then we identify more keywords that could be used to identify online resource:
vendor, buy, sell, sale, cheap, online, pharm, medz, drugz, pillz (and other relevant terms too).
Once we have the keywords, it is time to put all together in a regular expression:
substance='(fentan|acetylfentan|butyrylfentan|acrylfentan|furanylfentan|b.hydroxythiofentan|valerylfentan|acrylfentan|3.methylfentan|carfentan)[iy]l' resource='(vendor|buy|sell|sale|cheap|online|pharm|medz|drugz|pillz)'
Note, the last [iy] statement in the substance line is used to encounter for possible or deliberate spelling mistakes, e.g. fentanyl/fentanil).
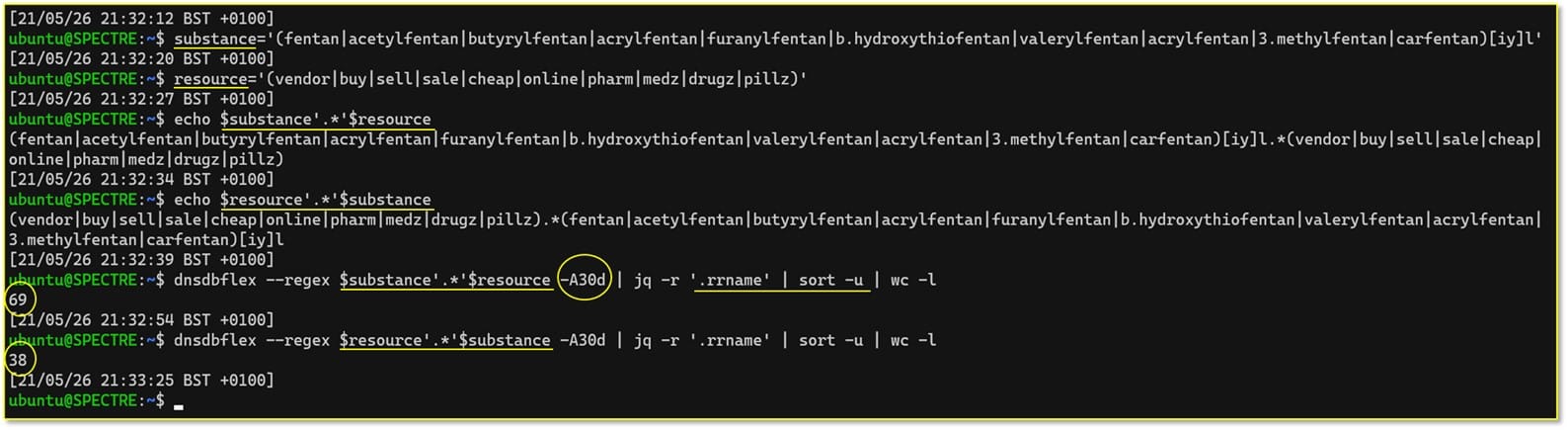
Now it is time to try our CLI dnsdbflex utility in the Unix-like shell of your choice. As you can see from the below screenshot:
- For convenience, we defined two variables
substanceandresource - We checked the permutation gives us the desirable regular expression result
- We executed Flexible Search looking for the resources (in the past 30 days from the time of this writing) that contain the specified pattern in its name, and counted the unique names we found – there were plenty
We now can check what some of those resources were:
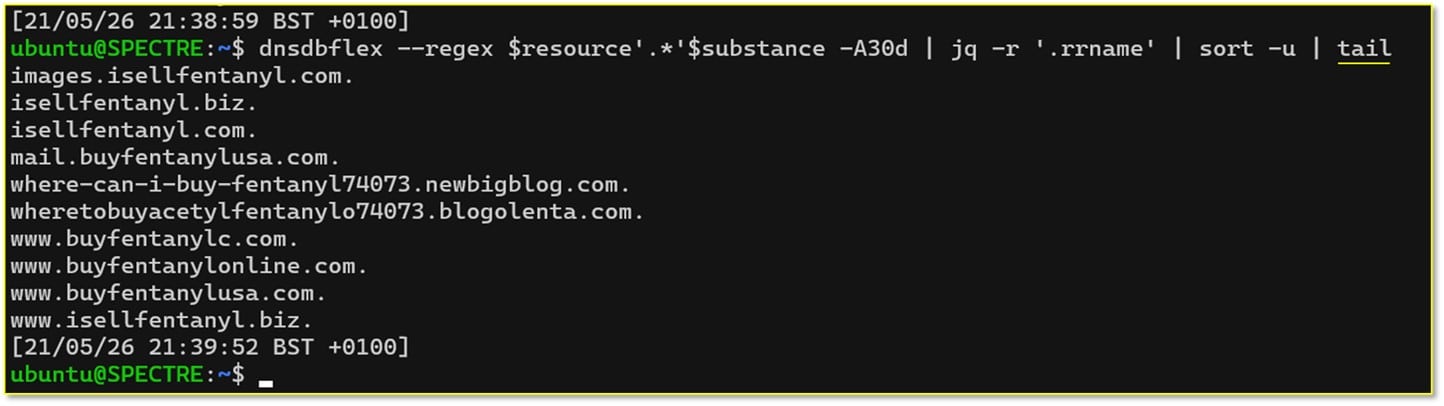
We need to be very careful with our findings and not to be overly excited – some resources are just a product of the “wildcard”:
[21/05/19 20:38:09 BST +0100] ubuntu@SPECTRE:~$ dig +short where-can-i-buy-fentanyl74073.newbigblog.com. 216.180.106.236 [21/05/19 20:39:51 BST +0100] ubuntu@SPECTRE:~$ dig +short where-can-i-buy-christmas-gift-hohoho.newbigblog.com. 216.180.106.236 [21/05/19 20:40:01 BST +0100] ubuntu@SPECTRE:~$ dig +short ab908016e4f78f4703d435a6ee77a49e640a030a.newbigblog.com. 216.180.106.236
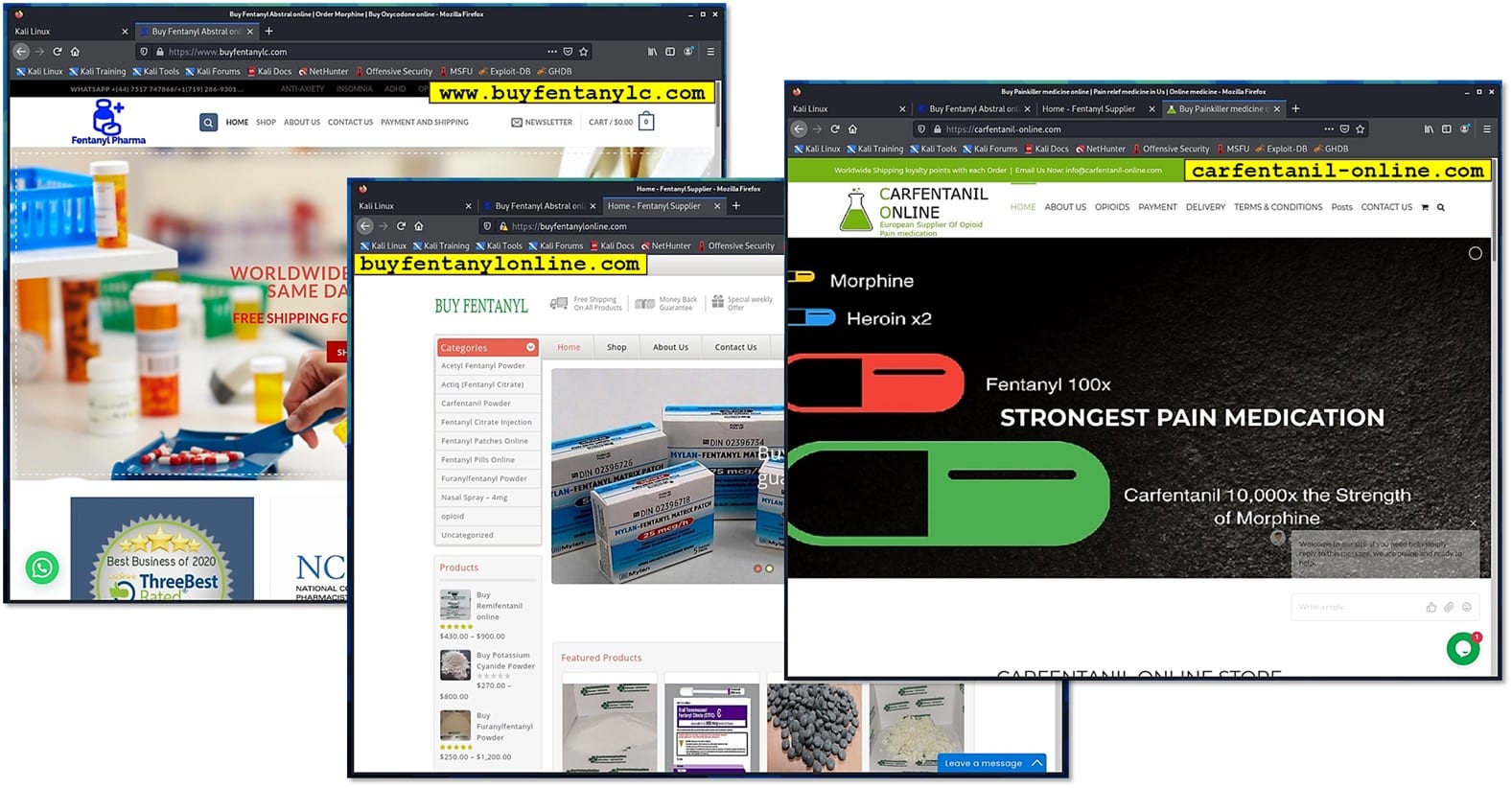
Some other resources, however, yield the results we anticipate!
Please, exercise caution visiting those resources, e.g., at the time of this writing one of them have crashed the fully patched FireFox browser (a sign of 0-day?).
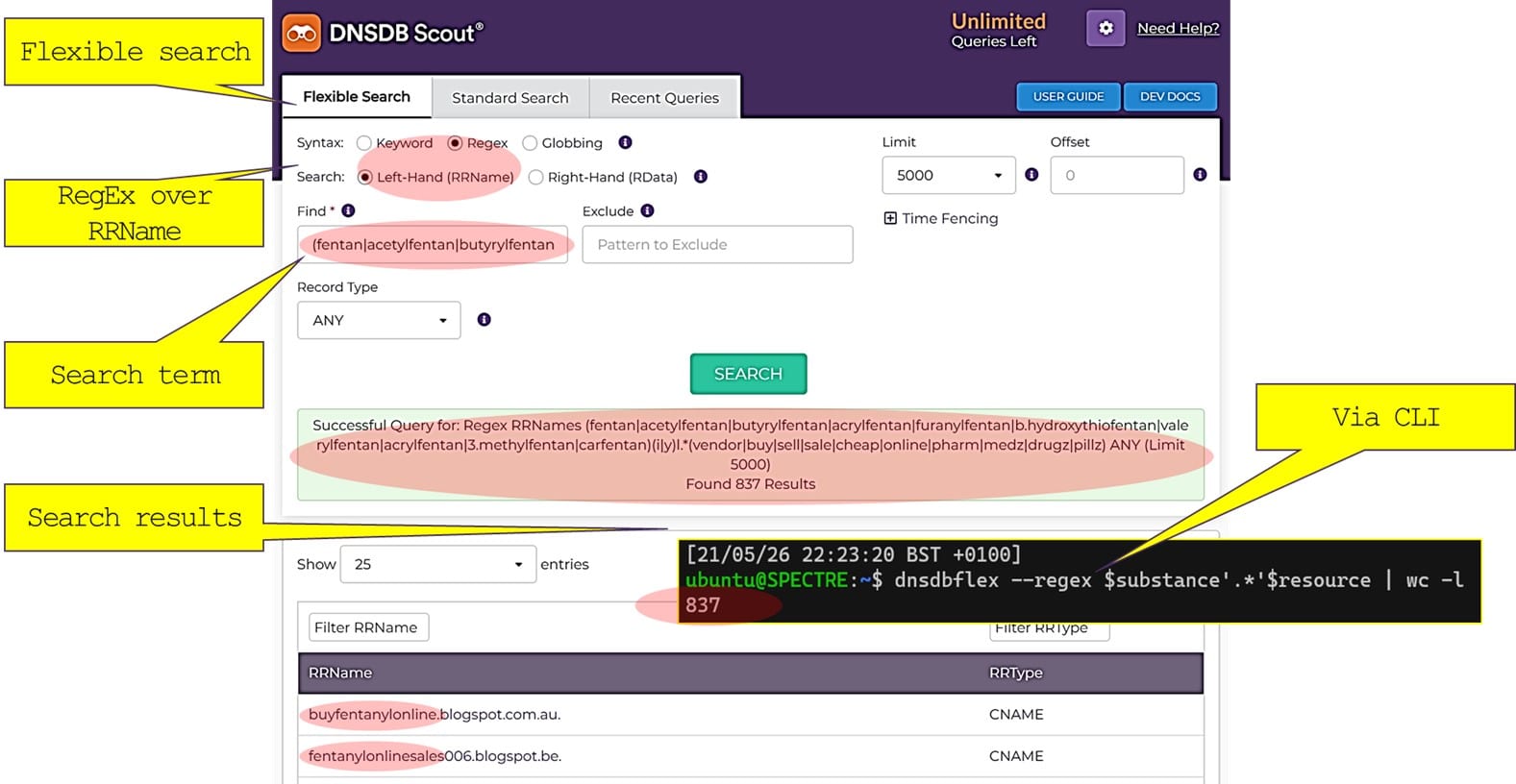
Let’s now do the same with our web-based GUI tool, called DNSDB Scout. We prepare the search term as before and execute. As you can see, the equivalent CLI command produces the same results:
Let’s now dig a bit deeper taking the first website we found at the first step www.buyfentanylc[.]com and uncover its “neighbourhood”. First, we execute a standard search to find the IPs this web site is being hosted on:
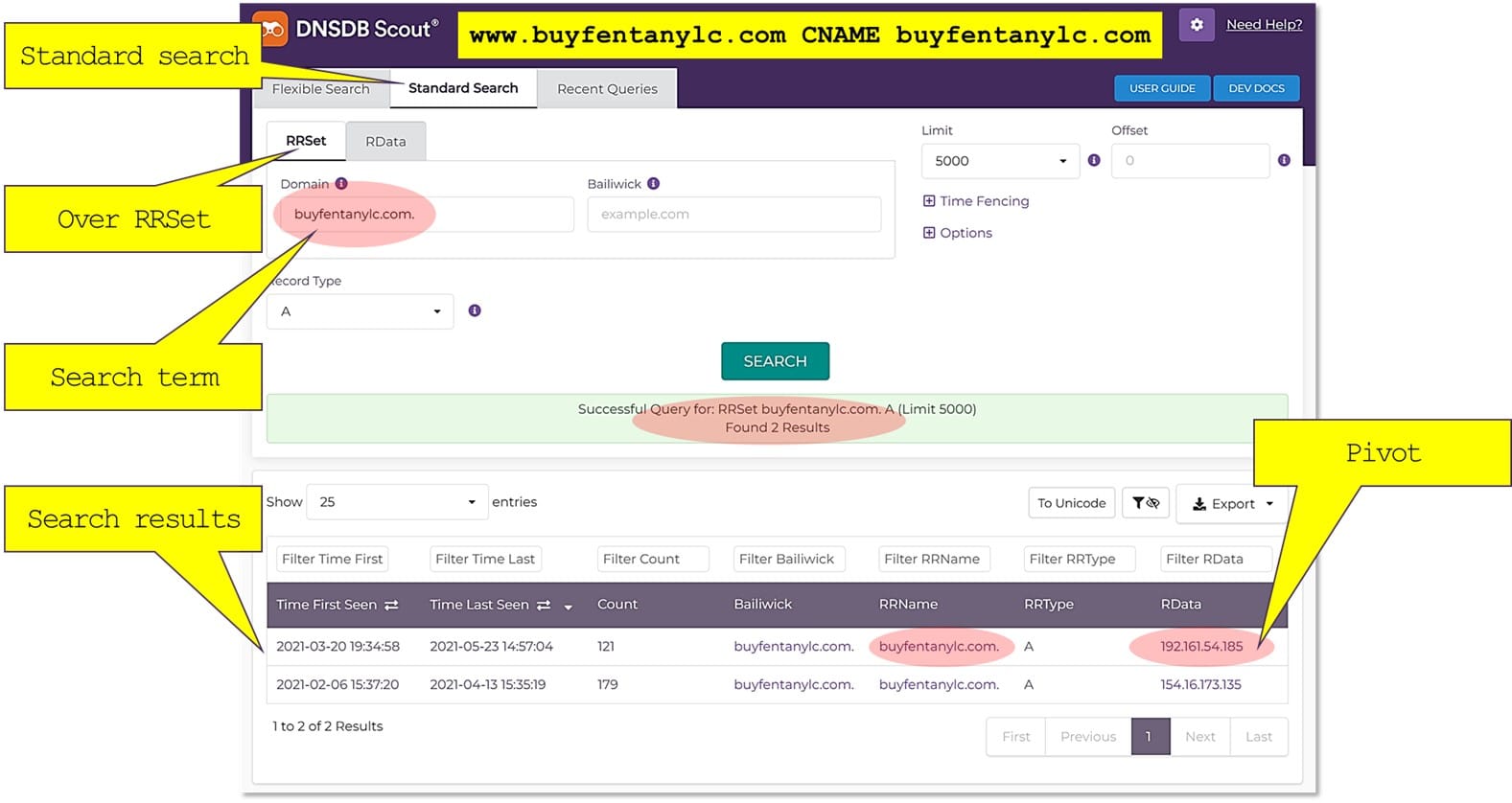
Note, we made a passive DNS search through our historical records vs Nameserver lookup that would leave a log entry in the suspected criminals’ DNS and network monitoring tools.
The next step is pivoting through the IP we discovered, asking DNSDB, the Farsight Security passive DNS historical database. Clicking on the IP address in the previous step, an automatic standard search will be executed revealing the assets that we historically observed were served from that IP:
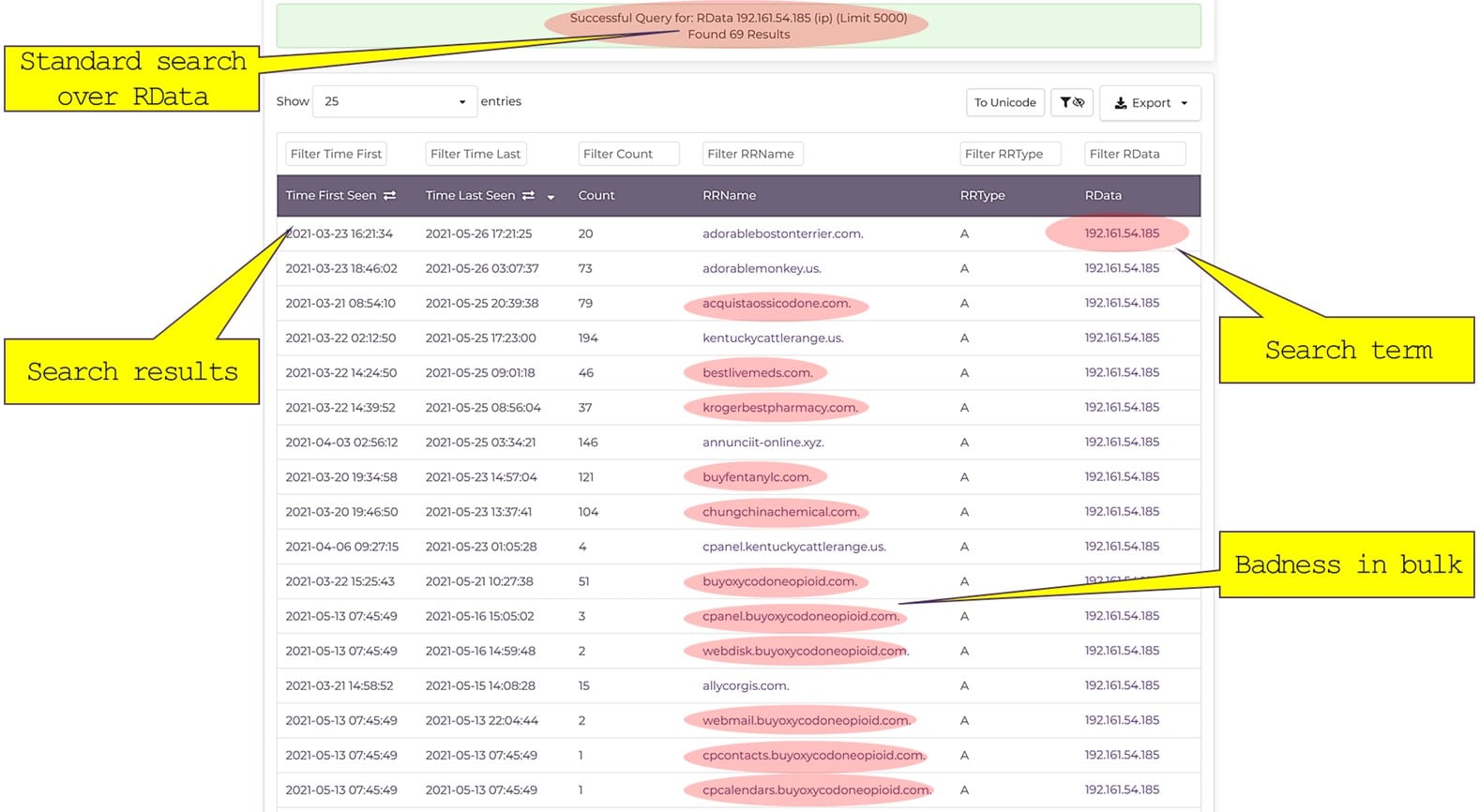
As you can see, there is plenty of names associated with controlled and illegal substances – a goldmine for Law Enforcement to pursue.
And there is more!
What if the criminals used typosquatting techniques to disguise their illicit resources? Our Expander tool comes to rescue! If you are a member of our Labs Community labs.fsi.io (join for free no obligation if not) – you can try our experimental version of Scout with built-in Expander. The idea is simple: 1) use the keyword of your interest, 2) “expand” it based on the numerous of typosquatting algorithms, and 3) execute:
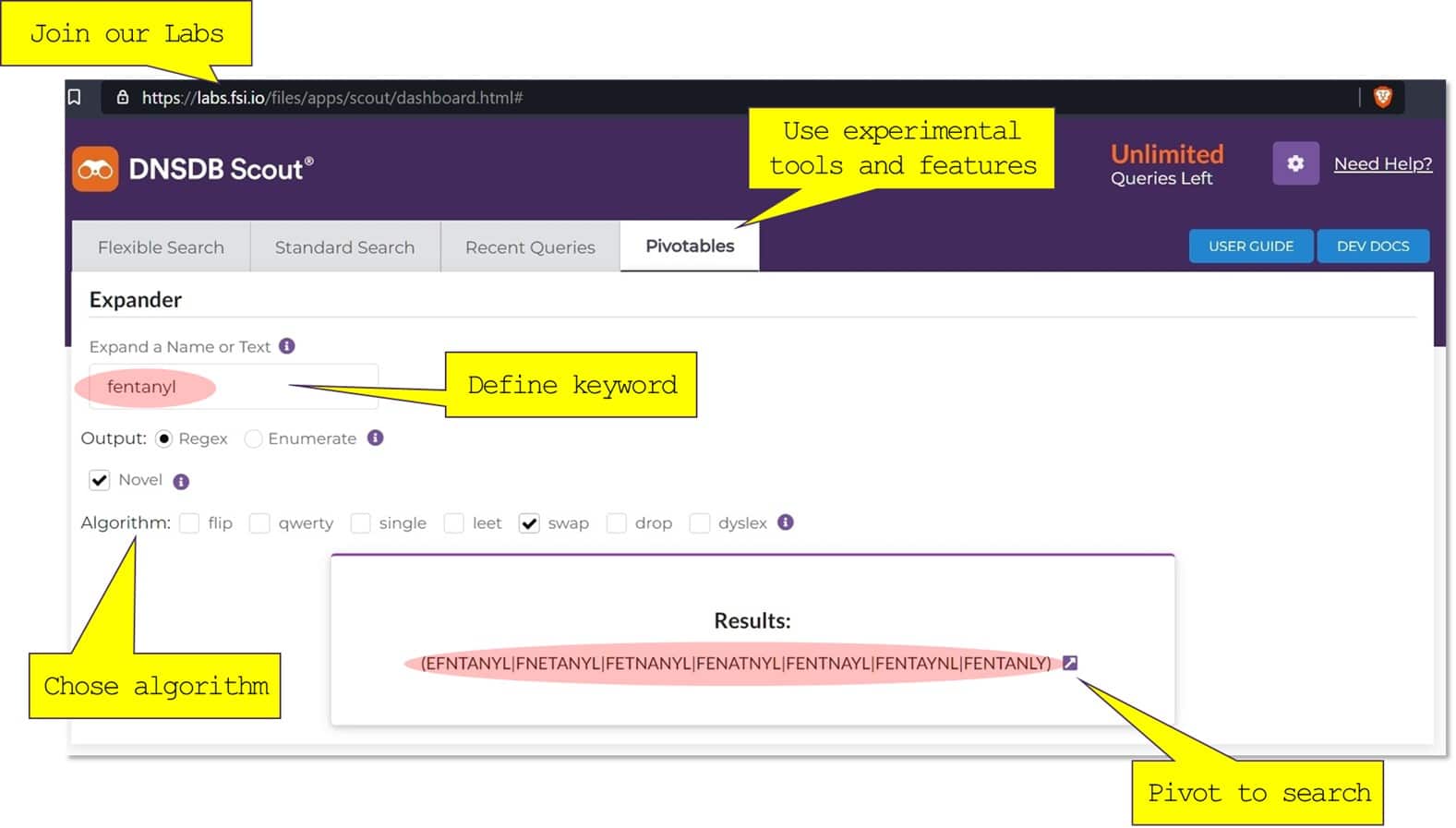
Note, if you have an idea about an algorithm that is not yet present – please, let us know via our forum forum.labs.fsi.io!
Once the query is executed, the results will be presented:
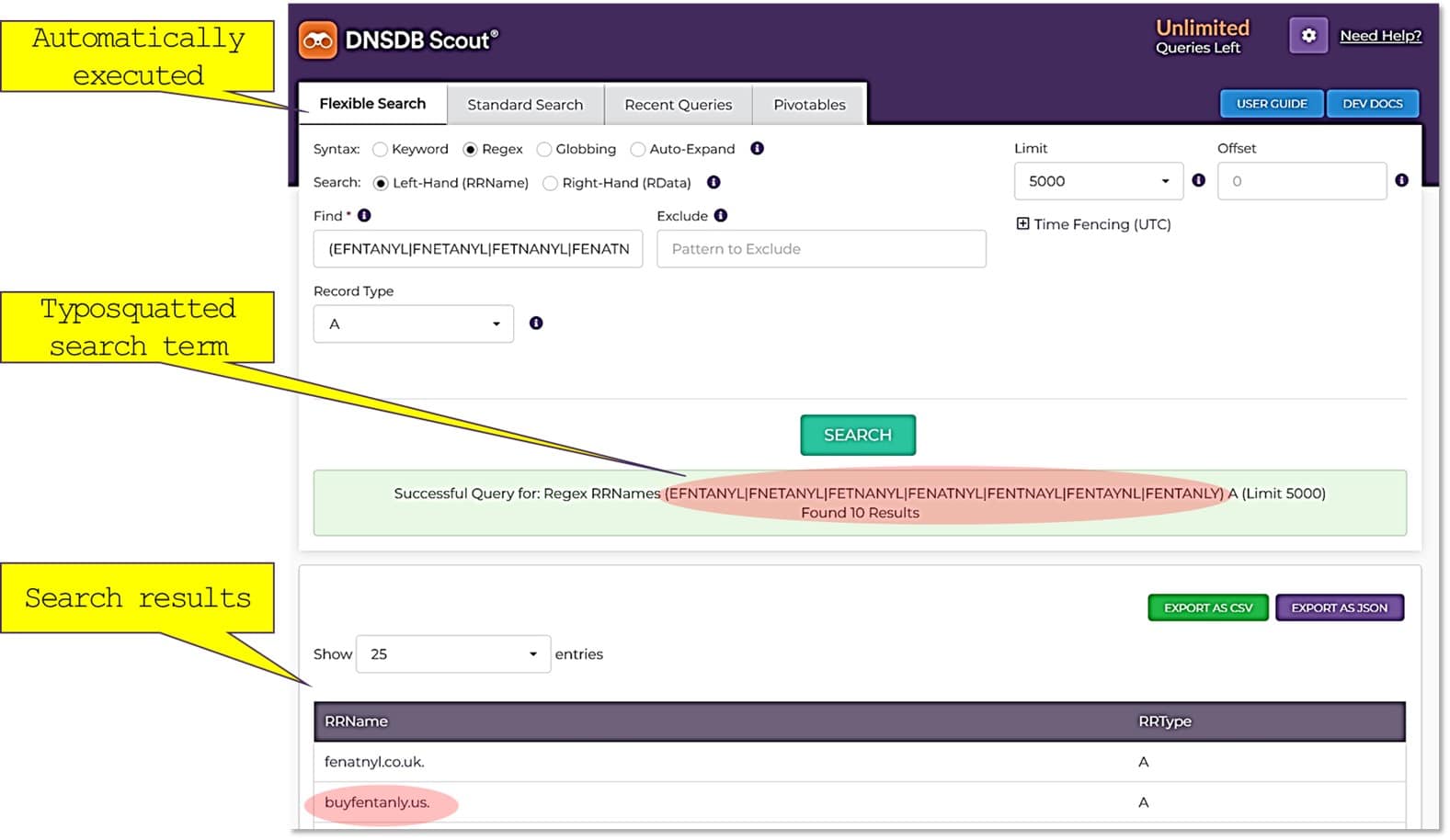
buyfentanly in .us TLD! Who would have guessed?!
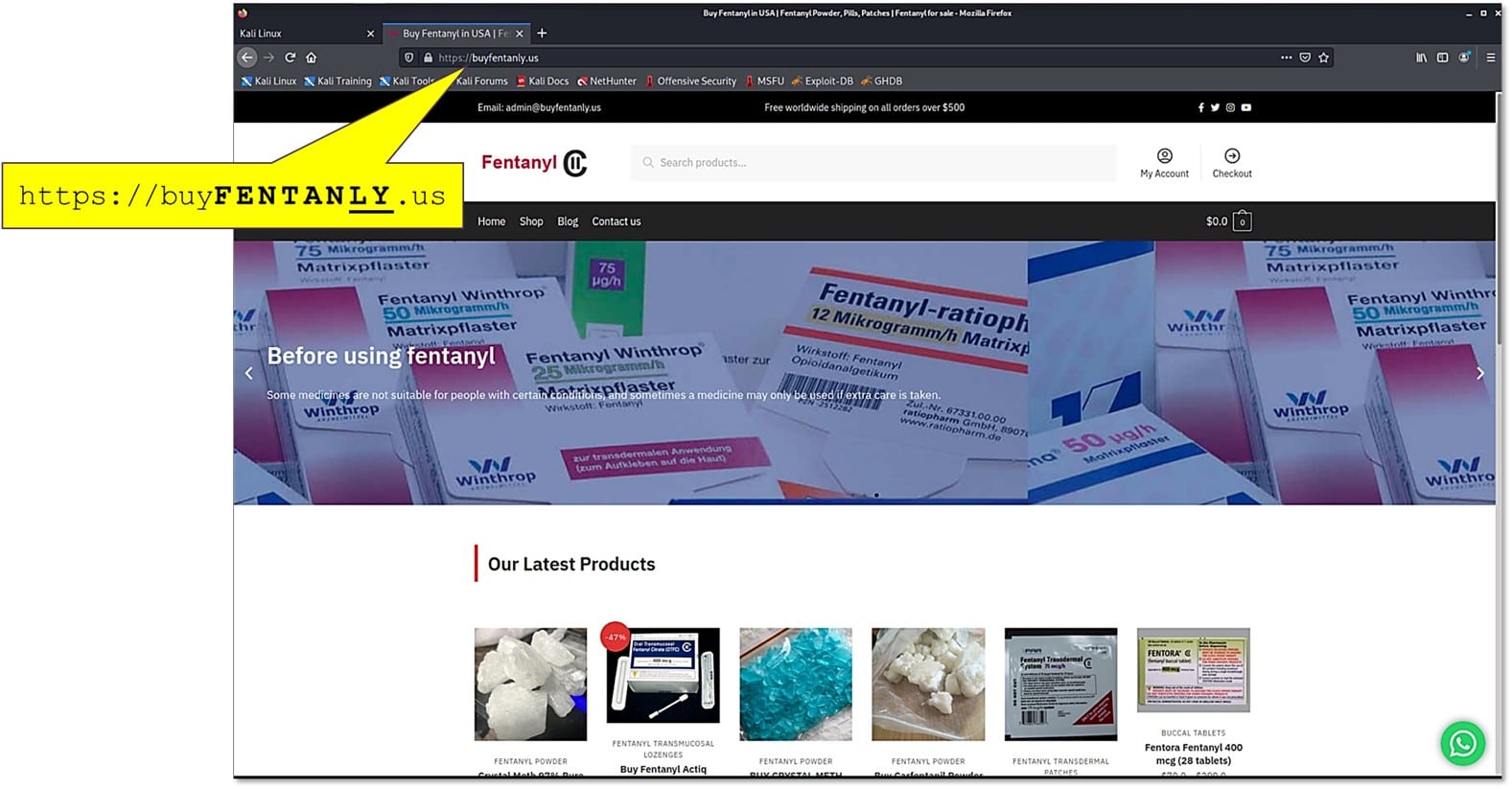
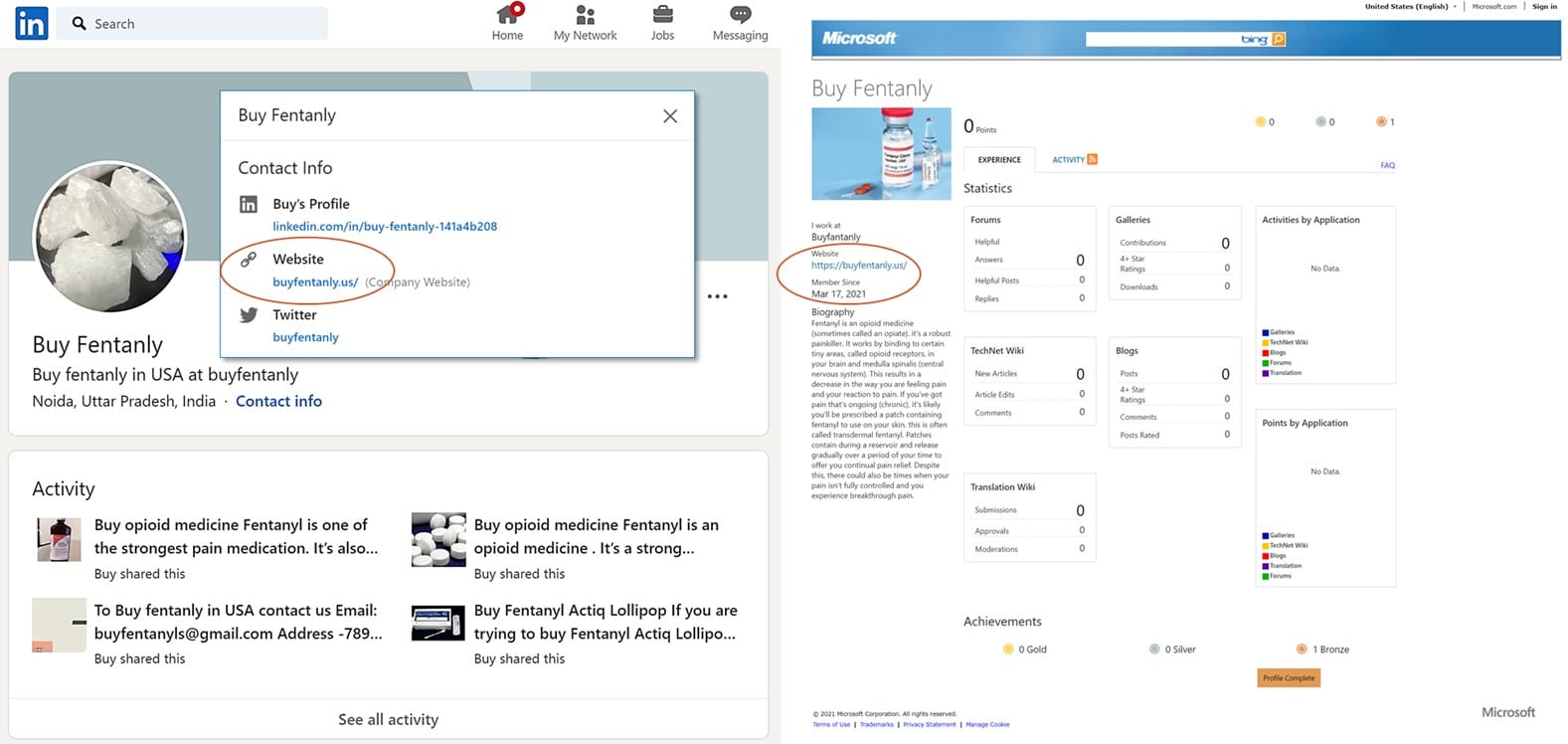
If you are curious, you could also find, that these folks have quite a marketing campaign:
Homework – practice makes it perfect
Following the steps you have learnt, you can try to assist the Law Enforcement further and identify online resources that might sell Scheduled controlled substances. Here is the hint:
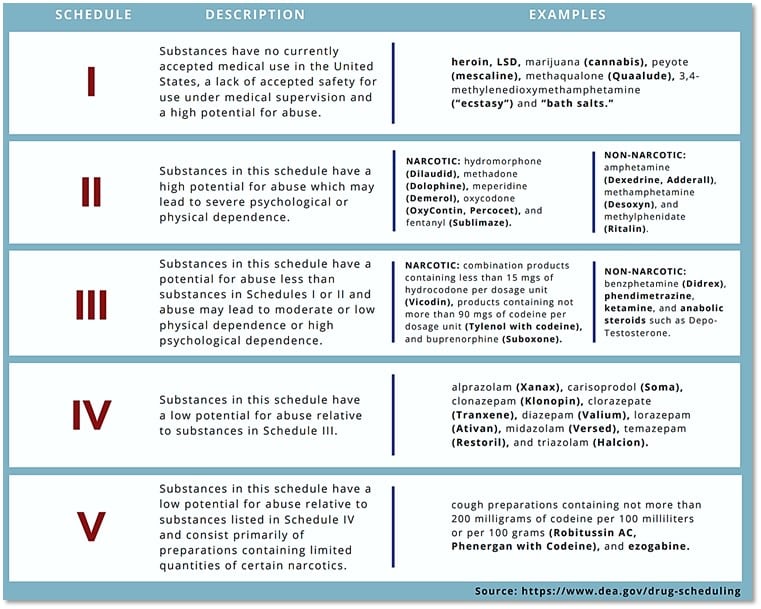
Please, exercise caution accessing the resources you found. Check your local Laws to make sure you are on the right side of it when checking out those resources.
Takeaways
Historical passive DNS records and flexible search are invaluable tool in many investigations, especially extremely sensitive and even dangerous ones. Accessing DNSDB will not tip off the owners of those resources and, therefore, a thorough investigation can be conducted to gather evidence you might need.
Conclusion
Using Passive DNS, specifically Farsight DNSDB with Flexible Search, you can uncover activity and related assets that may not be possible, in principle, by other means. During this research, we learned that using passive DNS observations and Flexible Regex Search we could identify other domains that have similar patterns of the expected behaviour. As it happened, some of the identified activities were likely unrelated. As demonstrated in this research, Farsight DNSDB enables you to improve the efficiency of your investigations, threat hunting, incident response, forensics, etc.
If you have any questions, reach out to our support team [email protected] or ask questions and discuss inside our Forum at labs.fsi.io.
Boris Taratine is a Principal Architect at [Farsight Security, Inc.]({{ site.basseurl }}/)



