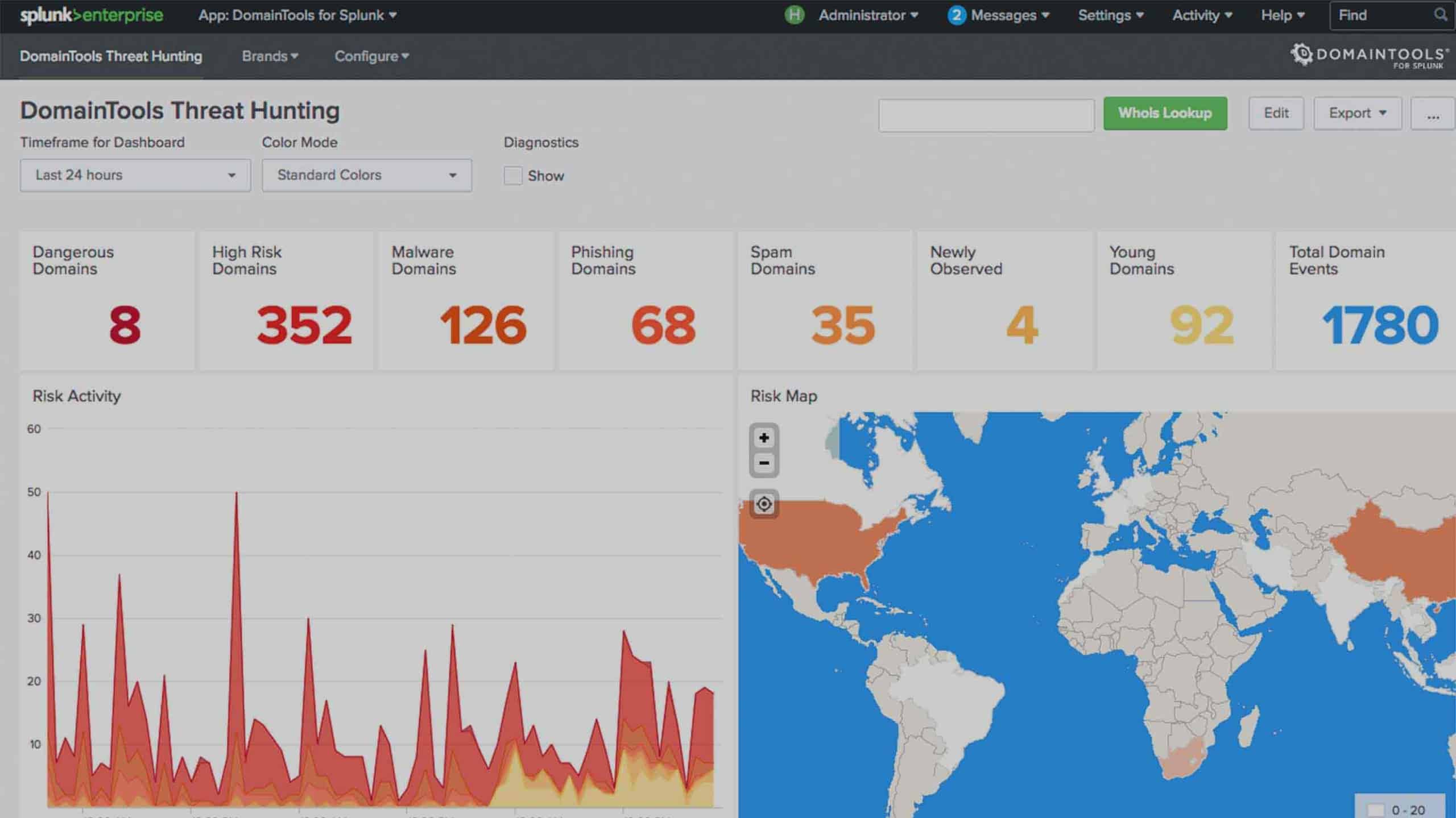
Improved DomainTools App for Splunk
Improved DomainTools App for Splunk
Today, we’re thrilled to announce the latest DomainTools app for Splunk – 3.4. With these enhancements, our customers can leverage the DomainTools Iris Enrich API and PhishEye API for rapid enrichment of domains with Iris tags, Domain Risk Score, domain age, Whois, IP, active DNS, website & SSL certificate data to surface evidence of malicious activity.
In this post, I’ll cover some of the new enhancements we added in this release. During conversations with our customers, we learned of the varied use cases they care about based on differing areas of focus. Hence we are adding functionalities across security operations, incident response, and threat hunting.
Iris Investigation Context to Splunk Events
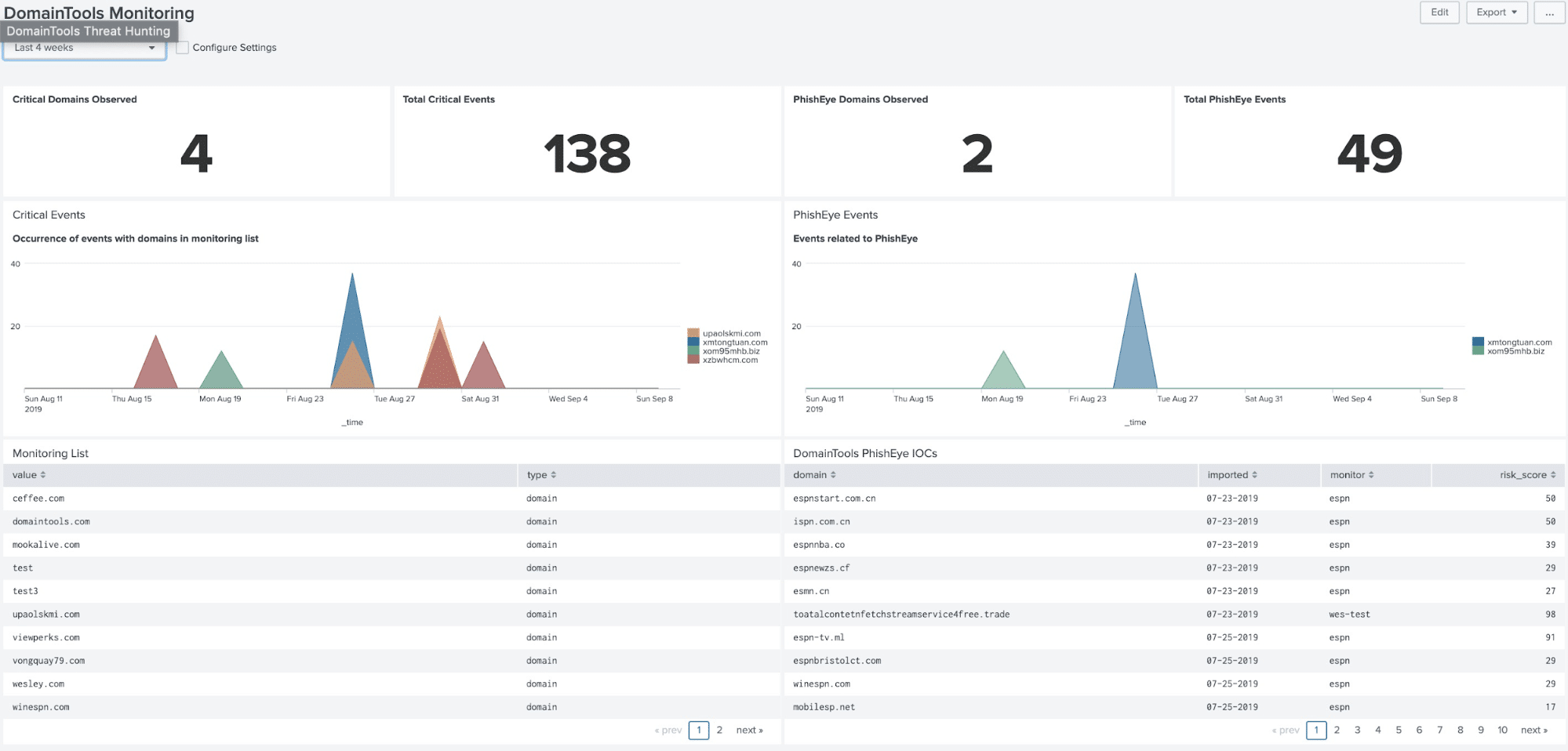
For DomainTools Iris customers who leverage the Iris Investigation platform for investigations, they can now tag observables during investigations for subsequent classification and remediation. With 3.4, we are bringing in those tags inside of Splunk to facilitate a faster-triaging process for all members of the SOC/CSIRT.
This allows the CSIRT to collaborate with investigators across the two platforms and share observations. Customers can further leverage these tags and monitor known malicious domains within their Splunk logs.

The Tagging Dashboard above gives a central view of observed domains with tags within your network. It includes tags, Domain Risk Score associated with the tagged domains, an event timeline associated with the observed domains, and operational metrics around tagged events.
We have also introduced initial capabilities around tag management within Splunk. For any benign domains, you will have an ability to suppress the tags in the Tag Dashboard. On the contrary, if you chose to add a malicious domain to the Critical Monitoring list, the application will automatically monitor events and report matches for the monitored domain.
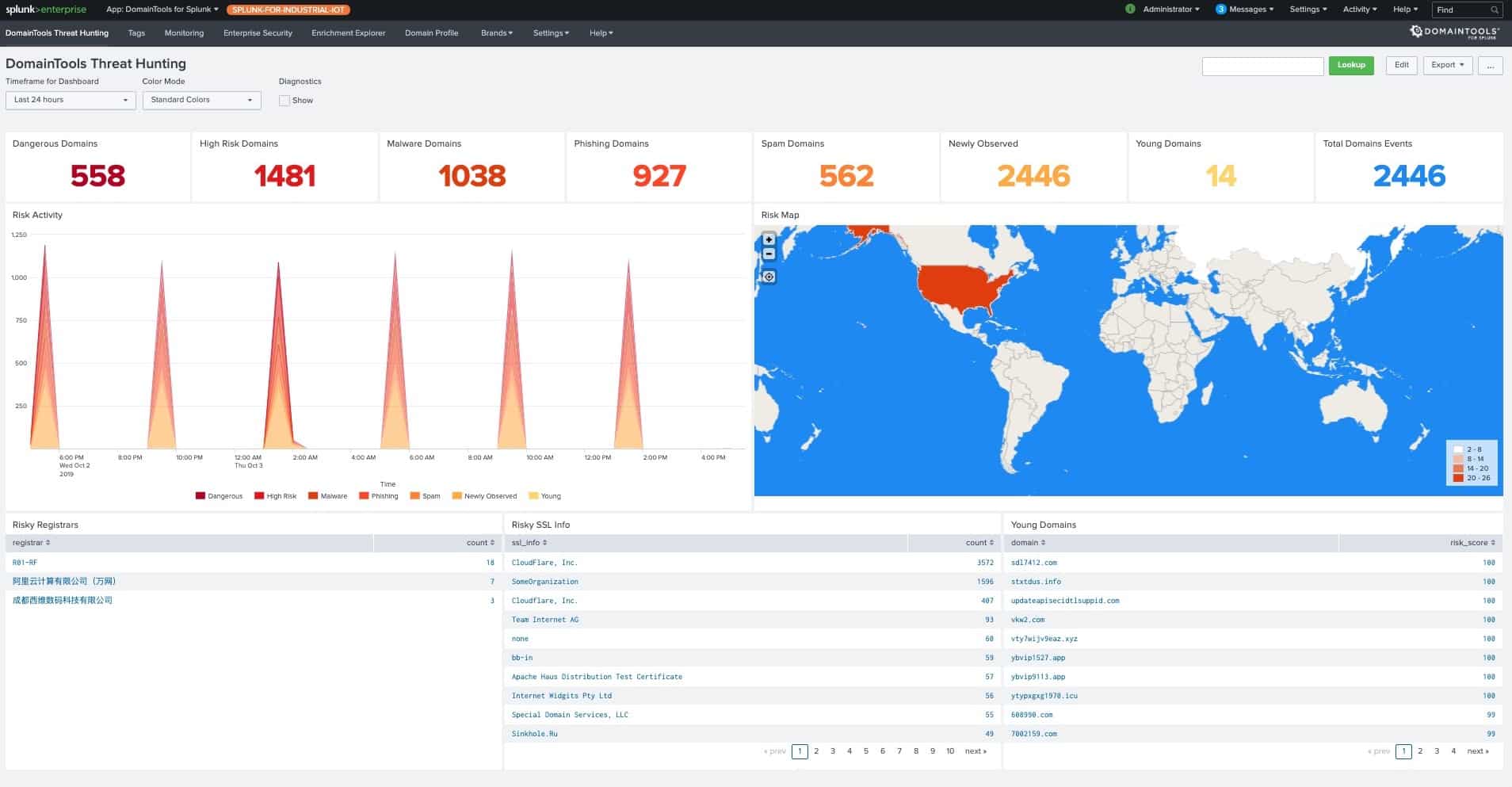
Centralized Monitoring
This new feature enables continuous monitoring of DomainTools intelligence and provides contextualized risk-prioritized alerts within Splunk. For Splunk Enterprise Security users, it raises Notable Events on risky domains with integration into Splunk’s Adaptive Response framework.
DomainTools customers can leverage their monitored terms from PhishEye, including newly registered domains inside of Splunk. This allows SOCs/CSIRTs to consume domain monitoring intelligence (such as newly discovered domains) in conjunction with investigative intelligence for quicker triaging inside of Splunk.
Automatically triaging DomainTools intelligence with internal and external sources available in Splunk, and persisting the enrichment data inside of Splunk repositories also dramatically reduces the time spent on security incident investigation and remediation.
Notable Events in Splunk ES
Splunk’s Enterprise Security is one of the most widely used SIEM products on the market today. Many of our customers utilize the application’s Incident Review functionality. To facilitate automation of workflows, customers can now look up events that triggered a notable event against IOCs, in a single pane of glass, within Splunk Enterprise Security.

We have also pre-packaged a comprehensive list of Correlation Searches for convenience. Once enabled by the click of a button, they can automate additional use cases around asset and risk management.

And Some More…
Additional features like the Enrichment Explorer, with the ability to refresh past IOCs and search query optimizations, have also been added.
These comprehensive functionalities and DomainTools datasets are made available inside of Splunk with the Iris Enrich API and PhishEye API.
Available for Download Now
The latest DomainTools App for Splunk is hosted on Splunkbase. We have also included detailed documentation on how to install the application into your Splunk environment.

Once installed, you will need two things handy: your DomainTools API username and key. If you’re already a DomainTools Enterprise API customer, please download the application and give it a try. Or, if you’re still considering how best to integrate DomainTools into your investigative processes, contact us and we’ll set you up with a free API account to try out the application.
I hope to receive your feedback and continued interests in additional features (email me your requests – [email protected]).