Introducing Iris Investigate With Collaboration Features
While some infosec analysts or investigators work on their own, many work as part of a team. This collaboration could be on specific investigations or as part of a larger charter within the group or organization. Recognizing this, we are delighted to introduce a suite of features in DomainTools Iris Investigate to make it easier for teams to, well, team up! Specifically, we have added shared investigations, investigation notes, and exportable reports. Let’s look at each in turn.
Shared Investigations
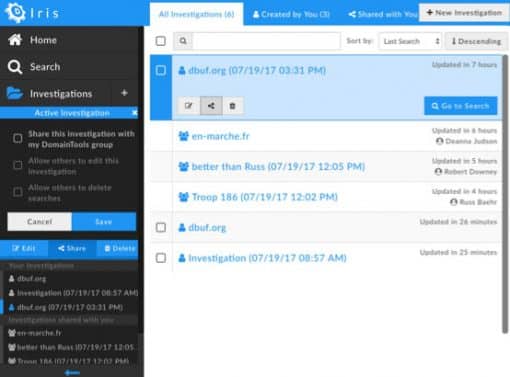
When users in your organization are part of a DomainTools group, you now have the ability to share investigations with the group, or to receive investigations that others have shared. Unlike the earlier hash export/import feature, a shared investigation can be viewed and contributed to by multiple people, in real time. Consider the following use cases:
- A team of analysts can leverage particular strengths or experience of various members of the group. Perhaps Alice has deep expertise in looking at infrastructure from the DNS standpoint, while Bob knows all about domain name patterns associated with a particular botnet family. By sharing an investigation, each of them can add pivots, filters, etc, to advance the investigation. And, if they use the notes feature (described below) they can communicate and even have a dialog about the findings of any given query.
- Experienced members of the group can share an investigation as a means of training newer members. Bring your junior team members up to speed on Iris Investigate and on how the different data types deliver particular insights about threat actors, campaigns, and infrastructure. Here again, the combination of sharing and notes is particularly potent.
It’s important to be aware that you must be part of a group in order to share, and sharing is with the entire group—you can’t pick out specific members with whom to share. You can share or unshare the investigation at any time by editing the sharing settings, which also give you some control over whether others in the group can add or delete searches within the investigation (the most basic share level is read-only).
Since collaboration happens in real time, if you share an investigation with others and give them read+write privileges, you can see their searches appearing as new nodes in the search history trail in near-real-time. If your browser permits pop-up notifications, you also will see those when your fellow collaborators add to investigations.
Investigation Notes
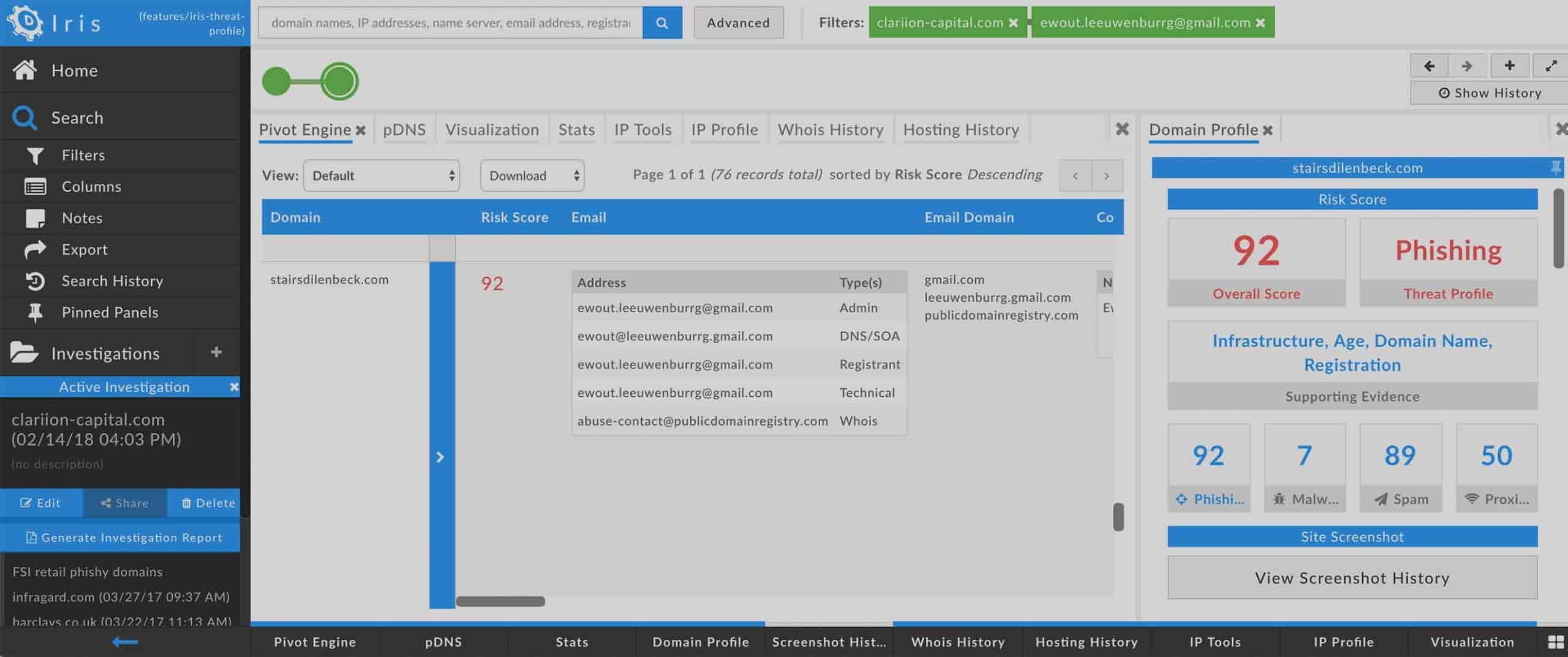
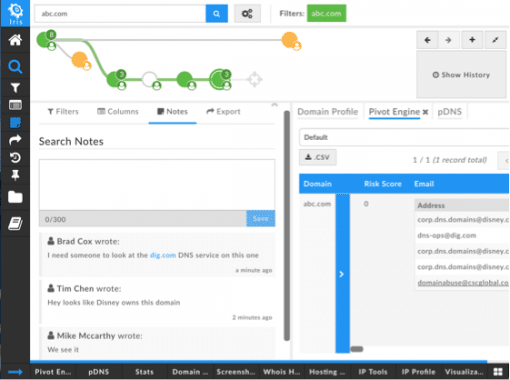
Did you ever look back at an investigation you had run sometime previously, and recall every single detail about why you made each pivot? Yeah, we didn’t either. So Iris Investigate now includes a Notes feature in Search History, allowing you to create a note for yourself—or your colleagues—on any search. And it’s not just one—you can leave multiple notes, or multiple collaborators can create a dialog in the notes. Any way you use it, the Notes feature will help you retain a good sense of context for each pivot. But it’s not just static text—when your notes include domain names, IPs, email addresses, etc., you can pivot on them, right from the Note, if you wish.
Exportable Investigation Reports
Sometimes you collaborate, report to, or have some other professional dealings with, people outside your immediate group or functional area. In the coming weeks, we will be releasing a PDF-format investigation report for Iris Investigate. This way you can share the fruits of your labor with whomever you need to. The reports include several key sections:
- Summary: We provide a space where you can write a summary or introduction to the report.
- Investigation Path: A tabular representation of Search History, indicating what actions led to each set of results (expand, narrow, etc). If you added Notes to any node of Search History, the notes are included in the report.
- Pivot Engine: The data from the Pivot Engine is given in tabular format. The columns in this section of the Report correspond to the columns you see in your Pivot Engine view.
- Visualization: The Visualization graph is also part of the report, though it’s worth bearing in mind that for large search results, the visualization graph may not be practical to read on a printed page. You can use the .svg export, directly from Visualization, to get a scalable image of Visualization.
- Stats: The contents of the Stats data panel are listed by section.
And, since no two investigations, or teams, are alike, the Reports control allows you to customize which information is included in the report. After all, you know your audience better than anyone else does.
Whether or not the hackneyed phrase “Teamwork makes the dream work” echoes off the halls of your organization, we hope you’ll agree that being able to collaborate on threat investigations is helpful. We certainly have talked to a lot of analysts and threat hunters who expressed the desire to be able to bounce ideas off their colleagues, send a report up the chain of command, or just jot down a note for later reference.
If you’re planning to be at the Black Hat conference, stop by booth 160 to see these and all the other Iris Investigate features for yourself!
Happy exploring.