Iris Investigations At-A-Glance: How to Pivot on Domain Data for Agile and Intelligent Threat Response

Last year, Japanese authorities reported a sophisticated and aggressive phishing campaign using websites spoofing Sagawa Express Co., a major shipping and logistics company in Asia. Hundreds of users were directed to fake websites and prompted to either enter personal data or install an app (malware) that would harvest their IDs, passwords and credit card information. Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) took action and worked with government authorities to shut the sites down.
The incident provides a prime case study for how integral domain and DNS data are to investigating threats and malicious activity. The Iris Investigate Platform is built upon this essential threat information, designed to power investigations through domain ownership, DNS observables, SSL Profiles, and other data in an intuitive and comprehensive interface.
Below is an example of what the threat hunting workflow looks like in Iris Investigate, using data from the Sagawa Express incident. It demonstrates how security teams can leverage different datasets brought together within Iris to identify, remediate and block suspicious and dangerous domains and IP addresses and additional correlated malicious infrastructure and domain activity.
In Iris Investigate, we can begin an investigation with a range of data points, such as a domain, IP address, email address, SSL certificate or Google Analytics code. In this example, we started with the lookalike domain, sagawa-app[.]com, one of the websites used in the Sagawa Express spoofing campaign. The Iris Investigate Pivot Engine interface provided a tabulated view of the most recent data relating to this website. This showed us ownership information, registrar and create date data, hosting infrastructure data, analytics codes, ad sense trackers, mail server information, redirects and SSL certificates.
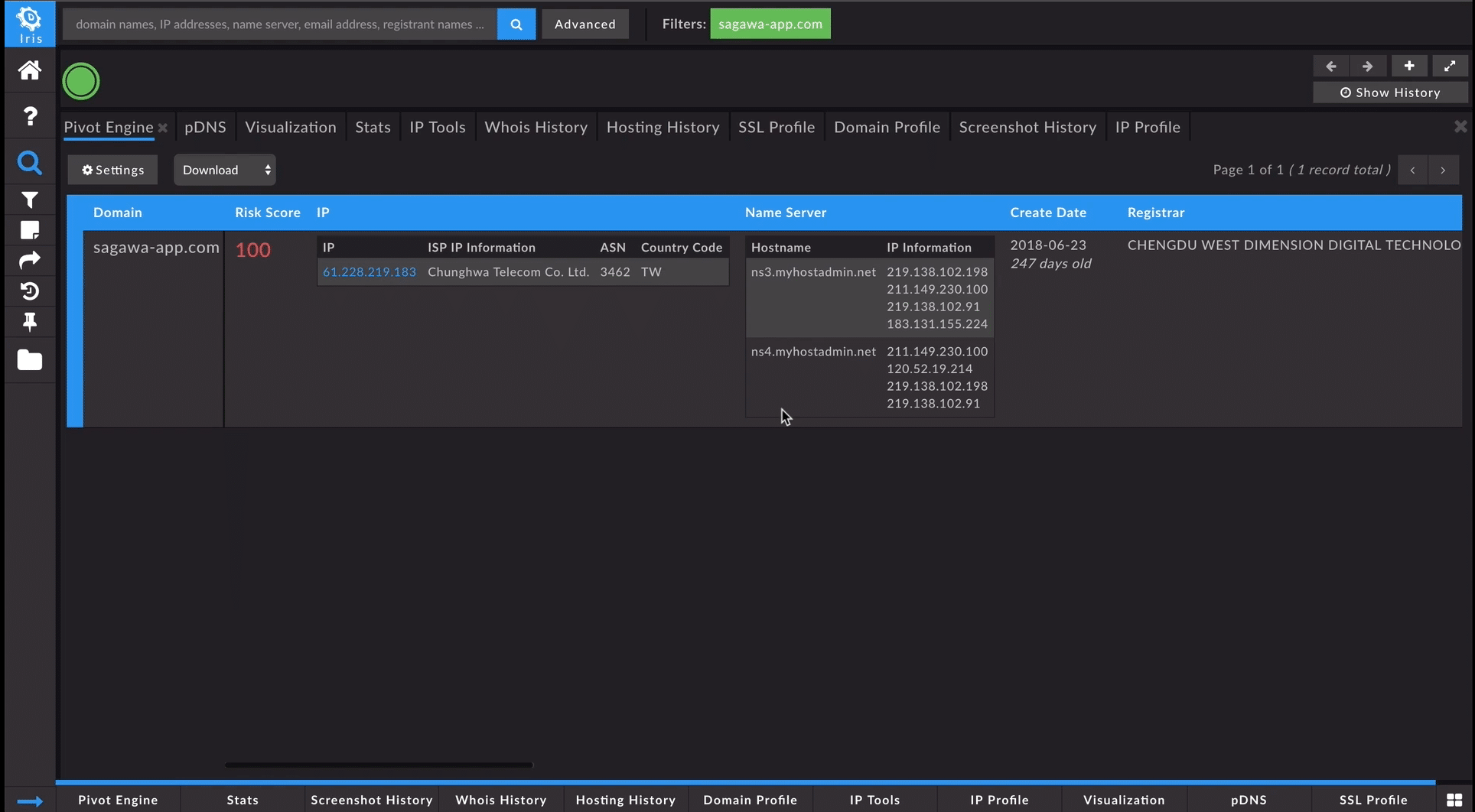
While the current contact information for sagawa-app[.]com was redacted, the Whois tab in Iris Investigate allowed us to look back in time at the historical records from when the domain was initially registered. This view showed the name, address, phone number and a yahoo.co.jp email address associated with the domain. We pivoted on that information directly in the interface to find other domains associated with that registrant information.
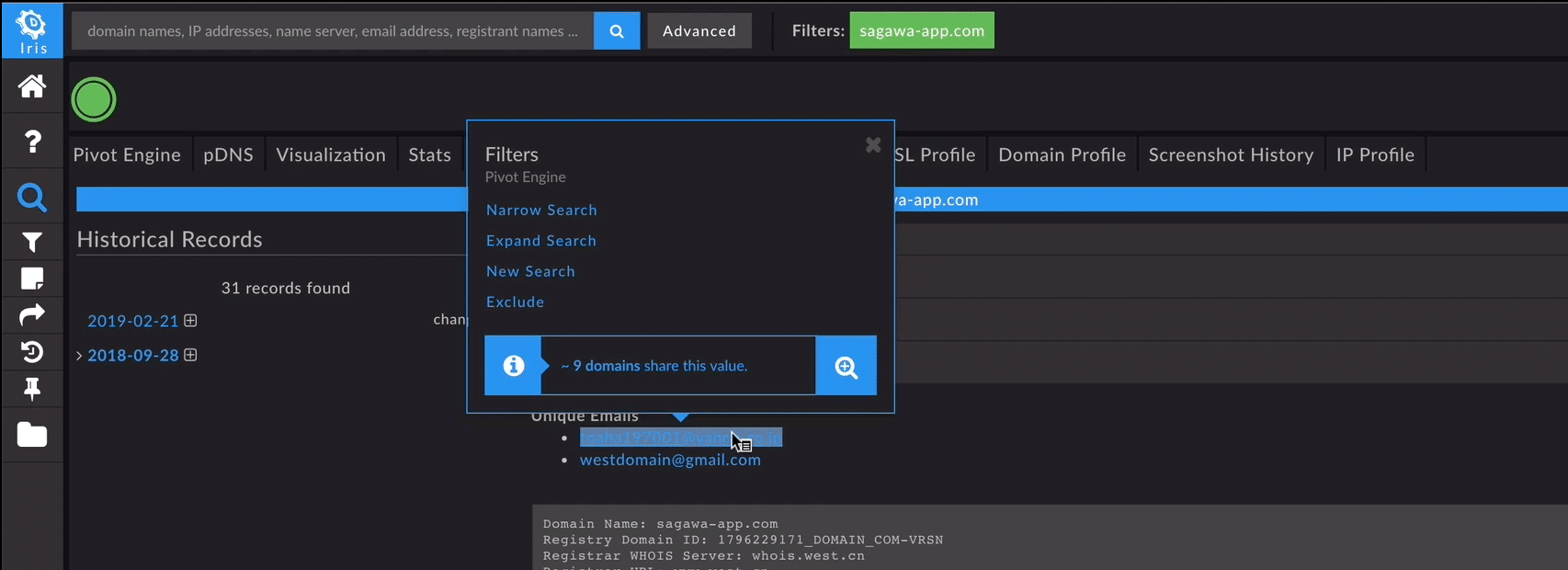
We then took a closer look at each of the associated domains to determine if they were relevant, before bringing them over to the Pivot Engine. In this case, Iris Investigate presented us with 65 associated malicious domains targeting Sagawa Express, as well as Yahoo Japan, Soft Bank, NTT Docomo, Rakuten and more. A simple expand selection sent the data into the Pivot Engine to enable a deeper dive into the threat actors’ activity.
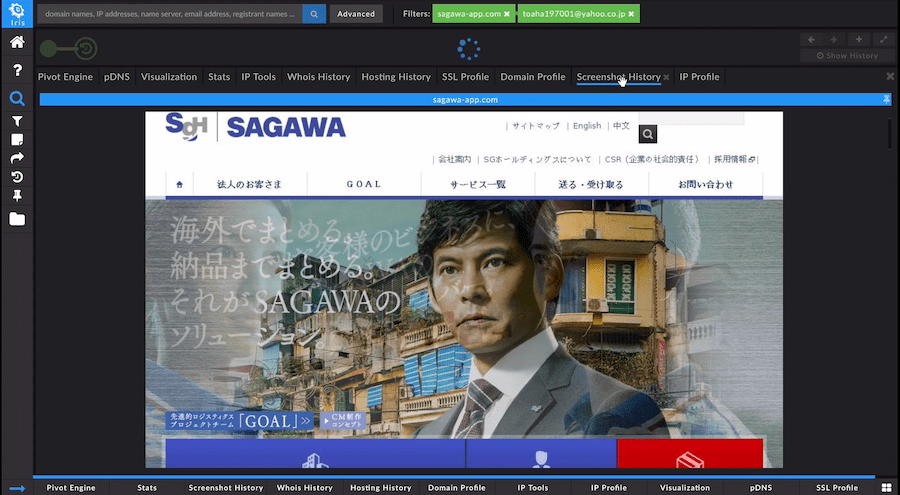
Another feature that supported this investigation is the platform’s Screenshot History tab, which displays historical screenshots of domains under investigation. A historical glance at the sagawa-app[.]com site showed a well-crafted lookalike using both the logo and website layout of the actual company. It also showed that the site included a step-by-step guide for visitors to overwrite the security settings on their Android device and then download a malicious application from a dropper domain, sagawa.oicp[.]io.
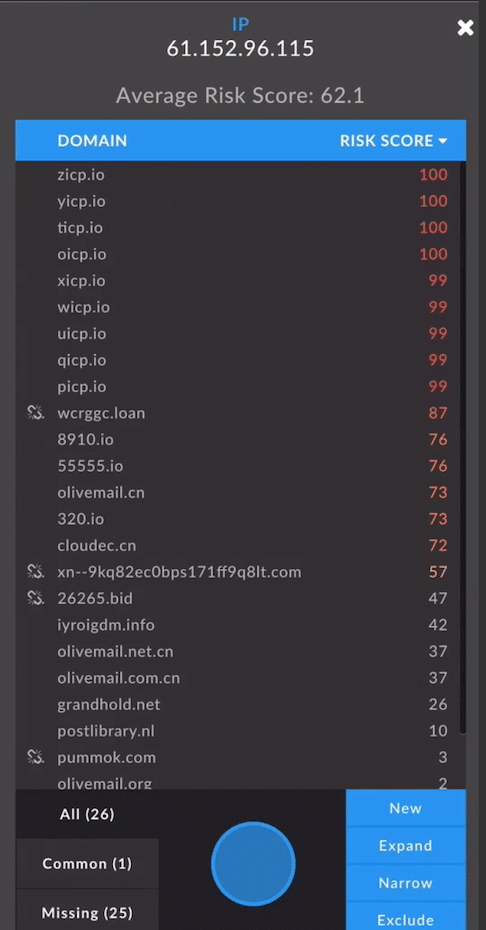
The Advanced Search interface within Iris Investigate allows investigators to add up to 1,000 domains at a time to an investigation, or craft a more sophisticated query based off of Pivot Engine datasets including create dates, Risk Score and more. Using this feature, we added sagawa.oicp[.]io into the Pivot Engine for a closer look. Guided Pivots highlighted potential pivot points that were likely to be useful and related to the investigation of the dropper domain. For sagawa.oicp[.]io, we found that the hosting IP address was highlighted, and hosted 26 other domains, many of which had similar variances to sagawa.oicp[.]io. Four of these had a Risk Score of 100, which indicated they had been observed on lists of known-malicious domains. A number of others had a Risk Score of 99, which meant that while they hadn’t made it to traditional intelligence feeds just yet, the predictive machine learning classifiers known as Domain Risk Score within Iris categorized them as malware as well as very likely nefarious. We expanded those into the Pivot Engine, so all of the data could be exported together to further the investigation (in a real-time scenario, these insights could also help inform and guide blocking decisions).
Passive DNS data within Iris Investigate provided a clear look at the dropper domain’s event timeline, and its activity in the wild. This information was examined to draw connections to additional malicious IP addresses, sub-domains, SOA records, text records and more, making it easier to zero in on adversary infrastructure.
The same investigation outlined above is just one example of the many ways in which domain and DNS information can make threat hunting and response efforts more intelligent and agile. To watch the complete walkthrough of this investigation in Iris Investigate, check out the video here. If you are interested in an in-depth demo, please get in touch with us!


