Marriott Data Breach: Why News Reports Act as a Wake Up Call for Cybercriminals
NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
In the wake of a significant data breach like the one recently announced by Marriott, the focus of most news stories is on the potential negative impact of the data stolen in the breach. This hyper-specificity may lead you to believe that if your information wasn’t included in the breach, you don’t have to worry. Right?
Unfortunately, that isn’t usually the case. Cybercriminals stay on top of the news cycle just like everyone else, and they capitalize on popular stories in order to make a profit.
One of the many ways criminals will try to profit off of an ongoing news story is by setting up fraudulent domains that appear to be related to the big stories of the day. Once they’re set up, criminals can use these sites to host malware or to phish for user information or credentials.
Let’s take a look at the news regarding the recent Marriott breach to see exactly how this is done.
To start out, criminals will read the news to find out what stories are garnering the most attention. From there, they can pick out specific terms that are most relevant to their malicious campaign. For example, in the first paragraph of this Time Magazine article, criminals can safely assume that the words “Marriott” and “Starwood” are probably going to be important both to the news story and their own nefarious campaign.
From there, criminals will register domains using terms intended to elicit an emotional response that will trick the user into clicking without thinking, such as “security,” “information,” or “settlement.” Using DomainTools PhishEye, we can see that cybercriminals wasted no time after Marriott announced their data breach, with several fraudulent websites being registered on the same day that the announcement was made.

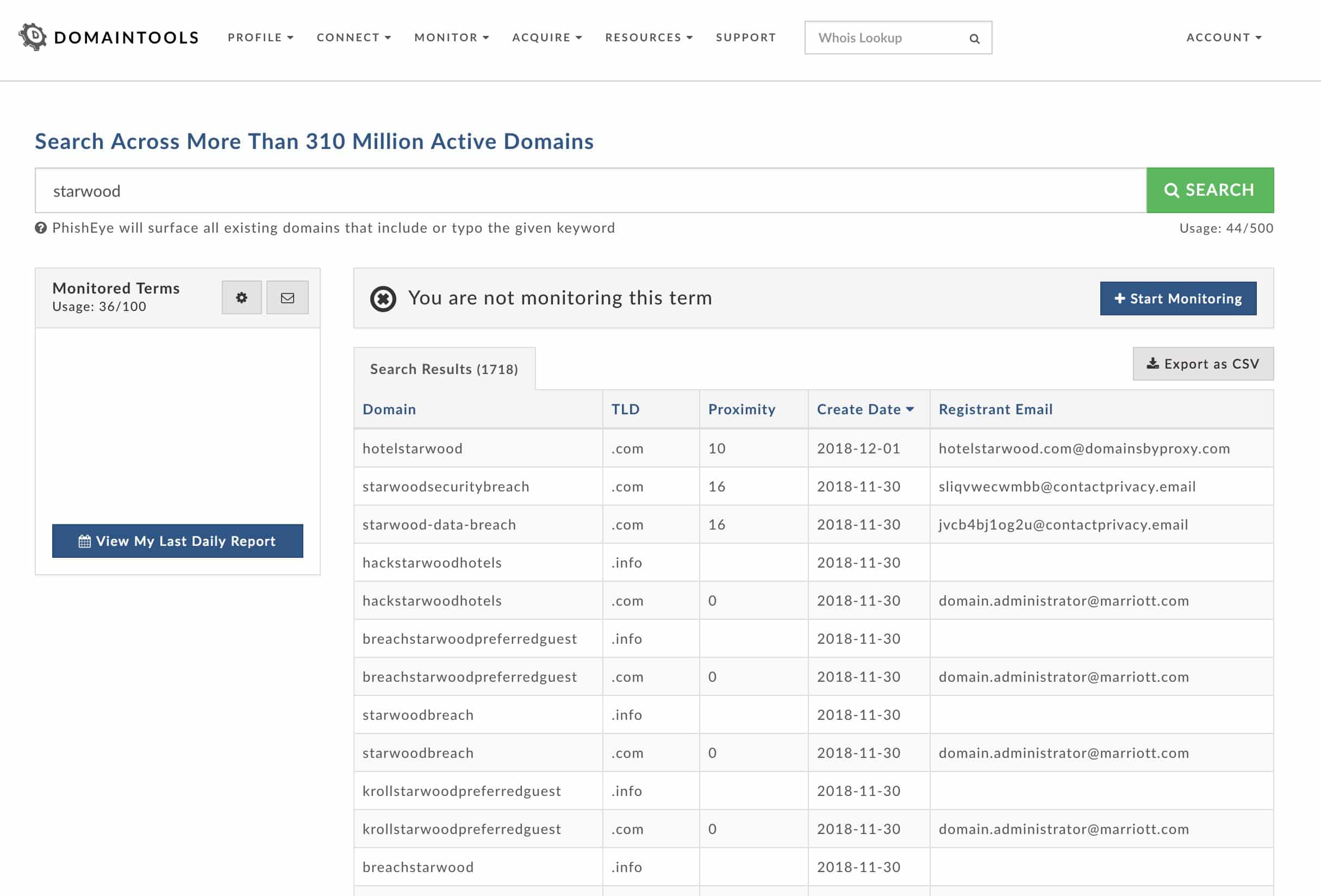
From the registrant email listed for these domains in PhishEye, we can see that only one of the domains registered on November 30th regarding Marriott seems to have been registered by a legitimate Marriott email address. To confirm marriottsecurity[.]com is indeed a legitimate site, we can use DomainTools Iris to gather more information regarding that domain.

If we compare the registration information from that website to that of the known legitimate Marriott site, we can see that they share common registration information, which adds to the probable legitimacy of the site.

Conducting a search in Iris for one of the other recently registered domains, we can see that the registration information has been listed as private, which is not a tactic that Marriott has typically used on their other legitimate sites. Therefore, we can deduce that this site is likely not legitimately associated with Marriott and may be used for phishing or spam campaigns.

Additionally, thanks to the machine learning algorithm used by DomainTools Risk Score, this domain already has a Risk Score of 60, which gives researchers a heads up that this is likely going to be used maliciously.
Once criminals have set up these domains, they can be used in a variety of ways. Criminals may design them to trick the user into entering their PII – “Enter your Social Security number here to see if you were affected by the breach” – or they may be designed to drop malware on the user’s machine. Criminals may send links out to these domains in spam campaigns to thousands of email addresses in hopes of getting a few clicks. In any case, they aren’t legitimate and should be avoided if possible.
These tactics aren’t new and aren’t specific to news pertaining to cybersecurity or data breaches. Criminals will capitalize on any event of interest – hurricanes, elections, wildfires – in order to set up malicious campaigns. Be mindful of emails you receive following big news stories and avoid clicking on unfamiliar links or entering credentials or PII on untrustworthy websites.



