Moving Target Defense and DNS Fast Flux
*Disclaimer: Mike Thompson holds a patent on one moving target defense technology and has a patent pending on a second technology. In his previous position at Argonne National Laboratory, he worked on a variety of dynamic defense strategies including MTDs.
Moving Target Defense has become a buzzword in cybersecurity circles because of its promise to function as a proactive solution for zero day vulnerabilities. A zero day is a vulnerability that is being actively exploited for some time before “day one” of the public’s knowledge of the vulnerability, which makes it impossible for security professionals to defend against it. These types of vulnerabilities are currently the hardest to defend against, because the require that we are able to successfully detect anomalous behavior on our networks. This is a significant challenge, and one that many vendors attempt to solve, however, even properly baselining most networks presents a challenge. Moving target defenses (MTDs are a family of defense strategies that center around altering system, network, configuration, or code properties dynamically either in reaction to or in anticipation of malicious activity. MTDs demonstrate that the right combination of system diversity and increasing attacker uncertainty could make zero day vulnerabilities a less potent threat. Figure 1 shows an example of an operating system hopping moving target defense system.

Example of an OS hopping MTD system (courtesy of Argonne National Laboratory)
Moving target strategies have been researched fairly extensively, but these strategies rarely make it into cyber defenders’ toolkits. However, they have been leveraged by malicious actors for some time in the form of DNS fast flux. Fast flux was first observed in the wild in 2006 and has been widely associated with the Storm Worm malware variants. It can be used by botnets to hide various types of malicious activities–including phishing, web proxying, malware delivery, and malware communication. This technique allows the botnet to “hide” behind an ever-changing network of compromised hosts, ultimately acting as proxies and making detection incredibly difficult. The goal of fast flux is for a domain name to have hundreds or even thousands of IP addresses associated with it. IP addresses are swapped in and out of flux with extreme frequency, using a combination of round-robin IP addresses and a very short Time-To-Live (TTL) for any given particular DNS Resource Record (RR). Website hostnames may be associated with a new set of IP addresses as often as every 3 minutes. Figure 2 shows a simplified example of what a DNS fast flux infrastructure might look like.
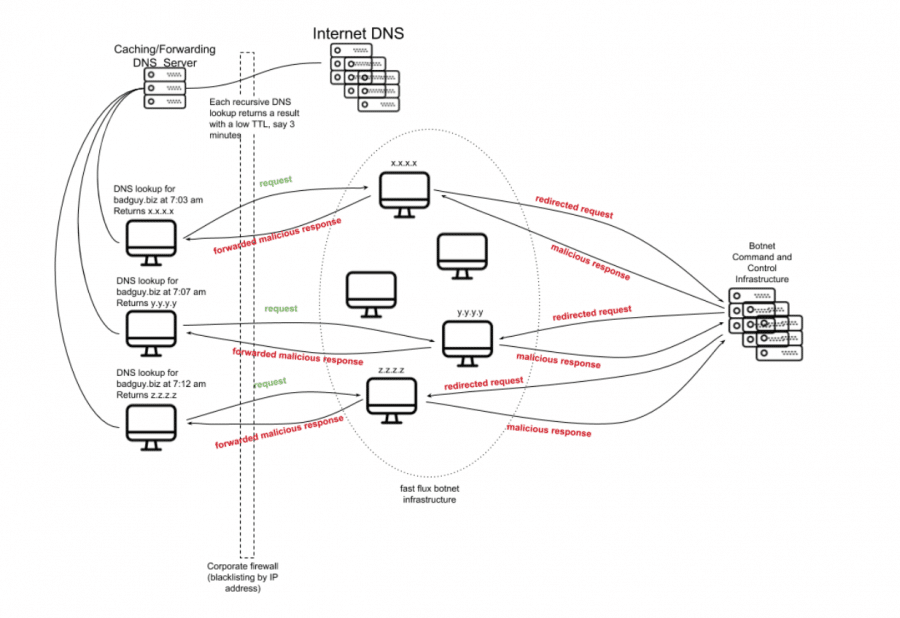
Fast flux techniques have been extremely effective at thwarting investigations and obfuscating command and control infrastructure. The combination of randomly generated DNS names and a large pool of IP addresses (usually associated with so-called bulletproof providers) make it difficult for investigators to identify patterns in communications or techniques. Successful takedowns of command and control infrastructure utilizing fast flux techniques have happened, but these are labor intensive and often take years to yield actionable intelligence.
Information security tends to be asymmetric between attackers and defenders. Defenders are in a position where they need to offer a service or application to a set of customers or stakeholders. Attackers often have virtually unlimited time to probe these services or applications for vulnerabilities and weaknesses. Additionally, attackers don’t generally need to maintain persistence in their own infrastructure (although they are often trying to do so on their victims’). This asymmetric property exhibits itself in the moving target strategy domain as well and helps explain why it’s been so difficult for defenders to utilize strategies that have worked so well for attackers.
The asymmetries don’t end there. Because attackers often have access to a nearly unlimited source of nodes (through botnets of infected machines), they can scale and/or lose machines without much damage to their operations. Moving target strategies for defenders often require a significant investment in infrastructure. Cloud technologies offer dynamic deployments which can offer similarities in the vein of what fast flux offers attackers, however, attackers don’t need to defend the platforms of their “intermediaries”—they are often protected by legal preventions against hacking victim machines, but those victim machines also often contain little to no information about the command and control infrastructure which may itself be disguised behind obfuscated DNS or side channels like IRC.
Measuring the effectiveness of moving target technologies is still evolving, as the number of implemented solutions is still small. However, many researchers agree on a simplified subset of measurable characteristics to quantify the value of a moving target solution: diversity (the different possible configuration states that the MTD solution can assume), agility (the speed at which a system can respond to attack, as well as the speed with which it can execute configuration adaptations), effectiveness (the degree with which the MTD solution can mitigate or prevent attacks), and performance (the impacts and ability for the MTD system to execute its required tasks, i.e. – serving a web page application or providing access to a database).
Moving target strategies for defenders that rely on rotation of resources or respawning of machines rarely use cloud infrastructure (due to the complexity involved and the lack of maturity in MTDs) and even those that are similar to fast flux infrastructures usually suffer from all the same dangers as static infrastructure when faced with the danger of zero day vulnerabilities. Even MTDs that defend against low level exploits may not offer reasonable protections against application layer vulnerabilities. Content delivery networks (CDNs) offer many of the infrastructure resilience benefits of a fast flux infrastructure. CDNs are often used as a mitigation for distributed denial of service (DDoS) attacks. CDNs, however, do not offer compelling defenses against zero day vulnerabilities in applications. It is in CDN’s advantage to have homogenous environments. In other words, if one system is vulnerable to a zero day, all of them will be equally vulnerable. The use of a CDN may offer a buffer or an extra layer of diversity to a targeted infrastructure, but a zero day vulnerability in either the CDN provider’s software stack or the targeted infrastructure owner’s software stack still offers a very low level of complexity for a sophisticated attacker (compared to the level of complexity in an attacker’s infrastructure). Therefore, a CDN may be very agile, but it offers very little diversity, whereas a fast flux infrastructure is both agile and diverse.
Fast flux infrastructures have much to teach us about proactively defending information resources. Though attackers goals and resources are quite different than defenders, there are enough similarities that they highlight one area where dynamic system designers need to devote their efforts—diversity and agility are critical throughout the full stack for MTD to be successful. In the meantime, gathering information about attacks and sharing that information is critical. Logging and monitoring are critical first steps to baselining networks and detecting malicious activities. Good security hygiene and user education are essential parts of a healthy information security regime—if users don’t click on malicious links, many of the attack vectors that are most prevalent today disappear. Creating IP blocklists is a necessary part of a security toolkit, but it clearly has its limitations. DNS is part of the core infrastructure of the internet and it can be difficult to filter properly, but DomainTools offers some of the best tools to investigate how DNS affects your organization and how DNS changes evolve.
Resources:
https://dl.acm.org/citation.cfm?id=2602088
https://fas.org/irp/eprint/proactive.pdf
http://www.dtic.mil/dtic/tr/fulltext/u2/a591804.pdf
http://ieeexplore.ieee.org/document/6900086/
https://coar.risc.anl.gov/research/moving-target-defense/
https://www.akamai.com/us/en/about/news/press/2017-press/fast-flux-botnets-still-wreaking-havoc-on-internet-according-to-akamai-research.jsp
http://www.honeynet.org/node/132
https://www.welivesecurity.com/2017/01/12/fast-flux-networks-work/
https://www.afcea.org/content/asymmetric-cyberwarfare-demands-new-information-assurance-approach
https://www.asymmetricthreat.net/pdf/symposium8_report.pdf
https://arxiv.org/pdf/1603.08312.pdf
http://www.few.vu.nl/~herbertb/papers/feederbot_ec2nd11.pdf
https://arxiv.org/pdf/1408.1136.pdf
http://scitlabs.com/products-solutions/technology
https://coar.risc.anl.gov/research/moving-target-defense/
http://www.springer.com/cda/content/document/cda_downloaddocument/9781461432951-c1.pdf?SGWID=0-0-45-1445116-p174291477




