New Phone, Who Dat?

Early mornings can be a fantastic and peaceful time of day. The sights of a glorious blue sky outside the bedroom window. The invigorating smells of freshly ground coffee permeating throughout the house. The blissful sound of silence (until the kids wake up). Have you experienced this recently? Was your perfect morning bubble of happiness popped by the jarring sound of a Slack message: “Hey! Sorry to bother you, but I may have clicked on a link in a text I got and I may have entered in some information and I’m not sure what to do next…”
If so, read on.
What is SMS Spam/Phishing?
SMS Spam and SMS Phishing (a.k.a Smishing as some would say… sounds like some sort of drunken wedding dance), is a common occurrence these days. The concept is similar to email spam and phishing, but does have its own nuances given the devices on the receiving end.
- An unsolicited text message is received by a recipient sent from an unrecognized phone number.
- The message consists of enticing wording with the intent of encouraging the recipient to click and open a URL. There are numerous examples of these messages in the wild reflecting recognizable brands such as FedEx, UPS, etc. In fact, UPS even has a page on it’s website with examples to better inform its customers to be vigilant against this type of activity.
- Typically, the URL in the message will be using one of numerous URL shortening services available.
While wireless phone carriers could probably do more to better protect their customers, finding out more context about what is really going on may be beneficial for organizations who wish to have visibility into the tactics illicit actors are using in conjunction with such activities. Additionally, tracking what groups or individuals who are targeted within an organization could paint an interesting picture when business risk concerns are taken into account.
Where Do SMS Spam Phone Numbers Come From?
The originating phone numbers typically used in SMS spam and phishing activities are usually sent from temporary phone numbers that aren’t active for long. There are numerous services that provide these numbers which are typically only a browser search away.
Another concern in the mix is the use of URL shortening services, which are notorious for being leveraged by illicit actors for numerous purposes including directing end-users to malicious websites. In fact, examples of illicit actors exhibiting uses of URL shortening as part of their tactics may be found when perusing through forums, paste sites, and other sources such as Twitter and Telegram.
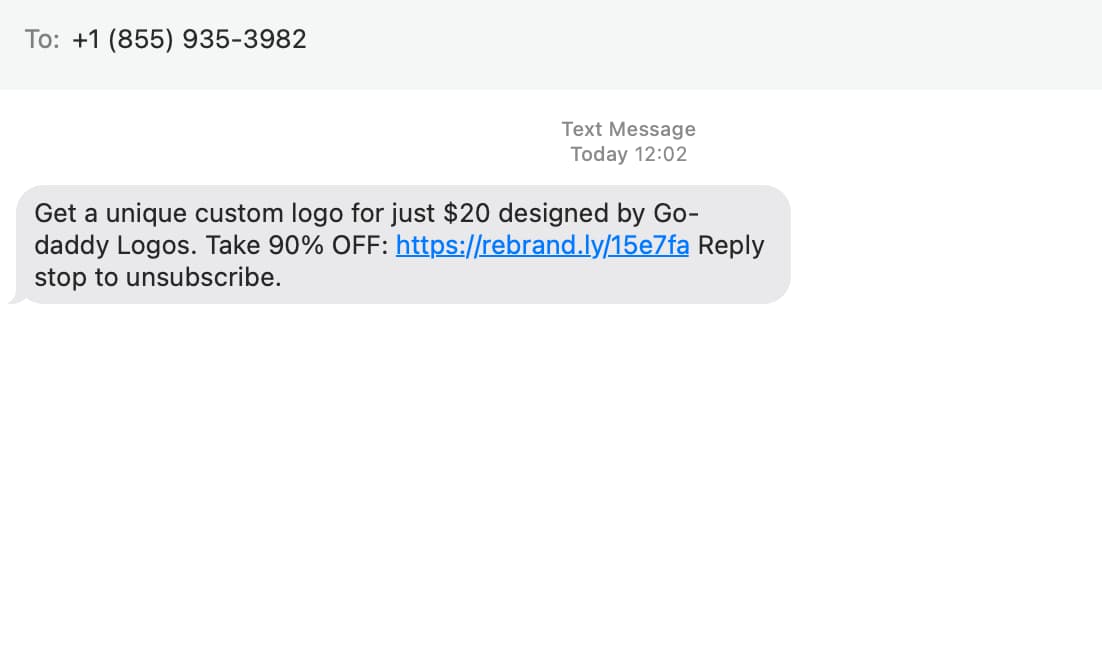
How SMS Spam Works
Let’s walk through a brief example and explore what may be learned from the phone number of a recent unsolicited SMS text.
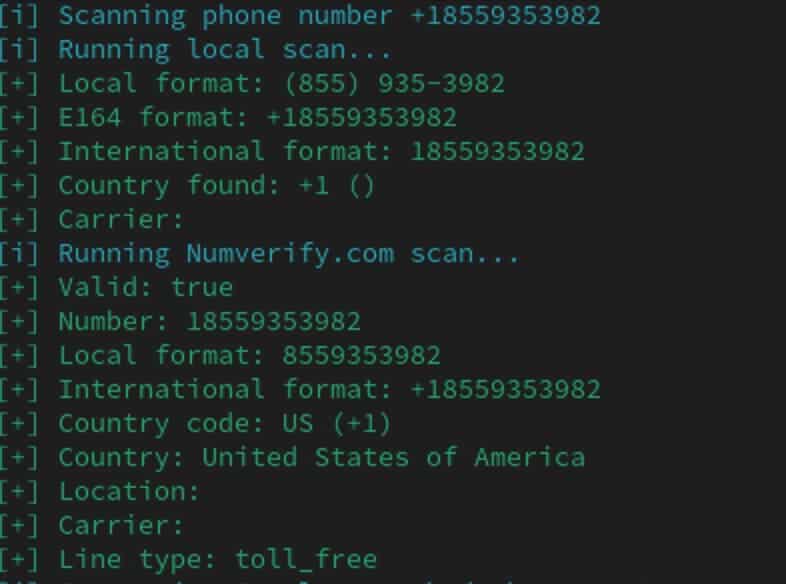
By running the phone number against a few sources and OSINT tools such as Phoneinfoga, we learn that the originating phone number, while apparently valid, doesn’t show up in any type of footprinting searches across social media platforms (Facebook, twitter, LinkedIn, Instagram, etc), nor does it show up in searches related to reputation or temporary number providers. Keep in mind, this could always change as these searches are a point in time and not a complete timeline unless you happen to have historical data stored somewhere to wash the phone numbers up against.
How Shortened URLS Work
Next, we can move onto the shortened URL.
By following the redirect from the shortened URL to the redirected domain, we can see that DomainTools has already performed analysis against the domain and has assigned it a risk score associated with Phishing activities.
Notice that there are numerous areas of opportunity where change could be made to further keep the momentum of the campaign going in order to perpetuate the goals of the actor behind the activity.
The actor could very quickly change the originating phone number, or change the URL shortening service without even making modifications to the final intended website’s underlying infrastructure while still having the option of moving go-daddylogos[.]com to a different hosting IP when necessary.
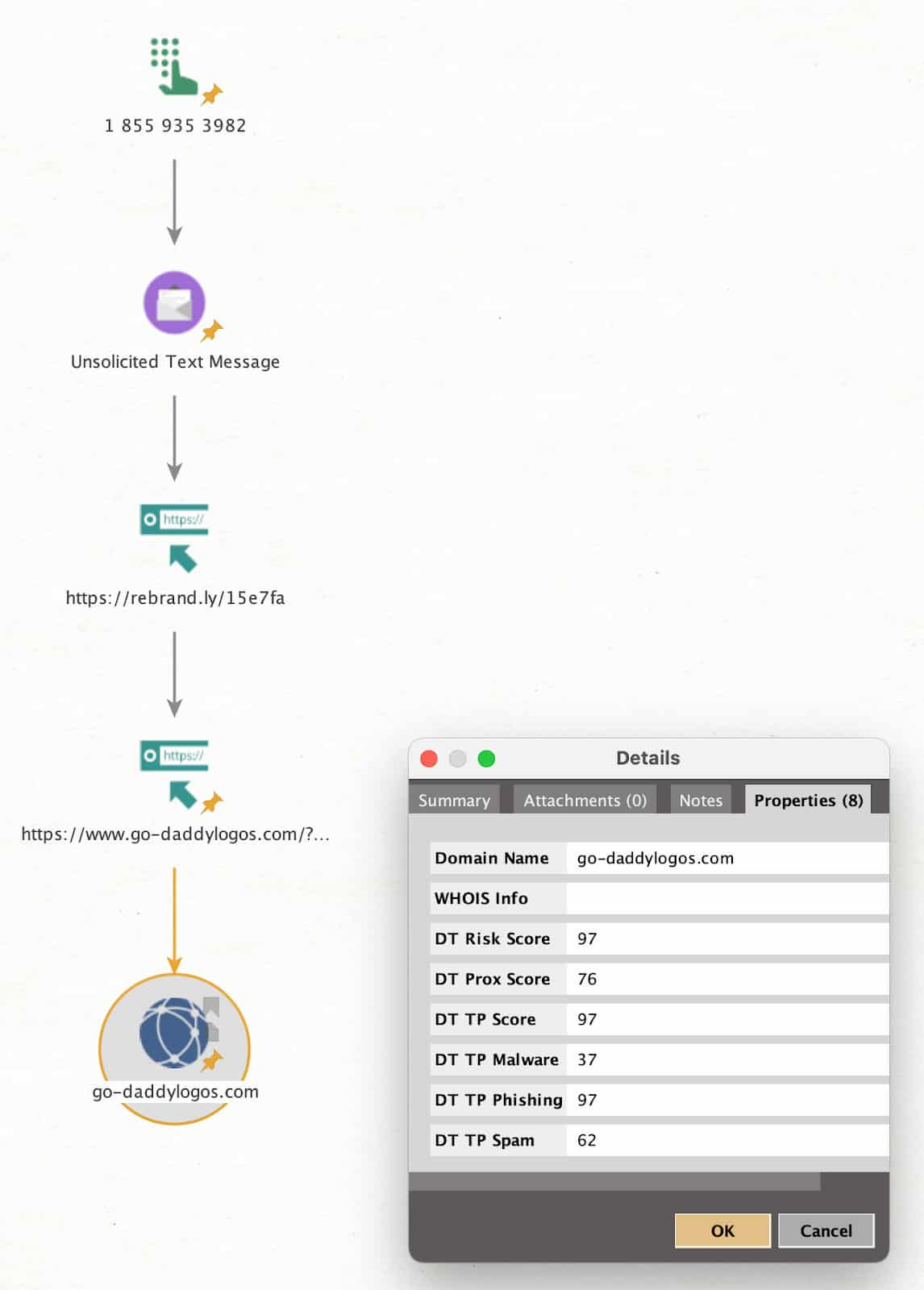
As we pivot from go-daddylogos[.]com to the hosting IP address, we find a few other domains being hosted that also have high risk scores. We’re also able to view this exact context within DomainTools Iris Investigate.
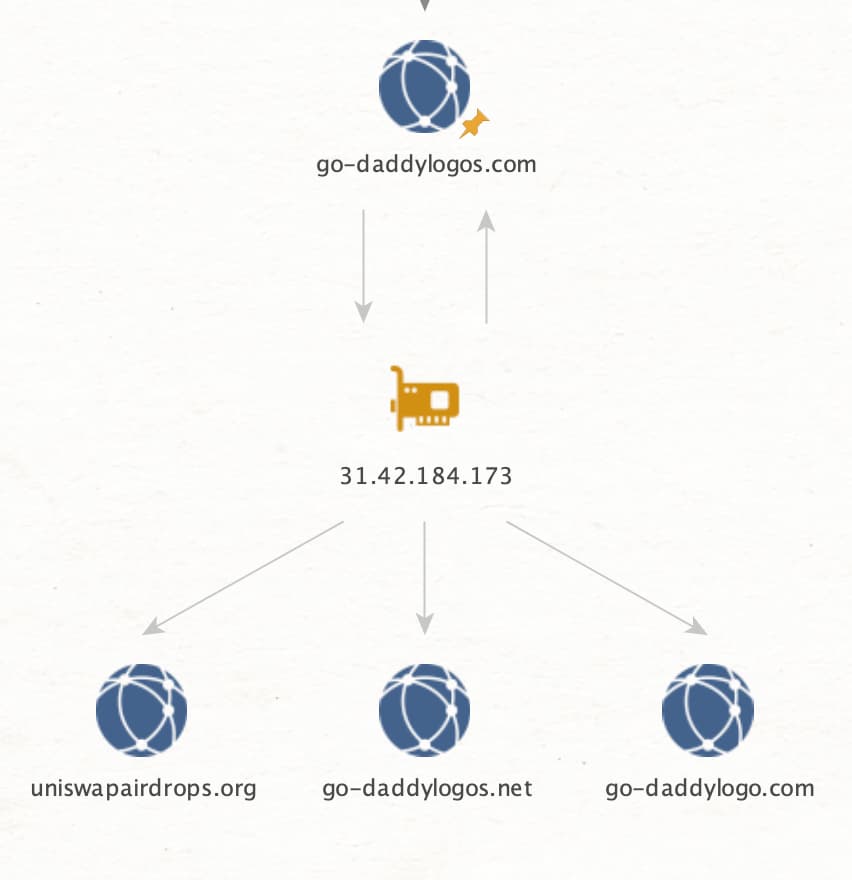
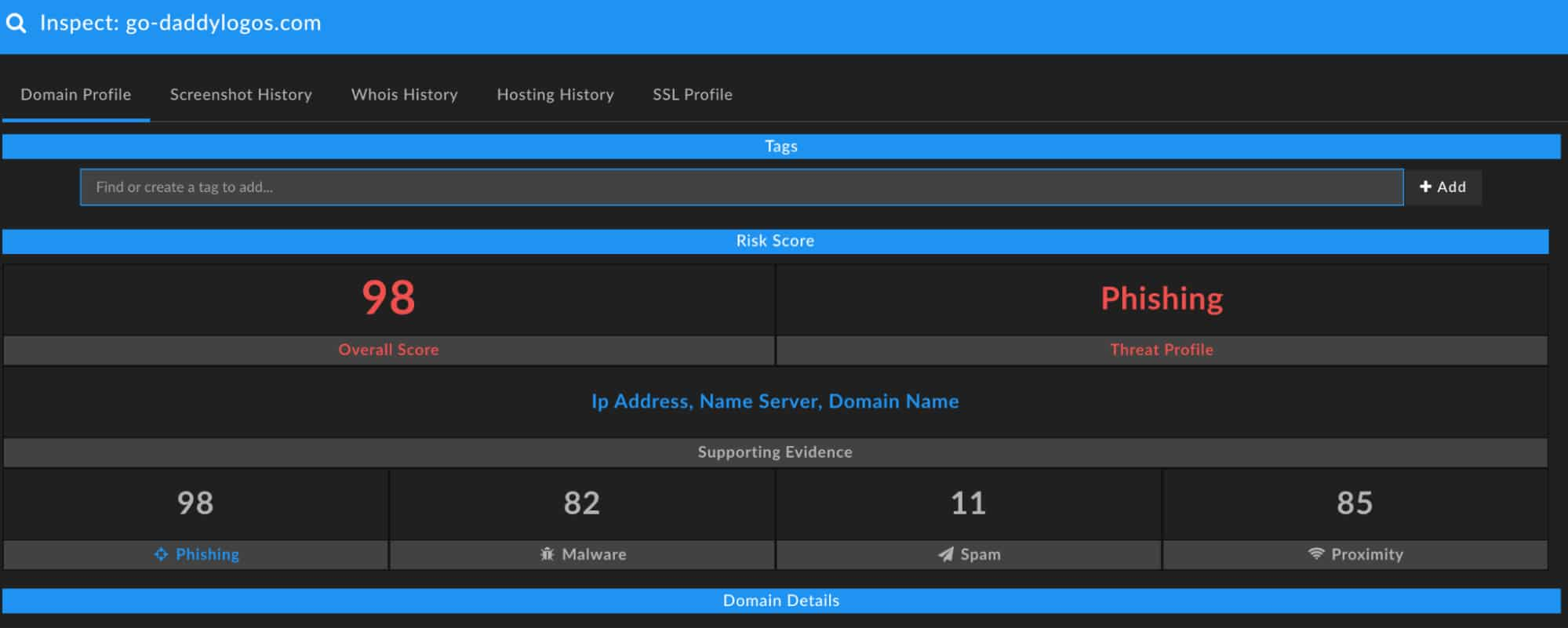
DomainTools determined that the threat profile of go-daddylogos[.]com is phishing. With DomainTools performing some of the analytical lift by providing context and risk scores, analysts leveraging DomainTools as one of their external data sources are able to make better-informed decisions and take appropriate action against illicit activity.
Much has already been written about DomainTools predictive scoring efforts. For those who wish to learn more about DomainTools Risk Score, visit our website.
Considering SMS spam and phishing can likely be threatening activity that can harm an organization’s business, stakeholders, employees, and customers, does your organization really even want this type of activity traversing infrastructure?
Blocking URL shortening services may be something to discuss within your organization.
Finally, there are also resources to report the unsolicited text messages. Visit the FCC and let them know about the event. https://reportfraud.ftc[.]gov/


