Post-GDPR Security Investigations Part 1

Part I – Conducting Investigations
In May 2018, the General Data Protection Regulation (GDPR) went into effect and subsequently altered the way that cybersecurity analysts are able to perform their investigations. Where, previously, connections between incidents and attribution had often been tied to publicly available Whois data, there was now the word REDACTED hindering those linkages.
However, not all was lost with the implementation of GDPR and there are still numerous methods by which to conduct an incident investigation. In this report, we will identify four methods by which threat researchers can perform analysis using techniques that were not impacted by GDPR regulation, including Risk Score within DomainTools Iris platform, non-registrant based connections and attributions, OSINT-based methodologies, and information sharing.
As a result, over the next three weeks I will be publishing a three part blog series to illustrate how to use these and other methods of investigations, analysts can still produce timely and relevant intelligence to defend their organizations, despite the roadblocks posed by GDPR. In today’s blog, I’ll focus on conducting an investigations leveraging DomainTools Risk Score.
DomainTools Risk Score
When conducting an investigation, it can be useful to determine the severity of an incident before spending a significant amount of time on analysis. Domain Risk Score can help give context and allow analysts to start off with an indication of how much attention they should pay to an indicator.
Drawing upon data points from more than 330 million current domains, Domain Risk Score predicts how likely a domain is to be malicious, often before it is weaponized. The score comes from two distinct algorithms: Proximity and Threat Profile. Proximity evaluates the likelihood a domain may be part of an attack campaign by analyzing how closely connected it is to other known-bad domains. Threat Profile leverages machine learning to model how closely the domain’s intrinsic properties resemble those of others used for spam, phishing, or malware. The strongest signal from either of those algorithms becomes the overall Domain Risk Score.
Domain Risk Score can be useful in identifying which domains warrant further research even in cases where little or no data is available about those domains. For example, during our research we came across a domain that was likely malicious, as it had a Domain Risk Score of 90 (domains that have a risk score of 70 or higher are considered suspect and warrant further research). There were no immediately obvious pivots or direct connections to malicious campaigns at first glance, but such a high Domain Risk Score indicated to us that this domain was worth a closer look.
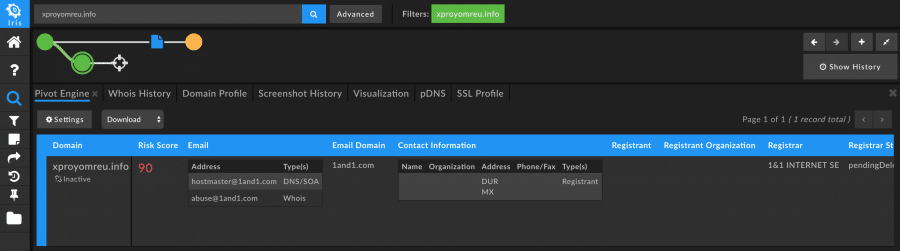
Reviewing the passive DNS records for this domain show an IP address that may be noteworthy.
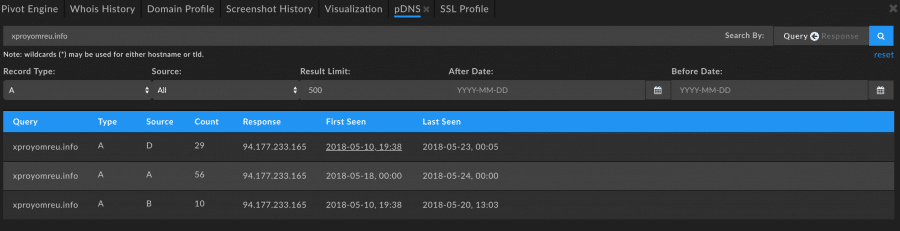
Pivoting on that IP, we can see that it has been associated with several domains, most of which also have high Domain Risk Score, indicating they too are likely malicious and may be a part of a campaign.
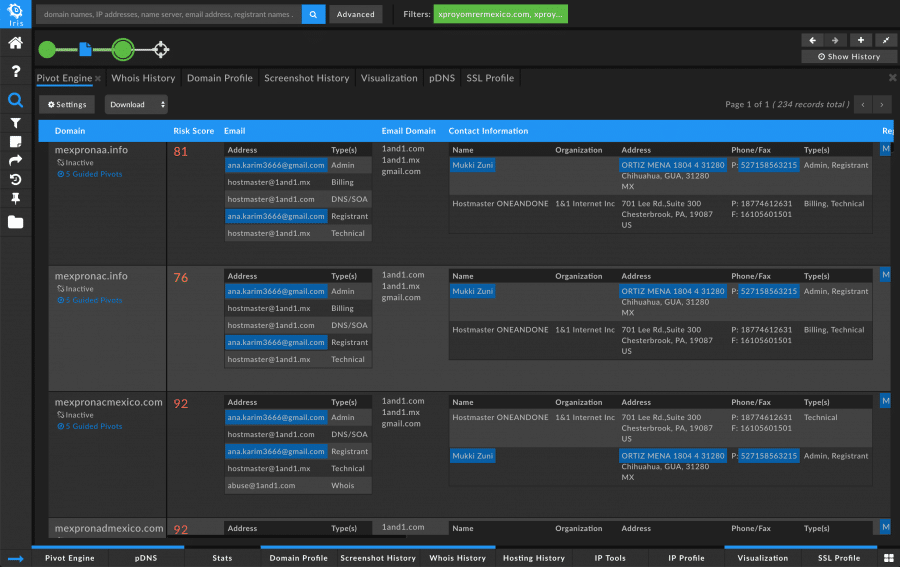
From this point, a researcher could pivot on any of the interesting pieces of information from those domains and uncover a network of badness. Most of the domains on this list had not yet been caught by any major blocklist, so by using Domain Risk Score to identify these as malicious, a researcher can proactively protect their organization from these types of threats.
I hope this example demonstrates how to not only enhance your investigations, but to provide you with a quick indication as to the potential severity of an indicator. Join me next Wednesday, February 13th, as we explore using non-registrant based connections to map connected infrastructure.

