RDAP and BGP in Investigative Journalism
One of the things we’re most proud of at DomainTools is our Grants program. We offer free access and training to investigative journalists, as well as security researchers involved in community-benefiting projects. Yearly presentations at the NICAR investigative reporter conference allow us to share techniques utilizing passive DNS and other domain intelligence that often prove useful in journalism as well. We also provide technical guidance and review, which sometimes brings us deep into third-party investigations. While our grantees are provided confidentiality by default, we recently engaged with a grantee investigation which the stakeholders gave us permission to talk about in the clear.
In this post, we’ll talk about the DomainTools side of the investigation and technical observables. For the deeper context of the stories, please see the original reporting at Frontstory.pl (Polish) and VSquare.org (English).
For the sake of brevity and privacy, some conversations have been condensed or omitted.
Part 1 – RDAP Mistake
In mid-May I had the opportunity to help train about twenty journalists and open-source intelligence (OSINT) analysts on the use of passive DNS and domain intelligence in investigations. These trainings are a favorite part of my job. There is deep overlap between cybersecurity, OSINT, and journalistic investigation skills, techniques, and needs, so the groups are always bright, engaged, and sharp.
In mid-June, we were contacted by two analysts that attended that training on behalf of Frontstory.pl and VSquare. A journalist they were working with uncovered something, but needed more context and provenance to ensure they understood what they were looking at.
Prior to this year, the primary mechanism tying identities to domains has been Whois. Oversight body ICANN deprecated Whois on January 28, 2025 in favor of the Registration Data Access Protocol, or RDAP (more background on that transition here). Protocol changes can be messy and involve learning lessons as you go, the hard way. At DomainTools, we’ve moved swiftly to ensure RDAP is available on our platform, and more work is on the horizon to explore and innovate around this change.
With this context, the analysts wanted to understand connections found between the domains wartears[.]org and foreigncombatants[.]ru, if and how news-front[.]info fit in, and the relationship between several different infrastructure providers. The inquiries began with a finding in Iris Investigate Domain History for wartears[.]org:

A screenshot displaying contact information with dates and times. The admin’s name and part of the contact information are visible and partially redacted. email: [email protected] is shown. Other fields are labeled as “private.
Wartears[.]org showed an open RDAP record being redacted on 2025-04-26, as shown above; in contrast, the Whois service for their registrar still served redacted data. The contact information dovetailed with other parts of the investigation, but further context was needed.
Records for other domains connected to the registrar’s nameservers and Whois/RDAP services surfaced a fascinating initial finding: when we initially ingested the records from hxxp://rdap.mastername[.]ru in November and December of 2024, much of the contact information was unredacted. Multiple unrelated domains using the service showed the same action: RDAP records replaced in April and May 2025 with redacted versions.
While there is more than one possibility to explain these findings, several of us internally agreed upon a likely explanation: given the messy nature of protocol changes, administrators at mastername[.]ru accidentally connected an unredacted customer database to their RDAP query server instead of the redacted database connected to Whois.
Consequently, rdap.mastername[.]ru responded to queries with full, clear RDAP records. When DomainTools requested the RDAP record for wartears[.]org on 2024-12-03, mastername provided the data for an Oleg Makarov with an email address of oleg@ledorub[.]org. At the same time, whois.mastername[.]ru provided a fully-redacted Whois record with marginal investigational value.
What connections could be made with this new information?
Nameservers for the site led us to without[.]ru. In fact, without[.]ru served as an infrastructure hub for a number of Russian-centric domains attributable through Whois and OSINT to an Oleg Makarov, identified in the original reporting linked above. Historical Whois records going back to 2007 reinforced this connection. The OSINT analysts surfaced more artifacts connecting a specific person to the name Oleg Makarov and traced the unredacted RDAP phone number to a Telegram account.
We then turned to the two domains in question.

We defer to Frontstory and VSquare for the deeper details and conclusions related to Oleg Makarov, and turn back to our other technical observations.
Part 2 – The Notorious BGP
The two domains at hand, wartears[.]org and foreigncombatants[.]ru, shared a number of infrastructure characteristics that we explored more deeply for additional context. Created one week apart in 2022, they shared an IP address and host, nameservers, mailservers, and more.

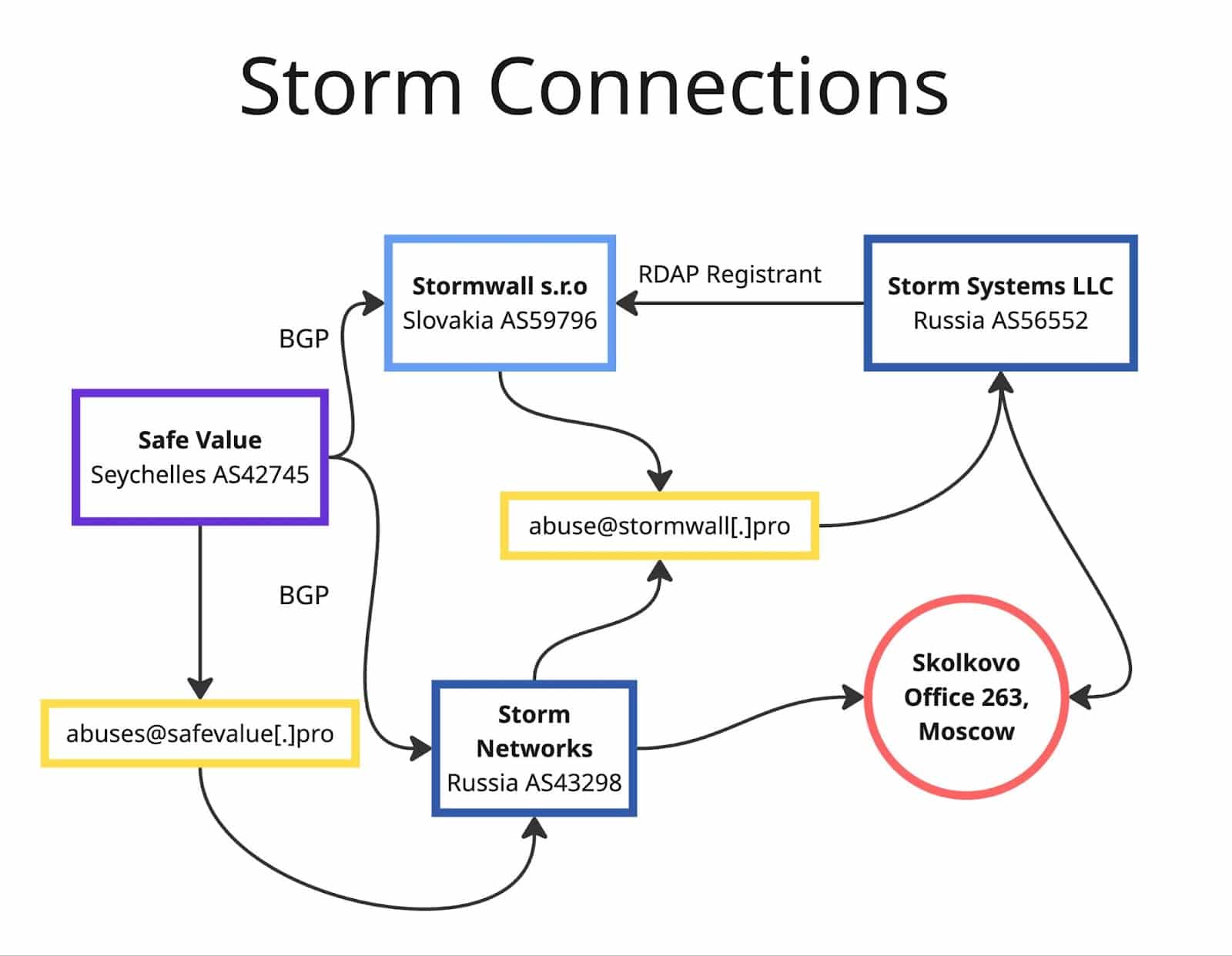
Across a number of domains connected to the larger investigation, we began seeing repeated characteristics: storm-pro[.]net nameservers, and DNS A records connected to Safe Value Limited, Storm Networks (RU), Storm Systems (RU), and Stormwall s.r.o (SK). Of those, the outlier was Safe Value Limited (ASN42745), located in the Seychelles. We decided to examine Safe Value’s current state, and whenever connections between ASNs are involved, BGP is the first thing to look at.
BGP is a complicated concept, but essentially it sits behind DNS and does some of the real core work of the internet. BGP tells you who is supposed to be responsible for announcing what block of IP addresses. BGP information from bgptools tells us that Safe Value (AS42745) has only two upstream connections: Storm Networks (AS43298) and Stormwall (AS59796). They have been the only ways to reach Safe Value from the Internet since 2023-08-09.

Historical BGP records show that Safe Value previously served up to 18 customers/peers but tapered off drastically after 2020. These records also show that Moscow-based Storm Networks (AS43298) is a re-used number applied to a relatively new Autonomous System. In plain language: Storm Networks appeared on 2023-05-17 10:18:30 UTC. Three and a half hours later, it became one of only two providers to Safe Value (2023-05-17 13:41:28), the other being Stormwall s.r.o. This is a strong indicator that Safe Value is likely under the same parent/umbrella network as Storm Networks.
Our analyst partner noted that the RIPE NCC membership website – who enthrones and delegates Autonomous Systems – served three Storm-related membership records with the same address:
Bolshoy Boulevard 42/1, office 263
121205 Moscow
RUSSIAN FEDERATION
This is the address for Skolkovo Innovation Center/Technopark, a Russian attempt at emulating Silicon Valley that has also involved itself in pro-Russian hacking and information operations to the extent that the park’s owning entity is under multiple overlapping US OFAC sanctions, including those targeting “individuals and entities involved in activities that undermine democratic processes and institutions, human rights abuses, and destabilizing activities related to Russia.” (OFAC)
In fact, if we seek further technical artifacts, we can turn to RIPE member RDAP records. Slovakian Stormwall s.r.o. (AS59796) shows an expected SK physical address, but an interesting abuse contact:
Ligurcekova 8
82106
Bratislava
SLOVAKIA
Email: abuse@stormwall[.]pro
Stormwall[.]pro is on IP space owned by Storm Networks in Moscow, with a Russian registrar and Russian mailservers. RDAP records for Storm Networks (AS439298) from rdap.db.ripe[.]net list the Skolkovo Innovation Center address – office 263 for the registrant – and the same abuse contact:
Bolshoy Boulevard 42/1, office 822
121205
Moscow
RUSSIAN FEDERATION
Email: abuse@stormwall[.]pro
In contrast, Safe Value’s RDAP shows a Seychelles physical address and different email address.
Global Gateway 8, Rue de la Perle, Providence, Mahe, Seychelles
Email: abuses@safevalue[.]pro
We should note at this point that safevalue[.]pro is self-hosted, but shows a Russian registrar and Russian mailservers. This is a strong indicator that Safe Value is controlled from the Russian Federation. This is further supported by the rapid winnowing of their customer and peering base, that they are a member of RIPE NCC but do not show up under their official company of the Seychelles.
At this moment, we happen upon Storm Systems LLC (AS56552). The registrant physical address in their RDAP record – essentially, the controlling entity – is the same Skolkovo office registrant office, 263, as Storm Networks. Interestingly, their NOC/technical address is:
821 06, Bratislava, Slovakia, Ligurcekova 8
Storm System LLC’s abuse service physical address is in Russia, and their abuse service email address is abuse@stormwall[.]pro. However, AS56552 has not been observed announcing routes since mid-2023. This likely indicates a subsidiary status for Stormwall s.r.o., possibly being administrated out of Office 263 in Skolkovo.
The narrative isn’t simple, but the takeaway is:

Part 3 – Passive DNS Never Forgets
Having established strong indicators of relationships between the two initial domains (wartears[.]org and foreigncombatants[.]ru) and between multiple infrastructure characteristics (Safe Value in a pinch position between Stormwall s.r.o. and Storm Networks with all three pointing to a sanctioned Moscow technology park), we turned to another pair of domains. A question emerged about how news-front[.]info and news-front[.]su relate to each other.
Our OSINT analyst partner uncovered a number of artifacts through sources like the Wayback Machine. In our case, we turned to historical passive DNS and domain intelligence to show technical and behavioral overlap. Service structure provided circumstantial support for a relationship, but historical passive DNS from DNSDB handed us the smoking gun: news-front[.]su began operating within hours of news-front[.]info ceasing to be observed, both in the main DNS A record as well as mirror-image country-coded subdomain records.

Behaviors can be easy to dismiss. Even some technical observations may not be airtight. But DNS does not lie, and in this case, two records are worth a thousand words.
Conclusion
In this post we presented, with our grantee’s permission, a recent investigation into the connection between two pairs of domains as well as several ASN organizations. Circumstances like the deprecation of an old record protocol for a newer one, information system complexities, and a chance find by an intrepid journalist show the value of technical observables like historical DNS and historical BGP in the course of investigating possible disinformation operations. This is especially true when paired with OSINT such as public identity information, company project announcements, and social media, as seen in the connected stories.
If you have not yet, please read the original reporting by our partners: Frontstory.pl and Vsquare.org.
Alicja Pawłowska contributed greatly to this research. You can find her at https://www.alicjapawlowska.com.
As ever, we at DomainTools are grateful for investigative journalists, OSINT analysts, and other personnel who support them. Together we can continue to work toward a safer Internet, and a progressively better world.
Postscript: Post-publication, we found a change in activity. As of 2025-07-02, Safe Value AS42745 suddenly has two new clients, after years of having none. Seychelles-based Safe Value now announces the IP routes for AS210644 and AS216246, both organizations being Aeza Group out of Russia, sanctioned by US OFAC the day before they became Safe Value clients.


